
Assigning Service Principals to Groups and Roles with the Azure CLI
The more I use Azure the more often I find myself needing to assign various managed identities / service principals to various groups and roles, and while that can be done in the Portal, it's cumbersome and I'd prefer to automate it.
So in this post I'll sharing a few Azure CLI commands that should prove useful whenever you're configuring Service Principals.
Getting a service principal's object id
Suppose you know the name of the service principal, but not the "object id", which is required for assigning it to groups and roles. You can use a filter with the az ad sp list command to find that service principal and then a query to pick out just the object id.
Note that you should avoid trying to use the query parameter to find the matching name, as that will likely not find it as it only applies to the first page of results .
Note that the object id is different from the app id. If you do need the app id for any reason you just need to change the query parameter:
Adding to a group
Suppose we want to add the service principal to a group. We need the group id to do that, and if we need to look it up, we can do so with the az ad group list command and using a filter .
Then the az ad group member add command allows us to add the object id of our service principal to the group.
Creating a role assignment
If we want to create a role assignment, then as well as knowing the user we're assigning the role to and the name of the role, we also need to provide a " scope " for that to apply to. This is typically a long / delimited path to an Azure resource. So for a KeyVault it might look like this:
You can of course construct this string yourself, but actually this is quite often just the "ID" of the resource as returned by the Azure CLI. So we could get the above value with the following command:
And now that we have the scope, we can simply use the az role assignment create to assign the role to our service principal, and we can pass the role name directly (in this example it's "Key Vault Administrator"):
Hope this proves useful to you.
.webp)
Using the Azure CLI To Update and Manage User Permissions
The Azure CLI is a great tool for scripting updates to user permissions. In this guide, we'll walk through the basics of roles and groups and the common commands.

If you need to make user permission updates in an automated way, the Azure CLI can be a great option. In this article, we will be outlining the two main sources of user permissions, roles and groups, and how they intersect.
With a combination of roles and groups, you can maintain granular permissions across many different projects while adhering to the principle of least privilege .
Understanding Roles with Azure RBAC
Azure roles are a flexible way to designate user permissions. With Azure RBAC (role-based access control), you can unlock access to certain resources and actions by assigning a user to a certain role, which comes with an accompanying set of permissions.
These are some examples of common built-in roles:
- Contributor: Can create and manage Azure resources
- Owner: Access to all resources and can extend access to others
- Reader: Can view only existing Azure resources
- User Access Administrator: Can manage access to Azure resources
You can narrow access further by assigning a user with a role in relation to a specific scope (e.g. resource group, application id, etc.). If you need a unique combination of permissions and expect to have similar use cases in the future, you can also create custom roles by providing either a JSON role definition file or a PSRoleDefinition object as input.

Assigning Roles with the Azure CLI
You will likely need to update someone’s role if they are new to your organization or have been assigned to a new project; or inversely, if they are leaving or no longer need access. Here are the steps for making these changes with the Azure CLI.
Adding a Role to a User
To assign a role to a user in Azure, you can use the “ az role assignment create ” command. You have to specify three components, the assignee, the role, and the resource groups or scope of access. In the following example, we’re assigning Reader access (role definition) to user John Smith for the scope of a certain resource group.
Removing a Role from a User
Next, to remove the role from the same user, we would use the “ az role assignment delete ” command. This command uses the exact same parameters:
These commands should enable you to make these role updates manually, or script a repeatable workflow for new employees or new projects.
Understanding Groups in Azure
In GCP or AWS, Identify Access Management (IAM) groups are a way to extend access and authorization services/APIs to a team. Groups in Azure serve the same purpose, but Azure is slightly different in that groups are created directly using Azure’s Active Directory (AD).
You can create a new group using the command “ az ad group create ” , and specify a display name and a mail nickname. Here’s an example:
Management of IAM groups in Azure involves the same kinds of tasks you would perform in typical user groups, whether it’s adding or deleting individual users, giving them specific levels of IAM permissions, or managing groups of users as a whole, among many others.
For example, you can assign a group with a certain role for a certain scope or resource group. To do this, you’ll first need to get the object ID for the group using this command:
The object ID will be a string of numbers in this format:
“xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx”
Now that you have the group ID, you can use the “ az role assignment create ” command to assign a role to that group:
The combination of user roles and group roles allows for organizations to have a flexible and secure solution for permissions as your company grows or projects change.

Adding or Removing a Users to Groups
If you want to add a user to a group, you’ll need to run the “ az ad group member add ” command. You will need to plug in values for a group parameter (either the specific group id or display name) and a member-id parameter.
Here is an example of that command:
Removing a member from a group uses the same parameters, and uses the “ az ad group member remove ” command instead:
You can also use the same parameters with the “ az ad group member check ” command to check whether the member was removed from the group.
Automate Permission Updates with Blink
Most likely, as your organization grows, changing and updating permissions and policies will take up more time. Instead of having to look up the specific command for each of these actions, you could use a low-code tool like Blink to handle tasks like this in a couple clicks.
Get started with Blink today to see how easy automation can be.
Automate your security operations everywhere.
Blink is secure, decentralized, and cloud-native. Get modern cloud and security operations today.

Verschaeve Dries
Cloud solution architect.
- [email protected]
- www.vddesign.be
- driesverschaeve
- dVerschaeve
- @driesverschaeve
Add and remove Azure AD role assignments using Azure CLI
For a customer, I recently needed to create a bash script that prepared their Azure environment for Terraform. Amongst Azure resources, the script also created service principals for Azure DevOps pipelines that would run Terraform. The Terraform code in Azure DevOps included the creation/destruction of Azure AD groups using the AzureAD provider. The Terraform documentation for managing groups with the azuread provider states that the service principal needs to be a member of the ‘User Account Administrator’ role in Azure AD to be able to delete Terraform created groups.
The bash script was using Azure CLI to create the different resources in Azure. I intended to use the “az role assignment create” command to setup the necessary permissions on the Service Principal, however I quickly discovered this was not possible inside Azure CLI for Azure Active Directory Roles and needed to find a solution as PowerShell was not an option.
Microsoft Graph API
After some research, I discovered in the Microsoft Graph Beta API that you can assign custom roles. The web page itself documented the needed endpoints and parameters, but did not include examples on how to use them. The web page itself can be found here: Assign custom admin roles using the Microsoft Graph API in Azure Active Directory
Within Azure CLI, you can execute rest methods using the ‘az rest’ command. So I embarked to assign the required permissions using this command inside my script. Let me guide you through the different steps to achieve this.
First, let’s start to retrieve a list of roles inside Azure Active Directory. So start up a Linux terminal where Azure CLI is installed and login into Azure using ‘az login –use-device-code’, ensure you log in using an account which has the necessary permissions to change role memberships.
Once logged in, we can execute the following bash command to retrieve our Azure AD roles:
Upon completion of the commands, you get a JSON object which contains activated AD roles in Azure AD:
JSON format is fine for a human eye to read (when not too complex). However when we want to use a value like the ID to actually grant a role assignment, we need to be able to parse the JSON file. The tool JQ is able to slice, filter, map and transform JSON, so we are going to use this to parse our JSON response from the Graph API. Ensure it’s installed, for an Ubuntu based distribution you can install it using sudo apt-get install jq
To filter out the displayName, we need to pipe our JSON output into jq:
Because our roles are returned in a value array by ‘az rest’, we first need to step into the value array with .value[]. Afterwards, we ask for the displayName (.displayName) of each entry and instruct JQ to output in raw format (-r).
Add Role Assignment
When we look at the Microsoft documentation to add a role assignment towards a user, the Microsoft Graph API expects the following parameters:
- PrincipalID: the object ID of the user we want to add to a role group, this is the GUID of the Azure AD user
- roleDefinitionId: the definition ID of the role we want to assign. This is the ID of the directory role which we retrieved in very first rest command of this article.
- directoryScopId: an optional scope for the role assignment. You can provide this if you need to limit the role assignment towards a specific administrative unit.
We can use Azure CLI commands and the ‘az rest’ methods to retrieve these values. To retrieve the GUID of the Azure AD user, we use the standard ‘az ad user list’ command and store the objectID parameter in a bash variable:
I started the article with a list of activated directory roles in Azure AD. To retrieve the role definition ID from this list, we will need to filter our results. With JQ we can further filter our JSON results to get the ID of a specific role. For example, the following command will only provide the information of the “Global Administrator” role:
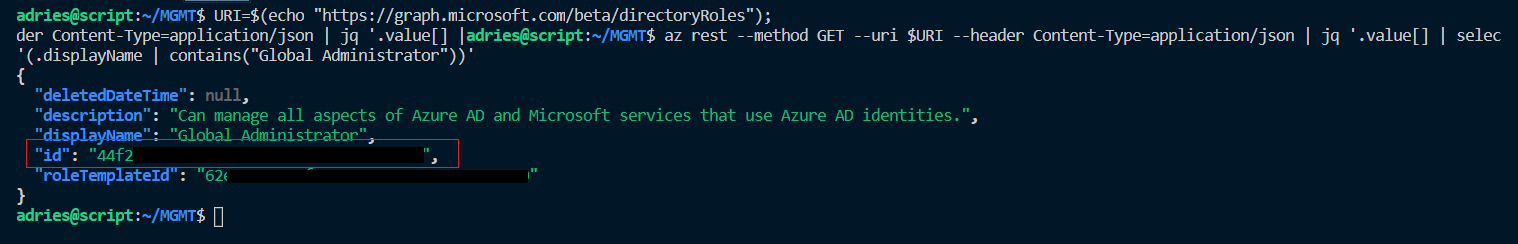
JQ by default outputs JSON, so we can pipe it towards another JQ instance to retrieve the ID of the role in a raw format (-r):
Now all we need to do on the roleDefinitionId is to refactor our commands to make it more generic and use variables. Our goal is to use this in an script so we want to avoid hard coding names like the ‘Global Administrator’ name inside our code. JQ supports input arguments (–arg) which present themselves as variables that can be used in filter statements. For example: when we specify the displayName argument, the value can be used inside our select statement using $displayName. Let’s refactor our code to:
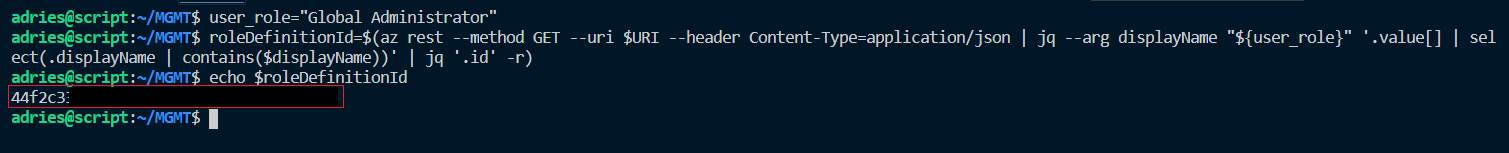
We now have all the information required to create a role assignment using the roleAssignments endpoint. To provide the Graph API the required information, we need to pass our information as a JSON object into the body of our API call. The API expects the following JSON structure:
We can use JQ to construct the expected body where we pass the information into our JQ statement using arguments.
All we have to do now is to refactor our code and use our variables in a post method towards the Graph API endpoint:
On success, you get the role assignment information back in JSON format:
Remove Role Assignment
Now that we have seen how to add a role assignment using Azure CLI commands, let’s have a quick look how to remove them again. According to the Microsoft documentation, we can use the following Graph API endpoint to remove a role assignment:
The documentation is not that extensive, but the Graph API expects that you pass the role assignment ID in the URL using a DELETE action. To do this, we first need to retrieve the role assignment ID, so back to our Linux terminal.
We already know that we can retrieve the different role assignments by making a GET call towards the roleAssignments endpoint, however we need to pass in a filter to retrieve only the role assignments for our user. So we filter on the principal ID using a query string filter and pass in the principalId of the user which we already fetched in a previous step:
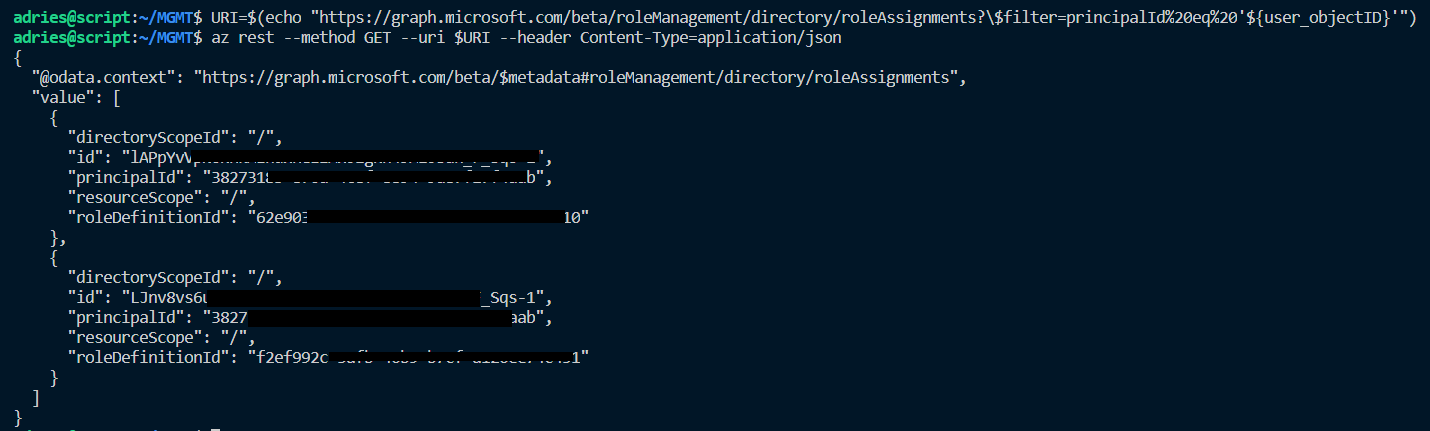
The result is a list of all role assignments the user has and requires to be filtered so that we can have the ID attribute of the role assignment we want to remove (‘Global Administrator’ in this case). The main caveat here is that the roleDefinitionId on the user role assignment list does not match the ID we get from the directoryRoles endpoint, instead it enlists the roleTemplateId:
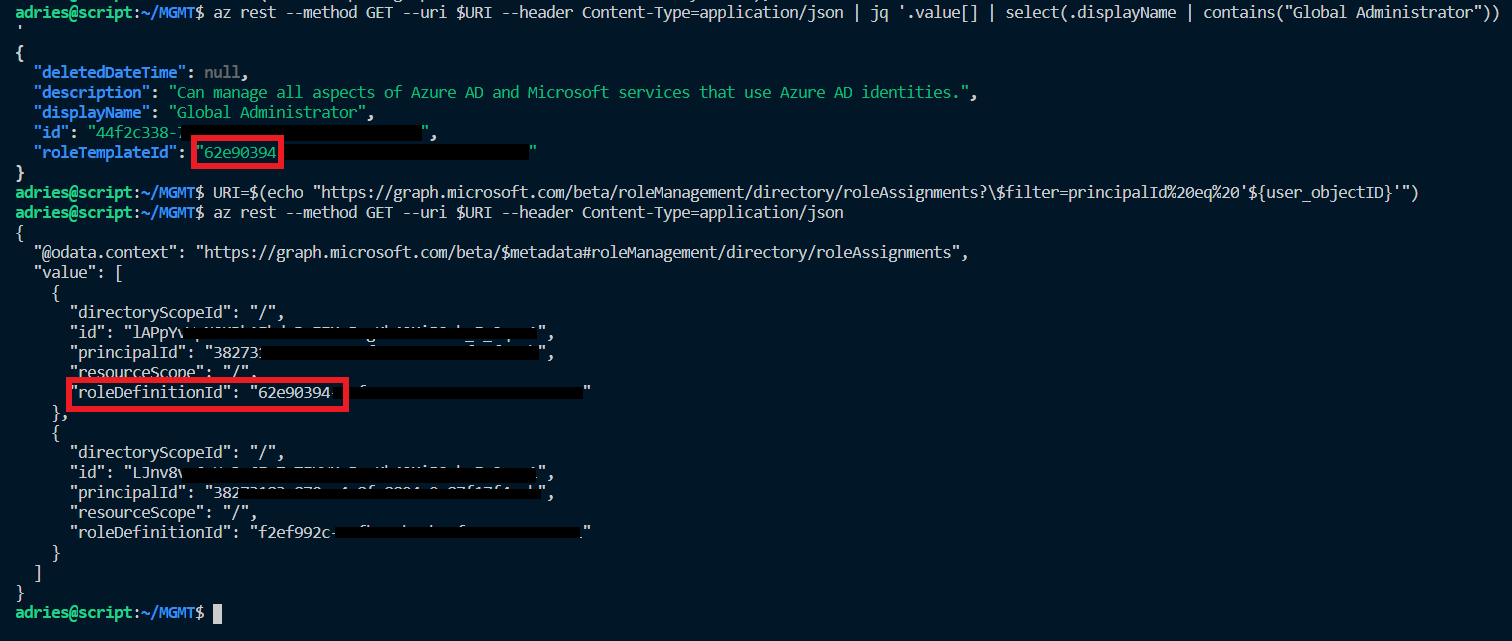
So when we construct our filter for the ‘Global Administrator’ role, we need to pass in the roleTemplateId. Which we don’t yet have at this point, so we need to retrieve it first using the following code:
Afterwards, we can filter our roleAssignments for our user and store the resulting ID in a variable:
Finally, we remove the role assignment by calling the Graph API:
Note: upon success, the command does not return a result. So if you want to check out the result, you need to go to the Azure AD portal and verify.
I’ve combined all the principles off this article into a Bash script that is hosted on my Github repository changeRoleassignment.sh . The script works with input parameters and supports both adding a role assignment and removing a role assignment. Expected parameters are:
- Action (Mandatory, possible values: add or remove)
- User Principal Name (Mandatory)
- Role Assignment Display Name (Mandatory)
- Scope (Optional)
To add a role assignment for a given user:
To remove a role assignment for a given user:
I hope you can use the learnings of this article to solve some of your automation tasks. For me it was quite challenging as I don’t do bash scripting often. It’s also based on the beta endpoints of the Microsoft Graph API, so documentation was not that extensive, support is limited and it can be modified by Microsoft at any time. During creation of the code, I’ve also noticed errors in the Microsoft documentation. I’ve reported them through a Github issue and was quite pleased that my suggestions were incorporated into the document quite quickly.
Fingers crossed that Azure CLI will support adding Azure AD role assignments in the future like it’s the case with PowerShell, until then feel free to use the knowledge and script of this article.
Share this post:
- Career Model
- Proactive Mentorship
- Productivity
- Review Model
- Work:Life Balance
- 3D Printing
- Announcements
- Conferences
How to find all the Azure Built-In Roles for Azure RBAC with Azure CLI, PowerShell, Docs, or AzAdvertizer
Here are a bunch of ways you can find which roles are built into Azure. This will come in super handy when you need to assign a role to a service principal or user with Azure CLI commands like this:
- Query the big honking json
- Query all, but only return Name and Id in a nice table
- Filter by name contains:
This one filters for roles with “Map” in the name:

Azure PowerShell
https://docs.microsoft.com/en-us/powershell/module/az.resources/get-azroledefinition?view=azps-3.8.0
This page has all the built in roles: https://docs.microsoft.com/azure/role-based-access-control/built-in-roles
AzAdvertizer
Just found this site today by Julian Hayward. It’s a great way to find roles
https://www.azadvertizer.net/azrolesadvertizer_all.html

Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
What is the default RBAC scope used when assigning a role in Azure with the CLI?
This is the documentation for the az role assignment create command: https://docs.microsoft.com/en-us/cli/azure/role/assignment?view=azure-cli-latest#az-role-assignment-create
--score is an optional parameter. This is what the documentation says about it:
Scope at which the role assignment or definition applies to, e.g., /subscriptions/0b1f6471-1bf0-4dda-aec3-111122223333, /subscriptions/0b1f6471-1bf0-4dda-aec3-111122223333/resourceGroups/myGroup, or /subscriptions/0b1f6471-1bf0-4dda-aec3-111122223333/resourceGroups/myGroup/providers/Microsoft.Compute/virtualMachines/myVM.
As you can see, it doesn't say what the default value for this parameter is. I can't find it anywhere, so I found myself forced to ask here.
- I can't select my own answer as the correct one because I have to wait 2 days, but that's the correct answer anyways. – Adrian Jan 22, 2022 at 4:25
https://docs.microsoft.com/en-us/azure/role-based-access-control/role-assignments-cli#step-4-assign-role
Apparently, when the --scope parameter is not provided its value depends on whether the --resource-group parameter is provided or not. If you provide that parameter, then it's like if you specified the resource group scope. Else, the subscription scope is assumed.
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged azure entra-id azure-cli ..
- The Overflow Blog
- An open-source development paradigm
- Developers get by with a little help from AI: Stack Overflow Knows code...
- Featured on Meta
- Testing a new version of Stack Overflow Jobs
- What deliverables would you like to see out of a working group?
Hot Network Questions
- How exactly does the JWST (James Webb Space Telescope) "see" light from so far away?
- Purpose of async/await in web servers
- Python secrets command-line tool
- Why would you build slow moving vehicles instead of faster ones?
- When travelling to Turkey my passport was scanned and then the immigration official called someone. Why could that be?
- Is there a word that means both "house" and "apartment"?
- What is a "rapid changes in gravitational force"
- Exponentials of truth values
- Is a double 30 amp breaker powering three rooms from a subpanel bad?
- Can a rental agreement state that no guests or parties are allowed?
- Can the subjunctive alone form a conditional's protasis?
- Mad Max is sentenced to the Gulags but gets cast out?
- Series expansion of a given function
- Was the appearance of the sand worms in David Lynch's Dune (1984) completely original to that film?
- Second opinion on PCB design for relay made in Altium
- Is there a technical reason why Datel Action Replay on PC required a card?
- Preserving / fixing class imbalance
- Magento2.4: How to show custom table data using knockoutJS?
- Is it bad style to write x^2, 2^\frac{1}{2} and 2^\sqrt{2}?
- How to create stored procedure in remote server using linked server
- What determines the number of firefox processes?
- Split a number in half, sum it, square it and get the number back
- Calculate the substraction values fields of the nearest point between two points layers
- How to avoid similar solutions?
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Add or edit Azure role assignment conditions using Azure CLI
- 6 contributors
An Azure role assignment condition is an additional check that you can optionally add to your role assignment to provide more fine-grained access control. For example, you can add a condition that requires an object to have a specific tag to read the object. This article describes how to add, edit, list, or delete conditions for your role assignments using Azure CLI.
Prerequisites
For information about the prerequisites to add or edit role assignment conditions, see Conditions prerequisites .
Add a condition
To add a role assignment condition, use az role assignment create . The az role assignment create command includes the following parameters related to conditions.
The following example shows how to assign the Storage Blob Data Reader role with a condition. The condition checks whether container name equals 'blobs-example-container'.
The following shows an example of the output:
Edit a condition
To edit an existing role assignment condition, use az role assignment update and a JSON file as input. The following shows an example JSON file where condition and description are updated. Only the condition , conditionVersion , and description properties can be edited. You must specify all the properties to update the role assignment condition.
Use az role assignment update to update the condition for the role assignment.
List a condition
To list a role assignment condition, use az role assignment list . For more information, see List Azure role assignments using Azure CLI .
Delete a condition
To delete a role assignment condition, edit the role assignment condition and set both the condition and condition-version properties to either an empty string ( "" ) or null .
Alternatively, if you want to delete both the role assignment and the condition, you can use the az role assignment delete command. For more information, see Remove Azure role assignments .
- Example Azure role assignment conditions for Blob Storage
- Tutorial: Add a role assignment condition to restrict access to blobs using Azure CLI
- Troubleshoot Azure role assignment conditions
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications You must be signed in to change notification settings
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement . We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
"(MissingSubscription) The request did not have a subscription or a valid tenant level resource provider." in DevOps pipeline #28372
nelson-w commented Feb 15, 2024 • edited
yonzhan commented Feb 15, 2024
Sorry, something went wrong.
microsoft-github-policy-service bot commented Feb 15, 2024
jiasli commented Feb 18, 2024
Nelson-w commented feb 18, 2024, nelson-w commented feb 19, 2024, jiasli commented feb 20, 2024.
- 👍 1 reaction
Successfully merging a pull request may close this issue.

COMMENTS
az role assignment create: Create a new role assignment for a user, group, or service principal. Core GA az role assignment delete: Delete role assignments. Core GA az role assignment list: List role assignments. Core GA az role assignment list-changelogs: List changelogs for role assignments. Core GA az role assignment update
To assign a role, you might need to specify the unique ID of the object. The ID has the format: 11111111-1111-1111-1111-111111111111. You can get the ID using the Azure portal or Azure CLI. User. For a Microsoft Entra user, get the user principal name, such as [email protected] or the user object ID.
To list a custom role definition, use az role definition list. This command is the same command you would use for a built-in role. Azure CLI. Copy. az role definition list --name {roleName} The following example lists the Virtual Machine Operator role definition: Azure CLI. Copy.
To address this scenario, you should specify the principal type when creating the role assignment. To assign a role, use az role assignment create, specify a value for --assignee-object-id, and then set --assignee-principal-type to ServicePrincipal.
If the Azure built-in roles don't meet the specific needs of your organization, you can create your own custom roles. For this tutorial, you create a custom role named Reader Support Tickets using Azure CLI. The custom role allows the user to view everything in the control plane of a subscription and also open support tickets.
The Azure-CLI command documentation can be found here. az role definition create --role-definition vm-restart.json . Once the role has been create you can use the following command to assign it to a group or user(s) az role assignment create --role "Restart Virtual Machines" --assignee [email protected] or assign it using the portal.
This is the Azure CLI Command to create a new role in Azure, where RoleInfo.json is the local file with all the configurations, scope, actions, data actions regarding that role. You need to follow the Microsoft's Custom Role Creation Documentation to make sure everything is setup in a proper way. az role definition create --role-definition ...
Step 2: Assign Roles to Users or Groups. Identify users or groups by their identifiers and associate roles: Replace <User or Group ID> with the actual Object IDs of users or the Microsoft Entra ID ...
Adding to a group. Suppose we want to add the service principal to a group. We need the group id to do that, and if we need to look it up, we can do so with the az ad group list command and using a filter. --query "[].id" -o tsv. Then the az ad group member add command allows us to add the object id of our service principal to the group.
Here are the steps for making these changes with the Azure CLI. Adding a Role to a User. To assign a role to a user in Azure, you can use the "az role assignment create" command. You have to specify three components, the assignee, the role, and the resource groups or scope of access. In the following example, we're assigning Reader access ...
Manage role assignments. Create a new role assignment for a user, group, or service principal. Delete role assignments. List role assignments. List changelogs for role assignments. Update an existing role assignment for a user, group, or service principal. Manage role definitions. Create a custom role definition.
The Initial Attempt. We create a new AzDO yaml pipeline to do the following: Use the Azure CLI task; Use the Service Connection created above; Use an incline script to perform the required role ...
The bash script was using Azure CLI to create the different resources in Azure. I intended to use the "az role assignment create" command to setup the necessary permissions on the Service Principal, however I quickly discovered this was not possible inside Azure CLI for Azure Active Directory Roles and needed to find a solution as ...
To assign the contributor role for the newly created UserAssignedIdentity run az role assignment create: az role assignment create — assignee {principalId} — role Contributor -g ...
Here are a bunch of ways you can find which roles are built into Azure. This will come in super handy when you need to assign a role to a service principal or user with Azure CLI commands like this: az role assignment create --assignee 3db3ad97-06be-4c28-aa96-f1bac93aeed3 --role "Azure Maps Data Reader" Azure CLI. Query the big honking json
List role assignments for a user. To list the role assignments for a specific user, use az role assignment list: Azure CLI. Copy. az role assignment list --assignee {assignee} By default, only role assignments for the current subscription will be displayed. To view role assignments for the current subscription and below, add the --all parameter.
Tour Start here for a quick overview of the site Help Center Detailed answers to any questions you might have Meta Discuss the workings and policies of this site
@Penberthy-- thanks for the info. az keyvault worked out but problem is, some of the teams cannot access the resource group at all because they are not contributors. but manually adding the azure ad group to the resource group with key-vault-contributor is working.teams can access the keyvault from the portal and through az cli.. Let me do some research and see if there is any documentation to ...
Create a role with read-only access to storage and network resources, and the ability to start or restart VMs. (Bash) Azure CLI. Copy. Open Cloud Shell. az role definition create --role-definition '{. "Name": "Contoso On-call",
I'd like to retrieve a list of users from an Azure AD App role by means of the Azure CLI. I am able to fetch some of my application's metadata by issuing az ad app list --app-id <app-id>.The resulting JSON does include the appRole for which I want to fetch all assigned users.. From the az ad app docs I only understand that App roles can be used in conjunction with az ad app create or az ad app ...
To edit an existing role assignment condition, use az role assignment update and a JSON file as input. The following shows an example JSON file where condition and description are updated. Only the condition, conditionVersion, and description properties can be edited. You must specify all the properties to update the role assignment condition.
Describe the bug I'm trying to run the following command in AzureCLI@2 task within an Azure DevOps yml pipeline: az role assignment create --assignee-object-id "523cafde-9001-4d5f-b1f8-0e82d325a459" --assignee-principal-type ServicePrinc...
My Az cli what-if for a bicep deployment at Management scope is not showing the change at the nested management group. ... Taking my C.bicep template below to create a new management group for example, ... Bicep role assignment to storage account in different resource group. 0.