
- Calculators
- Swot Analysis
- Pestle Analysis
- Five Forces Analysis
- Organizational Structure
- Copywriting
- Research Topics
- Student Resources

Services We Provide

Resources We Provide

Login / Register

- 15 Latest Networking Research Topics for Students
Comparative analysis between snort and suricata IDS software(s)
Description of the topic
The main focus of this research is to conduct a comparative analysis between Snort and Suricata software to determine which IDS software can provide better performance. There are various IDS software(s) available that can be used by organizations but it is difficult to identify which one is best (Aldarwbi et al., 2022). Different organizational structures are often facing problems while setting up an IDS system which results in false positives and intrusions. Through this research, it can be identified which IDS software is better and what secure configuration is required to detect intrusions (Waleed et al., 2022).
Research objectives
- To evaluate Snort and Suricata IDS software(s) to determine the most optimal one.
- To identify the false positive rate of Snort and Suricata on the networked environment.
Research questions
RQ1: Which IDS software can perform better on the production network in terms of performance, security, scalability and reliability?
RQ2: What different ways can be followed to deal with false positive problems in IDS technology?
Research methodology
The given research objectives and research questions can be addressed using quantitative research methodology where an experimental approach can be followed. For the given topic, both Snort and Suricata IDS systems should be configured and tested against different attacks. Depending on the findings, it can be analyzed which IDS software can perform better in terms of performance and security (Shuai & Li, 2021).
- Aldarwbi, M.Y., Lashkari, A.H. and Ghorbani, A.A. (2022) “The sound of intrusion: A novel network intrusion detection system,” Computers and Electrical Engineering , 104, p. 108455.
- Shuai, L. and Li, S. (2021) “Performance optimization of Snort based on DPDK and Hyperscan,” Procedia Computer Science , 183, pp. 837-843.
- Waleed, A., Jamali, A.F. and Masood, A. (2022) “Which open-source ids? Snort, Suricata or Zeek,” Computer Networks , 213, p. 109116.
Role of honeypots and honey nets in network security
Network Security has become essential nowadays and there is a need for setting up robust mechanisms to maintain confidentiality and integrity (Feng et al., 2023). Due to the number of security mechanisms available, organizations found it hard to finalize and implement them on their network. For example, honey pots and honeynet approaches look almost the same and have the same purpose but work differently. Under this research topic, the configuration of honeynets and honeypots can be done to check which one can perform better security in terms of trapping cyber attackers. The entire implementation can be carried out in the cloud-based instance for improved security and it can be identified which type of honey pot technology must be preferred (Maesschalck et al., 2022).
- To set up a honey pot system using Open Canary on the virtual instance to protect against cyber attackers.
- To set up a honeynet system on the virtual instance to assure protection is provided against malicious attackers.
- To test honeypots and honeynets by executing DDoS attacks to check which can provide better security.
RQ1: Why is there a need for using honeypots over honey pots in a production networked environment?
RQ2: What are the differences between cloud-based and local honey pot systems for endpoint protection?
This research can be carried out using the quantitative method of research. At the initial stage, the implementation of honeypots and honeypots can be done on the virtual instance following different security rules. Once the rules are applied, the testing can be performed using a Kali Linux machine to check whether honey pots were effective or honeynets (Gill et al., 2020).
- Feng, H. et al. (2023) “Game theory in network security for Digital Twins in industry,” Digital Communications and Networks [Preprint].
- Gill, K.S., Saxena, S. and Sharma, A. (2020) “GTM-CSEC: A game theoretic model for cloud security based on ids and Honeypot,” Computers & Security , 92, p. 101732
- Maesschalck, S. et al. (2022) “Don’t get stung, cover your ICS in honey: How do honeypots fit within industrial control system security,” Computers & Security , 114, p. 102598.
How do malware variants are progressively improving?
This research can be based on evaluating how malware variants are progressively improving and what should be its state in the coming future. Malware is able to compromise confidential user’s information assets which is why this research can be based on identifying current and future consequences owing to its improvements (Deng et al., 2023). In this field, there is no research work that has been carried out to identify how malware variants are improving their working and what is expected to see in future. Once the evaluation is done, a clear analysis can also be done on some intelligent preventive measures to deal with dangerous malware variants and prevent any kind of technological exploitation (Tang et al., 2023).
- To investigate types of malware variants available to learn more about malware's hidden features.
- To focus on future implications of malware executable programs and how they can be avoided.
- To discuss intelligent solutions to deal with all malware variants.
RQ1: How do improvements in malware variants impact enterprises?
RQ2: What additional solutions are required to deal with malware variants?
In this research, qualitative analysis can be conducted on malware variants and the main reason behind their increasing severity. The entire research can be completed based on qualitative research methodology to answer defined research questions and objectives. Some real-life case studies should also be integrated into the research which can be supported by the selected topic (Saidia Fasci et al., 2023).
- Deng, H. et al. (2023) “MCTVD: A malware classification method based on three-channel visualization and deep learning,” Computers & Security , 126, p. 103084.
- Saidia Fasci, L. et al. (2023) “Disarming visualization-based approaches in malware detection systems,” Computers & Security , 126, p. 103062.
- Tang, Y. et al. (2023) “BHMDC: A byte and hex n-gram based malware detection and classification method,” Computers & Security , p. 103118.
Implementation of IoT - enabled smart office/home using cisco packet tracer
The Internet of Things has gained much more attention over the past few years which is why each enterprise and individual aims at setting up an IoT network to automate their processes (Barriga et al., 2023). This research can be based on designing and implementing an IoT-enabled smart home/office network using Cisco Packet Tracer software. Logical workspace, all network devices, including IoT devices can be used for preparing a logical network star topology (Elias & Ali, 2014). To achieve automation, the use of different IoT rules can be done to allow devices to work based on defined rules.
- To set up an IoT network on a logical workspace using Cisco Packet Tracer simulation software.
- To set up IoT-enabled rules on an IoT registration server to achieve automation (Hou et al., 2023).
RQ: Why is the Cisco packet tracer preferred for network simulation over other network simulators?
At the beginning of this research, a quantitative research methodology can be followed where proper experimental set-up can be done. As a packet tracer is to be used, the star topology can be used to interconnect IoT devices, sensors and other network devices at the home/office. Once a placement is done, the configuration should be done using optimal settings and all IoT devices can be connected to the registration server. This server will have IoT rules which can help in achieving automation by automatically turning off lights and fans when no motion is detected (Baggan et al., 2022).
- Baggan, V. et al. (2022) “A comprehensive analysis and experimental evaluation of Routing Information Protocol: An Elucidation,” Materials Today: Proceedings , 49, pp. 3040–3045.
- Barriga, J.A. et al. (2023) “Design, code generation and simulation of IOT environments with mobility devices by using model-driven development: Simulateiot-Mobile,” Pervasive and Mobile Computing , 89, p. 101751.
- Elias, M.S. and Ali, A.Z. (2014) “Survey on the challenges faced by the lecturers in using packet tracer simulation in computer networking course,” Procedia - Social and Behavioral Sciences , 131, pp. 11–15.
- Hou, L. et al. (2023) “Block-HRG: Block-based differentially private IOT networks release,” Ad Hoc Networks , 140, p. 103059.
Comparative analysis between AODV, DSDV and DSR routing protocols in WSN networks
For wireless sensor networks (WSN), there is a major need for using WSN routing rather than performing normal routines. As WSN networks are self-configured, there is a need for an optimal routing protocol that can improve network performance in terms of latency, jitter, and packet loss (Luo et al., 2023). There are often various problems faced when WSN networks are set up due to a lack of proper routing protocol selection. As a result of this, severe downtime is faced and all links are not able to communicate with each other easily (Hemanand et al., 2023). In this research topic, the three most widely used WSN routing protocols AODV, DSDV and DSR can be compared based on network performance. To perform analysis, three different scenarios can be created in network simulator 2 (Ns2).
- To create three different scenarios on ns2 software to simulate a network for 1 to 100 seconds.
- To analyze which WSN routing is optimal in terms of network performance metrics, including latency, jitter and packet loss.
- To use CBR and NULL agents for all wireless scenarios to start with simulation purposes.
RQ: How do AODV, DSR and DSDV routing protocols differ from each other in terms of network performance?
This research can be carried out using a quantitative research method. The implementation for the provided research topic can be based on Ns2 simulation software where three different scenarios can be created (AODV, DSDV and DSR). For each scenario, NULL, CSR and UDP agents can be done to start with simulation for almost 1 to 100 seconds. For all transmissions made during the given time, network performance can be checked to determine which routing is best (Mohapatra & Kanungo, 2012).
- Human and, D. et al. (2023) “Analysis of power optimization and enhanced routing protocols for Wireless Sensor Networks,” Measurement: Sensors , 25, p. 100610. Available at: https://doi.org/10.1016/j.measen.2022.100610.
- Luo, S., Lai, Y. and Liu, J. (2023) “Selective forwarding attack detection and network recovery mechanism based on cloud-edge cooperation in software-defined wireless sensor network,” Computers & Security , 126, p. 103083. Available at: https://doi.org/10.1016/j.cose.2022.103083.
- Mohapatra, S. and Kanungo, P. (2012) “Performance analysis of AODV, DSR, OLSR and DSDV routing protocols using NS2 Simulator,” Procedia Engineering , 30, pp. 69–76. Available at: https://doi.org/10.1016/j.proeng.2012.01.835.
Securing wireless network using AAA authentication and WLAN controller
Wireless networks often face intrusion attempts due to insecure protocols and sometimes open SSIDs. As a result of this, man-in-the-middle and eavesdropping attacks become easier which results in the loss of confidential information assets (Sivasankari & Kamalakkannan, 2022). When it comes to managing networks in a large area, there are higher chances for attacks that enable cyber attackers in intercepting ongoing communication sessions. However, there is currently no research conducted where the use of AAA authentication has been done with WLAN controllers to make sure a higher level of protection is provided (Nashwan, 2021). The proposed research topic can be based on securing wireless networks with the help of AAA authentication and WLAN controllers. The use of AAA authentication can be done to set up a login portal for users whilst the WLAN controller can be used for managing all wireless access points connected to the network (Nashwan, 2021).
- To set up AAA authentication service on the wireless network simulated on Cisco Packet Tracer for proper access control.
- To set up a WLAN controller on the network to manage all wireless access points effortlessly.
- To use WPA2-PSK protocol on the network to assure guest users are only able to access wireless networks over a secure protocol.
RQ1: What additional benefits are offered by AAA authentication on the WLAN networks?
RQ2: Why are wireless networks more likely to face network intrusions than wired networks?
This research topic is based on the secure implementation of a wireless LAN network using a Cisco packet tracer. Hence, this research can be carried out using a quantitative research method. The implementation can be carried out using AAA authentication which can assure that access control is applied for wireless logins. On the other hand, a WLAN controller can also be configured which can ensure that all WAPs are managed (ZHANG et al., 2012).
- Nashwan, S. (2021) “AAA-WSN: Anonymous Access Authentication Scheme for wireless sensor networks in Big Data Environment,” Egyptian Informatics Journal , 22(1), pp. 15–26.
- Sivasankari, N. and Kamalakkannan, S. (2022) “Detection and prevention of man-in-the-middle attack in IOT network using regression modeling,” Advances in Engineering Software , 169, p. 103126.
- ZHANG, J. et al. (2012) “AAA authentication for Network mobility,” The Journal of China Universities of Posts and Telecommunications , 19(2), pp. 81-86.
OWASP's approach to secure web applications from web application exploits
The research can revolve around the development of web applications by considering OWASP's top 10 rules. Usually, web applications are deployed by organizations depending on their requirements and these applications are vulnerable to various exploits, including injection, broken authentication and other forgery attacks (Poston, 2020). Identifying every single vulnerability is difficult when reference is not taken and often organizations end up hosting a vulnerable server that leads to privacy issues and compromises confidential information easily. In this research, OWASP's top 10 approaches can be followed to develop a secure web application that can be able to protect against top web application exploits. This approach is based on emphasizing severe and minor vulnerabilities which must be patched for protecting against web application attacks (Deepa & Thilagam, 2016).
- The first objective can be setting up an insecure web application on the cloud environment which can be exploited with different techniques.
- The second objective can be to consider all techniques and procedures provided by OWASP's top 10 methodologies.
- The last objective can be applying all fixes to insecure web applications to make them resistant to OWASP top 10 attacks (Sonmez, 2019).
RQ1: What are the benefits of using OWASP's top 10 approaches to harden web applications in comparison to other security approaches?
The research methodology considered for this research project can be quantitative using an experimental approach. The practical work can be done for the selected topic using AWS or the Azure cloud platform. Simply, a virtual web server can be configured and set up with a secure and insecure web application. Following OWASP's top 10 techniques and procedures, the web application can be secured from possible attacks. In addition, insecure applications can also be exploited and results can be evaluated (Applebaum et al., 2021).
- Applebaum, S., Gaber, T. and Ahmed, A. (2021) “Signature-based and machine-learning-based web application firewalls: A short survey,” Procedia Computer Science , 189, pp. 359–367. Available at: https://doi.org/10.1016/j.procs.2021.05.105.
- Deepa, G. and Thilagam, P.S. (2016) “Securing web applications from injection and logic vulnerabilities: Approaches and challenges,” Information and Software Technology , 74, pp. 160–180. Available at: https://doi.org/10.1016/j.infsof.2016.02.005.
- Poston, H. (2020) “Mapping the owasp top Ten to the blockchain,” Procedia Computer Science , 177, pp. 613-617. Available at: https://doi.org/10.1016/j.procs.2020.10.087.
- Sonmez, F.Ö. (2019) “Security qualitative metrics for Open Web Application Security Project Compliance,” Procedia Computer Science , 151, pp. 998-1003. Available at: https://doi.org/10.1016/j.procs.2019.04.140.
Importance of configuring RADIUS (AAA) server on the network
User authentication has become significant nowadays as it guarantees that a legitimate user is accessing the network. But a problem is faced when a particular security control is to be identified for authentication and authorization. These controls can be categorized based on mandatory access controls, role-based access control, setting up captive portals and many more. Despite several other security controls, one of the most efficient ones is the RADIUS server (SONG et al., 2008). This server can authenticate users on the network to make sure network resources are accessible to only legal users. This research topic can be based on understanding the importance of RADIUS servers on the network which can also be demonstrated with the help of the Cisco Packet Tracer. A network can be designed and equipped with a RADIUS server to ensure only legal users can access network resources (WANG et al., 2009).
- To configure RADIUS (AAA) server on the network which can be able to authenticate users who try to access network resources.
- To simulate a network on a packet tracer simulation software and verify network connectivity.
RQ1: What are other alternatives to RADIUS (AAA) authentication servers for network security?
RQ2: What are the common and similarities between RADIUS and TACACS+ servers?
As a logical network is to be designed and configured, a quantitative research methodology can be followed. In this research coursework, a secure network design can be done using a packet tracer network simulator, including a RADIUS server along with the DMZ area. The configuration for the RADIUS server can be done to allow users to only access network resources by authenticating and authorizing (Nugroho et al., 2022).
- Nugroho, Y.S. et al. (2022) “Dataset of network simulator related-question posts in stack overflow,” Data in Brief , 41, p. 107942.
- SONG, M., WANG, L. and SONG, J.-de (2008) “A secure fast handover scheme based on AAA protocol in Mobile IPv6 Networks,” The Journal of China Universities of Posts and Telecommunications , 15, pp. 14-18.
- WANG, L. et al. (2009) “A novel congestion control model for interworking AAA in heterogeneous networks,” The Journal of China Universities of Posts and Telecommunications , 16, pp. 97-101.
Comparing mod security and pF sense firewall to block illegitimate traffic
Firewalls are primarily used for endpoint security due to their advanced features ranging from blocking to IDS capabilities and many more. It is sometimes challenging to identify which type of firewall is best and due to this reason, agencies end up setting up misconfigured firewalls (Tiwari et al., 2022). This further results in a cyber breach, destroying all business operations. The research can be emphasizing conducting a comparison between the two most widely used firewalls i.e. Mod Security and pF sense. Using a virtualized environment, both firewalls can be configured and tested concerning possible cyber-attacks (Lu & Yang, 2020).
- To use the local environment to set up Mod security and pF sense firewall with appropriate access control rules.
- To test both firewalls by executing distributed denial of service attacks from a remote location.
- To compare which type of firewall can provide improved performance and robust security.
RQ: How do Mod security and pF sense differ from each other in terms of features and performance?
The practical experimentation for both firewalls can be done using a virtualized environment where two different machines can be created. Hence, this research can be carried out using a quantitative research method . The first machine can have Mod security and the second machine can have pF sense configured. A new subnet can be created which can have these two machines. The third machine can be an attacking machine which can be used for testing firewalls. The results obtained can be then evaluated to identify which firewall is best for providing security (Uçtu et al., 2021).
- Lu, N. and Yang, Y. (2020) “Application of evolutionary algorithm in performance optimization of Embedded Network Firewall,” Microprocessors and Microsystems , 76, p. 103087.
- Tiwari, A., Papini, S. and Hemamalini, V. (2022) “An enhanced optimization of parallel firewalls filtering rules for scalable high-speed networks,” Materials Today: Proceedings , 62, pp. 4800-4805.
- Uçtu, G. et al. (2021) “A suggested testbed to evaluate multicast network and threat prevention performance of Next Generation Firewalls,” Future Generation Computer Systems , 124, pp. 56-67.
Conducting a comprehensive investigation on the PETYA malware
The main purpose of this research is to conduct a comprehensive investigation of the PETYA malware variant (McIntosh et al., 2021). PETYA often falls under the category of ransomware attacks which not only corrupt and encrypt files but can compromise confidential information easily. Along with PETYA, there are other variants also which lead to a security outage and organizations are not able to detect these variants due to a lack of proper detection capabilities (Singh & Singh, 2021). In this research, a comprehensive analysis has been done on PETYA malware to identify its working and severity level. Depending upon possible causes of infection of PETYA malware, some proactive techniques can also be discussed (Singh & Singh, 2021). A separation discussion can also be made on other malware variants, their features, and many more.
- The main objective of this research is to scrutinize the working of PETYA malware because a ransomware attack can impact the micro and macro environment of the organizations severely.
- The working of PETYA malware along with its source code can be reviewed to identify its structure and encryption type.
- To list all possible CVE IDs which are exploited by the PETYA malware.
RQ1: How dangerous is PETYA malware in comparison to other ransomware malware?
This research can be based on qualitative research methodology to evaluate the working of PETYA malware from various aspects, the methodology followed and what are its implications. The research can be initiated by evaluating the working of PETYA malware, how it is triggered, what encryption is applied and other factors. A sample source code can also be analyzed to learn more about how cryptography is used with ransomware (Abijah Roseline & Geetha, 2021).
- Abijah Roseline, S. and Geetha, S. (2021) “A comprehensive survey of tools and techniques mitigating computer and mobile malware attacks,” Computers & Electrical Engineering , 92, p. 107143.
- McIntosh, T. et al. (2021) “Enforcing situation-aware access control to build malware-resilient file systems,” Future Generation Computer Systems , 115, pp. 568-582.
- Singh, J. and Singh, J. (2021) “A survey on machine learning-based malware detection in executable files,” Journal of Systems Architecture , 112, p. 101861.
Setting up a Live streaming server on the cloud platform
Nowadays, various organizations require a live streaming server to stream content depending upon their business. However, due to a lack of proper hardware, organizations are likely to face high network congestion, slowness and other problems (Ji et al., 2023). Referring to the recent cases, it has been observed that setting up a streaming server on the local environment is not expected to perform better than a cloud-based streaming server configuration (Martins et al., 2019). This particular research topic can be based on setting up a live streaming server on the AWS or Azure cloud platform to make sure high network bandwidth is provided with decreased latency. The research gap analysis would be conducted to analyze the performance of live streaming servers on local and cloud environments in terms of network performance metrics (Bilal et al., 2018).
- To set up a live streaming server on the AWS or Azure cloud platform to provide live streaming services.
- To use load balancers alongside streaming servers to ensure the load is balanced and scalability is achieved.
- To use Wireshark software to test network performance during live streaming.
RQ1: Why are in-house streaming servers not able to provide improved performance in comparison to cloud-based servers?
RQ2: What additional services are provided by cloud service providers which help in maintaining network performance?
The implementation is expected to carry out on the AWS cloud platform with other AWS services i.e. load balancer, private subnet and many more (Efthymiopoulou et al., 2017). Hence, this research can be carried out using a quantitative research method. The configuration of ec2 instances can be done which can act as a streaming server for streaming media and games. For testing this project, the use of OBS studio can be done which can help in checking whether streaming is enabled or not. For network performance, Wireshark can be used for testing network performance (George et al., 2020).
- Bilal, KErbad, A. and Hefeeda, M. (2018) “QoE-aware distributed cloud-based live streaming of multi-sourced Multiview Videos,” Journal of Network and Computer Applications , 120, pp. 130-144.
- Efthymiopoulou, M. et al. (2017) “Robust control in cloud-assisted peer-to-peer live streaming systems,” Pervasive and Mobile Computing , 42, pp. 426-443.
- George, L.C. et al. (2020) “Usage visualization for the AWS services,” Procedia Computer Science , 176, pp. 3710–3717.
- Ji, X. et al. (2023) “Adaptive QoS-aware multipath congestion control for live streaming,” Computer Networks , 220, p. 109470.
- Martins, R. et al. (2019) “Iris: Secure reliable live-streaming with Opportunistic Mobile Edge Cloud offloading,” Future Generation Computer Systems , 101, pp. 272-292.
Significance of using OSINT framework for Network reconnaissance
Network reconnaissance is becoming important day by day when it comes to penetration testing. Almost all white hat hackers are dependent on the OSINT framework to start with network reconnaissance and footprinting when it comes to evaluating organizational infrastructure. On the other hand, cyber attackers are also using this technique to start fetching information about their target. Currently, there is no investigation carried out to identify how effective the OSINT framework is over traditional reconnaissance activities (Liu et al., 2022). This research is focused on using OSINT techniques to analyze victims using different sets of tools like Maltego, email analysis and many other techniques. The analysis can be based on fetching sensitive information about the target which can be used for conducting illegal activities (Abdullah, 2019).
- To use Maltego software to conduct network reconnaissance on the target by fetching sensitive information.
- To compare the OSINT framework with other techniques to analyze why it performs well.
RQ1: What is the significance of using the OSINT framework in conducting network reconnaissance?
RQ2: How can the OSINT framework be used by cyber hackers for conducting illegitimate activities?
The OSINT framework is easily accessible on its official website where different search options are given. Hence, this research can be carried out using a quantitative research method. Depending upon the selected target, each option can be selected and tools can be shortlisted for final implementation. Once the tools are shortlisted, they can be used to conduct network reconnaissance (González-Granadillo et al., 2021). For example, Maltego can be used as it is a powerful software to fetch information about the target.
- Abdullah, S.A. (2019) “Seui-64, bits an IPv6 addressing strategy to mitigate reconnaissance attacks,” Engineering Science and Technology , an International Journal, 22(2), pp. 667–672.
- Gonzalez-Granadillo, G. et al. (2021) “ETIP: An enriched threat intelligence platform for improving OSINT correlation, analysis, visualization and sharing capabilities,” Journal of Information Security and Applications , 58, p. 102715.
- Liu, W. et al. (2022) “A hybrid optimization framework for UAV Reconnaissance Mission Planning,” Computers & Industrial Engineering , 173, p. 108653.
Wired and wireless network hardening in cisco packet tracer
At present, network security has become essential and if enterprises are not paying attention to the security infrastructure, there are several chances for cyber breaches. To overcome all these issues, there is a need for setting up secure wired and wireless networks following different techniques such as filtered ports, firewalls, VLANs and other security mechanisms. For the practical part, the use of packet tracer software can be done to design and implement a highly secure network (Sun, 2022).
- To use packet tracer simulation software to set up secure wired and wireless networks.
- Use different hardening techniques, including access control rules, port filtering, enabling passwords and many more to assure only authorized users can access the network (Zhang et al., 2012).
RQ: Why is there a need for emphasizing wired and wireless network security?
Following the quantitative approach, the proposed research topic implementation can be performed in Cisco Packet Tracer simulation software. Several devices such as routers, switches, firewalls, wireless access points, hosts and workstations can be configured and interconnected using Cat 6 e cabling. For security, every device can be checked and secure design principles can be followed like access control rules, disabled open ports, passwords, encryption and many more (Smith & Hasan, 2020).
- Smith, J.D. and Hasan, M. (2020) “Quantitative approaches for the evaluation of Implementation Research Studies,” Psychiatry Research , 283, p. 112521.
- Sun, J. (2022) “Computer Network Security Technology and prevention strategy analysis,” Procedia Computer Science , 208, pp. 570–576.
- Zhang, YLiang, R. and Ma, H. (2012) “Teaching innovation in computer network course for undergraduate students with a packet tracer,” IERI Procedia , 2, pp. 504–510.
Different Preemptive ways to resist spear phishing attacks
When it comes to social engineering, phishing attacks are rising and are becoming one of the most common ethical issues as it is one of the easiest ways to trick victims into stealing information. This research topic is based on following different proactive techniques which would help in resisting spear phishing attacks (Xu et al., 2023). This can be achieved by using the Go-Phish filter on the machine which can automatically detect and alert users as soon as the phished URL is detected. It can be performed on the cloud platform where the apache2 server can be configured along with an anti-phishing filter to protect against phishing attacks (Yoo & Cho, 2022).
- To set up a virtual instance on the cloud platform with an apache2 server and anti-phishing software to detect possible phishing attacks.
- To research spear phishing and other types of phishing attacks that can be faced by victims (Al-Hamar et al., 2021).
RQ1: Are phishing attacks growing just like other cyber-attacks?
RQ2: How effective are anti-phishing filters in comparison to cyber awareness sessions?
The entire research can be conducted by adhering to quantitative research methodology which helps in justifying all research objectives and questions. The implementation of the anti-phishing filter can be done by creating a virtual instance on the cloud platform which can be configured with an anti-phishing filter. Along with this, some phishing attempts can also be performed to check whether the filter works or not (Siddiqui et al., 2022).
- Al-Hamar, Y. et al. (2021) “Enterprise credential spear-phishing attack detection,” Computers & Electrical Engineering , 94, p. 107363.
- Siddiqui, N. et al. (2022) “A comparative analysis of US and Indian laws against phishing attacks,” Materials Today: Proceedings , 49, pp. 3646–3649.
- Xu, T., Singh, K. and Rajivan, P. (2023) “Personalized persuasion: Quantifying susceptibility to information exploitation in spear-phishing attacks,” Applied Ergonomics , 108, p. 103908.
- Yoo, J. and Cho, Y. (2022) “ICSA: Intelligent chatbot security assistant using text-CNN and multi-phase real-time defense against SNS phishing attacks,” Expert Systems with Applications , 207, p. 117893.
Evaluating the effectiveness of distributed denial of service attacks
The given research topic is based on evaluating the effectiveness of distributed denial of service attacks on cloud and local environments. Hence, this research can be carried out using a quantitative research method. Cyber attackers find DDoS as one of the most dangerous technological exploitation when it comes to impacting network availability (Krishna Kishore et al., 2023). This research can revolve around scrutinizing the impact of DDoS attacks on the local environment and cloud environment. This can be done by executing DDoS attacks on a simulated environment using hoping or other software(s) to check where it has a higher magnitude (de Neira et al., 2023).
- To set up a server on the local and cloud environment to target using DDoS attacks for checking which had experienced slowness.
- To determine types of DDoS attack types, their magnitude and possible mitigation techniques.
RQ: Why do DDoS attacks have dynamic nature and how is it likely to sternly impact victims?
The experimentation for this research can be executed by creating a server on the local and cloud environment. Hence, this research can be carried out using a quantitative research method. These servers can be set up as web servers using apache 2 service. On the other hand, a Kali Linux machine can be configured with DDoS execution software. Each server can be targeted with DDoS attacks to check its effectiveness (Benlloch-Caballero et al., 2023).
- Benlloch-Caballero, P., Wang, Q. and Alcaraz Calero, J.M. (2023) “Distributed dual-layer autonomous closed loops for self-protection of 5G/6G IOT networks from distributed denial of service attacks,” Computer Networks , 222, p. 109526.
- de Neira, A.B., Kantarci, B. and Nogueira, M. (2023) “Distributed denial of service attack prediction: Challenges, open issues and opportunities,” Computer Networks , 222, p. 109553.
- Krishna Kishore, P., Ramamoorthy, S. and Rajavarman, V.N. (2023) “ARTP: Anomaly-based real time prevention of distributed denial of service attacks on the web using machine learning approach,” International Journal of Intelligent Networks , 4, pp. 38–45.
Recommended Readings
Latest Web Development Research Topics
Top Management Research Topics
Newest AI Research Topics

Research in every field is becoming more and more essential because of constant developments around the world. Similar is the case in the field of networking. This is the reason; students who are preparing to master the field of networking need to keep their knowledge of the current state of the art in the field up to date.
However, choosing the right research topic often becomes a tough task for students to carry out their research effectively. That being the case, this list contains 15 latest research topics in the field of networking. Whether you are a seasoned researcher or just starting, this list can provide you with ample inspiration and guidance to drive your research forward in the dynamic and evolving field of Networking.
Copyright © 2023 CrowJack. All Rights Reserved
- Our Promise
- Our Achievements
- Our Mission
- Proposal Writing
- System Development
- Paper Writing
- Paper Publish
- Synopsis Writing
- Thesis Writing
- Assignments
- Survey Paper
- Conference Paper
- Journal Paper
- Empirical Paper
- Journal Support
- Top 5 Interesting Computer Network Research Topics
A computer network is a network of diverse computing hardware linked through different communication technologies to share various resources . The communication links of the network can be either wired (cables) or wireless (radio waves / IR signals).
This page shows you useful information on Computer Network Research Topics, Projects with Source Code, Research Areas, Project Topics, and Tools!!!
Moreover, the network can be differentiated in the characteristics of constrained resources, network structure, requests history/demand, communication technologies , and more. However, it is flexible to share resources, and it has some technical challenges in real-time development. Here, we have given you the common services that we offer for overcoming network issues.
Our Approaches and Services to Solving Computer Network Issues
- Communication technologies selection
- Communication protocols in the network
- Performing both conceptual and practical research
- Study in qualitative and quantitative aspects
- Simulation Models
- Proofs / Theorems / Prototypes Testing / Use Cases
- Experiments for Various Simulation Scenarios
- Graphical / Tabular Representation of Results
- Developing New Techniques
- Thinking Novel Ideas
- Multiple Evaluations
- IEEE Standards Refinement
The layering approach in networking is used to divide the message into various chunks . Basically, there are seven layers in the networking process where each layer has unique responsibilities. All these layers co-operatively work together to transfer the message from one end to another (i.e., source to destination ). Now, we can see the available layers and their function in sequential order.
What are the layers of computer networks?
- Physical Layer – Used for offering mechanical / electrical needs, distribute the bits through transmission medium
- Data Link Layer – Used for offering hop-to-hop distribution, arrange the bits into frames
- Network Layer – Used for offering internetworking, pass over the packets between source and destination
- Transport Layer – Used for offering error correction and process-to-process distribution
- Session Layer – Used for launching and manage temporary sessions
- Presentation Layer – Used for data translation, compression, and encryption
- Application Layer – User for users to access the network resources / services
With an aim to support wireless communications, numerous different technologies have been launched. Before selecting this technology, one should undergo deep study on which is more suitable for their computer network projects . Our research team will help you in both business/individual if you need the best guidance over that selection of innovative computer network research topics . Usually, we recommend the technology based on the requirement of your selected networking projects for final year students . For your information, here we have given you a few lists of communication technologies,
Communication Technologies in Computer Networks
- Wi-Fi and Wi-Max
- Radio Frequency Identification (RFID)
- Ultra-Wideband, Bluetooth and Zigbee
- Global Positioning System (GPS)
- Mobile Communication (4G, 5G, 5G Beyond and 6G)
- Radar and Satellite Communication
- 3GPP – LTE-M, EC-GSM and Narrowband-IoT
- Non-3GPP – Sigfox, Wieghtless and LoRa
In recent days, you can witness the gradual growth of computer networks in networking industries through many new developments. It includes so many technologies to portrait the actual networking industry’s performance. Here, we have given you some new networking technologies that are expected to master the next networking industries. .
Current Technologies in Computer Networks
- Artificial Intelligence (AI) and Cloud Repatriation
- Software Defined Networks
- Fog-Edge Computing
- UAV-Wireless Data Links
- Responsive Internet Architecture
- Multiple Cloud Services Technology
- Internet of Things and Inter-Networking
- Quantum and Serverless Computing
- 5G enabled Nano Technology
- Digital Twin and Machine Learning (ML)
- Digital Communications
- Network Communications Protocols
For illustrative purpose, Digital Communication work in accordance with enabling communication technologies, modulation, signal processing projects, channel modeling, and error control . Similarly, Network Communications Protocols take an in-charge of routing, resource allocation, data distribution, and medium access control.
Both technologies/areas have high capabilities in a different dimension of the networking process. And they are network designing, model construction, networking testing on testbeds, experimental analysis, and performance assessments. Our researchers have given you the currently ongoing of innovative computer network research topics mentioned below for your reference.
Latest Computer Network Research Topics
- Enhancing System Robustness in Decentralized Network
- Improving Network Quality of Services and Resource Usage
- SLA–Aware Resource Scheduling and Provisioning
- Network Architectures Design and Processes Management
How to develop computer networks projects with source code?
Basically, networking is a widespread process where network construction and deployment in the real world is a challenging job. So, the entire process is fragmented into different tasks where they are performed by a set of skilled networking engineers as follows,
- Software Developer – Design and build software applications
- Networking Experts – modeling the network structure
- Database Admin – Store and manage the network information
- Support Specialist – Analyze the connected entities of the system
- Programmer – Develop the suitable code works for achieving required performance
For research purposes, we can simulate the original network behavior and performance inappropriate simulation tools. Most importantly, it reduces the cost of real-time implementation and deployment.
Our developers have long-term experience in handling networking concepts . So, if you need the best Computer Networks Projects with Source Code support , you can approach our team. Below, we have also mentioned our qualified services in your project.
- We do both conceptual and practical study on recent research topics
- We design unique network simulation models, proof-of-concept prototypes and investigational testbeds
- We employ result guaranteed new technologies to upgrade and assess the existing standard of networking systems
- We develop own algorithm, protocols and hybrid techniques based on project requirements
- We precisely access the network performance using suitable network parameters for comparative study of different systems
Performance Analysis of Computer Networks
Now, we can see the performance measurement of the networking model. Through the sophisticated simulation tool / experimental testbeds , we can develop any kind of network scenario. Once the model is processed, then the efficiency of the model is verified by several metrics. Here, we have given you the metrics along with different modelling techniques .
- Medium Access Control – Retransmissions Delay, Collisions and Packet loss
- Network Protocols – Latency, Throughput and Packet loss
- RF Channel Models – Noise, Shadowing and Fading
- Spectrum (Sense and Observation) – Latency and Detection Trustworthiness
- Links and Transceivers – Block error ratio and Signal-to-Noise Ratio (SNR)
What is computer network simulation?
Simulate the network model based on the code of the software application . Through code, we can instruct the model to perform our project requirements. At the end of the simulation, it yields the overall performance and behaviour of the network in different dimensions and metrics. Further, it also measures the communication between the network entities.
Purposes of source code
The source code of software has the main responsibility to create strong basements for designing and simulating the network model . Through the code only, the developers can make the smart work to tackle the problem in a simplified way. Effective code work is also a part of the contribution in research.
Since your code can help for learning or reusability (other application development), for your clarity, our developers will explain the implementation of research methodologies while delivering Computer Networks Projects with Source Code . Below, we have given you the different simulations of real-time network models,
How does computer network simulation works?
- Plan and design the model
- Develop the suitable hypothesis model
- Forecast the hypothetical aspects
- Perform comparative study to improve the hypothesis
- Simulate the developed model
- Based on experimental results, relate and enhance the hypothesis / model
- Do the experiments and get the results
So far, we have discussed computer networks, network layers, communication technologies, current research areas, computer network research topics, project simulation, and performance estimation . Now, our development team has a list of widely used network simulator tools.
Network simulators let the users modify the simulator operations for their project needs. Then the users can analyze the system performance and entity behavior under different circumstances. Further, it supports communication standards/protocols like TCP, WLAN, CR, Wi-Max, WSN , and many more. Here, we have given you the list of a few best result yielding simulators which is more apt for computer network simulations,
- Component-based network simulator with graphical user interface support
- Allow to design traffic models, decentralized system, protocols, computer networks, multi-processors, and many more
- Further, it enables animated and responsive simulation in modular environs
- Empower to design and deploy network application, device and infrastructure
- Develop predictive model, protocol and communication networks to interpret the network functionalities
- Support both real-time wired and wireless models
- Allow to create Finite State Automata for figuring out the network behavior
- Easy to design and develop traffic models
- Utilize QualNet analyzer to understand the obtained simulated outcome
- Enabled OS: Linux and Windows
For instance, NS3 (network Simulator 3) is detailed here.
NS3 is one of the best simulation tools to design and simulate networking projects . With the help of this tool, we can virtually design different nodes through Helper classes. By the by, it enables the installation of internet stacks, applications, devices, and many more. Further, we can insert parameters in the channel for performance evaluation in implementing computer network research topics . And let them produce traffic at runtime and pass the packets from source to destination through the selected route path. The other special features are given as follows,
- Create pcap file to get the core information of the transmitting packets. For instance: Source IP, Sequence no, Destination IP, etc. Employ Wireshark tool to view the pcap.
- Trace the network route for assess number of packets send/receive. For this purpose, the trace files will be produced automatically to monitor whole network.
- Easy to plot the graph from obtained simulation outcome in with assurance of preciseness.
- Network Animator is released to depict the realistic view of the network through animation. It shows you the real structure and how the data are transferred between nodes.
To sum up, we have sufficient technical professionals to support you in all the latest research areas of computer networks . In addition, our developments also give you the best assistance in project development from tool selection to result in an assessment. So, if you need our reliable service computer network research topics, projects with source code then communicate our team.
MILESTONE 1: Research Proposal
Finalize journal (indexing).
Before sit down to research proposal writing, we need to decide exact journals. For e.g. SCI, SCI-E, ISI, SCOPUS.
Research Subject Selection
As a doctoral student, subject selection is a big problem. Phdservices.org has the team of world class experts who experience in assisting all subjects. When you decide to work in networking, we assign our experts in your specific area for assistance.
Research Topic Selection
We helping you with right and perfect topic selection, which sound interesting to the other fellows of your committee. For e.g. if your interest in networking, the research topic is VANET / MANET / any other
Literature Survey Writing
To ensure the novelty of research, we find research gaps in 50+ latest benchmark papers (IEEE, Springer, Elsevier, MDPI, Hindawi, etc.)
Case Study Writing
After literature survey, we get the main issue/problem that your research topic will aim to resolve and elegant writing support to identify relevance of the issue.
Problem Statement
Based on the research gaps finding and importance of your research, we conclude the appropriate and specific problem statement.
Writing Research Proposal
Writing a good research proposal has need of lot of time. We only span a few to cover all major aspects (reference papers collection, deficiency finding, drawing system architecture, highlights novelty)
MILESTONE 2: System Development
Fix implementation plan.
We prepare a clear project implementation plan that narrates your proposal in step-by step and it contains Software and OS specification. We recommend you very suitable tools/software that fit for your concept.
Tools/Plan Approval
We get the approval for implementation tool, software, programing language and finally implementation plan to start development process.
Pseudocode Description
Our source code is original since we write the code after pseudocodes, algorithm writing and mathematical equation derivations.
Develop Proposal Idea
We implement our novel idea in step-by-step process that given in implementation plan. We can help scholars in implementation.
Comparison/Experiments
We perform the comparison between proposed and existing schemes in both quantitative and qualitative manner since it is most crucial part of any journal paper.
Graphs, Results, Analysis Table
We evaluate and analyze the project results by plotting graphs, numerical results computation, and broader discussion of quantitative results in table.
Project Deliverables
For every project order, we deliver the following: reference papers, source codes screenshots, project video, installation and running procedures.
MILESTONE 3: Paper Writing
Choosing right format.
We intend to write a paper in customized layout. If you are interesting in any specific journal, we ready to support you. Otherwise we prepare in IEEE transaction level.
Collecting Reliable Resources
Before paper writing, we collect reliable resources such as 50+ journal papers, magazines, news, encyclopedia (books), benchmark datasets, and online resources.
Writing Rough Draft
We create an outline of a paper at first and then writing under each heading and sub-headings. It consists of novel idea and resources
Proofreading & Formatting
We must proofread and formatting a paper to fix typesetting errors, and avoiding misspelled words, misplaced punctuation marks, and so on
Native English Writing
We check the communication of a paper by rewriting with native English writers who accomplish their English literature in University of Oxford.
Scrutinizing Paper Quality
We examine the paper quality by top-experts who can easily fix the issues in journal paper writing and also confirm the level of journal paper (SCI, Scopus or Normal).
Plagiarism Checking
We at phdservices.org is 100% guarantee for original journal paper writing. We never use previously published works.
MILESTONE 4: Paper Publication
Finding apt journal.
We play crucial role in this step since this is very important for scholar’s future. Our experts will help you in choosing high Impact Factor (SJR) journals for publishing.
Lay Paper to Submit
We organize your paper for journal submission, which covers the preparation of Authors Biography, Cover Letter, Highlights of Novelty, and Suggested Reviewers.
Paper Submission
We upload paper with submit all prerequisites that are required in journal. We completely remove frustration in paper publishing.
Paper Status Tracking
We track your paper status and answering the questions raise before review process and also we giving you frequent updates for your paper received from journal.
Revising Paper Precisely
When we receive decision for revising paper, we get ready to prepare the point-point response to address all reviewers query and resubmit it to catch final acceptance.
Get Accept & e-Proofing
We receive final mail for acceptance confirmation letter and editors send e-proofing and licensing to ensure the originality.
Publishing Paper
Paper published in online and we inform you with paper title, authors information, journal name volume, issue number, page number, and DOI link
MILESTONE 5: Thesis Writing
Identifying university format.
We pay special attention for your thesis writing and our 100+ thesis writers are proficient and clear in writing thesis for all university formats.
Gathering Adequate Resources
We collect primary and adequate resources for writing well-structured thesis using published research articles, 150+ reputed reference papers, writing plan, and so on.
Writing Thesis (Preliminary)
We write thesis in chapter-by-chapter without any empirical mistakes and we completely provide plagiarism-free thesis.
Skimming & Reading
Skimming involve reading the thesis and looking abstract, conclusions, sections, & sub-sections, paragraphs, sentences & words and writing thesis chorological order of papers.
Fixing Crosscutting Issues
This step is tricky when write thesis by amateurs. Proofreading and formatting is made by our world class thesis writers who avoid verbose, and brainstorming for significant writing.
Organize Thesis Chapters
We organize thesis chapters by completing the following: elaborate chapter, structuring chapters, flow of writing, citations correction, etc.
Writing Thesis (Final Version)
We attention to details of importance of thesis contribution, well-illustrated literature review, sharp and broad results and discussion and relevant applications study.
How PhDservices.org deal with significant issues ?
1. novel ideas.
Novelty is essential for a PhD degree. Our experts are bringing quality of being novel ideas in the particular research area. It can be only determined by after thorough literature search (state-of-the-art works published in IEEE, Springer, Elsevier, ACM, ScienceDirect, Inderscience, and so on). SCI and SCOPUS journals reviewers and editors will always demand “Novelty” for each publishing work. Our experts have in-depth knowledge in all major and sub-research fields to introduce New Methods and Ideas. MAKING NOVEL IDEAS IS THE ONLY WAY OF WINNING PHD.
2. Plagiarism-Free
To improve the quality and originality of works, we are strictly avoiding plagiarism since plagiarism is not allowed and acceptable for any type journals (SCI, SCI-E, or Scopus) in editorial and reviewer point of view. We have software named as “Anti-Plagiarism Software” that examines the similarity score for documents with good accuracy. We consist of various plagiarism tools like Viper, Turnitin, Students and scholars can get your work in Zero Tolerance to Plagiarism. DONT WORRY ABOUT PHD, WE WILL TAKE CARE OF EVERYTHING.
3. Confidential Info
We intended to keep your personal and technical information in secret and it is a basic worry for all scholars.
- Technical Info: We never share your technical details to any other scholar since we know the importance of time and resources that are giving us by scholars.
- Personal Info: We restricted to access scholars personal details by our experts. Our organization leading team will have your basic and necessary info for scholars.
CONFIDENTIALITY AND PRIVACY OF INFORMATION HELD IS OF VITAL IMPORTANCE AT PHDSERVICES.ORG. WE HONEST FOR ALL CUSTOMERS.
4. Publication
Most of the PhD consultancy services will end their services in Paper Writing, but our PhDservices.org is different from others by giving guarantee for both paper writing and publication in reputed journals. With our 18+ year of experience in delivering PhD services, we meet all requirements of journals (reviewers, editors, and editor-in-chief) for rapid publications. From the beginning of paper writing, we lay our smart works. PUBLICATION IS A ROOT FOR PHD DEGREE. WE LIKE A FRUIT FOR GIVING SWEET FEELING FOR ALL SCHOLARS.
5. No Duplication
After completion of your work, it does not available in our library i.e. we erased after completion of your PhD work so we avoid of giving duplicate contents for scholars. This step makes our experts to bringing new ideas, applications, methodologies and algorithms. Our work is more standard, quality and universal. Everything we make it as a new for all scholars. INNOVATION IS THE ABILITY TO SEE THE ORIGINALITY. EXPLORATION IS OUR ENGINE THAT DRIVES INNOVATION SO LET’S ALL GO EXPLORING.
Client Reviews
I ordered a research proposal in the research area of Wireless Communications and it was as very good as I can catch it.
I had wishes to complete implementation using latest software/tools and I had no idea of where to order it. My friend suggested this place and it delivers what I expect.
It really good platform to get all PhD services and I have used it many times because of reasonable price, best customer services, and high quality.
My colleague recommended this service to me and I’m delighted their services. They guide me a lot and given worthy contents for my research paper.
I’m never disappointed at any kind of service. Till I’m work with professional writers and getting lot of opportunities.
- Christopher
Once I am entered this organization I was just felt relax because lots of my colleagues and family relations were suggested to use this service and I received best thesis writing.
I recommend phdservices.org. They have professional writers for all type of writing (proposal, paper, thesis, assignment) support at affordable price.
You guys did a great job saved more money and time. I will keep working with you and I recommend to others also.
These experts are fast, knowledgeable, and dedicated to work under a short deadline. I had get good conference paper in short span.
Guys! You are the great and real experts for paper writing since it exactly matches with my demand. I will approach again.
I am fully satisfied with thesis writing. Thank you for your faultless service and soon I come back again.
Trusted customer service that you offer for me. I don’t have any cons to say.
I was at the edge of my doctorate graduation since my thesis is totally unconnected chapters. You people did a magic and I get my complete thesis!!!
- Abdul Mohammed
Good family environment with collaboration, and lot of hardworking team who actually share their knowledge by offering PhD Services.
I enjoyed huge when working with PhD services. I was asked several questions about my system development and I had wondered of smooth, dedication and caring.
I had not provided any specific requirements for my proposal work, but you guys are very awesome because I’m received proper proposal. Thank you!
- Bhanuprasad
I was read my entire research proposal and I liked concept suits for my research issues. Thank you so much for your efforts.
- Ghulam Nabi
I am extremely happy with your project development support and source codes are easily understanding and executed.
Hi!!! You guys supported me a lot. Thank you and I am 100% satisfied with publication service.
- Abhimanyu
I had found this as a wonderful platform for scholars so I highly recommend this service to all. I ordered thesis proposal and they covered everything. Thank you so much!!!
Related Pages
- Privacy Policy

Home » 500+ Computer Science Research Topics
500+ Computer Science Research Topics

Computer Science is a constantly evolving field that has transformed the world we live in today. With new technologies emerging every day, there are countless research opportunities in this field. Whether you are interested in artificial intelligence, machine learning, cybersecurity, data analytics, or computer networks, there are endless possibilities to explore. In this post, we will delve into some of the most interesting and important research topics in Computer Science. From the latest advancements in programming languages to the development of cutting-edge algorithms, we will explore the latest trends and innovations that are shaping the future of Computer Science. So, whether you are a student or a professional, read on to discover some of the most exciting research topics in this dynamic and rapidly expanding field.
Computer Science Research Topics
Computer Science Research Topics are as follows:
- Using machine learning to detect and prevent cyber attacks
- Developing algorithms for optimized resource allocation in cloud computing
- Investigating the use of blockchain technology for secure and decentralized data storage
- Developing intelligent chatbots for customer service
- Investigating the effectiveness of deep learning for natural language processing
- Developing algorithms for detecting and removing fake news from social media
- Investigating the impact of social media on mental health
- Developing algorithms for efficient image and video compression
- Investigating the use of big data analytics for predictive maintenance in manufacturing
- Developing algorithms for identifying and mitigating bias in machine learning models
- Investigating the ethical implications of autonomous vehicles
- Developing algorithms for detecting and preventing cyberbullying
- Investigating the use of machine learning for personalized medicine
- Developing algorithms for efficient and accurate speech recognition
- Investigating the impact of social media on political polarization
- Developing algorithms for sentiment analysis in social media data
- Investigating the use of virtual reality in education
- Developing algorithms for efficient data encryption and decryption
- Investigating the impact of technology on workplace productivity
- Developing algorithms for detecting and mitigating deepfakes
- Investigating the use of artificial intelligence in financial trading
- Developing algorithms for efficient database management
- Investigating the effectiveness of online learning platforms
- Developing algorithms for efficient and accurate facial recognition
- Investigating the use of machine learning for predicting weather patterns
- Developing algorithms for efficient and secure data transfer
- Investigating the impact of technology on social skills and communication
- Developing algorithms for efficient and accurate object recognition
- Investigating the use of machine learning for fraud detection in finance
- Developing algorithms for efficient and secure authentication systems
- Investigating the impact of technology on privacy and surveillance
- Developing algorithms for efficient and accurate handwriting recognition
- Investigating the use of machine learning for predicting stock prices
- Developing algorithms for efficient and secure biometric identification
- Investigating the impact of technology on mental health and well-being
- Developing algorithms for efficient and accurate language translation
- Investigating the use of machine learning for personalized advertising
- Developing algorithms for efficient and secure payment systems
- Investigating the impact of technology on the job market and automation
- Developing algorithms for efficient and accurate object tracking
- Investigating the use of machine learning for predicting disease outbreaks
- Developing algorithms for efficient and secure access control
- Investigating the impact of technology on human behavior and decision making
- Developing algorithms for efficient and accurate sound recognition
- Investigating the use of machine learning for predicting customer behavior
- Developing algorithms for efficient and secure data backup and recovery
- Investigating the impact of technology on education and learning outcomes
- Developing algorithms for efficient and accurate emotion recognition
- Investigating the use of machine learning for improving healthcare outcomes
- Developing algorithms for efficient and secure supply chain management
- Investigating the impact of technology on cultural and societal norms
- Developing algorithms for efficient and accurate gesture recognition
- Investigating the use of machine learning for predicting consumer demand
- Developing algorithms for efficient and secure cloud storage
- Investigating the impact of technology on environmental sustainability
- Developing algorithms for efficient and accurate voice recognition
- Investigating the use of machine learning for improving transportation systems
- Developing algorithms for efficient and secure mobile device management
- Investigating the impact of technology on social inequality and access to resources
- Machine learning for healthcare diagnosis and treatment
- Machine Learning for Cybersecurity
- Machine learning for personalized medicine
- Cybersecurity threats and defense strategies
- Big data analytics for business intelligence
- Blockchain technology and its applications
- Human-computer interaction in virtual reality environments
- Artificial intelligence for autonomous vehicles
- Natural language processing for chatbots
- Cloud computing and its impact on the IT industry
- Internet of Things (IoT) and smart homes
- Robotics and automation in manufacturing
- Augmented reality and its potential in education
- Data mining techniques for customer relationship management
- Computer vision for object recognition and tracking
- Quantum computing and its applications in cryptography
- Social media analytics and sentiment analysis
- Recommender systems for personalized content delivery
- Mobile computing and its impact on society
- Bioinformatics and genomic data analysis
- Deep learning for image and speech recognition
- Digital signal processing and audio processing algorithms
- Cloud storage and data security in the cloud
- Wearable technology and its impact on healthcare
- Computational linguistics for natural language understanding
- Cognitive computing for decision support systems
- Cyber-physical systems and their applications
- Edge computing and its impact on IoT
- Machine learning for fraud detection
- Cryptography and its role in secure communication
- Cybersecurity risks in the era of the Internet of Things
- Natural language generation for automated report writing
- 3D printing and its impact on manufacturing
- Virtual assistants and their applications in daily life
- Cloud-based gaming and its impact on the gaming industry
- Computer networks and their security issues
- Cyber forensics and its role in criminal investigations
- Machine learning for predictive maintenance in industrial settings
- Augmented reality for cultural heritage preservation
- Human-robot interaction and its applications
- Data visualization and its impact on decision-making
- Cybersecurity in financial systems and blockchain
- Computer graphics and animation techniques
- Biometrics and its role in secure authentication
- Cloud-based e-learning platforms and their impact on education
- Natural language processing for machine translation
- Machine learning for predictive maintenance in healthcare
- Cybersecurity and privacy issues in social media
- Computer vision for medical image analysis
- Natural language generation for content creation
- Cybersecurity challenges in cloud computing
- Human-robot collaboration in manufacturing
- Data mining for predicting customer churn
- Artificial intelligence for autonomous drones
- Cybersecurity risks in the healthcare industry
- Machine learning for speech synthesis
- Edge computing for low-latency applications
- Virtual reality for mental health therapy
- Quantum computing and its applications in finance
- Biomedical engineering and its applications
- Cybersecurity in autonomous systems
- Machine learning for predictive maintenance in transportation
- Computer vision for object detection in autonomous driving
- Augmented reality for industrial training and simulations
- Cloud-based cybersecurity solutions for small businesses
- Natural language processing for knowledge management
- Machine learning for personalized advertising
- Cybersecurity in the supply chain management
- Cybersecurity risks in the energy sector
- Computer vision for facial recognition
- Natural language processing for social media analysis
- Machine learning for sentiment analysis in customer reviews
- Explainable Artificial Intelligence
- Quantum Computing
- Blockchain Technology
- Human-Computer Interaction
- Natural Language Processing
- Cloud Computing
- Robotics and Automation
- Augmented Reality and Virtual Reality
- Cyber-Physical Systems
- Computational Neuroscience
- Big Data Analytics
- Computer Vision
- Cryptography and Network Security
- Internet of Things
- Computer Graphics and Visualization
- Artificial Intelligence for Game Design
- Computational Biology
- Social Network Analysis
- Bioinformatics
- Distributed Systems and Middleware
- Information Retrieval and Data Mining
- Computer Networks
- Mobile Computing and Wireless Networks
- Software Engineering
- Database Systems
- Parallel and Distributed Computing
- Human-Robot Interaction
- Intelligent Transportation Systems
- High-Performance Computing
- Cyber-Physical Security
- Deep Learning
- Sensor Networks
- Multi-Agent Systems
- Human-Centered Computing
- Wearable Computing
- Knowledge Representation and Reasoning
- Adaptive Systems
- Brain-Computer Interface
- Health Informatics
- Cognitive Computing
- Cybersecurity and Privacy
- Internet Security
- Cybercrime and Digital Forensics
- Cloud Security
- Cryptocurrencies and Digital Payments
- Machine Learning for Natural Language Generation
- Cognitive Robotics
- Neural Networks
- Semantic Web
- Image Processing
- Cyber Threat Intelligence
- Secure Mobile Computing
- Cybersecurity Education and Training
- Privacy Preserving Techniques
- Cyber-Physical Systems Security
- Virtualization and Containerization
- Machine Learning for Computer Vision
- Network Function Virtualization
- Cybersecurity Risk Management
- Information Security Governance
- Intrusion Detection and Prevention
- Biometric Authentication
- Machine Learning for Predictive Maintenance
- Security in Cloud-based Environments
- Cybersecurity for Industrial Control Systems
- Smart Grid Security
- Software Defined Networking
- Quantum Cryptography
- Security in the Internet of Things
- Natural language processing for sentiment analysis
- Blockchain technology for secure data sharing
- Developing efficient algorithms for big data analysis
- Cybersecurity for internet of things (IoT) devices
- Human-robot interaction for industrial automation
- Image recognition for autonomous vehicles
- Social media analytics for marketing strategy
- Quantum computing for solving complex problems
- Biometric authentication for secure access control
- Augmented reality for education and training
- Intelligent transportation systems for traffic management
- Predictive modeling for financial markets
- Cloud computing for scalable data storage and processing
- Virtual reality for therapy and mental health treatment
- Data visualization for business intelligence
- Recommender systems for personalized product recommendations
- Speech recognition for voice-controlled devices
- Mobile computing for real-time location-based services
- Neural networks for predicting user behavior
- Genetic algorithms for optimization problems
- Distributed computing for parallel processing
- Internet of things (IoT) for smart cities
- Wireless sensor networks for environmental monitoring
- Cloud-based gaming for high-performance gaming
- Social network analysis for identifying influencers
- Autonomous systems for agriculture
- Robotics for disaster response
- Data mining for customer segmentation
- Computer graphics for visual effects in movies and video games
- Virtual assistants for personalized customer service
- Natural language understanding for chatbots
- 3D printing for manufacturing prototypes
- Artificial intelligence for stock trading
- Machine learning for weather forecasting
- Biomedical engineering for prosthetics and implants
- Cybersecurity for financial institutions
- Machine learning for energy consumption optimization
- Computer vision for object tracking
- Natural language processing for document summarization
- Wearable technology for health and fitness monitoring
- Internet of things (IoT) for home automation
- Reinforcement learning for robotics control
- Big data analytics for customer insights
- Machine learning for supply chain optimization
- Natural language processing for legal document analysis
- Artificial intelligence for drug discovery
- Computer vision for object recognition in robotics
- Data mining for customer churn prediction
- Autonomous systems for space exploration
- Robotics for agriculture automation
- Machine learning for predicting earthquakes
- Natural language processing for sentiment analysis in customer reviews
- Big data analytics for predicting natural disasters
- Internet of things (IoT) for remote patient monitoring
- Blockchain technology for digital identity management
- Machine learning for predicting wildfire spread
- Computer vision for gesture recognition
- Natural language processing for automated translation
- Big data analytics for fraud detection in banking
- Internet of things (IoT) for smart homes
- Robotics for warehouse automation
- Machine learning for predicting air pollution
- Natural language processing for medical record analysis
- Augmented reality for architectural design
- Big data analytics for predicting traffic congestion
- Machine learning for predicting customer lifetime value
- Developing algorithms for efficient and accurate text recognition
- Natural Language Processing for Virtual Assistants
- Natural Language Processing for Sentiment Analysis in Social Media
- Explainable Artificial Intelligence (XAI) for Trust and Transparency
- Deep Learning for Image and Video Retrieval
- Edge Computing for Internet of Things (IoT) Applications
- Data Science for Social Media Analytics
- Cybersecurity for Critical Infrastructure Protection
- Natural Language Processing for Text Classification
- Quantum Computing for Optimization Problems
- Machine Learning for Personalized Health Monitoring
- Computer Vision for Autonomous Driving
- Blockchain Technology for Supply Chain Management
- Augmented Reality for Education and Training
- Natural Language Processing for Sentiment Analysis
- Machine Learning for Personalized Marketing
- Big Data Analytics for Financial Fraud Detection
- Cybersecurity for Cloud Security Assessment
- Artificial Intelligence for Natural Language Understanding
- Blockchain Technology for Decentralized Applications
- Virtual Reality for Cultural Heritage Preservation
- Natural Language Processing for Named Entity Recognition
- Machine Learning for Customer Churn Prediction
- Big Data Analytics for Social Network Analysis
- Cybersecurity for Intrusion Detection and Prevention
- Artificial Intelligence for Robotics and Automation
- Blockchain Technology for Digital Identity Management
- Virtual Reality for Rehabilitation and Therapy
- Natural Language Processing for Text Summarization
- Machine Learning for Credit Risk Assessment
- Big Data Analytics for Fraud Detection in Healthcare
- Cybersecurity for Internet Privacy Protection
- Artificial Intelligence for Game Design and Development
- Blockchain Technology for Decentralized Social Networks
- Virtual Reality for Marketing and Advertising
- Natural Language Processing for Opinion Mining
- Machine Learning for Anomaly Detection
- Big Data Analytics for Predictive Maintenance in Transportation
- Cybersecurity for Network Security Management
- Artificial Intelligence for Personalized News and Content Delivery
- Blockchain Technology for Cryptocurrency Mining
- Virtual Reality for Architectural Design and Visualization
- Natural Language Processing for Machine Translation
- Machine Learning for Automated Image Captioning
- Big Data Analytics for Stock Market Prediction
- Cybersecurity for Biometric Authentication Systems
- Artificial Intelligence for Human-Robot Interaction
- Blockchain Technology for Smart Grids
- Virtual Reality for Sports Training and Simulation
- Natural Language Processing for Question Answering Systems
- Machine Learning for Sentiment Analysis in Customer Feedback
- Big Data Analytics for Predictive Maintenance in Manufacturing
- Cybersecurity for Cloud-Based Systems
- Artificial Intelligence for Automated Journalism
- Blockchain Technology for Intellectual Property Management
- Virtual Reality for Therapy and Rehabilitation
- Natural Language Processing for Language Generation
- Machine Learning for Customer Lifetime Value Prediction
- Big Data Analytics for Predictive Maintenance in Energy Systems
- Cybersecurity for Secure Mobile Communication
- Artificial Intelligence for Emotion Recognition
- Blockchain Technology for Digital Asset Trading
- Virtual Reality for Automotive Design and Visualization
- Natural Language Processing for Semantic Web
- Machine Learning for Fraud Detection in Financial Transactions
- Big Data Analytics for Social Media Monitoring
- Cybersecurity for Cloud Storage and Sharing
- Artificial Intelligence for Personalized Education
- Blockchain Technology for Secure Online Voting Systems
- Virtual Reality for Cultural Tourism
- Natural Language Processing for Chatbot Communication
- Machine Learning for Medical Diagnosis and Treatment
- Big Data Analytics for Environmental Monitoring and Management.
- Cybersecurity for Cloud Computing Environments
- Virtual Reality for Training and Simulation
- Big Data Analytics for Sports Performance Analysis
- Cybersecurity for Internet of Things (IoT) Devices
- Artificial Intelligence for Traffic Management and Control
- Blockchain Technology for Smart Contracts
- Natural Language Processing for Document Summarization
- Machine Learning for Image and Video Recognition
- Blockchain Technology for Digital Asset Management
- Virtual Reality for Entertainment and Gaming
- Natural Language Processing for Opinion Mining in Online Reviews
- Machine Learning for Customer Relationship Management
- Big Data Analytics for Environmental Monitoring and Management
- Cybersecurity for Network Traffic Analysis and Monitoring
- Artificial Intelligence for Natural Language Generation
- Blockchain Technology for Supply Chain Transparency and Traceability
- Virtual Reality for Design and Visualization
- Natural Language Processing for Speech Recognition
- Machine Learning for Recommendation Systems
- Big Data Analytics for Customer Segmentation and Targeting
- Cybersecurity for Biometric Authentication
- Artificial Intelligence for Human-Computer Interaction
- Blockchain Technology for Decentralized Finance (DeFi)
- Virtual Reality for Tourism and Cultural Heritage
- Machine Learning for Cybersecurity Threat Detection and Prevention
- Big Data Analytics for Healthcare Cost Reduction
- Cybersecurity for Data Privacy and Protection
- Artificial Intelligence for Autonomous Vehicles
- Blockchain Technology for Cryptocurrency and Blockchain Security
- Virtual Reality for Real Estate Visualization
- Natural Language Processing for Question Answering
- Big Data Analytics for Financial Markets Prediction
- Cybersecurity for Cloud-Based Machine Learning Systems
- Artificial Intelligence for Personalized Advertising
- Blockchain Technology for Digital Identity Verification
- Virtual Reality for Cultural and Language Learning
- Natural Language Processing for Semantic Analysis
- Machine Learning for Business Forecasting
- Big Data Analytics for Social Media Marketing
- Artificial Intelligence for Content Generation
- Blockchain Technology for Smart Cities
- Virtual Reality for Historical Reconstruction
- Natural Language Processing for Knowledge Graph Construction
- Machine Learning for Speech Synthesis
- Big Data Analytics for Traffic Optimization
- Artificial Intelligence for Social Robotics
- Blockchain Technology for Healthcare Data Management
- Virtual Reality for Disaster Preparedness and Response
- Natural Language Processing for Multilingual Communication
- Machine Learning for Emotion Recognition
- Big Data Analytics for Human Resources Management
- Cybersecurity for Mobile App Security
- Artificial Intelligence for Financial Planning and Investment
- Blockchain Technology for Energy Management
- Virtual Reality for Cultural Preservation and Heritage.
- Big Data Analytics for Healthcare Management
- Cybersecurity in the Internet of Things (IoT)
- Artificial Intelligence for Predictive Maintenance
- Computational Biology for Drug Discovery
- Virtual Reality for Mental Health Treatment
- Machine Learning for Sentiment Analysis in Social Media
- Human-Computer Interaction for User Experience Design
- Cloud Computing for Disaster Recovery
- Quantum Computing for Cryptography
- Intelligent Transportation Systems for Smart Cities
- Cybersecurity for Autonomous Vehicles
- Artificial Intelligence for Fraud Detection in Financial Systems
- Social Network Analysis for Marketing Campaigns
- Cloud Computing for Video Game Streaming
- Machine Learning for Speech Recognition
- Augmented Reality for Architecture and Design
- Natural Language Processing for Customer Service Chatbots
- Machine Learning for Climate Change Prediction
- Big Data Analytics for Social Sciences
- Artificial Intelligence for Energy Management
- Virtual Reality for Tourism and Travel
- Cybersecurity for Smart Grids
- Machine Learning for Image Recognition
- Augmented Reality for Sports Training
- Natural Language Processing for Content Creation
- Cloud Computing for High-Performance Computing
- Artificial Intelligence for Personalized Medicine
- Virtual Reality for Architecture and Design
- Augmented Reality for Product Visualization
- Natural Language Processing for Language Translation
- Cybersecurity for Cloud Computing
- Artificial Intelligence for Supply Chain Optimization
- Blockchain Technology for Digital Voting Systems
- Virtual Reality for Job Training
- Augmented Reality for Retail Shopping
- Natural Language Processing for Sentiment Analysis in Customer Feedback
- Cloud Computing for Mobile Application Development
- Artificial Intelligence for Cybersecurity Threat Detection
- Blockchain Technology for Intellectual Property Protection
- Virtual Reality for Music Education
- Machine Learning for Financial Forecasting
- Augmented Reality for Medical Education
- Natural Language Processing for News Summarization
- Cybersecurity for Healthcare Data Protection
- Artificial Intelligence for Autonomous Robots
- Virtual Reality for Fitness and Health
- Machine Learning for Natural Language Understanding
- Augmented Reality for Museum Exhibits
- Natural Language Processing for Chatbot Personality Development
- Cloud Computing for Website Performance Optimization
- Artificial Intelligence for E-commerce Recommendation Systems
- Blockchain Technology for Supply Chain Traceability
- Virtual Reality for Military Training
- Augmented Reality for Advertising
- Natural Language Processing for Chatbot Conversation Management
- Cybersecurity for Cloud-Based Services
- Artificial Intelligence for Agricultural Management
- Blockchain Technology for Food Safety Assurance
- Virtual Reality for Historical Reenactments
- Machine Learning for Cybersecurity Incident Response.
- Secure Multiparty Computation
- Federated Learning
- Internet of Things Security
- Blockchain Scalability
- Quantum Computing Algorithms
- Explainable AI
- Data Privacy in the Age of Big Data
- Adversarial Machine Learning
- Deep Reinforcement Learning
- Online Learning and Streaming Algorithms
- Graph Neural Networks
- Automated Debugging and Fault Localization
- Mobile Application Development
- Software Engineering for Cloud Computing
- Cryptocurrency Security
- Edge Computing for Real-Time Applications
- Natural Language Generation
- Virtual and Augmented Reality
- Computational Biology and Bioinformatics
- Internet of Things Applications
- Robotics and Autonomous Systems
- Explainable Robotics
- 3D Printing and Additive Manufacturing
- Distributed Systems
- Parallel Computing
- Data Center Networking
- Data Mining and Knowledge Discovery
- Information Retrieval and Search Engines
- Network Security and Privacy
- Cloud Computing Security
- Data Analytics for Business Intelligence
- Neural Networks and Deep Learning
- Reinforcement Learning for Robotics
- Automated Planning and Scheduling
- Evolutionary Computation and Genetic Algorithms
- Formal Methods for Software Engineering
- Computational Complexity Theory
- Bio-inspired Computing
- Computer Vision for Object Recognition
- Automated Reasoning and Theorem Proving
- Natural Language Understanding
- Machine Learning for Healthcare
- Scalable Distributed Systems
- Sensor Networks and Internet of Things
- Smart Grids and Energy Systems
- Software Testing and Verification
- Web Application Security
- Wireless and Mobile Networks
- Computer Architecture and Hardware Design
- Digital Signal Processing
- Game Theory and Mechanism Design
- Multi-agent Systems
- Evolutionary Robotics
- Quantum Machine Learning
- Computational Social Science
- Explainable Recommender Systems.
- Artificial Intelligence and its applications
- Cloud computing and its benefits
- Cybersecurity threats and solutions
- Internet of Things and its impact on society
- Virtual and Augmented Reality and its uses
- Blockchain Technology and its potential in various industries
- Web Development and Design
- Digital Marketing and its effectiveness
- Big Data and Analytics
- Software Development Life Cycle
- Gaming Development and its growth
- Network Administration and Maintenance
- Machine Learning and its uses
- Data Warehousing and Mining
- Computer Architecture and Design
- Computer Graphics and Animation
- Quantum Computing and its potential
- Data Structures and Algorithms
- Computer Vision and Image Processing
- Robotics and its applications
- Operating Systems and its functions
- Information Theory and Coding
- Compiler Design and Optimization
- Computer Forensics and Cyber Crime Investigation
- Distributed Computing and its significance
- Artificial Neural Networks and Deep Learning
- Cloud Storage and Backup
- Programming Languages and their significance
- Computer Simulation and Modeling
- Computer Networks and its types
- Information Security and its types
- Computer-based Training and eLearning
- Medical Imaging and its uses
- Social Media Analysis and its applications
- Human Resource Information Systems
- Computer-Aided Design and Manufacturing
- Multimedia Systems and Applications
- Geographic Information Systems and its uses
- Computer-Assisted Language Learning
- Mobile Device Management and Security
- Data Compression and its types
- Knowledge Management Systems
- Text Mining and its uses
- Cyber Warfare and its consequences
- Wireless Networks and its advantages
- Computer Ethics and its importance
- Computational Linguistics and its applications
- Autonomous Systems and Robotics
- Information Visualization and its importance
- Geographic Information Retrieval and Mapping
- Business Intelligence and its benefits
- Digital Libraries and their significance
- Artificial Life and Evolutionary Computation
- Computer Music and its types
- Virtual Teams and Collaboration
- Computer Games and Learning
- Semantic Web and its applications
- Electronic Commerce and its advantages
- Multimedia Databases and their significance
- Computer Science Education and its importance
- Computer-Assisted Translation and Interpretation
- Ambient Intelligence and Smart Homes
- Autonomous Agents and Multi-Agent Systems.
About the author
Muhammad Hassan
Researcher, Academic Writer, Web developer
You may also like

200+ Funny Research Topics

500+ Sports Research Topics

300+ American History Research Paper Topics

500+ Cyber Security Research Topics

500+ Environmental Research Topics

500+ Economics Research Topics
Research Topics & Ideas: CompSci & IT
50+ Computer Science Research Topic Ideas To Fast-Track Your Project

Finding and choosing a strong research topic is the critical first step when it comes to crafting a high-quality dissertation, thesis or research project. If you’ve landed on this post, chances are you’re looking for a computer science-related research topic , but aren’t sure where to start. Here, we’ll explore a variety of CompSci & IT-related research ideas and topic thought-starters, including algorithms, AI, networking, database systems, UX, information security and software engineering.
NB – This is just the start…
The topic ideation and evaluation process has multiple steps . In this post, we’ll kickstart the process by sharing some research topic ideas within the CompSci domain. This is the starting point, but to develop a well-defined research topic, you’ll need to identify a clear and convincing research gap , along with a well-justified plan of action to fill that gap.
If you’re new to the oftentimes perplexing world of research, or if this is your first time undertaking a formal academic research project, be sure to check out our free dissertation mini-course. In it, we cover the process of writing a dissertation or thesis from start to end. Be sure to also sign up for our free webinar that explores how to find a high-quality research topic.
Overview: CompSci Research Topics
- Algorithms & data structures
- Artificial intelligence ( AI )
- Computer networking
- Database systems
- Human-computer interaction
- Information security (IS)
- Software engineering
- Examples of CompSci dissertation & theses
Topics/Ideas: Algorithms & Data Structures
- An analysis of neural network algorithms’ accuracy for processing consumer purchase patterns
- A systematic review of the impact of graph algorithms on data analysis and discovery in social media network analysis
- An evaluation of machine learning algorithms used for recommender systems in streaming services
- A review of approximation algorithm approaches for solving NP-hard problems
- An analysis of parallel algorithms for high-performance computing of genomic data
- The influence of data structures on optimal algorithm design and performance in Fintech
- A Survey of algorithms applied in internet of things (IoT) systems in supply-chain management
- A comparison of streaming algorithm performance for the detection of elephant flows
- A systematic review and evaluation of machine learning algorithms used in facial pattern recognition
- Exploring the performance of a decision tree-based approach for optimizing stock purchase decisions
- Assessing the importance of complete and representative training datasets in Agricultural machine learning based decision making.
- A Comparison of Deep learning algorithms performance for structured and unstructured datasets with “rare cases”
- A systematic review of noise reduction best practices for machine learning algorithms in geoinformatics.
- Exploring the feasibility of applying information theory to feature extraction in retail datasets.
- Assessing the use case of neural network algorithms for image analysis in biodiversity assessment
Topics & Ideas: Artificial Intelligence (AI)
- Applying deep learning algorithms for speech recognition in speech-impaired children
- A review of the impact of artificial intelligence on decision-making processes in stock valuation
- An evaluation of reinforcement learning algorithms used in the production of video games
- An exploration of key developments in natural language processing and how they impacted the evolution of Chabots.
- An analysis of the ethical and social implications of artificial intelligence-based automated marking
- The influence of large-scale GIS datasets on artificial intelligence and machine learning developments
- An examination of the use of artificial intelligence in orthopaedic surgery
- The impact of explainable artificial intelligence (XAI) on transparency and trust in supply chain management
- An evaluation of the role of artificial intelligence in financial forecasting and risk management in cryptocurrency
- A meta-analysis of deep learning algorithm performance in predicting and cyber attacks in schools

Topics & Ideas: Networking
- An analysis of the impact of 5G technology on internet penetration in rural Tanzania
- Assessing the role of software-defined networking (SDN) in modern cloud-based computing
- A critical analysis of network security and privacy concerns associated with Industry 4.0 investment in healthcare.
- Exploring the influence of cloud computing on security risks in fintech.
- An examination of the use of network function virtualization (NFV) in telecom networks in Southern America
- Assessing the impact of edge computing on network architecture and design in IoT-based manufacturing
- An evaluation of the challenges and opportunities in 6G wireless network adoption
- The role of network congestion control algorithms in improving network performance on streaming platforms
- An analysis of network coding-based approaches for data security
- Assessing the impact of network topology on network performance and reliability in IoT-based workspaces

Topics & Ideas: Database Systems
- An analysis of big data management systems and technologies used in B2B marketing
- The impact of NoSQL databases on data management and analysis in smart cities
- An evaluation of the security and privacy concerns of cloud-based databases in financial organisations
- Exploring the role of data warehousing and business intelligence in global consultancies
- An analysis of the use of graph databases for data modelling and analysis in recommendation systems
- The influence of the Internet of Things (IoT) on database design and management in the retail grocery industry
- An examination of the challenges and opportunities of distributed databases in supply chain management
- Assessing the impact of data compression algorithms on database performance and scalability in cloud computing
- An evaluation of the use of in-memory databases for real-time data processing in patient monitoring
- Comparing the effects of database tuning and optimization approaches in improving database performance and efficiency in omnichannel retailing
Topics & Ideas: Human-Computer Interaction
- An analysis of the impact of mobile technology on human-computer interaction prevalence in adolescent men
- An exploration of how artificial intelligence is changing human-computer interaction patterns in children
- An evaluation of the usability and accessibility of web-based systems for CRM in the fast fashion retail sector
- Assessing the influence of virtual and augmented reality on consumer purchasing patterns
- An examination of the use of gesture-based interfaces in architecture
- Exploring the impact of ease of use in wearable technology on geriatric user
- Evaluating the ramifications of gamification in the Metaverse
- A systematic review of user experience (UX) design advances associated with Augmented Reality
- A comparison of natural language processing algorithms automation of customer response Comparing end-user perceptions of natural language processing algorithms for automated customer response
- Analysing the impact of voice-based interfaces on purchase practices in the fast food industry

Topics & Ideas: Information Security
- A bibliometric review of current trends in cryptography for secure communication
- An analysis of secure multi-party computation protocols and their applications in cloud-based computing
- An investigation of the security of blockchain technology in patient health record tracking
- A comparative study of symmetric and asymmetric encryption algorithms for instant text messaging
- A systematic review of secure data storage solutions used for cloud computing in the fintech industry
- An analysis of intrusion detection and prevention systems used in the healthcare sector
- Assessing security best practices for IoT devices in political offices
- An investigation into the role social media played in shifting regulations related to privacy and the protection of personal data
- A comparative study of digital signature schemes adoption in property transfers
- An assessment of the security of secure wireless communication systems used in tertiary institutions
Topics & Ideas: Software Engineering
- A study of agile software development methodologies and their impact on project success in pharmacology
- Investigating the impacts of software refactoring techniques and tools in blockchain-based developments
- A study of the impact of DevOps practices on software development and delivery in the healthcare sector
- An analysis of software architecture patterns and their impact on the maintainability and scalability of cloud-based offerings
- A study of the impact of artificial intelligence and machine learning on software engineering practices in the education sector
- An investigation of software testing techniques and methodologies for subscription-based offerings
- A review of software security practices and techniques for protecting against phishing attacks from social media
- An analysis of the impact of cloud computing on the rate of software development and deployment in the manufacturing sector
- Exploring the impact of software development outsourcing on project success in multinational contexts
- An investigation into the effect of poor software documentation on app success in the retail sector
CompSci & IT Dissertations/Theses
While the ideas we’ve presented above are a decent starting point for finding a CompSci-related research topic, they are fairly generic and non-specific. So, it helps to look at actual dissertations and theses to see how this all comes together.
Below, we’ve included a selection of research projects from various CompSci-related degree programs to help refine your thinking. These are actual dissertations and theses, written as part of Master’s and PhD-level programs, so they can provide some useful insight as to what a research topic looks like in practice.
- An array-based optimization framework for query processing and data analytics (Chen, 2021)
- Dynamic Object Partitioning and replication for cooperative cache (Asad, 2021)
- Embedding constructural documentation in unit tests (Nassif, 2019)
- PLASA | Programming Language for Synchronous Agents (Kilaru, 2019)
- Healthcare Data Authentication using Deep Neural Network (Sekar, 2020)
- Virtual Reality System for Planetary Surface Visualization and Analysis (Quach, 2019)
- Artificial neural networks to predict share prices on the Johannesburg stock exchange (Pyon, 2021)
- Predicting household poverty with machine learning methods: the case of Malawi (Chinyama, 2022)
- Investigating user experience and bias mitigation of the multi-modal retrieval of historical data (Singh, 2021)
- Detection of HTTPS malware traffic without decryption (Nyathi, 2022)
- Redefining privacy: case study of smart health applications (Al-Zyoud, 2019)
- A state-based approach to context modeling and computing (Yue, 2019)
- A Novel Cooperative Intrusion Detection System for Mobile Ad Hoc Networks (Solomon, 2019)
- HRSB-Tree for Spatio-Temporal Aggregates over Moving Regions (Paduri, 2019)
Looking at these titles, you can probably pick up that the research topics here are quite specific and narrowly-focused , compared to the generic ones presented earlier. This is an important thing to keep in mind as you develop your own research topic. That is to say, to create a top-notch research topic, you must be precise and target a specific context with specific variables of interest . In other words, you need to identify a clear, well-justified research gap.
Fast-Track Your Research Topic
If you’re still feeling a bit unsure about how to find a research topic for your Computer Science dissertation or research project, check out our Topic Kickstarter service.
You Might Also Like:

Investigating the impacts of software refactoring techniques and tools in blockchain-based developments.
Steps on getting this project topic
I want to work with this topic, am requesting materials to guide.
Information Technology -MSc program
It’s really interesting but how can I have access to the materials to guide me through my work?
That’s my problem also.
Investigating the impacts of software refactoring techniques and tools in blockchain-based developments is in my favour. May i get the proper material about that ?
BLOCKCHAIN TECHNOLOGY
I NEED TOPIC
Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Print Friendly
Topics in Networking Research
- Conference paper
- Cite this conference paper

- Debasis Mitra 1
Part of the book series: Lecture Notes in Computer Science ((LNCCN,volume 4516))
Included in the following conference series:
- International Teletraffic Congress
1404 Accesses
What are the big movements in networking that researchers should heed? A standout is the global spread of communities of interest (the networking analogue of the flat world) and their need for “dynamic virtual networks” that support rich applications requiring resources from several domains. The imperative for inter-networking, i.e., the enablement of coordinated sharing of resources across multiple domains, is certain. This challenge has many facets, ranging from the organizational, e.g., different, possibly competing, owners to the technical, e.g., different technologies. Yet another key characteristic of the emerging networking environment is that the service provider is required to handle ever-increasing uncertainty in demand, both in volume and time. On the other hand there are new instruments available to handle the challenge. Thus, inter-networking and uncertainty management are important challenges of emerging networking that deserve attention from the research community.
We describe research that touch on both topics. First, we consider a model of data-optical inter-networking, where routes connecting end-points in data domains are concatenation of segments in the data and optical domains. The optical domain in effect acts as a carrier’s carrier for multiple data domains. The challenge to inter-networking stems from the limited view that the data and optical domains have of each other. Coordination has to be enabled through parsimonious and qualitatively restrictive information exchange across domains. Yet the overall optimization objective, which is to maximize end-to-end carried traffic with minimum lightpath provisioning cost, enmeshes data and optical domains. This example of inter-networking also involves two technologies. A mathematical reflection of the latter fact is the integrality of some of the decision variables due to wavelengths being the bandwidth unit in optical transmission. Through an application of Generalized Bender’s Decomposition the problem of optimizing provisioning and routing is decomposed into sub-problems, which are solved by the different domains and the results exchanged in iterations that provably converge to the global optimum.
In turning to uncertainty management we begin by presenting a framework for stochastic traffic management. Traffic demands are uncertain and given by probability distributions. While there are alternative perspectives (and metrics) to resource usage, such as social welfare and network revenue, we adopt the latter, which is aligned with the service provider’s interests. Uncertainty introduces the risk of misallocation of resources. What is the right measure of risk in networking? We examine various definitions of risk, some taken from modern portfolio theory, and suggest a balanced solution. Next we consider the optimization of an objective which is a risk-adjusted measure of network revenue. We obtain conditions under which the optimization problem is an instance of convex programming. Studies of the properties of the solution show that it asymptotically meets the stochastic efficiency criterion. Service providers’ risk mitigation policies are suggested. For instance, by selecting the appropriate mix of long-term contracts and opportunistic servicing of random demand, the service provider can optimize its risk-adjusted revenue. The “efficient frontier”, which is the set of Pareto optimal pairs of mean revenue and revenue risk, is useful to the service provider in selecting its operating point.
Joint work with Qiong Wang and Anwar Walid, Bell Labs, Murray Hill.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
Author information
Authors and affiliations.
Bell Labs, Alcatel-Lucent, Murray Hill, NJ 07974, USA
Debasis Mitra
You can also search for this author in PubMed Google Scholar
Editor information
Rights and permissions.
Reprints and permissions
Copyright information
© 2007 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper.
Mitra, D. (2007). Topics in Networking Research. In: Mason, L., Drwiega, T., Yan, J. (eds) Managing Traffic Performance in Converged Networks. ITC 2007. Lecture Notes in Computer Science, vol 4516. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-540-72990-7_3
Download citation
DOI : https://doi.org/10.1007/978-3-540-72990-7_3
Publisher Name : Springer, Berlin, Heidelberg
Print ISBN : 978-3-540-72989-1
Online ISBN : 978-3-540-72990-7
eBook Packages : Computer Science Computer Science (R0)
Share this paper
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research

- Advisers & Contacts
- Bachelor of Arts & Bachelor of Science in Engineering
- Prerequisites
- Declaring Computer Science for AB Students
- Declaring Computer Science for BSE Students
- Class of '25, '26 & '27 - Departmental Requirements
- Class of 2024 - Departmental Requirements
- COS126 Information
- Important Steps and Deadlines
- Independent Work Seminars
- Guidelines and Useful Information
Undergraduate Research Topics
- AB Junior Research Workshops
- Undergraduate Program FAQ
- How to Enroll
- Requirements
- Certificate Program FAQ
- Interdepartmental Committee
- Minor Program
- Funding for Student Group Activities
- Mailing Lists and Policies
- Study Abroad
- Jobs & Careers
- Admissions Requirements
- Breadth Requirements
- Pre-FPO Checklist
- FPO Checklist
- M.S.E. Track
- M.Eng. Track
- Departmental Internship Policy (for Master's students)
- General Examination
- Fellowship Opportunities
- Travel Reimbursement Policy
- Communication Skills
- Course Schedule
- Course Catalog
- Research Areas
- Interdisciplinary Programs
- Technical Reports
- Computing Facilities
- Researchers
- Technical Staff
- Administrative Staff
- Graduate Students
- Undergraduate Students
- Graduate Alumni
- Climate and Inclusion Committee
- Resources for Undergraduate & Graduate Students
- Outreach Initiatives
- Resources for Faculty & Staff
- Spotlight Stories
- Job Openings
- Undergraduate Program
- Independent Work & Theses
Suggested Undergraduate Research Topics

How to Contact Faculty for IW/Thesis Advising
Send the professor an e-mail. When you write a professor, be clear that you want a meeting regarding a senior thesis or one-on-one IW project, and briefly describe the topic or idea that you want to work on. Check the faculty listing for email addresses.
Parastoo Abtahi, Room 419
Available for single-semester IW and senior thesis advising, 2024-2025
- Research Areas: Human-Computer Interaction (HCI), Augmented Reality (AR), and Spatial Computing
- Input techniques for on-the-go interaction (e.g., eye-gaze, microgestures, voice) with a focus on uncertainty, disambiguation, and privacy.
- Minimal and timely multisensory output (e.g., spatial audio, haptics) that enables users to attend to their physical environment and the people around them, instead of a 2D screen.
- Interaction with intelligent systems (e.g., IoT, robots) situated in physical spaces with a focus on updating users’ mental model despite the complexity and dynamicity of these systems.
Ryan Adams, Room 411
Research areas:
- Machine learning driven design
- Generative models for structured discrete objects
- Approximate inference in probabilistic models
- Accelerating solutions to partial differential equations
- Innovative uses of automatic differentiation
- Modeling and optimizing 3d printing and CNC machining
Andrew Appel, Room 209
Available for Fall 2024 IW advising, only
- Research Areas: Formal methods, programming languages, compilers, computer security.
- Software verification (for which taking COS 326 / COS 510 is helpful preparation)
- Game theory of poker or other games (for which COS 217 / 226 are helpful)
- Computer game-playing programs (for which COS 217 / 226)
- Risk-limiting audits of elections (for which ORF 245 or other knowledge of probability is useful)
Sanjeev Arora, Room 407
- Theoretical machine learning, deep learning and its analysis, natural language processing. My advisees would typically have taken a course in algorithms (COS423 or COS 521 or equivalent) and a course in machine learning.
- Show that finding approximate solutions to NP-complete problems is also NP-complete (i.e., come up with NP-completeness reductions a la COS 487).
- Experimental Algorithms: Implementing and Evaluating Algorithms using existing software packages.
- Studying/designing provable algorithms for machine learning and implementions using packages like scipy and MATLAB, including applications in Natural language processing and deep learning.
- Any topic in theoretical computer science.
David August, Room 221
Not available for IW or thesis advising, 2024-2025
- Research Areas: Computer Architecture, Compilers, Parallelism
- Containment-based approaches to security: We have designed and tested a simple hardware+software containment mechanism that stops incorrect communication resulting from faults, bugs, or exploits from leaving the system. Let's explore ways to use containment to solve real problems. Expect to work with corporate security and technology decision-makers.
- Parallelism: Studies show much more parallelism than is currently realized in compilers and architectures. Let's find ways to realize this parallelism.
- Any other interesting topic in computer architecture or compilers.
Mark Braverman, 194 Nassau St., Room 231
- Research Areas: computational complexity, algorithms, applied probability, computability over the real numbers, game theory and mechanism design, information theory.
- Topics in computational and communication complexity.
- Applications of information theory in complexity theory.
- Algorithms for problems under real-life assumptions.
- Game theory, network effects
- Mechanism design (could be on a problem proposed by the student)
Sebastian Caldas, 221 Nassau Street, Room 105
- Research Areas: collaborative learning, machine learning for healthcare. Typically, I will work with students that have taken COS324.
- Methods for collaborative and continual learning.
- Machine learning for healthcare applications.
Bernard Chazelle, 194 Nassau St., Room 301
- Research Areas: Natural Algorithms, Computational Geometry, Sublinear Algorithms.
- Natural algorithms (flocking, swarming, social networks, etc).
- Sublinear algorithms
- Self-improving algorithms
- Markov data structures
Danqi Chen, Room 412
- My advisees would be expected to have taken a course in machine learning and ideally have taken COS484 or an NLP graduate seminar.
- Representation learning for text and knowledge bases
- Pre-training and transfer learning
- Question answering and reading comprehension
- Information extraction
- Text summarization
- Any other interesting topics related to natural language understanding/generation
Marcel Dall'Agnol, Corwin 034
- Research Areas: Theoretical computer science. (Specifically, quantum computation, sublinear algorithms, complexity theory, interactive proofs and cryptography)
- Research Areas: Machine learning
Jia Deng, Room 423
- Research Areas: Computer Vision, Machine Learning.
- Object recognition and action recognition
- Deep Learning, autoML, meta-learning
- Geometric reasoning, logical reasoning
Adji Bousso Dieng, Room 406
- Research areas: Vertaix is a research lab at Princeton University led by Professor Adji Bousso Dieng. We work at the intersection of artificial intelligence (AI) and the natural sciences. The models and algorithms we develop are motivated by problems in those domains and contribute to advancing methodological research in AI. We leverage tools in statistical machine learning and deep learning in developing methods for learning with the data, of various modalities, arising from the natural sciences.
Robert Dondero, Corwin Hall, Room 038
- Research Areas: Software engineering; software engineering education.
- Develop or evaluate tools to facilitate student learning in undergraduate computer science courses at Princeton, and beyond.
- In particular, can code critiquing tools help students learn about software quality?
Zeev Dvir, 194 Nassau St., Room 250
- Research Areas: computational complexity, pseudo-randomness, coding theory and discrete mathematics.
- Independent Research: I have various research problems related to Pseudorandomness, Coding theory, Complexity and Discrete mathematics - all of which require strong mathematical background. A project could also be based on writing a survey paper describing results from a few theory papers revolving around some particular subject.
Benjamin Eysenbach, Room 416
- Research areas: reinforcement learning, machine learning. My advisees would typically have taken COS324.
- Using RL algorithms to applications in science and engineering.
- Emergent behavior of RL algorithms on high-fidelity robotic simulators.
- Studying how architectures and representations can facilitate generalization.
Christiane Fellbaum, 1-S-14 Green
- Research Areas: theoretical and computational linguistics, word sense disambiguation, lexical resource construction, English and multilingual WordNet(s), ontology
- Anything having to do with natural language--come and see me with/for ideas suitable to your background and interests. Some topics students have worked on in the past:
- Developing parsers, part-of-speech taggers, morphological analyzers for underrepresented languages (you don't have to know the language to develop such tools!)
- Quantitative approaches to theoretical linguistics questions
- Extensions and interfaces for WordNet (English and WN in other languages),
- Applications of WordNet(s), including:
- Foreign language tutoring systems,
- Spelling correction software,
- Word-finding/suggestion software for ordinary users and people with memory problems,
- Machine Translation
- Sentiment and Opinion detection
- Automatic reasoning and inferencing
- Collaboration with professors in the social sciences and humanities ("Digital Humanities")
Adam Finkelstein, Room 424
- Research Areas: computer graphics, audio.
Robert S. Fish, Corwin Hall, Room 037
- Networking and telecommunications
- Learning, perception, and intelligence, artificial and otherwise;
- Human-computer interaction and computer-supported cooperative work
- Online education, especially in Computer Science Education
- Topics in research and development innovation methodologies including standards, open-source, and entrepreneurship
- Distributed autonomous organizations and related blockchain technologies
Michael Freedman, Room 308
- Research Areas: Distributed systems, security, networking
- Projects related to streaming data analysis, datacenter systems and networks, untrusted cloud storage and applications. Please see my group website at http://sns.cs.princeton.edu/ for current research projects.
Ruth Fong, Room 032
- Research Areas: computer vision, machine learning, deep learning, interpretability, explainable AI, fairness and bias in AI
- Develop a technique for understanding AI models
- Design a AI model that is interpretable by design
- Build a paradigm for detecting and/or correcting failure points in an AI model
- Analyze an existing AI model and/or dataset to better understand its failure points
- Build a computer vision system for another domain (e.g., medical imaging, satellite data, etc.)
- Develop a software package for explainable AI
- Adapt explainable AI research to a consumer-facing problem
Note: I am happy to advise any project if there's a sufficient overlap in interest and/or expertise; please reach out via email to chat about project ideas.
Tom Griffiths, Room 405
Available for Fall 2024 single-semester IW advising, only
Research areas: computational cognitive science, computational social science, machine learning and artificial intelligence
Note: I am open to projects that apply ideas from computer science to understanding aspects of human cognition in a wide range of areas, from decision-making to cultural evolution and everything in between. For example, we have current projects analyzing chess game data and magic tricks, both of which give us clues about how human minds work. Students who have expertise or access to data related to games, magic, strategic sports like fencing, or other quantifiable domains of human behavior feel free to get in touch.
Aarti Gupta, Room 220
- Research Areas: Formal methods, program analysis, logic decision procedures
- Finding bugs in open source software using automatic verification tools
- Software verification (program analysis, model checking, test generation)
- Decision procedures for logical reasoning (SAT solvers, SMT solvers)
Elad Hazan, Room 409
- Research interests: machine learning methods and algorithms, efficient methods for mathematical optimization, regret minimization in games, reinforcement learning, control theory and practice
- Machine learning, efficient methods for mathematical optimization, statistical and computational learning theory, regret minimization in games.
- Implementation and algorithm engineering for control, reinforcement learning and robotics
- Implementation and algorithm engineering for time series prediction
Felix Heide, Room 410
- Research Areas: Computational Imaging, Computer Vision, Machine Learning (focus on Optimization and Approximate Inference).
- Optical Neural Networks
- Hardware-in-the-loop Holography
- Zero-shot and Simulation-only Learning
- Object recognition in extreme conditions
- 3D Scene Representations for View Generation and Inverse Problems
- Long-range Imaging in Scattering Media
- Hardware-in-the-loop Illumination and Sensor Optimization
- Inverse Lidar Design
- Phase Retrieval Algorithms
- Proximal Algorithms for Learning and Inference
- Domain-Specific Language for Optics Design
Peter Henderson , 302 Sherrerd Hall
- Research Areas: Machine learning, law, and policy
Kyle Jamieson, Room 306
- Research areas: Wireless and mobile networking; indoor radar and indoor localization; Internet of Things
- See other topics on my independent work ideas page (campus IP and CS dept. login req'd)
Alan Kaplan, 221 Nassau Street, Room 105
Research Areas:
- Random apps of kindness - mobile application/technology frameworks used to help individuals or communities; topic areas include, but are not limited to: first response, accessibility, environment, sustainability, social activism, civic computing, tele-health, remote learning, crowdsourcing, etc.
- Tools automating programming language interoperability - Java/C++, React Native/Java, etc.
- Software visualization tools for education
- Connected consumer devices, applications and protocols
Brian Kernighan, Room 311
- Research Areas: application-specific languages, document preparation, user interfaces, software tools, programming methodology
- Application-oriented languages, scripting languages.
- Tools; user interfaces
- Digital humanities
Zachary Kincaid, Room 219
- Research areas: programming languages, program analysis, program verification, automated reasoning
- Independent Research Topics:
- Develop a practical algorithm for an intractable problem (e.g., by developing practical search heuristics, or by reducing to, or by identifying a tractable sub-problem, ...).
- Design a domain-specific programming language, or prototype a new feature for an existing language.
- Any interesting project related to programming languages or logic.
Gillat Kol, Room 316
Aleksandra korolova, 309 sherrerd hall.
- Research areas: Societal impacts of algorithms and AI; privacy; fair and privacy-preserving machine learning; algorithm auditing.
Advisees typically have taken one or more of COS 226, COS 324, COS 423, COS 424 or COS 445.
Pravesh Kothari, Room 320
- Research areas: Theory
Amit Levy, Room 307
- Research Areas: Operating Systems, Distributed Systems, Embedded Systems, Internet of Things
- Distributed hardware testing infrastructure
- Second factor security tokens
- Low-power wireless network protocol implementation
- USB device driver implementation
Kai Li, Room 321
- Research Areas: Distributed systems; storage systems; content-based search and data analysis of large datasets.
- Fast communication mechanisms for heterogeneous clusters.
- Approximate nearest-neighbor search for high dimensional data.
- Data analysis and prediction of in-patient medical data.
- Optimized implementation of classification algorithms on manycore processors.
Xiaoyan Li, 221 Nassau Street, Room 104
- Research areas: Information retrieval, novelty detection, question answering, AI, machine learning and data analysis.
- Explore new statistical retrieval models for document retrieval and question answering.
- Apply AI in various fields.
- Apply supervised or unsupervised learning in health, education, finance, and social networks, etc.
- Any interesting project related to AI, machine learning, and data analysis.
Lydia Liu, Room 414
- Research Areas: algorithmic decision making, machine learning and society
- Theoretical foundations for algorithmic decision making (e.g. mathematical modeling of data-driven decision processes, societal level dynamics)
- Societal impacts of algorithms and AI through a socio-technical lens (e.g. normative implications of worst case ML metrics, prediction and model arbitrariness)
- Machine learning for social impact domains, especially education (e.g. responsible development and use of LLMs for education equity and access)
- Evaluation of human-AI decision making using statistical methods (e.g. causal inference of long term impact)
Wyatt Lloyd, Room 323
- Research areas: Distributed Systems
- Caching algorithms and implementations
- Storage systems
- Distributed transaction algorithms and implementations
Alex Lombardi , Room 312
- Research Areas: Theory
Margaret Martonosi, Room 208
- Quantum Computing research, particularly related to architecture and compiler issues for QC.
- Computer architectures specialized for modern workloads (e.g., graph analytics, machine learning algorithms, mobile applications
- Investigating security and privacy vulnerabilities in computer systems, particularly IoT devices.
- Other topics in computer architecture or mobile / IoT systems also possible.
Jonathan Mayer, Sherrerd Hall, Room 307
Available for Spring 2025 single-semester IW, only
- Research areas: Technology law and policy, with emphasis on national security, criminal procedure, consumer privacy, network management, and online speech.
- Assessing the effects of government policies, both in the public and private sectors.
- Collecting new data that relates to government decision making, including surveying current business practices and studying user behavior.
- Developing new tools to improve government processes and offer policy alternatives.
Mae Milano, Room 307
- Local-first / peer-to-peer systems
- Wide-ares storage systems
- Consistency and protocol design
- Type-safe concurrency
- Language design
- Gradual typing
- Domain-specific languages
- Languages for distributed systems
Andrés Monroy-Hernández, Room 405
- Research Areas: Human-Computer Interaction, Social Computing, Public-Interest Technology, Augmented Reality, Urban Computing
- Research interests:developing public-interest socio-technical systems. We are currently creating alternatives to gig work platforms that are more equitable for all stakeholders. For instance, we are investigating the socio-technical affordances necessary to support a co-op food delivery network owned and managed by workers and restaurants. We are exploring novel system designs that support self-governance, decentralized/federated models, community-centered data ownership, and portable reputation systems. We have opportunities for students interested in human-centered computing, UI/UX design, full-stack software development, and qualitative/quantitative user research.
- Beyond our core projects, we are open to working on research projects that explore the use of emerging technologies, such as AR, wearables, NFTs, and DAOs, for creative and out-of-the-box applications.
Christopher Moretti, Corwin Hall, Room 036
- Research areas: Distributed systems, high-throughput computing, computer science/engineering education
- Expansion, improvement, and evaluation of open-source distributed computing software.
- Applications of distributed computing for "big science" (e.g. biometrics, data mining, bioinformatics)
- Software and best practices for computer science education and study, especially Princeton's 126/217/226 sequence or MOOCs development
- Sports analytics and/or crowd-sourced computing
Radhika Nagpal, F316 Engineering Quadrangle
- Research areas: control, robotics and dynamical systems
Karthik Narasimhan, Room 422
- Research areas: Natural Language Processing, Reinforcement Learning
- Autonomous agents for text-based games ( https://www.microsoft.com/en-us/research/project/textworld/ )
- Transfer learning/generalization in NLP
- Techniques for generating natural language
- Model-based reinforcement learning
Arvind Narayanan, 308 Sherrerd Hall
Research Areas: fair machine learning (and AI ethics more broadly), the social impact of algorithmic systems, tech policy
Pedro Paredes, Corwin Hall, Room 041
My primary research work is in Theoretical Computer Science.
* Research Interest: Spectral Graph theory, Pseudorandomness, Complexity theory, Coding Theory, Quantum Information Theory, Combinatorics.
The IW projects I am interested in advising can be divided into three categories:
1. Theoretical research
I am open to advise work on research projects in any topic in one of my research areas of interest. A project could also be based on writing a survey given results from a few papers. Students should have a solid background in math (e.g., elementary combinatorics, graph theory, discrete probability, basic algebra/calculus) and theoretical computer science (226 and 240 material, like big-O/Omega/Theta, basic complexity theory, basic fundamental algorithms). Mathematical maturity is a must.
A (non exhaustive) list of topics of projects I'm interested in: * Explicit constructions of better vertex expanders and/or unique neighbor expanders. * Construction deterministic or random high dimensional expanders. * Pseudorandom generators for different problems. * Topics around the quantum PCP conjecture. * Topics around quantum error correcting codes and locally testable codes, including constructions, encoding and decoding algorithms.
2. Theory informed practical implementations of algorithms Very often the great advances in theoretical research are either not tested in practice or not even feasible to be implemented in practice. Thus, I am interested in any project that consists in trying to make theoretical ideas applicable in practice. This includes coming up with new algorithms that trade some theoretical guarantees for feasible implementation yet trying to retain the soul of the original idea; implementing new algorithms in a suitable programming language; and empirically testing practical implementations and comparing them with benchmarks / theoretical expectations. A project in this area doesn't have to be in my main areas of research, any theoretical result could be suitable for such a project.
Some examples of areas of interest: * Streaming algorithms. * Numeric linear algebra. * Property testing. * Parallel / Distributed algorithms. * Online algorithms. 3. Machine learning with a theoretical foundation
I am interested in projects in machine learning that have some mathematical/theoretical, even if most of the project is applied. This includes topics like mathematical optimization, statistical learning, fairness and privacy.
One particular area I have been recently interested in is in the area of rating systems (e.g., Chess elo) and applications of this to experts problems.
Final Note: I am also willing to advise any project with any mathematical/theoretical component, even if it's not the main one; please reach out via email to chat about project ideas.
Iasonas Petras, Corwin Hall, Room 033
- Research Areas: Information Based Complexity, Numerical Analysis, Quantum Computation.
- Prerequisites: Reasonable mathematical maturity. In case of a project related to Quantum Computation a certain familiarity with quantum mechanics is required (related courses: ELE 396/PHY 208).
- Possible research topics include:
1. Quantum algorithms and circuits:
- i. Design or simulation quantum circuits implementing quantum algorithms.
- ii. Design of quantum algorithms solving/approximating continuous problems (such as Eigenvalue problems for Partial Differential Equations).
2. Information Based Complexity:
- i. Necessary and sufficient conditions for tractability of Linear and Linear Tensor Product Problems in various settings (for example worst case or average case).
- ii. Necessary and sufficient conditions for tractability of Linear and Linear Tensor Product Problems under new tractability and error criteria.
- iii. Necessary and sufficient conditions for tractability of Weighted problems.
- iv. Necessary and sufficient conditions for tractability of Weighted Problems under new tractability and error criteria.
3. Topics in Scientific Computation:
- i. Randomness, Pseudorandomness, MC and QMC methods and their applications (Finance, etc)
Yuri Pritykin, 245 Carl Icahn Lab
- Research interests: Computational biology; Cancer immunology; Regulation of gene expression; Functional genomics; Single-cell technologies.
- Potential research projects: Development, implementation, assessment and/or application of algorithms for analysis, integration, interpretation and visualization of multi-dimensional data in molecular biology, particularly single-cell and spatial genomics data.
Benjamin Raphael, Room 309
- Research interests: Computational biology and bioinformatics; Cancer genomics; Algorithms and machine learning approaches for analysis of large-scale datasets
- Implementation and application of algorithms to infer evolutionary processes in cancer
- Identifying correlations between combinations of genomic mutations in human and cancer genomes
- Design and implementation of algorithms for genome sequencing from new DNA sequencing technologies
- Graph clustering and network anomaly detection, particularly using diffusion processes and methods from spectral graph theory
Vikram Ramaswamy, 035 Corwin Hall
- Research areas: Interpretability of AI systems, Fairness in AI systems, Computer vision.
- Constructing a new method to explain a model / create an interpretable by design model
- Analyzing a current model / dataset to understand bias within the model/dataset
- Proposing new fairness evaluations
- Proposing new methods to train to improve fairness
- Developing synthetic datasets for fairness / interpretability benchmarks
- Understanding robustness of models
Ran Raz, Room 240
- Research Area: Computational Complexity
- Independent Research Topics: Computational Complexity, Information Theory, Quantum Computation, Theoretical Computer Science

Szymon Rusinkiewicz, Room 406
- Research Areas: computer graphics; computer vision; 3D scanning; 3D printing; robotics; documentation and visualization of cultural heritage artifacts
- Research ways of incorporating rotation invariance into computer visiontasks such as feature matching and classification
- Investigate approaches to robust 3D scan matching
- Model and compensate for imperfections in 3D printing
- Given a collection of small mobile robots, apply control policies learned in simulation to the real robots.
Olga Russakovsky, Room 408
- Research Areas: computer vision, machine learning, deep learning, crowdsourcing, fairness&bias in AI
- Design a semantic segmentation deep learning model that can operate in a zero-shot setting (i.e., recognize and segment objects not seen during training)
- Develop a deep learning classifier that is impervious to protected attributes (such as gender or race) that may be erroneously correlated with target classes
- Build a computer vision system for the novel task of inferring what object (or part of an object) a human is referring to when pointing to a single pixel in the image. This includes both collecting an appropriate dataset using crowdsourcing on Amazon Mechanical Turk, creating a new deep learning formulation for this task, and running extensive analysis of both the data and the model
Sebastian Seung, Princeton Neuroscience Institute, Room 153
- Research Areas: computational neuroscience, connectomics, "deep learning" neural networks, social computing, crowdsourcing, citizen science
- Gamification of neuroscience (EyeWire 2.0)
- Semantic segmentation and object detection in brain images from microscopy
- Computational analysis of brain structure and function
- Neural network theories of brain function
Jaswinder Pal Singh, Room 324
- Research Areas: Boundary of technology and business/applications; building and scaling technology companies with special focus at that boundary; parallel computing systems and applications: parallel and distributed applications and their implications for software and architectural design; system software and programming environments for multiprocessors.
- Develop a startup company idea, and build a plan/prototype for it.
- Explore tradeoffs at the boundary of technology/product and business/applications in a chosen area.
- Study and develop methods to infer insights from data in different application areas, from science to search to finance to others.
- Design and implement a parallel application. Possible areas include graphics, compression, biology, among many others. Analyze performance bottlenecks using existing tools, and compare programming models/languages.
- Design and implement a scalable distributed algorithm.
Mona Singh, Room 420
- Research Areas: computational molecular biology, as well as its interface with machine learning and algorithms.
- Whole and cross-genome methods for predicting protein function and protein-protein interactions.
- Analysis and prediction of biological networks.
- Computational methods for inferring specific aspects of protein structure from protein sequence data.
- Any other interesting project in computational molecular biology.
Robert Tarjan, 194 Nassau St., Room 308
- Research Areas: Data structures; graph algorithms; combinatorial optimization; computational complexity; computational geometry; parallel algorithms.
- Implement one or more data structures or combinatorial algorithms to provide insight into their empirical behavior.
- Design and/or analyze various data structures and combinatorial algorithms.
Olga Troyanskaya, Room 320
- Research Areas: Bioinformatics; analysis of large-scale biological data sets (genomics, gene expression, proteomics, biological networks); algorithms for integration of data from multiple data sources; visualization of biological data; machine learning methods in bioinformatics.
- Implement and evaluate one or more gene expression analysis algorithm.
- Develop algorithms for assessment of performance of genomic analysis methods.
- Develop, implement, and evaluate visualization tools for heterogeneous biological data.
David Walker, Room 211
- Research Areas: Programming languages, type systems, compilers, domain-specific languages, software-defined networking and security
- Independent Research Topics: Any other interesting project that involves humanitarian hacking, functional programming, domain-specific programming languages, type systems, compilers, software-defined networking, fault tolerance, language-based security, theorem proving, logic or logical frameworks.
Shengyi Wang, Postdoctoral Research Associate, Room 216
Available for Fall 2024 single-semester IW, only
- Independent Research topics: Explore Escher-style tilings using (introductory) group theory and automata theory to produce beautiful pictures.
Kevin Wayne, Corwin Hall, Room 040
- Research Areas: design, analysis, and implementation of algorithms; data structures; combinatorial optimization; graphs and networks.
- Design and implement computer visualizations of algorithms or data structures.
- Develop pedagogical tools or programming assignments for the computer science curriculum at Princeton and beyond.
- Develop assessment infrastructure and assessments for MOOCs.
Matt Weinberg, 194 Nassau St., Room 222
- Research Areas: algorithms, algorithmic game theory, mechanism design, game theoretical problems in {Bitcoin, networking, healthcare}.
- Theoretical questions related to COS 445 topics such as matching theory, voting theory, auction design, etc.
- Theoretical questions related to incentives in applications like Bitcoin, the Internet, health care, etc. In a little bit more detail: protocols for these systems are often designed assuming that users will follow them. But often, users will actually be strictly happier to deviate from the intended protocol. How should we reason about user behavior in these protocols? How should we design protocols in these settings?
Huacheng Yu, Room 310
- data structures
- streaming algorithms
- design and analyze data structures / streaming algorithms
- prove impossibility results (lower bounds)
- implement and evaluate data structures / streaming algorithms
Ellen Zhong, Room 314
Opportunities outside the department.
We encourage students to look in to doing interdisciplinary computer science research and to work with professors in departments other than computer science. However, every CS independent work project must have a strong computer science element (even if it has other scientific or artistic elements as well.) To do a project with an adviser outside of computer science you must have permission of the department. This can be accomplished by having a second co-adviser within the computer science department or by contacting the independent work supervisor about the project and having he or she sign the independent work proposal form.
Here is a list of professors outside the computer science department who are eager to work with computer science undergraduates.
Maria Apostolaki, Engineering Quadrangle, C330
- Research areas: Computing & Networking, Data & Information Science, Security & Privacy
Branko Glisic, Engineering Quadrangle, Room E330
- Documentation of historic structures
- Cyber physical systems for structural health monitoring
- Developing virtual and augmented reality applications for documenting structures
- Applying machine learning techniques to generate 3D models from 2D plans of buildings
- Contact : Rebecca Napolitano, rkn2 (@princeton.edu)
Mihir Kshirsagar, Sherrerd Hall, Room 315
Center for Information Technology Policy.
- Consumer protection
- Content regulation
- Competition law
- Economic development
- Surveillance and discrimination
Sharad Malik, Engineering Quadrangle, Room B224
Select a Senior Thesis Adviser for the 2020-21 Academic Year.
- Design of reliable hardware systems
- Verifying complex software and hardware systems
Prateek Mittal, Engineering Quadrangle, Room B236
- Internet security and privacy
- Social Networks
- Privacy technologies, anonymous communication
- Network Science
- Internet security and privacy: The insecurity of Internet protocols and services threatens the safety of our critical network infrastructure and billions of end users. How can we defend end users as well as our critical network infrastructure from attacks?
- Trustworthy social systems: Online social networks (OSNs) such as Facebook, Google+, and Twitter have revolutionized the way our society communicates. How can we leverage social connections between users to design the next generation of communication systems?
- Privacy Technologies: Privacy on the Internet is eroding rapidly, with businesses and governments mining sensitive user information. How can we protect the privacy of our online communications? The Tor project (https://www.torproject.org/) is a potential application of interest.
Ken Norman, Psychology Dept, PNI 137
- Research Areas: Memory, the brain and computation
- Lab: Princeton Computational Memory Lab
Potential research topics
- Methods for decoding cognitive state information from neuroimaging data (fMRI and EEG)
- Neural network simulations of learning and memory
Caroline Savage
Office of Sustainability, Phone:(609)258-7513, Email: cs35 (@princeton.edu)
The Campus as Lab program supports students using the Princeton campus as a living laboratory to solve sustainability challenges. The Office of Sustainability has created a list of campus as lab research questions, filterable by discipline and topic, on its website .
An example from Computer Science could include using TigerEnergy , a platform which provides real-time data on campus energy generation and consumption, to study one of the many energy systems or buildings on campus. Three CS students used TigerEnergy to create a live energy heatmap of campus .
Other potential projects include:
- Apply game theory to sustainability challenges
- Develop a tool to help visualize interactions between complex campus systems, e.g. energy and water use, transportation and storm water runoff, purchasing and waste, etc.
- How can we learn (in aggregate) about individuals’ waste, energy, transportation, and other behaviors without impinging on privacy?
Janet Vertesi, Sociology Dept, Wallace Hall, Room 122
- Research areas: Sociology of technology; Human-computer interaction; Ubiquitous computing.
- Possible projects: At the intersection of computer science and social science, my students have built mixed reality games, produced artistic and interactive installations, and studied mixed human-robot teams, among other projects.
David Wentzlaff, Engineering Quadrangle, Room 228
Computing, Operating Systems, Sustainable Computing.
- Instrument Princeton's Green (HPCRC) data center
- Investigate power utilization on an processor core implemented in an FPGA
- Dismantle and document all of the components in modern electronics. Invent new ways to build computers that can be recycled easier.
- Other topics in parallel computer architecture or operating systems
151+ Research Proposal Topics [Updated 2024]

Crafting a compelling research proposal begins with selecting the right topic—a task that demands careful consideration and a thoughtful approach. In this blog post, we’ll delve into the intricacies of choosing research proposal topics, exploring the importance of a well-defined focus and guiding you through the steps to create a robust proposal.
How to Select Research Proposal Topics?
Table of Contents
Selecting research proposal topics is a crucial step in the research process. Here’s a step-by-step guide to help you choose a compelling and impactful research topic:
- Self-reflection:
- Identify your personal interests, passions, and curiosities.
- Consider topics that resonate with you on a deep level.
- Academic and Professional Interests:
- Reflect on subjects that captivated you during coursework or work experience.
- Assess the relevance of these interests to your academic or career goals.
- Current Issues and Trends:
- Stay informed about contemporary challenges and emerging trends in your field.
- Choose a topic that addresses current issues for greater relevance and impact.
- Literature Review:
- Conduct a thorough review of existing research in your chosen field.
- Identify gaps and limitations in the current body of knowledge.
- Formulate Clear Research Questions:
- Develop clear and concise research questions based on the gaps identified.
- Ensure your questions are feasible and align with the chosen topic.
- Choose a Methodology:
- Select an appropriate research methodology (experimental, qualitative, quantitative, or mixed methods).
- Justify your choice and discuss data collection techniques.
- Significance and Contribution:
- Articulate the relevance of your proposed research.
- Highlight the potential contributions your work can make to the field.
- Research Design and Plan:
- Outline the specifics of your research design.
- Create a realistic timeline, allocating resources and budget effectively.
- Address Challenges and Limitations:
- Acknowledge potential challenges and limitations.
- Discuss strategies to mitigate challenges and be transparent about constraints.
- Conclusion:
- Summarize key points of your research proposal.
- Emphasize the importance of the chosen topic and encourage feedback.
By following these steps, you can ensure that your research proposal topic is not only engaging but also has the potential to make a meaningful contribution to your field of study.
151+ Research Proposal Topics: Category Wise
Science and technology.
- The Impact of Artificial Intelligence on Job Market Trends
- Advancements in Renewable Energy Technologies
- Exploring the Potential of CRISPR Technology in Genetic Engineering
- Cybersecurity Measures for Critical Infrastructure Protection
- The Role of Blockchain in Supply Chain Management
- Augmented Reality in Education: Enhancing Learning Experiences
- Quantum Computing: Current Status and Future Implications
- Sustainable Technologies for Environmental Conservation
- Smart Cities: Integrating Technology for Urban Development
- Robotics in Healthcare: Applications and Ethical Considerations
Health and Medicine
- Precision Medicine: Customizing Healthcare Based on Genetic Factors
- The Impact of Telemedicine on Patient Care
- Mental Health Stigma: Strategies for Reduction and Education
- Vaccination Hesitancy: Understanding Causes and Developing Interventions
- Aging Population and Healthcare Challenges
- Bioinformatics and Personalized Cancer Therapies
- The Role of Artificial Intelligence in Diagnosing Medical Conditions
- Emerging Infectious Diseases: Preparedness and Response Strategies
- Nutrition Education in Schools: Promoting Healthy Lifestyles
- Healthcare Disparities: Addressing and Eliminating Gaps in Access
Social Sciences
- Social Media and its Influence on Political Discourse
- Impact of Social Isolation on Mental Health in Elderly Populations
- Cultural Competence in Education: Training and Implementation
- The Role of Gender Stereotypes in Career Choices
- Cyberbullying: Prevention and Intervention Strategies
- The Effects of Immigration Policies on Migrant Communities
- Restorative Justice in Criminal Justice Systems
- Examining the Relationship Between Social Media Use and Self-Esteem
- Intersectionality in Feminist Movements: Challenges and Opportunities
- Community Policing: Building Trust between Law Enforcement and Communities
- E-Learning Platforms: Effectiveness and Challenges
- Inquiry-Based Learning: Enhancing Critical Thinking Skills
- Inclusive Education Practices: Meeting the Needs of Diverse Learners
- The Impact of Standardized Testing on Educational Equity
- School Safety Measures: Strategies for Prevention and Response
- Teacher Professional Development: Models and Effectiveness
- Online Education Accessibility for Students with Disabilities
- Gamification in Education: Engaging Students in Learning
- Bilingual Education: Benefits and Challenges
- STEM Education Initiatives: Encouraging Interest in Science and Technology
Business and Economics
- Sustainable Business Practices: Balancing Profit and Environmental Impact
- Corporate Social Responsibility in Multinational Corporations
- Impact of Artificial Intelligence on Business Operations
- Economic Consequences of Global Health Crises
- Digital Marketing Trends and Consumer Behavior
- Financial Literacy Education: Bridging the Gap
- Small Business Sustainability: Challenges and Strategies
- The Gig Economy: Implications for Workers and Employers
- Supply Chain Resilience in the Face of Global Disruptions
- Innovation and Entrepreneurship in Emerging Markets
Environment and Sustainability
- Climate Change Adaptation Strategies for Coastal Communities
- Biodiversity Conservation in Urban Environments
- Circular Economy Models: Reducing Waste and Promoting Sustainability
- Water Scarcity: Technological Solutions and Policy Measures
- Impact of Plastic Pollution on Marine Ecosystems
- Sustainable Agriculture Practices: Balancing Production and Conservation
- Environmental Education in Schools: Fostering Eco-Consciousness
- Green Building Technologies: Enhancing Energy Efficiency
- Ecotourism: Balancing Conservation and Economic Development
- The Role of International Agreements in Addressing Environmental Issues
Psychology and Behavior
- The Influence of Social Media on Body Image and Self-Esteem
- Cognitive Behavioral Therapy for Anxiety and Depression
- Impact of Childhood Trauma on Adult Mental Health
- Positive Psychology Interventions: Enhancing Well-Being
- Sleep Hygiene and its Impact on Mental Health
- The Psychology of Procrastination: Causes and Interventions
- Emotional Intelligence in the Workplace: Benefits and Training
- The Impact of Parenting Styles on Child Development
- Cross-Cultural Psychology: Understanding Cultural Influences on Behavior
- The Role of Music in Emotional Regulation and Stress Reduction
Political Science and International Relations
- The Rise of Populism: Causes and Consequences
- Cyber Warfare and International Security
- Human Rights Violations in Conflict Zones: Challenges and Solutions
- The Role of International Organizations in Global Governance
- Political Polarization: Understanding Divisive Trends
- Nuclear Proliferation and Arms Control Agreements
- Comparative Analysis of Electoral Systems
- Immigration Policies and Social Cohesion
- Global Health Diplomacy: Collaborative Approaches to Health Challenges
- The Impact of Disinformation on Democratic Processes
History and Cultural Studies
- Reevaluating Historical Narratives: Perspectives and Interpretations
- Cultural Impact of Globalization: Trends and Reactions
- Indigenous Rights and Representation in Historical Context
- History of Scientific Discoveries and their Societal Impact
- Archaeological Excavations: Uncovering Lost Civilizations
- Cultural Appropriation: Examining Controversies and Contexts
- The Role of Women in Historical Movements
- Preservation of Cultural Heritage: Challenges and Innovations
- Historical Trauma and its Contemporary Repercussions
- Impact of Colonialism on Contemporary Societies
Communication and Media Studies
- Influence of Social Media on Political Participation
- Media Representation of Marginalized Groups
- Fake News and Misinformation: Identifying and Combating Trends
- The Evolution of Print Media in the Digital Age
- Media Literacy Education: Navigating Information in the Digital Era
- Celebrity Culture and its Impact on Society
- The Role of Public Relations in Shaping Organizational Image
- Cross-Cultural Communication in Global Business
- Podcasting as an Emerging Medium of Communication
- Advertising and Consumer Behavior: Analyzing Persuasion Techniques
Philosophy and Ethics
- Ethical Considerations in Artificial Intelligence Research
- Bioethics in Medical Decision-Making
- Existentialism and its Relevance in Contemporary Society
- Animal Rights and Ethical Treatment in Scientific Research
- Environmental Ethics: Balancing Human Needs and Ecological Sustainability
- The Ethics of Genetic Engineering and Cloning
- Virtue Ethics in Professional Decision-Making
- Technology and Privacy: Ethical Dilemmas in the Digital Age
- Ethical Implications of Artificial Intelligence in Warfare
- Utilitarianism and its Application in Ethical Decision-Making
Education Policy and Administration
- School Voucher Programs: Impact on Educational Equity
- Teacher Evaluation Systems: Effectiveness and Fairness
- Inclusive Leadership in Educational Institutions
- Early Childhood Education: Policy and Implementation
- Standardized Testing: Implications for Educational Policy
- Education Funding Models: Challenges and Solutions
- School Choice and its Impact on Student Achievement
- Educational Technology Integration in Classroom Settings
- Community Engagement in School Decision-Making
- The Role of Educational Leaders in Fostering Inclusive Schools
Economics and Development Studies
- Microfinance and Poverty Alleviation Strategies
- Impact of Global Trade Policies on Developing Economies
- Economic Empowerment of Women in Developing Countries
- Sustainable Development Goals: Progress and Challenges
- Rural-Urban Migration: Economic and Social Impacts
- Financial Inclusion: Strategies for Bridging the Gap
- Foreign Aid Effectiveness: Assessing Outcomes
- Technology Transfer and Innovation in Developing Nations
- Income Inequality: Causes and Policy Solutions
- The Role of Microenterprise in Local Economic Development
Criminal Justice and Law
- Restorative Justice: Implementation and Impact on Recidivism
- Police Body Cameras: Efficacy and Ethical Considerations
- Cybercrime Laws and Challenges in the Digital Age
- Juvenile Justice Reform: Strategies for Rehabilitation
- Bail Reform: Addressing Inequities in Pretrial Detention
- Criminal Profiling: Validity and Ethical Concerns
- Drug Policy Reform: Exploring Alternatives to Criminalization
- The Impact of Hate Crime Legislation on Social Cohesion
- Eyewitness Testimony Reliability: Challenges and Improvements
- International Criminal Court: Effectiveness and Challenges
Public Health and Epidemiology
- Disease Surveillance Systems: Enhancing Early Detection
- Health Inequalities: Social Determinants and Interventions
- Maternal and Child Health Interventions in Developing Countries
- Impact of Health Education on Preventive Behaviors
- Access to Healthcare Services in Rural Areas
- Lifestyle Interventions for Chronic Disease Prevention
- Community-Based Participatory Research in Public Health
- Mental Health Interventions in School Settings
- The Role of Public Health in Pandemic Preparedness and Response
Computer Science
- Explainable Artificial Intelligence: Bridging the Gap Between Performance and Interpretability
- The Role of Quantum Computing in Revolutionizing Cryptography
- Ethical Considerations in the Development of Autonomous Vehicles
- Cybersecurity Challenges in the Internet of Things (IoT) Ecosystem
- Human-Computer Interaction: Enhancing User Experience in Virtual Reality Environments
How to Compose a Research Proposal?
Composing a research proposal is a systematic process that involves careful planning, organization, and clear articulation of your research idea. Here’s a step-by-step guide on how to compose a research proposal:
- Title:
- Create a clear and concise title that reflects the essence of your research.
- Introduction:
- Provide background information on the research topic.
- Clearly state the research problem or question.
- Justify the importance and relevance of your research.
- Summarize relevant existing literature.
- Identify gaps, limitations, and areas for further exploration.
- Establish a theoretical framework for your study.
- Research Questions or Hypotheses:
- Formulate clear and specific research questions or hypotheses.
- Ensure they align with the research problem and are feasible.
- Objectives or Aims:
- Outline the specific goals of your research.
- Clearly state what you aim to achieve with your study.
- Methodology:
- Describe the research design and justify your choice.
- Detail the data collection methods and tools you plan to use.
- Address ethical considerations related to your research.
- Explain the importance of your research.
- Clearly state the potential contributions your study can make.
- Provide a detailed plan for executing your research.
- Include a timeline, milestones, and the allocation of resources.
- Potential Challenges and Limitations:
- Acknowledge possible obstacles and limitations.
- Discuss strategies to address challenges proactively.
- Summarize the key points of your research proposal.
- Reiterate the significance of your research.
- Invite feedback and suggestions.
- References:
- Cite all the sources and literature used in your proposal.
- Follow the appropriate citation style ( APA, MLA, Chicago , etc.).
- Appendices (if necessary):
- Include any supplementary materials such as surveys, questionnaires, or additional data.
Tips for Composing a Research Proposal
- Clarity and Conciseness: Use clear and straightforward language. Avoid unnecessary jargon that may confuse readers.
- Alignment: Ensure that each section of your proposal aligns with the overall research objective.
- Feasibility: Confirm that your proposed research is feasible within the given time and resource constraints.
- Review and Revise: Review your proposal for coherence, consistency, and clarity. Seek feedback from peers, mentors, or advisors and make revisions accordingly.
- Adherence to Guidelines: Follow any specific guidelines or instructions provided by your institution or funding agency.
- Engage the Reader: Capture the reader’s attention in the introduction and maintain engagement throughout.
- Ethical Considerations: Clearly address any ethical concerns related to your research, ensuring compliance with ethical standards.
Selecting research proposal topics is a nuanced process that requires a blend of personal passion, academic rigor, and an understanding of the broader context.
By following this comprehensive guide, you can navigate the seas of research proposal development with confidence, ensuring that your chosen topic is not only compelling but also lays the foundation for meaningful and impactful research.
Related Posts

Step by Step Guide on The Best Way to Finance Car

The Best Way on How to Get Fund For Business to Grow it Efficiently
- Research & Faculty
- Offices & Services
- Information for:
- Faculty & Staff
- News & Events
- Contact & Visit
- About the Department
- Message from the Chair
- Computer Science Major (BS/BA)
- Computer Science Minor
- Data Science and Engineering Minor
- Combined BS (or BA)/MS Degree Program
- Intro Courses
- Special Programs & Opportunities
- Student Groups & Organizations
- Undergraduate Programs
- Undergraduate Research
- Senior Thesis
- Peer Mentors
- Curriculum & Requirements
- MS in Computer Science
- PhD in Computer Science
- Admissions FAQ
- Financial Aid
- Graduate Programs
- Courses Collapse Courses Submenu
- Research Overview
- Research Areas
- Systems and Networking
- Security and Privacy
- Programming Languages
- Artificial Intelligence
- Human-Computer Interaction
- Vision and Graphics
- Groups & Labs
- Affiliated Centers & Institutes
- Industry Partnerships
- Adobe Research Partnership
- Center for Advancing Safety of Machine Intelligence
- Submit a Tech Report
- Tech Reports
- Tenure-Track Faculty
- Faculty of Instruction
- Affiliated Faculty
- Adjunct Faculty
- Postdoctoral Fellows
- PhD Students
- Outgoing PhDs and Postdocs
- Visiting Scholars
- News Archive
- Weekly Bulletin
- Monthly Student Newsletter
- All Public Events
- Seminars, Workshops, & Talks
- Distinguished Lecture Series
- CS Colloquium Series
- CS + X Events
- Tech Talk Series
- Honors & Awards
- External Faculty Awards
- University Awards
- Department Awards
- Student Resources
- Undergraduate Student Resources
- MS Student Resources
- PhD Student Resources
- Student Organization Resources
- Faculty Resources
- Postdoc Resources
- Staff Resources
- Purchasing, Procurement and Vendor Payment
- Expense Reimbursements
- Department Operations and Facilities
- Initiatives
- Student Groups
- CS Faculty Diversity Committee
- Broadening Participation in Computing (BPC) Plan
- Northwestern Engineering
Academics / Courses / Descriptions COMP_SCI 397, 497: Selected Topics in Computer Networks
Prerequisites, description.
The course will cover a broad range of topics including congestion control, routing, analysis and design of network protocols (both wired and wireless), data centers, analysis and performance of content distribution networks, network security, vulnerability, and defenses, net neutrality, and online social networks.
Students will form teams of two or three; each team will tackle a well-defined research project during the quarter. A list of suggested project topics will be provided. All projects are subjected to approval by the instructor. The project component will include a short written project proposal, a short mid-term project report, a final project presentation, and a final project report. Each component adds some significant element to the paper, and the overall project grade will be based on the quality of each component of your work.
The above project components are due by email to the instructor by the end of the given day of the respective week.
- Week 1: Project presentations by group leaders
- Week 2: Form groups of 2 or 3, choose a topic for your project, and meet with the project leader.
- Week 3: Write an introduction describing the problem and how you plan to approach it (what will you actually do?). Include motivation (why does the problem matter?) and related work (what have others already done about it?). 2 pages total.
- Week 6: Midterm presentation. Update your paper to include your preliminary results. 5 pages total.
- Week 11: Presentations by all groups.
- Week 12: Turn in your completed paper. 10 pages total. You should incorporate the comments received during the presentation.
Each team will have a weekly meeting with project leaders. Grading
- Paper reviews (15%), presentations (20%) and debating in the class (15%): 50%
- Projects 50% (Project proposal: 5%; Midterm report: 5%; weekly report and meeting: 10%; project presentation: 10%; final project report: 20%)
- Research idea report (optional, 3 pages): 10%
PREREQUISITES: Recommended: CS 340 or equivalent networking course
Classes, Textbook, and other readings
There will be no textbook for this class. A key part of the class will be to review and discuss networking research papers. Students must read the assigned papers and submit paper reviews before each lecture. Two teams of students will be chosen to debate and lead the discussion. One team will be designated the offense and the other the defense. In class, the defense team will present first. For 30 minutes the team will discuss the work as if it were their own.
- The team should present the work and make a compelling case why the contribution is significant. This will include the context of the contribution, prior work, and in cases where papers are previously published, how the work has influenced the research community or industry's directions (impact). If the paper is very recent, the defense should present arguments for the potential impact. Coming up with potential future work can show how the paper opens doors to new
- The presentation should go well beyond a paper "summary". The defense should not critique the work other than to try to pre-empt attacks from the offense (e.g., by explicitly limiting the scope of the contribution).
- The defense should also try to look up related work to support their case (CiteSeer is a good place to start looking.)
After the defense presentation, the offense team will state their case for 20 minutes.
- This team should critique the work, and make a case for missing links, unaddressed issues, lack of impact, inappropriateness of the problem formulation,
- The more insightful and less obvious the criticisms the better.
- While the offense should prepare remarks in advance, they should also react to the points made by the defense.
- The offense should also try to look up related work to support their case.
Next, the defense and offense will be allowed follow up arguments, and finally, the class will question either side either for clarifications or to add to the discussions and controversy and make their own points on either side. The presentations should be written in Powerpoint format and will be posted on the course web page after each class.
Writing and Submitting Reviews
All students must read the assigned papers and write reviews for the papers before each lecture. Email the reviews to the instructor ([email protected]) prior to each lecture and the reviews will be posted on the course web page. Periodically, the instructor will evaluate a random subset of the reviews and provide feedback and grades to students.
Please send one review in plain text per email in the body of the email message.
A review should summarize the paper sufficiently to demonstrate your understanding, should point out the paper's contributions, strengths as well as weaknesses. Think in terms of what makes good research? What qualities make a good paper? What are the potential future impacts of the work? Note that there is no right or wrong answer to these questions. A review's quality will mainly depend on its thoughtfulness. Restating the abstract/conclusion of the paper will not earn a top grade. Reviews are roughly half-page and should cover all of the following aspects:
- What is the main result of the paper? (One or two sentence summary)
- What strengths do you see in this paper? (Your review needs have at least one or two positive things to say)
- What are some key limitations, unproven assumptions, or methodological problems with the work?
- How could the work be improved?
- What is its relevance today, or what future work does it suggest?
COMMUNICATION
Course web site: TBA.
Check it out regularly for schedule changes and other course-related announcements.
Group Email: TBA
COURSE COORDINATOR: Aleksandar Kuzmanovic
COURSE INSTRUCTOR: Prof. Kuzmanovic
computer network Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
Big Data Security Management Countermeasures in the Prevention and Control of Computer Network Crime
This paper aims to study the Countermeasures of big data security management in the prevention and control of computer network crime in the absence of relevant legislation and judicial practice. Starting from the concepts and definitions of computer crime and network crime, this paper puts forward the comparison matrix, investigation and statistics method and characteristic measure of computer crime. Through the methods of crime scene investigation, network investigation and network tracking, this paper studies the big data security management countermeasures in the prevention and control of computer network crime from the perspective of criminology. The experimental results show that the phenomenon of low age is serious, and the number of Teenagers Participating in network crime is on the rise. In all kinds of cases, criminals under the age of 35 account for more than 50%.
Mathematical Models of Effective Topology of Computer Networks for Electric Power Supply Control on Railway Transport
The paper is devoted to analysis of modern directions of innovation-investment formation of intelligent computer networks that control the fast-moving technological processes of electricity supply. It is based on the conclusion that the problem of increasing the productivity of information exchange between information resources and consumers is dominant. A method for increasing the efficiency of information exchange is proposed as a search for the rational location of a new node and the organization of such a set of its connections among the whole set of nodes of the computer network, which provides a minimum average topological distance. Mathematical models of effective topological organization of connections in computer network of power consumption control at the level of traction substations, electric power distances and the railway in general are proposed.
AI-assisted Computer Network Operations testbed for Nature-Inspired Cyber Security based adaptive defense simulation and analysis
D-ram distribution: a popular energy-saving memory mining blockchain technology.
<p>Cryptocurrencies have been a massive surge since last decade leads to blockchain technology steps in epical milestone. Blockchain is a distributed database that is shared among the nodes of a computer network. Bitcoin, as a critical role in cryptocurrency system is known as a typical blockchain, maintaining a secure and decentralized record of transactions. The value and advantage of blockchain technology has been acknowledged by the public and applied in difference areas. The defect of blockchain technology is gradually revealed. Excessively wasting electricity have severely affect the utilities usage in many countries. Therefore, DRD Memory Mining is developed to solve the defects. This article illustrates the algorithm of DRD Memory Mining and how the memory consensus mechanism works.</p>
Computer Network Attack Detection Using Enhanced Clustering Technologies
The need for security means has brought from the fact of privacy of data especially after the communication revolution in the recent times. The advancement of data mining and machine learning technology has paved the road for establishment an efficient attack prediction paradigm for protecting of large scaled networks. In this project, computer network intrusions had been eliminated by using smart machine learning algorithm. Referring a big dataset named as KDD computer intrusion dataset which includes large number of connections that diagnosed with several types of attacks; the model is established for predicting the type of attack by learning through this data. Feed forward neural network model is outperformed over the other proposed clustering models in attack prediction accuracy.
Research and Implementation of Recommendation Algorithm in Current Computer Network
Computer network security protection strategy based on big data, exploration of constructing a new mode of evaluation of tcm surgery based on computer network platform, computer network security defense model.
Abstract With the rapid development of the Internet industry, hundreds of millions of online resources are also booming. In the information space with huge and complex resources, it is necessary to quickly help users find the resources they are interested in and save users time. At this stage, the content industry’s application of the recommendation model in the content distribution process has become the mainstream. The content recommendation model provides users with a highly efficient and highly satisfying reading experience, and solves the problem of information redundancy to a certain extent. Knowledge tag personalized dynamic recommendation technology is currently widely used in the field of e-commerce. The purpose of this article is to study the optimization of the knowledge tag personalized dynamic recommendation system based on artificial intelligence algorithms. This article first proposes a hybrid recommendation algorithm based on the comparison between content-based filtering and collaborative filtering algorithms. It mainly introduces user browsing behavior analysis and design, KNN-based item similarity algorithm design, and hybrid recommendation algorithm implementation. Finally, through algorithm simulation experiments, the effectiveness of the algorithm in this paper is verified, and the accuracy of the recommendation has been improved.
Export Citation Format
Share document.
For enquiries call:
+1-469-442-0620

60+ Latest Cyber Security Research Topics in 2024
Home Blog Security 60+ Latest Cyber Security Research Topics in 2024
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cybersecurity thesis topics helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
The network can be attacked in various ways, including Distributed DoS, Knowledge Disruptions, Computer Viruses / Worms, and many more. Cyber-attacks are still rising, and more are waiting to harm their targeted systems and networks. Detecting Intrusions in cybersecurity has become challenging due to their Intelligence Performance. Therefore, it may negatively affect data integrity, privacy, availability, and security.
This article aims to demonstrate the most current Cyber Security Topics for Projects and areas of research currently lacking. We will talk about cyber security research questions, cyber security topics for the project, latest research titles about cyber security.
.jpg&w=3840&q=75)
List of Trending Cyber Security Research Topics in 2024
Digital technology has revolutionized how all businesses, large or small, work, and even governments manage their day-to-day activities, requiring organizations, corporations, and government agencies to utilize computerized systems. To protect data against online attacks or unauthorized access, cybersecurity is a priority. There are many Cyber Security Courses online where you can learn about these topics. With the rapid development of technology comes an equally rapid shift in Cyber Security Research Topics and cybersecurity trends, as data breaches, ransomware, and hacks become almost routine news items. In 2024, these will be the top cybersecurity trends.
A. Exciting Mobile Cyber Security Research Paper Topics
- The significance of continuous user authentication on mobile gadgets.
- The efficacy of different mobile security approaches.
- Detecting mobile phone hacking.
- Assessing the threat of using portable devices to access banking services.
- Cybersecurity and mobile applications.
- The vulnerabilities in wireless mobile data exchange.
- The rise of mobile malware.
- The evolution of Android malware.
- How to know you’ve been hacked on mobile.
- The impact of mobile gadgets on cybersecurity.
B. Top Computer and Software Security Topics to Research
- Learn algorithms for data encryption
- Concept of risk management security
- How to develop the best Internet security software
- What are Encrypting Viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC
- Infiltrating a Mac OS X operating system
- What are the effects of RSA on network security ?
- How do encrypting viruses work?
- DDoS attacks on IoT devices
C. Trending Information Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2024
- Discuss digital piracy in 2024
- critical cyber-attack concepts
- Social engineering and its importance
D. Current Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Firewall
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
E. Best Data Security Research Topics
- Importance of backup and recovery
- Benefits of logging for applications
- Understand physical data security
- Importance of Cloud Security
- In computing, the relationship between privacy and data security
- Talk about data leaks in mobile apps
- Discuss the effects of a black hole on a network system.
F. Important Application Security Research Topics
- Detect Malicious Activity on Google Play Apps
- Dangers of XSS attacks on apps
- Discuss SQL injection attacks.
- Insecure Deserialization Effect
- Check Security protocols
G. Cybersecurity Law & Ethics Research Topics
- Strict cybersecurity laws in China
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries' cybersecurity laws
- Discuss The Pipeline Security Act in the United States
H. Recent Cyberbullying Topics
- Protecting your Online Identity and Reputation
- Online Safety
- Sexual Harassment and Sexual Bullying
- Dealing with Bullying
- Stress Center for Teens
I. Operational Security Topics
- Identify sensitive data
- Identify possible threats
- Analyze security threats and vulnerabilities
- Appraise the threat level and vulnerability risk
- Devise a plan to mitigate the threats
J. Cybercrime Topics for a Research Paper
- Crime Prevention.
- Criminal Specialization.
- Drug Courts.
- Criminal Courts.
- Criminal Justice Ethics.
- Capital Punishment.
- Community Corrections.
- Criminal Law.
Cyber Security Future Research Topics
- Developing more effective methods for detecting and responding to cyber attacks
- Investigating the role of social media in cyber security
- Examining the impact of cloud computing on cyber security
- Investigating the security implications of the Internet of Things
- Studying the effectiveness of current cyber security measures
- Identifying new cyber security threats and vulnerabilities
- Developing more effective cyber security policies
- Examining the ethical implications of cyber security
Cyber Security Topics For Research Paper
- Cyber security threats and vulnerabilities
- Cyber security incident response and management
- Cyber security risk management
- Cyber security awareness and training
- Cyber security controls and countermeasures
- Cyber security governance
- Cyber security standards
- Cyber security insurance
- Cyber security and the law
- The future of cyber security
5 Current Research Topics in Cybersecurity
Below are the latest 5 cybersecurity research topics. They are:
- Artificial Intelligence
- Digital Supply Chains
- Internet of Things
- State-Sponsored Attacks
- Working From Home
Research Area in Cyber Security
The field of cyber security is extensive and constantly evolving. Its research covers a wide range of subjects, including:
- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
- RFID Security
- Authorisation Infrastructure
- Digital Forensics
- Autonomous Security
- Social Influence on Social Networks
How to Choose the Best Research Topics in Cyber Security
A good cybersecurity assignment heading is a skill that not everyone has, and unfortunately, not everyone has one. You might have your teacher provide you with the topics, or you might be asked to come up with your own. If you want more research topics, you can take references from Certified Ethical Hacker Certification, where you will get more hints on new topics. If you don't know where to start, here are some tips. Follow them to create compelling cybersecurity assignment topics.
1. Brainstorm
In order to select the most appropriate heading for your cybersecurity assignment, you first need to brainstorm ideas. What specific matter do you wish to explore? In this case, come up with relevant topics about the subject and select those relevant to your issue when you use our list of topics. You can also go to cyber security-oriented websites to get some ideas. Using any blog post on the internet can prove helpful if you intend to write a research paper on security threats in 2024. Creating a brainstorming list with all the keywords and cybersecurity concepts you wish to discuss is another great way to start. Once that's done, pick the topics you feel most comfortable handling. Keep in mind to stay away from common topics as much as possible.
2. Understanding the Background
In order to write a cybersecurity assignment, you need to identify two or three research paper topics. Obtain the necessary resources and review them to gain background information on your heading. This will also allow you to learn new terminologies that can be used in your title to enhance it.
3. Write a Single Topic
Make sure the subject of your cybersecurity research paper doesn't fall into either extreme. Make sure the title is neither too narrow nor too broad. Topics on either extreme will be challenging to research and write about.
4. Be Flexible
There is no rule to say that the title you choose is permanent. It is perfectly okay to change your research paper topic along the way. For example, if you find another topic on this list to better suit your research paper, consider swapping it out.
The Layout of Cybersecurity Research Guidance
It is undeniable that usability is one of cybersecurity's most important social issues today. Increasingly, security features have become standard components of our digital environment, which pervade our lives and require both novices and experts to use them. Supported by confidentiality, integrity, and availability concerns, security features have become essential components of our digital environment.
In order to make security features easily accessible to a wider population, these functions need to be highly usable. This is especially true in this context because poor usability typically translates into the inadequate application of cybersecurity tools and functionality, resulting in their limited effectiveness.
Writing Tips from Expert
Additionally, a well-planned action plan and a set of useful tools are essential for delving into Cyber Security Research Topics. Not only do these topics present a vast realm of knowledge and potential innovation, but they also have paramount importance in today's digital age. Addressing the challenges and nuances of these research areas will contribute significantly to the global cybersecurity landscape, ensuring safer digital environments for all. It's crucial to approach these topics with diligence and an open mind to uncover groundbreaking insights.
- Before you begin writing your research paper, make sure you understand the assignment.
- Your Research Paper Should Have an Engaging Topic
- Find reputable sources by doing a little research
- Precisely state your thesis on cybersecurity
- A rough outline should be developed
- Finish your paper by writing a draft
- Make sure that your bibliography is formatted correctly and cites your sources.
Discover the Power of ITIL 4 Foundation - Unleash the Potential of Your Business with this Cost-Effective Solution. Boost Efficiency, Streamline Processes, and Stay Ahead of the Competition. Learn More!
Studies in the literature have identified and recommended guidelines and recommendations for addressing security usability problems to provide highly usable security. The purpose of such papers is to consolidate existing design guidelines and define an initial core list that can be used for future reference in the field of Cyber Security Research Topics.
The researcher takes advantage of the opportunity to provide an up-to-date analysis of cybersecurity usability issues and evaluation techniques applied so far. As a result of this research paper, researchers and practitioners interested in cybersecurity systems who value human and social design elements are likely to find it useful. You can find KnowledgeHut’s Cyber Security courses online and take maximum advantage of them.
Frequently Asked Questions (FAQs)
Businesses and individuals are changing how they handle cybersecurity as technology changes rapidly - from cloud-based services to new IoT devices.
Ideally, you should have read many papers and know their structure, what information they contain, and so on if you want to write something of interest to others.
The field of cyber security is extensive and constantly evolving. Its research covers various subjects, including Quantum & Space, Data Privacy, Criminology & Law, and AI & IoT Security.
Inmates having the right to work, transportation of concealed weapons, rape and violence in prison, verdicts on plea agreements, rehab versus reform, and how reliable are eyewitnesses?

Mrinal Prakash
I am a B.Tech Student who blogs about various topics on cyber security and is specialized in web application security
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates

Latest Research Topics in Computer Networks
Latest Research Topics in Computer Networks provides lot of ongoing projects topics on computer networks. Currently, students and also scholars have focused on wireless networks and also computer security. To ensure the standard of our research activities, we continuously update with recent technological innovations. Our experts can also fight with emerging technological challenges and respond with new ideas to ensuring sufficient flexibility due to our seven years of experience. We also offer basic and advanced tutoring services in any specific domain for students and scholars by our great experts.
Every domain is a Deep-Sea……..
You have to swim against the sea continuously to reach your dream destination………
Latest Research Topics
Latest Research Topics in Computer Networks created by us in the concern of enhance students and scholars knowledge in computer networks. A computer network is an interesting field to facilitate communication through video conferencing, instant messaging, and also email over the Internet.
We have also completed nearly 1000+ projects in computer networks using various simulation tools, including NS2/NS3, Omnet++, Opnet, Qualnet, and other programming languages like Matlab, Matlab Simulink, and also Java. We also have provided below a few latest research topics in computer networks and major research areas also for your reference:
Major Research Area in Networking
-Network security
-Cyber security
-Cryptography
-Steganography
-Data security
-Information security
-Grid security
-Product security
-Key distribution and also management
- Data Center Networking
–Cloud Computing:
-Applications through Internet e.g. Google Docs
-Backup and also storage through Internet e.g. Microsoft’s Azure
-Computing through Internet e.g. Amazon EC2/S3
-Geo replicated cloud storage
-Cloud services resource allocation
-Service centric networking
-Content aware search system
-Data replication and also consistency problem in multiple cloud
- Energy Networking
–Ad hoc networks:
-Wireless space networks
-Wireless sensor networks
-Body sensor networks
-Vehicular ad hoc networks
-Underwater sensor networks
-Energy management also in mobile networks
- Mobile and Wireless Networking
-Anomaly detection detection and prevention
-Bot net detection
-Mobile cloud computing security
-Ad hoc mobile networks also in IoT
-Scheduling also in mobile cloud computing
- Next Generation Internet
-Intrusion Detection System
-ImageNet
-Velocity Compiler
-Social based routing
-Human trust and also security in social networks
- Software Defined Networking
-Control plane and also Data plane separation
-Multi tenants also in the Datacenter
-5G technology
- M2M Communications in IoT
- Network controller also for 3G/4G/5G mobile and wireless networks
- Genetic Algorithms also in network routing
- Ultra wide band networking
- Tolerant routing also based on mobile ad hoc network
- Peer-to-peer keyword searching
- Switch selection in SDN
- Protocol layering also in Microsoft windows
- Smart sensor networks also using Bluetooth
- Ultra wideband networking
- Flexible optical networking
- Non Ethernet applications also for industrial Ethernet cabling
- Distribute firewalls based data security also in local network
- Network management and also security
- Privacy defiance also in cloud/distributed systems/big data
- Pervasive security enabled host devices
- Anonymous traffic networks
- Software defined networking vulnerabilities
We also provided a few latest research topics in computer networks. For more information, contact our experts online or offline. In addition, We also support our students in projects, document writing, and also current technologies. If you need assistance for any specific technology, we also provide you the best outcome for your project….
Related Pages
Services we offer.
Mathematical proof
Pseudo code
Conference Paper
Research Proposal
System Design
Literature Survey
Data Collection
Thesis Writing
Data Analysis
Rough Draft
Paper Collection
Code and Programs
Paper Writing
Course Work
- How it works
Useful Links
How much will your dissertation cost?
Have an expert academic write your dissertation paper!
Dissertation Services

Get unlimited topic ideas and a dissertation plan for just £45.00
Order topics and plan

Get 1 free topic in your area of study with aim and justification
Yes I want the free topic

Computing Engineering Dissertation Topics
Published by Jamie Walker at January 10th, 2023 , Revised On August 18, 2023
Over a period of time, dissertations have become an inherent component of higher education studies. They are not only entrenched within the master or a PhD. Degree but also in undergraduate programmes. Computer engineering dissertations allow the researchers to choose a topic of particular interest to them and research further into the topic to add to the current body of literature.
However, choosing a topic from an extensive list of topics is always easier than working on the first topic you find interesting.
To help you get started with brainstorming for computer topic ideas, we have developed a list of the latest computer engineering dissertation topics that can be used for writing your computer engineering dissertation.
These topics have been developed by PhD-qualified writers of our team , so you can trust to use these topics for drafting your dissertation.
You may also want to start your dissertation by requesting a brief research proposal from our writers on any of these topics, which includes an introduction to the problem, research questions , aim and objectives , literature review along with the proposed methodology of research to be conducted. Let us know if you need any help in getting started.
Check our example dissertations to get an idea of how to structure your dissertation .
You can review step by step guide on how to write your dissertation here.
View our free dissertation topics database.
Computer Engineering Dissertation Topics
Computers are the greatest innovation of the modern era and have done wonders for mankind. There is only one language that computers understand; the binary. But there are various high-level coding languages that even computers do not understand and therefore use a compiler for translation.
Computing refers to computer hardware or software coding development technology and covers all aspects of computer technologies. It is the practical and scientific study of the implementation of computing information. Computing is also interchangeably known as computer sciences.
A computing engineer or a computer scientist specializes in practical work, the theory of computing, and the design of computational systems. Essentially, it is the study of structure, expression, mechanization, and feasibility of algorithms (logical procedures) that cause processing, communication, representation, access of information, and acquisition in a computer. This area has a wide range of topics, some of which have been listed below:
- Risk calculation in the application and development process.
- Generation of the java application.
- Implementing a behavioural based approach to detect cheating in online games.
- Analysis of coding environment of different applications.
- Identification of different languages used for coding.
- Identification of stake holder’s interest in App development process.
- Role of visualization in complex hierarchal structures of computing.
- Analysing the requirements of Inventory Management Software.
- Development of single-player simulation game.
- Investigation of web teaching aid system.
- Development of online based library management system.
- Implementation of Electronic banking system.
2022 Computing Engineering Dissertation Topics
Topic 1: an investigation of the blockchain's application on the energy sector leading towards electricity production and e-mobility..
Research Aim: This study aims to investigate the applications of blockchain within the energy sector. This study will identify how blockchain can be used to produce electricity from the comfort of home. Moreover, this study aims to introduce the concept of e-mobility through blockchain, according to which blockchain can be used to share the car ride with the other commuters residing at nearby places. Another objective of this research is to develop a framework that could assess blockchain’s use for the consumers staying within a budget and letting them assess how much money they have been spending so far.
Topic 2: Investigating the Issues that Impact Data Security in Cloud-Based Blockchain Technology: An Global Tourism Industry Case Study
Research Aim: This research focuses on a significant shift in trend found in the worldwide tourist business, which is the usage of the cloud for data and services. It attempts to supply the requirements for this implementation owing to the demand for ease, saving, and improved service providing. Furthermore, it will also focus on the limits of traditional blockchain technology primitives and assess control models. These constraints are related to security issues involving data in a cloud environment in the global tourism industry.
Topic 3: Is Digital Technology overtaking Human Interactions in the Medical Fields? An Examination of the Use of Computational biology and Machine Leaning in Patient Diagnosis and Treatment.
Research Aim: The current study seeks to examine how digital technology is replacing human interactions in the medical industry in the importance of computational biology and machine learning in patient diagnosis and treatment. This study will set forth the theoretical foundations and significance of computational biology and machine learning and will also make recommendations for further enhancement.
Topic 4: Evaluating the use of databases and information retrieval systems in the perspective of the United States National security policy.
Research Aim: The current study aims to evaluate the use of databases and information retrieval systems from the perspective of United States national security policy. This study addresses the databases and information retrieval system to provide a clear understanding. It will also focus on specific elements d criteria in the united state’s national security and highlights the benefits and drawbacks of employing them to enhance national security strategy in the united states.
Topic 5: Development of growing infusion of computer technology in the area of medicine- examining NHS policies.
Research Aim: This research aims to examine the development of the growing infusion of computer technology in the area of medicine by evaluating existing NHS policy. The study will provide a theoretical framework for the application of computer science technologies in medicine and will also set out the benefits of using contemporary computer technology as well as analyse the drawbacks that have occurred as a result of the growth of this new technology in this field. It will also focus on the policies employed by NHS to assist the development of technologies in the UK healthcare sector.
Computer Engineering Dissertation Topics for 2021
A 3-d visualization system for ultrasound images.
Research Aim: This research will focus on the visualization of 3-D ultrasound images and their medical therapy benefits.
Reliable and realistic study of remote communication systems in telephony and multipath faded systems
Research Aim: This research’s primary emphasis is on telephony’s practical implementation in a remote communication system.
Establishing a Neural Network Device
Research Aim: In terms of energy efficiency, the human brain is much greater than any modern supercomputer. A whole new generation of energy-efficient, brain-like computers is being designed for this study.
Methods for Artifact EEG Brain function study, caused by sugar, salt, fat, and their replacements
Research Aim: This study relies on the procedure for calculating sweetness taste is developed and validated. Part of the project includes modern electrode technologies to capture the purest possible brain signal from EEG equipment.
Find 100s of dissertation topics in your other academic subjects in our free topics database.
The impact of Covid-19 on tech spends in 2021
Research Aim: This research aims to study the impact of Covid-19 on tech spends in 2021.
Analysis of information system built for e-learning
Research Aim: This research aims to analyze the information system built for e-learning
Advantages and disadvantages of an information system
Research Aim: This research aims to address the advantages and disadvantages of an information system.
Covid-19 Computer Engineering Research Topics
Research to study the effects of coronavirus on it industries.
Research Aim: This research will focus on the impacts of COVID-19 on the growth of IT industries highlighting the issues responsible for it and the possible solutions to overcome them.
Research to identify the impact of Coronavirus on the computer science research community
Research Aim: Coronavirus has infected thousands of people and has been responsible for the deaths of several innocent people worldwide. This study will focus on identifying the effects of this pandemic on the computer science research community.
Research to study the impacts of COVID-19 on tech spends in 2021
Research Aim: As a result of COVID-19, the economy of the entire world has been disrupted. The purpose of this research is to know the tech expenditures after COVID-19 became widespread. How are the tech industries dealing with the challenging situation created by COVID-19?
Research to identify the contribution of computer science to control the spread of Coronavirus pandemic
Research Aim: This research aims at identifying the contributions and efforts made by computer engineers to control the pandemic. What is the role of computer scientists during the pandemic?
Research to identify the unemployment of computer engineers after the Coronavirus pandemic
Research Aim: This research will focus on identifying the increased unemployment issues raised after the COVID-19 pandemic and finding out the possible solutions to overcome the reduced unemployment of computer engineers.
Hardware, Network and Security Dissertation Topics
Network security is very crucial for any organisation. It is dependent upon a well-managed network through the implementation of policies drafted by network administrators to manage the access of the organisational information. Network security provides stability, safety, integrity, reliability, and utility of data and network.
It works efficiently with the latest hardware equipment and updated software. Network security offers many advantages to businesses, such as protection against any disruption to keep employees motivated, energetic, regular, and productive.
In certain instances, a virus may break into the network security. However, the network administrator generally uses an anti-virus program to prevent this sort of attack.
Therefore, it will be fair to say that network security plays a vital role in maintaining a business’s reputation and operations which is the most important asset to any organisation. Below is a list of topics that you can base your dissertation on:
- Performance analysis of transmission control protocol over Ethernet LAN.
- Gateway usage for the intrusion detection system.
- Impact of security machinimas in online transactions.
- Investigation of smart card specification.
- Importance of router placement in the network.
- Level of customer’s trust in E-banking.
- Role of antivirus in a shared network.
- Application of database technologies for data network management.
- Network worm: A headache to networking.
- Implementation of various tools in programming language.
- Study of retroactive data structures.
- Role of Voice over Internet Protocol over Ethernet LAN.
- The usefulness of data transfer security over Wi-Fi Network.
- Influence of signal strength of Wi-Fi upon data transfer.
- Analysis of tree inclusion complexities.
- Analysis of the implementation of the set procedure.
- Analysis of the application of programming tools.
- Implementation of File Sharing System in Network.
- Study of virus behaviours in the secured programming environment.
- Investigation of issues of user’s security and data protection over the network.
- Benefits of network security to customers.
- Improvements of mobile data service for future usage.
- Study of Asymmetry k-center variant.
- Analysis of issues in emerging 4G networks.
- Role of dynamic proxies in a mobile environment to support Remote method Invocation.
Software, Programming and Algorithm Dissertation Topics
In layman language, the software is collectively known as the “combination of operating information and all the programs that are being used by the computer.” It is a set of instructions to direct computers to perform a specific task depending upon thususer’s instructions.
The software can be written in both high and low-level languages. Low-level language is also known as machine code and is faster because it doesn’t require any compiler and directly communicates with the computer. A high-level language is pretty similar to a human language, and therefore can be easily understood by the developers. High-level language requires the compiler to translate commands to the computer.
Programming and algorithms can be termed as commands given to the computer to perform actions. Programming leads to executable programs from a computing problem and involves developing, generating, and analysing algorithms. Algorithms refer to an act done involving a step-by-step process to solve a problem. It is a set of logic written in software.
There are two types of software; operating software that helps in operation and system software necessary to run a system. Operating software can be rewritten and changed according to demand, but system software cannot be altered. If developers require any alterations, they would have to develop new software.
There are various topics that can be considered for research dissertation purposes under this theme, a list of which is given below.
- Application of algorithms.
- Importance of approximation algorithms on graphs.
- Critical analysis of data structures on trees.
- Evaluation and implementation of new algorithms.
- System software: A link to communicate hardware.
- Difference between binary dispatching and multiple dispatching.
- Analysis of plan sweep techniques.
- Investigation of software support to drivers of devices.
- Intelligent interface for database systems.
- Analysis of function and types of union-find.
- The usefulness of different coding languages.
- Application of basic hardware knowledge and math skills.
- Analysis of the design of converter based on new moduli.
- Analysis of information travelling via software.
- Evaluation and implementation of heuristic algorithms.
- Development of applications using Java.
- Analysis of fault tolerance in a network by using simulation.
- Importance of system software for computers.
- Effects of larger integer module operations.
- Consequences of wrong commands in coding.
- Investigation of the coding language of system software.
- Analysis of feasibility environment of platform.
- Evaluation of heuristic algorithms for generating clusters.
- Critical analysis of fixed control variable.
- Analysis of design of converter with large dynamic range.
- Ways to recover corrupted software.
- Analysis of fault tolerance of sorting network.
- Analysis of the difference between LAN and WAN.
- Development of an algorithm for a one-way hashing system.
- Relation between dynamic access and fixed values.
- Importance of right language selection while coding.
- Study of optimization problems.
- Analysis of security frameworks for web services.
- Investigating algorithms techniques.
- Partial persistence of algorithms vs others.
- Study of time and space problems of algorithmic functions.
- Effects of linear and logarithmic factors over programming.
- Discussion about union-find with deletion.
- Importance of data structure for bridge core problems.
- Consequences of fault in interconnected networks.
- Difference between rooted and unrooted tree.
Information Systems Dissertation Topics
Information systems refer to a group of people and computers that are being used for the interpretation of all kinds of information. Computer-based information systems are a very interesting topic for research. It includes all information regarding decision making, management support, and operations and can also be used to access the database.
There is an obvious difference between computer systems, information systems, and business processes. The information system provides the tools to manage businesses successfully.
An information system can be said to be a workstation where humans and machines work together towards the success of a business. One such example is Wal-Mart. The company is entirely based on information systems and has connected its suppliers, vendors, customers and together.
It deals with a large number of data and consists of hardware, software, network, and telecommunications of the operation. Below is a list of research topics in the field of information systems for you to base your dissertation on:
- Analysis of challenges in building information systems for any organisation.
- Impact of cyberinfrastructure on the customer.
- Role of information system in scientific innovations.
- The usefulness of information systems for businesses.
- Advantages of information systems.
- Access to information systems by employees anywhere in the world.
- Preparation of a database management system.
- Analysis and solution of database management systems.
- Study of support of information system to hardware.
- Managing information systems of big stores, The case of Walmart.
- Analysis of information system built for E-learning.
- Critical analysis of the changing nature of the web.
- Role of information system in decision making of disruptions.
- Examine customer response through the information system.
- Investigate the impact of a virus in the network
- Relationship between I.T education and an organization.
- Role of information system in global warming.
- Investigate the reason for adopting green information systems.
- Analysis of the between social networks and information systems.
- Role of information system in dealing with complex business problems.
Important Notes:
As a computing engineering student looking to get good grades, it is essential to develop new ideas and experiment with existing computing engineering theories – i.e., to add value and interest in your research topic.
The field of computing engineering is vast and interrelated to so many other academic disciplines like civil engineering , finance , construction , law , healthcare , mental health , artificial intelligence , tourism , physiotherapy , sociology , management , marketing and nursing . That is why it is imperative to create a project management dissertation topic that is articular, sound, and actually solves a practical problem that may be rampant in the field.
We can’t stress how important it is to develop a logical research topic; it is the basis of your entire research. There are several significant downfalls to getting your topic wrong; your supervisor may not be interested in working on it, the topic has no academic creditability, the research may not make logical sense, there is a possibility that the study is not viable.
This impacts your time and efforts in writing your dissertation as you may end up in the cycle of rejection at the very initial stage of the dissertation. That is why we recommend reviewing existing research to develop a topic, taking advice from your supervisor, and even asking for help in this particular stage of your dissertation.
While developing a research topic, keeping our advice in mind will allow you to pick one of the best computing engineering dissertation topics that fulfill your requirement of writing a research paper and add to the body of knowledge.
Therefore, it is recommended that when finalizing your dissertation topic, you read recently published literature to identify gaps in the research that you may help fill.
Remember- dissertation topics need to be unique, solve an identified problem, be logical, and be practically implemented. Take a look at some of our sample computing engineering dissertation topics to get an idea for your own dissertation.
How to Structure your Dissertation on Computing Engineering
A well-structured dissertation can help students to achieve a high overall academic grade.
- A Title Page
- Acknowledgements
- Declaration
- Abstract: A summary of the research completed
- Table of Contents
- Introduction : This chapter includes the project rationale, research background, key research aims and objectives, and the research problems to be addressed. An outline of the structure of a dissertation can also be added to this chapter.
- Literature Review : This chapter presents relevant theories and frameworks by analysing published and unpublished literature available on the chosen research topic, in light of research questions to be addressed. The purpose is to highlight and discuss the relative weaknesses and strengths of the selected research area whilst identifying any research gaps. Break down of the topic, and key terms can have a positive impact on your dissertation and your tutor.
- Methodology: The data collection and analysis methods and techniques employed by the researcher are presented in the Methodology chapter which usually includes research design, research philosophy, research limitations, code of conduct, ethical consideration, data collection methods and data analysis strategy .
- Findings and Analysis: Findings of the research are analysed in detail under the Findings and Analysis chapter. All key findings/results are outlined in this chapter without interpreting the data or drawing any conclusions. It can be useful to include graphs , charts, and tables in this chapter to identify meaningful trends and relationships.
- Discussion and Conclusion: The researcher presents his interpretation of results in this chapter, and states whether the research hypothesis has been verified or not. An essential aspect of this section of the paper is to draw a linkage between the results and evidence from the literature. Recommendations with regards to implications of the findings and directions for the future may also be provided. Finally, a summary of the overall research, along with final judgments, opinions, and comments, must be included in the form of suggestions for improvement.
- References: This should be completed in accordance with your University’s requirements
- Bibliography
- Appendices: Any additional information, diagrams, graphs that were used to complete the dissertation but not part of the dissertation should be included in the Appendices chapter. Essentially, the purpose is to expand the information/data.
About ResearchProspect Ltd
ResearchProspect is a UK-based academic writing service that provides help with Dissertation Proposal Writing , Ph.D. Proposal Writing , Dissertation Writing , Dissertation Editing and Improvement .
For further assistance with your dissertation, take a look at our full dissertation writing service .
Our team of writers is highly qualified. Our writers are experts in their respective fields. They have been working in the industry for a long time. Thus they are aware of the issues and the trends of the industry they are working in.
Need more Topics.?
Free Dissertation Topic
Phone Number
Academic Level Select Academic Level Undergraduate Graduate PHD
Academic Subject
Area of Research
Frequently Asked Questions
How to find dissertation topics about computing engineering.
To find computing engineering dissertation topics:
- Explore emerging technologies.
- Investigate industry challenges.
- Review recent research papers.
- Consider AI, cybersecurity, IoT.
- Brainstorm software/hardware innovations.
- Select a topic aligning with your passion and career aspirations.
You May Also Like
If you have aimed to write your dissertation about leadership and direly looking for some exceptional leadership research topics, do not worry; we have got your back.
Need interesting and manageable Effects of Social Media on the Youth dissertation topics? Here are the trending Effects of Social Media on the Youth dissertation titles so you can choose the most suitable one.
The topic of dementia nursing is still unfamiliar to many healthcare professionals and individuals despite the availability of so many resources online. Despite the fact that it is one of the most fulfilling careers.
USEFUL LINKS
LEARNING RESOURCES

COMPANY DETAILS

- How It Works
share this!
April 26, 2024
This article has been reviewed according to Science X's editorial process and policies . Editors have highlighted the following attributes while ensuring the content's credibility:
fact-checked
Researchers propose framework for future network systems
by Engineering
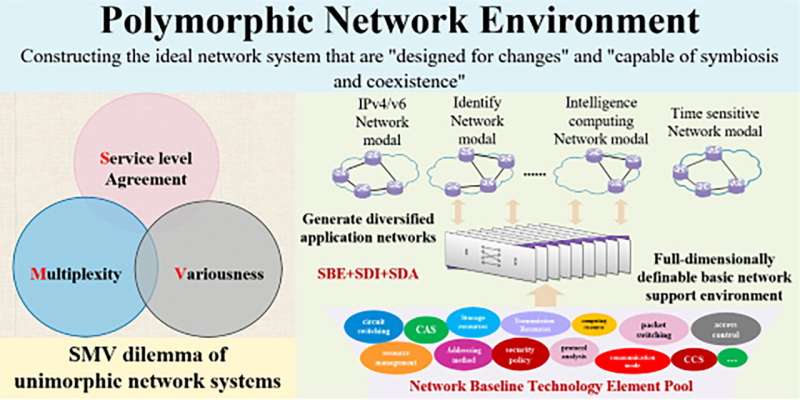
In a new study published in Engineering , Wu Jiangxing's research team unveils a theoretical framework that could revolutionize the landscape of network systems and architectures.
The paper titled "Theoretical Framework for a Polymorphic Network Environment," addresses a fundamental challenge in network design—achieving global scalability while accommodating the diverse needs of evolving services.
For decades, the quest for an ideal network capable of seamlessly scaling across various dimensions has remained elusive. The team, however, has identified a critical barrier known as the "impossible service-level agreement (S), multiplexity (M), and variousness (V) triangle" dilemma, which highlights the inherent limitations of traditional unimorphic network systems.
These systems struggle to adapt to the growing complexity of services and application scenarios while maintaining global scalability throughout the network's life cycle.
To overcome this challenge, the researchers propose a paradigm shift in network development—an approach they term the polymorphic network environment (PNE). At the core of this framework lies the separation of application network systems from the underlying infrastructure environment.
By leveraging core technologies such as network elementization and dynamic resource aggregation, the PNE enables the creation of a versatile "network of networks" capable of accommodating diverse service requirements.
Through extensive theoretical analysis and environment testing, the team demonstrates the viability of the PNE model. Results indicate that the framework not only supports multiple application network modalities simultaneously but also aligns with technical and economic constraints, thus paving the way for scalable and adaptable network architectures.
This study challenges the conventional wisdom surrounding network design and offers a promising path towards achieving the elusive goal of an ideal network system. The PNE not only addresses the limitations of current approaches but also lays the foundation for a more flexible and resilient network infrastructure.
Looking ahead, the team aims to further refine the PNE framework and explore key techniques such as elemental extraction and flexible resource scheduling. By doing so, they seek to unlock the full potential of polymorphic network systems and usher in a new era of connectivity and innovation.
The publication of this paper marks a significant milestone in the field of network engineering, with implications that extend far beyond academia. As society becomes increasingly reliant on interconnected systems, the development of scalable and adaptable networks is more crucial than ever. With the PNE, researchers are one step closer to realizing this vision.
Explore further
Feedback to editors

Proof of concept study shows path to easier recycling of solar modules
14 hours ago

New circuit boards can be repeatedly recycled
15 hours ago

Researchers develop an automated benchmark for language-based task planners

Built-in bionic computing: Researchers develop method to control pneumatic artificial muscles

Custom-made catalyst leads to longer-lasting and more sustainable green hydrogen production
16 hours ago

Researchers outline path forward for tandem solar cells
17 hours ago

Researcher develop high-performance amorphous p-type oxide semiconductor
18 hours ago

Scientists create new atomic clock that is both ultra-precise and sturdy
A framework to compare lithium battery testing data and results during operation
21 hours ago

New approach could make reusing captured carbon far cheaper, less energy-intensive
Apr 26, 2024
Related Stories

Technological breakthrough may be key to overcoming current 5G network limitations
Aug 8, 2023

National roaming can increase resilience of Dutch mobile networks
Apr 17, 2024

Building a template for the future 6G network
Oct 1, 2021
A graphical diagnostics tool for high-speed railway internet connectivity
Nov 27, 2023

Researchers offer future 6G network concept
Dec 29, 2021

Researchers use AI to make mobile networks more efficient
Oct 31, 2023
Recommended for you

Study explores why human-inspired machines can be perceived as eerie
Apr 25, 2024

Engineers uncover key to efficient and stable organic solar cells

Adobe's VideoGigaGAN uses AI to make blurry videos sharp and clear
Let us know if there is a problem with our content.
Use this form if you have come across a typo, inaccuracy or would like to send an edit request for the content on this page. For general inquiries, please use our contact form . For general feedback, use the public comments section below (please adhere to guidelines ).
Please select the most appropriate category to facilitate processing of your request
Thank you for taking time to provide your feedback to the editors.
Your feedback is important to us. However, we do not guarantee individual replies due to the high volume of messages.
E-mail the story
Your email address is used only to let the recipient know who sent the email. Neither your address nor the recipient's address will be used for any other purpose. The information you enter will appear in your e-mail message and is not retained by Tech Xplore in any form.
Your Privacy
This site uses cookies to assist with navigation, analyse your use of our services, collect data for ads personalisation and provide content from third parties. By using our site, you acknowledge that you have read and understand our Privacy Policy and Terms of Use .
E-mail newsletter

- [email protected]
- +91-97 91 62 64 69
Research Topics in Computer Networks and Security
A literature review is examined as an intriguing as well as significant work. It is important to follow several guidelines to effectively carry out this process. For conducting a literature review based on the networking research topic, we offer a well-formatted procedures and hints, along with some instances relevant to the latest research areas in the domain of networking:
Procedures for Carrying out a Literature Review
- Specify Your Scope: The research topic or query that you intend to investigate has to be stated in an explicit manner. Extensive research areas are involved in the domain of networking, and not constrained to network security, software-defined networking (SDN), network protocols, and wireless communication.
- Search for Related Literature:
- It is approachable to employ search engines and academic databases, including Google Scholar, ScienceDirect, ACM Digital Library, and IEEE Xplore.
- To expand your exploration, examine most relevant wordings and synonyms, and use particular key terms that align with your chosen topic.
- Screen and Choose Sources:
- For finding papers, which are exactly related to your research query, you need to cover titles and abstracts at the beginning stage.
- To assess the appropriateness, methodology, standard, and discoveries, read the chosen papers in an extensive manner.
- Organize and Classify:
- By means of any categorization like discoveries, methodologies, or subtopics which assists the goals of your review, you should arrange your studies.
- You must outline all the major discoveries of your review. Any gaps, challenges, or concurrences that exist in the research have to be observed.
- Synthesize Discoveries:
- The latest condition of research, developments in the field of the selected topic, and recent patterns must be described.
- In the literature, in which evolving techniques may affect upcoming studies or where there is a requirement for even more exploration, find potential gaps.
- Draft and Revise:
- By adhering to any particular instructions that are suggested by your publication avenue or educational university, you must depict all your discoveries systematically.
- To assure consistency, extensive analysis of the literature, and transparency, review the initial writings.
Instances of Networking Research Topics
- Network Security:
- Current innovations in quantum-resistant cryptography.
- The efficacy of machine learning in the identification and reduction of network assaults.
- Wireless Communication:
- The effect of 5G mechanisms on mobile networks and services.
- Issues and solutions for perfect combination among heterogeneous wireless networks.
- Network Protocols:
- Advancements in transport layer protocols for enhancing the pace and credibility of the internet.
- Enhancement of Protocol for Internet of Things (IoT) devices to improve data transmission and energy effectiveness.
- Software-Defined Networking (SDN):
- The contribution of SDN in improving and automating network arrangements for cloud services.
- In software-defined networks, safety impacts and solutions.
- Edge Computing:
- The part of edge computing in minimizing utilization of bandwidth and latency in IoT-based applications.
- Safety issues and policies for the placements of edge computing.
What are the best topics for a research project related to Computer Network Security?
In the field of Computer Network Security, various topics and areas have emerged in a gradual manner. The following are numerous interesting topics which provide significant possibility for effective studies and also considered as related to the latest research trends:
- Zero Trust Architecture Implementation and Challenges
- Explanation: The concepts of zero Trust framework has to be investigated by considering the issues that are confronted in the conversion from conventional network safety models, and the application of Zero Trust in different industrial scenarios.
- Possible Implication: For tackling general barriers and implementing Zero Trust, this topic can provide perceptions on efficient tactics.
- AI and ML in Cyber Threat Detection and Response
- Explanation : The major aim of this topic is to explore in what way the methods of machine learning (ML) and artificial intelligence (AI) can automate response mechanisms and enhance the identification of cyber hazards.
- Possible Implication : Developments in this research area could exceed human abilities by substantially improving the preciseness and pace of hazard identification and response.
- Blockchain for Network Security
- Explanation : In protecting network interactions and transactions, the implementation of blockchain mechanisms must be analyzed. This is specifically to solve various problems relevant to non-repudiation, authentication, and data morality.
- Possible Implication : This research plan could result in minimization of dependency on centralized trust frameworks due to the creation of decentralized safety approaches.
- Quantum Cryptography and Post-Quantum Cryptography
- Explanation : Consider the realistic application of quantum key distribution (QKD), and the creation of cryptographic methods which are protective from the assaults related to quantum computing.
- Possible Implication : In opposition to the growth of quantum computing, this topic is crucial for future-evident cryptographic safety.
- Privacy-Preserving Technologies in Network Communications
- Explanation : To improve the confidentiality of the users in network interactions, explore protocols and mechanisms, like differential privacy and anonymous routing protocols.
- Possible Implication : In the period of widespread monitoring and data gathering, it could enhance the security of individual confidentiality.
- Securing the Internet of Things (IoT)
- Explanation : By concentrating on secure device provisioning, lightweight cryptographic approaches, and update techniques, the specific safety problems which are caused by IoT networks and devices have to be solved.
- Possible Implication : For assuring the morality and safety of highly extensive IoT placements, this research idea is most significant.
- Software-Defined Networking (SDN) Security
- Explanation : The safety risks that are associated with SDN frameworks should be investigated. In order to protect SDN controllers and the interaction among network devices and controllers, create techniques.
- Possible Implication : It supports the placement of effective and adaptable SDN mechanisms in a secure way.
- 5G Network Security
- Explanation : The safety impacts of 5G mechanisms, as well as the higher assault areas because of the combination of IoT, the safety of network slicing, and edge computing have to be explored.
- Possible Implication : This topic assures that the major framework and services can be facilitated by the future cellular networks in a protective manner.
- Attack Simulation and Penetration Testing Automation
- Explanation : For the simulation of cyber assaults, create automatic techniques and tools. To find risks in network frameworks, carry out penetration testing.
- Possible Implication : Contrary to the evolving cyber hazards, it could result in highly powerful network structures and arrangements.
- Advanced Persistent Threats (APT) Detection and Mitigation
- Explanation : For the violation of network security, the tactics, techniques, and procedures (TTPs) that are utilized by APTs have to be examined. To identify and reduce these hazards, create policies.
- Possible Implication : Resistant to intricate and focused cyber espionage or disruptive actions, the strength of networks can be improved.

Networking Research Topics and Ideas
We understand the importance of finding the right Networking research topics and ideas for both undergraduate and postgraduate students and scholars. At phdprime.com, we are here to assist you in tailoring your Networking research work to meet your specific needs. With over 18 years of experience, we have been supporting scholars with innovative Networking research. Stay connected with phdprime.com to discover more in this field.
- A distributed routing-aware power control scheme for underwater wireless sensor networks
- Energy-optimal routing for electric vehicles using deep reinforcement learning with transformer
- Discovering Lin-Kernighan-Helsgaun heuristic for routing optimization using self-supervised reinforcement learning
- A stochastic formulation of the two-echelon vehicle routing and loading bay reservation problem
- THSI-RP: A two-tier hybrid swarm intelligence based node clustering and multi-hop routing protocol optimization for wireless sensor networks
- Two-dimensional loading in vehicle routing problem with release and due dates
- Routing states transition during oscillatory bursts and attentional selection
- Traffic and fragmentation aware algorithm for routing and spectrum assignment in Elastic Optical Network (EON)
- Interference Aware Joint Power Control and Routing Optimization in Multi-UAV FANETs
- Pickup capacitated vehicle routing problem with three-dimensional loading constraints: Model and algorithms
- Split-demand multi-trip vehicle routing problem with simultaneous pickup and delivery in airport baggage transit
- Computational approaches for solving two-echelon vehicle and UAV routing problems for post-disaster humanitarian operations
- Note: Demonstrating analytics in a low-tech context–truck-routing for solid-waste collection in an Indian metropolis
- Tactical planning for dynamic technician routing and scheduling problems
- Dual-neighborhood iterated local search for routing and wavelength assignment
- A novel routing protocol for underwater wireless sensor networks based on shifted energy efficiency and priority
- Energy Efficient Region based Source Distributed Routing Algorithm for Sink Mobility in Underwater Sensor Network
- Mitigating stochastic uncertainty from weather routing for ships with wind propulsion
- An analysis of the value of optimal routing and signal timing control strategy with connected autonomous vehicles
- Enhanced Fuzzy Logic Zone Stable Election Protocol for Cluster Head Election (E-FLZSEPFCH) and Multipath Routing in wireless sensor networks

Opening Hours
- Mon-Sat 09.00 am – 6.30 pm
- Lunch Time 12.30 pm – 01.30 pm
- Break Time 04.00 pm – 04.30 pm
- 18 years service excellence
- 40+ country reach
- 36+ university mou
- 194+ college mou
- 6000+ happy customers
- 100+ employees
- 240+ writers
- 60+ developers
- 45+ researchers
- 540+ Journal tieup
Payment Options

Our Clients

Social Links

- Terms of Use

Opening Time

Closing Time
- We follow Indian time zone


IMAGES
VIDEO
COMMENTS
2022 Computer Networking Dissertation Topics. Research Aim: The research aims to evaluate the network security issues associated with M2M communication in IoT. Objectives: To evaluate the factors affecting the network security of IoT devices. To determine the methods for increasing data integrity in M2M communication against physical tampering ...
The proposed research topic can be based on securing wireless networks with the help of AAA authentication and WLAN controllers. The use of AAA authentication can be done to set up a login portal for users whilst the WLAN controller can be used for managing all wireless access points connected to the network (Nashwan, 2021).
A computer network is a network of diverse computing hardware linked through different communication technologies to share various resources.The communication links of the network can be either wired (cables) or wireless (radio waves / IR signals).. This page shows you useful information on Computer Network Research Topics, Projects with Source Code, Research Areas, Project Topics, and Tools!!!
Computer Science Research Topics. Computer Science Research Topics are as follows: Using machine learning to detect and prevent cyber attacks. Developing algorithms for optimized resource allocation in cloud computing. Investigating the use of blockchain technology for secure and decentralized data storage. Developing intelligent chatbots for ...
Software defined networking. Network security and also cryptography. Network Function Virtualization. Cognitive computing and also machine learning. Micro services architecture. Adaptive security. Augmented and virtual reality. Cloud networking. Big data analytics in mobile networking.
Dear Mubashir Iqbal, During the SARS-CoV-2 (Covid-19) coronavirus pandemic, the scale of cybercriminal and hacking activities on the Internet increased. Therefore, I propose the following research ...
Computer networks are a. system of i nterconnected computers for the purpose of. sharing digital information. The computer network. enables to analyze, organize and disseminate the. information ...
Explore the latest full-text research PDFs, articles, conference papers, preprints and more on COMPUTER NETWORKING. Find methods information, sources, references or conduct a literature review on ...
If you've landed on this post, chances are you're looking for a computer science-related research topic, but aren't sure where to start. Here, we'll explore a variety of CompSci & IT-related research ideas and topic thought-starters, including algorithms, AI, networking, database systems, UX, information security and software ...
A group of computers sharing resources that are available on or offered by network nodes is known as a computer network. Via Digital links, Computers communicate with one another using standard ...
Thus, inter-networking and uncertainty management are important challenges of emerging networking that deserve attention from the research community. We describe research that touch on both topics. First, we consider a model of data-optical inter-networking, where routes connecting end-points in data domains are concatenation of segments in the ...
Research areas: Interpretability of AI systems, Fairness in AI systems, Computer vision. Independen Work Topics: Constructing a new method to explain a model / create an interpretable by design model. Analyzing a current model / dataset to understand bias within the model/dataset.
151+ Research Proposal Topics: Category Wise. Science and Technology. Health and Medicine. Social Sciences. Education. Business and Economics. Environment and Sustainability. Psychology and Behavior. Political Science and International Relations.
Research idea report (optional, 3 pages): 10%; PREREQUISITES: Recommended: CS 340 or equivalent networking course Classes, Textbook, and other readings There will be no textbook for this class. A key part of the class will be to review and discuss networking research papers.
Fidelity or Li-Fi [2], is an emerging piece of technology that uses Visible Light Communication (VLC) technology. instead of radio wav es to send data as a remedy to these shortcomings. Compared ...
Characteristic Measure. This paper aims to study the Countermeasures of big data security management in the prevention and control of computer network crime in the absence of relevant legislation and judicial practice. Starting from the concepts and definitions of computer crime and network crime, this paper puts forward the comparison matrix ...
Criminal Law. Cyber Security Future Research Topics. Developing more effective methods for detecting and responding to cyber attacks. Investigating the role of social media in cyber security. Examining the impact of cloud computing on cyber security. Investigating the security implications of the Internet of Things.
Software Defined Networking. -Control plane and also Data plane separation. -Multi tenants also in the Datacenter. -5G technology. M2M Communications in IoT. Latest Research Topics in Computer Networks. Network controller also for 3G/4G/5G mobile and wireless networks. Genetic Algorithms also in network routing. Ultra wide band networking.
In the domain of computer networks, there are several areas that are progressing in contemporary years. The following are numerous regions that are expected to persist or become crucial points of study in computer networks: 6G Wireless Communication; Research Area: Generally, study into 6G technology will obtain speed along with 5G ...
Research proposal examples. Writing a research proposal can be quite challenging, but a good starting point could be to look at some examples. We've included a few for you below. Example research proposal #1: "A Conceptual Framework for Scheduling Constraint Management" Example research proposal #2: "Medical Students as Mediators of ...
2022 Computing Engineering Dissertation Topics. Topic 1: An investigation of the blockchain's application on the energy sector leading towards electricity production and e-mobility. Research Aim: This study aims to investigate the applications of blockchain within the energy sector.
International Research Journal of Modernization in Engineering Technology and Science Volume:03/Issue:07/July-2021 Impact Factor- 5.354 www.irjmets.com ... A computer network is merely computers connected together through wires that permit them to share data or devices like hard drives, CD-ROMs, fax modems, printers, etc. Fig 1 provides an ...
These systems struggle to adapt to the growing complexity of services and application scenarios while maintaining global scalability throughout the network's life cycle. To overcome this challenge, the researchers propose a paradigm shift in network development—an approach they term the polymorphic network environment (PNE). At the core of ...
Instances of Networking Research Topics. Network Security: Current innovations in quantum-resistant cryptography. The efficacy of machine learning in the identification and reduction of network assaults. Wireless Communication: The effect of 5G mechanisms on mobile networks and services.