Windows OS Hub / Windows 10 / Allow or Prevent Non-Admin Users from Reboot/Shutdown Windows

Allow or Prevent Non-Admin Users from Reboot/Shutdown Windows
How to allow or prevent shutdown/reboot options in windows via gpo, allow remote shutdown/restart without admin permissions, disable (hide) shutdown or restart options from windows, how to find out who restarted/shutdown a windows server.
You can set the permissions to restart or shutdown Windows using the Shut down the system parameter in the GPO section Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> User Rights Assignment. This GPO option allows you to specify which locally logged-on users can shut down an operating system.
Please note that the default restart/shutdown permissions for desktop versions of Windows 10/11 and Windows Server editions are different.
Open the Local Group Policy Editor ( gpedit.msc ) and navigate to the section specified above. As you can see, the members of local groups Administrators , Users and Backup Operators have the permission to shutdown/reboot a computer running Windows 10 or 11 .
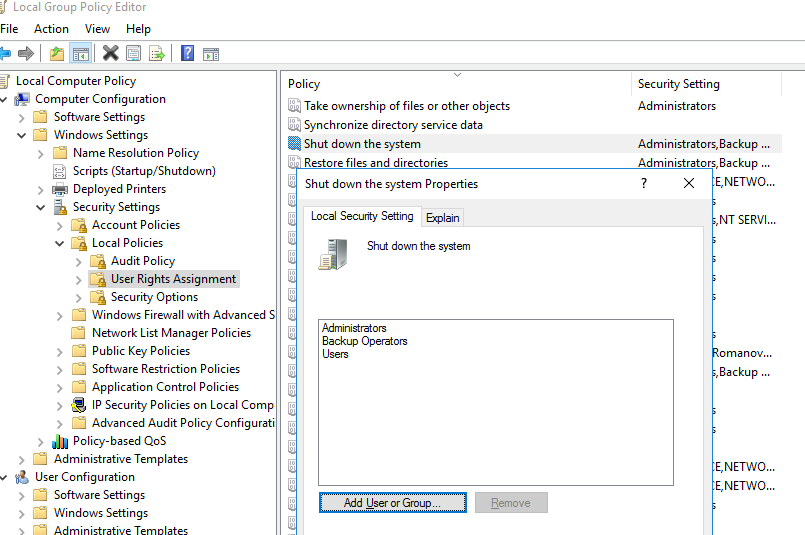
On Windows Server 2022/2019/2016 , only Administrators or Backup Operators can shut down or restart the server. It is reasonable, since in most cases a non-admin user must not have the privileges to shutdown a server (even accidentally). Just imagine an RDS farm host that is often shuts down since users accidentally click on the “Shutdown” button in the Start menu…
On Active Directory domain controllers, the rights to shut down Windows are delegated to:
- Administrators
- Backup Operators
- Server Operators
- Print Operators
If the user does not have permission to restart/shutdown the operating system, then an error will appear when running the following command:
shutdown –r –t 0
You can manually grant permissions to shut down the computer locally using the legacy ntrights tool from the Windows Server 2003 Resource Kit:
ntrights +r SeShutdownPrivilege -u woshub\j.smith
To prevent a user from shutting down or restarting Windows:
ntrights -r SeShutdownPrivilege -u woshub\j.smith
Or, vice versa, you can prevent users of workstations running the desktop Windows 10/11 edition from restarting the computer that performs some kind of server function. In this case, just remove Users group from the local policy Shut down the system .
In the same way, you can prevent (or allow) shutdown/reboot operations for non-admin users on all computers in a specific Organizational Unit (OU) of an Active Directory domain using a domain GPO.
- Create the grpAllowRestartComputers user group in AD, to whom you want to grant the permissions to restart computers. You can create a new group using the ADUC snap-in ( dsa.msc ) or the New-ADGroup PowerShell cmdlet. Add users to the group;
- Set the GPO name ( gpoAllowReboot ) and edit it;
- Navigate to Computer Configuration -> Policies -> Windows Settings -> Security Settings -> User Rights Assignment;
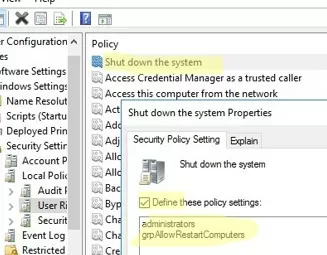
- Update the GPO settings on the target computers and check the resulting GPO settings with the rsop.msc snap-in. Users in your group can now shut down or reboot this host;
To do it, add a user account to the Force shutdown from a remote system Group Policy option in the same GPO section ( User Rights Assignment ).
By default, only administrators can shutdown/restart the server remotely. Add a user account to the policy.
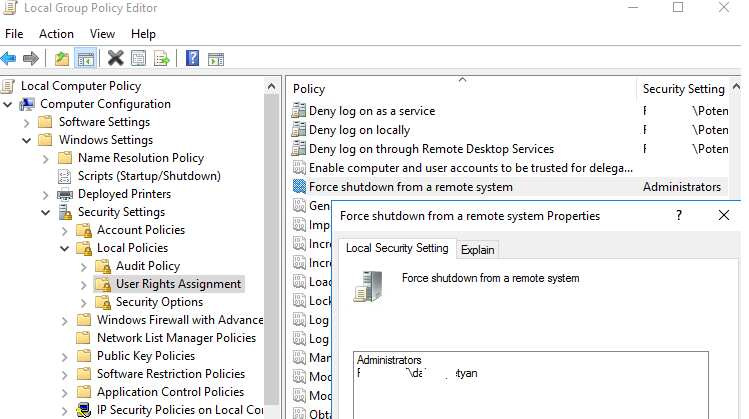
ntrights +r SeRemoteShutdownPrivilege -u woshub\j.smith
After that, the user will get the SeRemoteShutdown privilege and will be able to restart the server remotely using the command:
Or using the Restart-Computer PowerShell cmdlet:
Restart-Computer –ComputerName hamb-rds01 –Force
If WinRM (Windows Remote Management) is enabled on the remote computer, you can use WSman instead of WMI to connect:
Restart-Computer -ComputerName hamb-rds01 -Protocol WSMan
If the user does not have permission to connect to the WMI namespace, an error will appear:
You can use Group Policy to hide the Shutdown, Restart, Sleep and Hibernate options from the sign-in screen and Start Menu. This GPO option is called Remove and Prevent Access to the Shut Down, Restart, Sleep, and Hibernate commands and is located under User Configuration -> Administrative Templates -> Start Menu and Taskbar
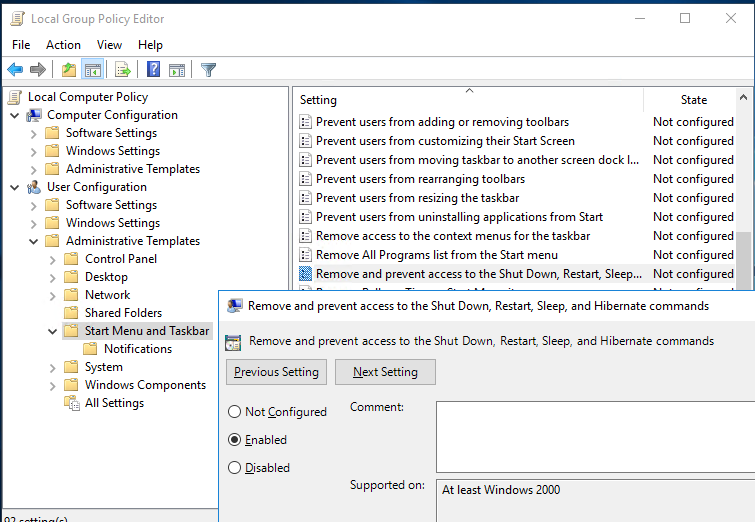
After you enable this policy, a user will be able only to disconnect the current session or use the logoff command. The Shutdown, Sleep and Restart buttons will become unavailable.
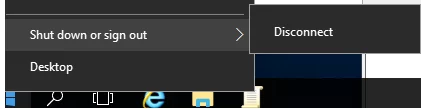
You can use some registry tweaks to hide only a specific item from the Power/Shutdown menu in Windows. For example, you want to hide only the “Shut down” option in the Start menu, but keep “Restart”.
- Open the Registry Editor ( regedit.exe );
- Go to HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\default\Start\HideShutDown ;
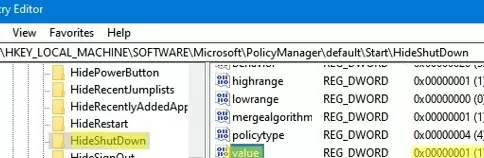
REG ADD "HKLM\SOFTWARE\Microsoft\PolicyManager\default\Start\HideShutDown" /v "value" /t REG_DWORD /d 1 /f
Or using PowerShell:
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\PolicyManager\default\Start\HideShutDown" -Name "value" -Value 1
Also, you can hide other options in the Start Menu and Windows sign-in screen:
- Hide only thr Restart option in Windows: REG ADD "HKLM\SOFTWARE\Microsoft\PolicyManager\default\Start\HideRestart " /v "value" /t REG_DWORD /d 1 /f
- Hide Hibernate option from Start Menu in Windows: R EG ADD "HKLM\SOFTWARE\Microsoft\PolicyManager\default\Start\HideHibernate" /v "value" /t REG_DWORD /d 1 /f
- Hide Sleep from the Start Menu: REG ADD "HKLM\SOFTWARE\Microsoft\PolicyManager\default\Start\HideSleep" /v "value" /t REG_DWORD /d 1 /f
- To completely disable the Power button and remove the “Shut down or sign out” option from WinX menu: REG ADD "HKLM\SOFTWARE\Microsoft\PolicyManager\default\Start\HidePowerButton" /v "value" /t REG_DWORD /d 1 /f
Please note that in Windows Server 2019/2022, after assigning restart permission to a user, an error may appear:
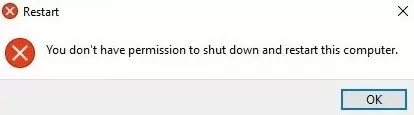
In this case, you need to enable the UAC parameter “User Account Control: Run all administrators in Admin Approval Mode” in the GPO:
If you have granted permission to reboot a computer for a non-admin user, you may want to know who restarted a Windows Server : a user or one of the administrators.
Use the Event Viewer ( eventvwr.msc ) to search for shutdown logs in Windows. Go to Windows Logs -> System and filter the current log by the Event ID 1074 .
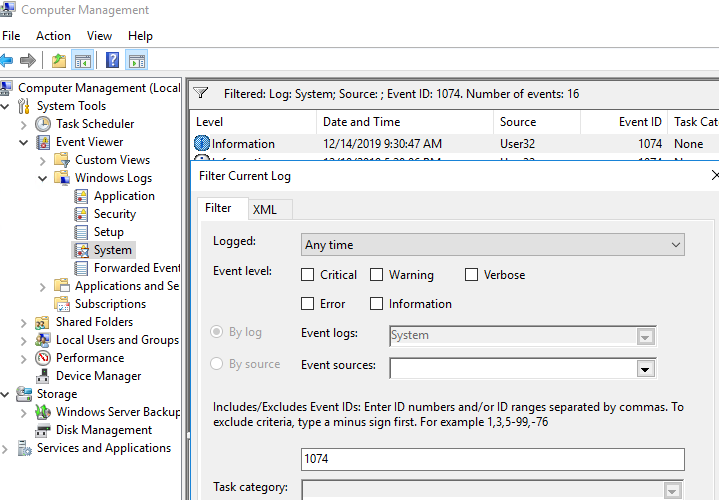
As you can see, there are server restart events in the log in chronological order. The event description includes the restart time, the reason, and the user account that restarted the host.
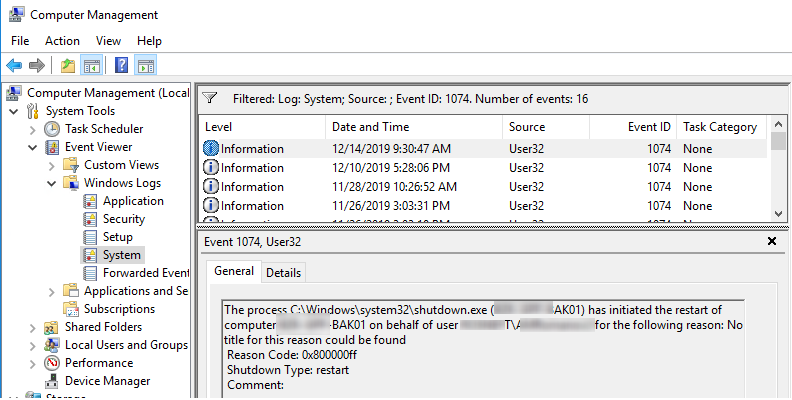
You can get information about recent Windows shutdown events using the same Event ID 1076 :
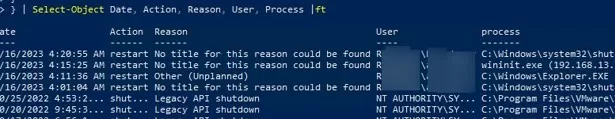
Use the following simple PowerShell script to list the last ten computer restart and shutdown events. This list contains the names of the users and processes from which the reboot was initiated.
Get-EventLog -LogName System | where {$_.EventId -eq 1074} |select-object -first 10 | ForEach-Object { $rv = New-Object PSObject | Select-Object Date, User, Action, process, Reason, ReasonCode if ($_.ReplacementStrings[4]) { $rv.Date = $_.TimeGenerated $rv.User = $_.ReplacementStrings[6] $rv.Process = $_.ReplacementStrings[0] $rv.Action = $_.ReplacementStrings[4] $rv.Reason = $_.ReplacementStrings[2] $rv } } | Select-Object Date, Action, Reason, User, Process |ft
Fix: Can’t Extend Volume in Windows
Fix: windows needs your current credentials pop-up message, related reading, testing internet speed from windows command prompt (powershell), configure file and folder access auditing on windows..., install any os from iso image over network..., how to add or remove pinned folders to..., how to assign (passthrough) a physical gpu to....
So sad that there’s no option to disable only shutdown. I have a need to allow user to restart their machines but not shutdown.
FYI you can hide shutdown from the start menu using HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\default\Start\HideShutDown
Thanks, but even so an advanced user would know to turn it off using other ways.
Thank you MT.. this helped..
On Windows 11, this did work, however, a user who is blocked from restarting/shutting down in this way, can still press Control-Alt-Delete and has the restart/shutdown option in the lower right hand corner. Is there a way to remove that, too?
I just actually tried it from a “non-privileged” account. The good news is that although the options appear, they don’t actually work. 🙃
Leave a Comment Cancel Reply
Notify me of followup comments via e-mail. You can also subscribe without commenting.
Current ye@r *
Leave this field empty
Prevent users from shutting down or restarting Windows computer
Prevent access to shutdown, restart, sleep, hibernate commands.
This policy setting prevents users from performing the following commands from the Start menu or Windows Security screen: Shut Down, Restart, Sleep, and Hibernate. This policy setting does not prevent users from running Windows-based programs that perform these functions.
Prevent specific users from shutting down Windows
This security setting determines which users who are logged on locally to the computer can or cannot shut down the operating system using the Shut Down command.
At the edge of tweaking
Advertisement
To Allow Users or Groups to Shut Down Windows 10,
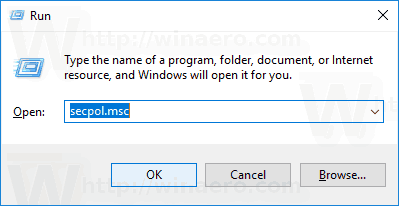
- On the right, double-click the option Shut down the system .
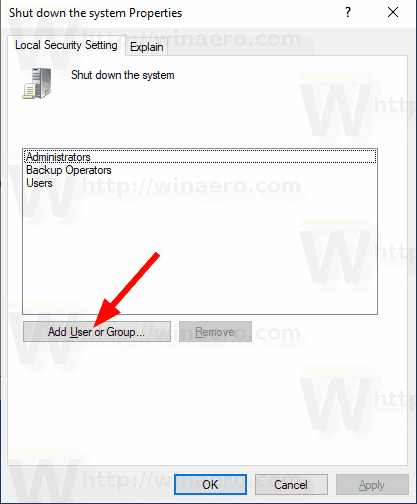
- From the list, select the user account or group to deny log on locally for it. You can select more than one entry at once by holding the Shift or Ctrl keys and clicking on the items the list.
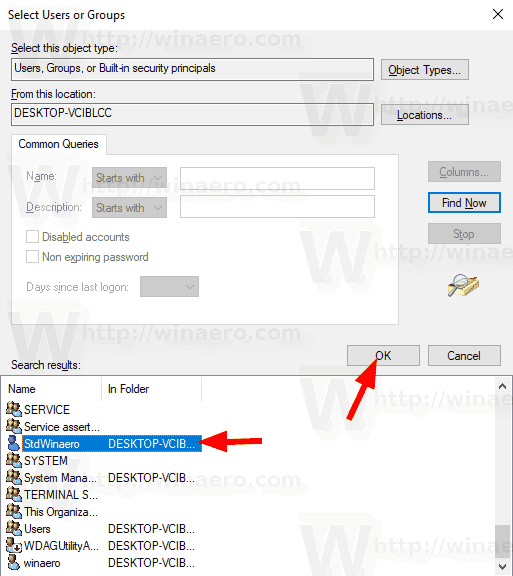
You are done.
To Prevent Users or Groups from Shutting Down Windows 10,
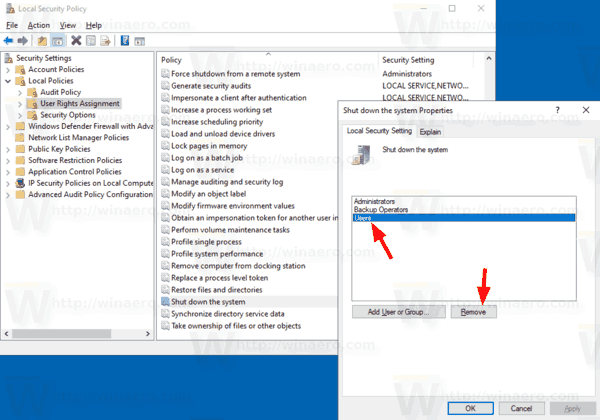
If your Windows edition doesn't include the secpol.msc tool, here is an alternative solution.
If your Windows edition doesn't include the secpol.msc tool, you can use the ntrights.exe tool from Windows 2003 Resource Kit . Many resource kit tools released for previous Windows versions will run successfully on Windows 10. ntrights.exe is one of them.
The ntrights tool
The ntrights tool allows you to edit user account privileges from the command prompt. It is a console tool with the following syntax.
- Grant a right: ntrights +r Right -u UserOrGroup [-m \\Computer] [-e Entry]
- Revoke a right: ntrights -r Right -u UserOrGroup [-m \\Computer] [-e Entry]
The tool supports plenty of privileges which can be assigned to or revoked from a user account or group. Privileges are case sensitive . To learn more about the supported privileges, type ntrights /? .
To add ntrights.exe to Windows 10 , read this post: What is the ntrights app and how you can use it . You can place the ntrights.exe file to the C:\Windows\System32 folder to quickly call it.
Revoke Shut Down Right with ntrights
- Open an elevated command prompt .
Substitute the SomeUserName portion with the actual user name or group name. The specified user will be prevented from locally signing to Windows 10.
- To undo the change and allow the user to log on locally, execute ntrights -u SomeUserName -r SeShutdownPrivilege
Related articles.
- How to set the default action for the Shutdown dialog in Windows 10
- All ways to restart and shutdown Windows 10
- The Slide-to-Shutdown feature in Windows 10
- Speed up slow shutdown in Windows 10
- Enable Shutdown Event Tracker in Windows 10
- How to Find the Shutdown Log in Windows 10
- How to Clear Pagefile at Shutdown in Windows 10
- Add Shutdown Context Menu in Windows 10
- Create a Shut Down Windows Dialog Shortcut in Windows 10
- Create Shutdown, Restart, Hibernate and Sleep Shortcuts in Windows 10
- Create Slide to Shutdown Shortcut in Windows 10
- How to create a shortcut to the Shut Down Windows dialog in Windows 10
- Abnormal Shutdown Diagnosis in Windows 10
- Close Apps Automatically at Restart, Shut Down, or Sign Out in Windows 10
- Disable Shut Down, Restart, Sleep, and Hibernate in Windows 10
Winaero greatly relies on your support. You can help the site keep bringing you interesting and useful content and software by using these options:
If you like this article, please share it using the buttons below. It won't take a lot from you, but it will help us grow. Thanks for your support!
Author: Sergey Tkachenko
Sergey Tkachenko is a software developer who started Winaero back in 2011. On this blog, Sergey is writing about everything connected to Microsoft, Windows and popular software. Follow him on Telegram , Twitter , and YouTube . View all posts by Sergey Tkachenko
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *

Privacy Overview
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
How to add a user group in the "Shut down the system" group policy in Windows Server by CMD or PowerShell
I've read some documentation on Microsoft and other sites. Some of them suggest GPRegistryValue for registry-based policies and other recommended third-party software.
The full path of the key is: "Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment"
But in my case I cannot use other packages except CMD or PowerShell (UI not available).
- group-policy
- windows-server
- superuser.com/questions/1254253/… and blakedrumm.com/blog/set-and-check-user-rights-assignment might help you for a starting point to play with. – Vomit IT - Chunky Mess Style Commented Nov 25, 2022 at 21:25
- This is just local security policy settings. What did you search for as this is a common task? powershell 'Local User Rights Management' – postanote Commented Nov 25, 2022 at 21:37
Windows provides the secedit.exe tool for this and or custom code, as per the link provided in my comment to you.
Also, did you check the mspowershellgallery.com site for modules that assist with local user security policy?
Update as per '@Vomit IT - Chunky Mess Style', suggestion.
The more succinct/elegant option.
FYI --- Update for '@Vomit IT - Chunky Mess Style'. Using the PS_LSA.Wrapper
- 1 @VomitIT-ChunkyMessStyle... update provided. – postanote Commented Nov 25, 2022 at 21:43
- Oh yeah, now you're talking!!! I saw github examples of that Indented.SecurityPolicy you suggested listed there. I like it! – Vomit IT - Chunky Mess Style Commented Nov 25, 2022 at 21:55
- 1 Yeppers, I've got a bunch of these I've collected, refactored, and written over the years in different engagements. Even one using the underlying OS PS_LSA Windows library. – postanote Commented Nov 25, 2022 at 22:06
- Thanks for helping me.The module of 'SecurityPolicy' is available, but when I try to find its modules "Get-Command -Module 'SecurityPolicy'" nothing is listed. Thus, I can't execute 'Add-UserRightsAssignment'. – Daniel Teodoro Commented Nov 29, 2022 at 13:38
- If you did this Get-Command -Module 'SecurityPolicy' , and you see nothing? If so, that means it's not installed/in your PSModulePath. Did you install the module as I show in my suggested answer? If not, then you need to. Then you use Get-Module -ListAvailable to validate it's on your system. – postanote Commented Nov 30, 2022 at 6:37
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged powershell group-policy windows-server ..
- The Overflow Blog
- How to build open source apps in a highly regulated industry
- Community Products Roadmap Update, July 2024
- Featured on Meta
- We spent a sprint addressing your requests — here’s how it went
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network...
Hot Network Questions
- In equation (3) from lecture 7 in Leonard Susskind’s ‘Classical Mechanics’, should the derivatives be partial?
- Sitting on a desk or at a desk? What's the diffrence?
- Why is Uranus colder than Neptune?
- What is the value of air anisotropy?
- Do Christians believe that Jews and Muslims go to hell?
- What does '\($*\)' mean in sed regular expression in a makefile?
- Is it possible to arrange the free n-minoes of orders 2, 3, 4 and 5 into a rectangle?
- Turning Misty step into a reaction to dodge spells/attacks
- Test whether a string is in a list
- Is arXiv strictly for new stuff?
- Position where last x halfmoves are determined
- Can you help me to identify the aircraft in a 1920s photograph?
- Book in 90's (?) about rewriting your own genetic code
- Can you arrange 25 whole numbers (not necessarily all different) so that the sum of any three successive terms is even but the sum of all 25 is odd?
- Why does the Trump immunity decision further delay the trial?
- Factor-smooth interactions in generalized additive models
- Python code doesn't work on 'Collection'
- Why do I see low voltage in a repaired underground cable?
- Derivation of two-body Coulomb interaction in momentum space
- Can someone explain the Trump immunity ruling?
- Why does the Egyptian Hieroglyph M8 (pool with lotus flowers) phonetically correspnd to 'Sh' sound?
- Who originated the idea that the purpose of government is to protect its citizens?
- Is it possible to reference and transpose each staff separately for midi output only in lilypond?
- Are there any parts of the US Constitution that state that the laws apply universally to all citizens?
WinSecWiki > Security Settings > Local Policies > User Rights
User Rights Assignments
Although in this section they are called user rights, these authority assignments are more commonly called privileges.
Privileges are computer level actions that you can assign to users or groups. For the sake of maintainability you should only assign privileges to groups not to individual users. Each computer has its own user rights assignments. In particular this means you should be cognizant of rights assignments on member servers which may easily differ from the rights assignments you find on your domain controllers. To centrally control user rights assignments on computers throughout your domain use group policy.
- Logon rights
- Admin equivalent rights
- Tracking user rights with the security log
- User rights in-depth
- Access this computer from the network
- Act as part of the operating system
- Add workstations to domain
- Adjust memory quotas for a process
- Allow log on locally
- Allow logon through Terminal Services
- Back up files and directories
- Bypass traverse checking
- Change the system time
- Create a pagefile
- Create a token object
- Create global objects
- Create permanent shared objects
- Debug programs
- Deny access to this computer from the network
- Deny logon as a batch job
- Deny logon as a service
- Deny logon locally
- Deny logon through Terminal Services
- Enable computer and user accounts to be trusted for delegation
- Force shutdown from a remote system
- Generate security audits
- Impersonate a client after authentication
- Increase scheduling priority
- Load and unload device drivers
- Lock pages in memory
- Log on as a batch job
- Log on as a service
- Manage auditing and security log
- Modify firmware environment values
- Perform volume maintenance tasks
- Profile single process
- Profile system performance
- Remove computer from docking station
- Replace a process level token
- Restore files and directories
- Shut down the system
- Synchronize directory service data
- Take ownership of files and other objects
Child articles:
- Logon Rights
- Admin Equivalent Rights
- Tracking User Rights with the Security Log
- User Rights In-Depth
Back to top
| • | |
| • | |
| • | |
| • |

Set and Check User Rights Assignment via PowershellYou can add, remove, and check user rights assignment (remotely / locally) with the following powershell scripts.. Posted by : blakedrumm on Jan 5, 2022 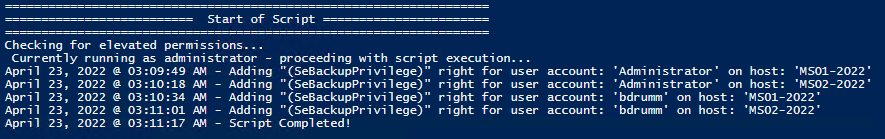 Local ComputerRemote computer, output types. This post was last updated on August 29th, 2022 I stumbled across this gem ( weloytty/Grant-LogonAsService.ps1 ) that allows you to grant Logon as a Service Right for a User. I modified the script you can now run the Powershell script against multiple machines, users, and user rights. Set User RightsHow to get it. All of the User Rights that can be set:
Note You may edit line 437 in the script to change what happens when the script is run without any arguments or parameters, this also allows you to change what happens when the script is run from the Powershell ISE. Here are a few examples: Add Users Single Users Example 1 Add User Right “Allow log on locally” for current user: . \Set-UserRights.ps1 -AddRight -UserRight SeInteractiveLogonRight Example 2 Add User Right “Log on as a service” for CONTOSO\User: . \Set-UserRights.ps1 -AddRight -Username CONTOSO\User -UserRight SeServiceLogonRight Example 3 Add User Right “Log on as a batch job” for CONTOSO\User: . \Set-UserRights.ps1 -AddRight -Username CONTOSO\User -UserRight SeBatchLogonRight Example 4 Add User Right “Log on as a batch job” for user SID S-1-5-11: . \Set-UserRights.ps1 -AddRight -Username S-1-5-11 -UserRight SeBatchLogonRight Add Multiple Users / Rights / Computers Example 5 Add User Right “Log on as a service” and “Log on as a batch job” for CONTOSO\User1 and CONTOSO\User2 and run on, local machine and SQL.contoso.com: . \Set-UserRights.ps1 -AddRight -UserRight SeServiceLogonRight , SeBatchLogonRight -ComputerName $ env : COMPUTERNAME , SQL.contoso.com -UserName CONTOSO\User1 , CONTOSO\User2 Remove Users Single Users Example 1 Remove User Right “Allow log on locally” for current user: . \Set-UserRights.ps1 -RemoveRight -UserRight SeInteractiveLogonRight Example 2 Remove User Right “Log on as a service” for CONTOSO\User: . \Set-UserRights.ps1 -RemoveRight -Username CONTOSO\User -UserRight SeServiceLogonRight Example 3 Remove User Right “Log on as a batch job” for CONTOSO\User: . \Set-UserRights.ps1 -RemoveRight -Username CONTOSO\User -UserRight SeBatchLogonRight Example 4 Remove User Right “Log on as a batch job” for user SID S-1-5-11: . \Set-UserRights.ps1 -RemoveRight -Username S-1-5-11 -UserRight SeBatchLogonRight Remove Multiple Users / Rights / Computers Example 5 Remove User Right “Log on as a service” and “Log on as a batch job” for CONTOSO\User1 and CONTOSO\User2 and run on, local machine and SQL.contoso.com: . \Set-UserRights.ps1 -RemoveRight -UserRight SeServiceLogonRight , SeBatchLogonRight -ComputerName $ env : COMPUTERNAME , SQL.contoso.com -UserName CONTOSO\User1 , CONTOSO\User2 Check User RightsIn order to check the Local User Rights, you will need to run the above (Get-UserRights), you may copy and paste the above script in your Powershell ISE and press play. 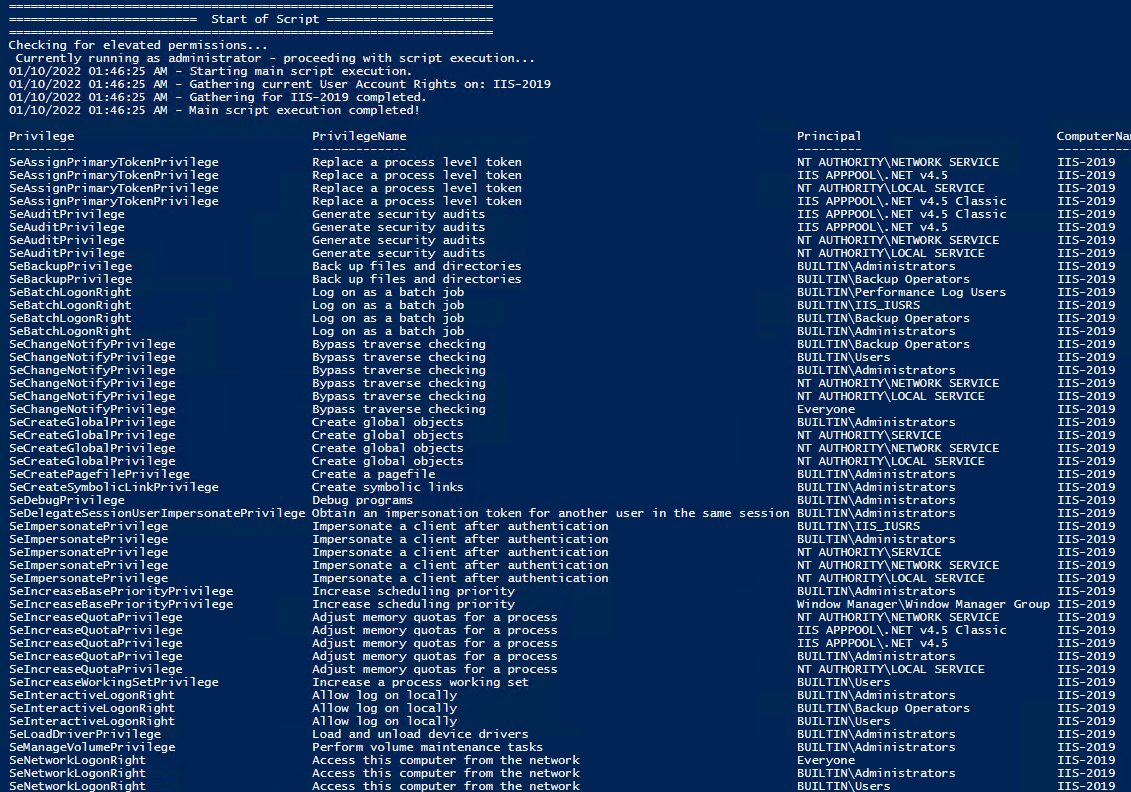 Note You may edit line 467 in the script to change what happens when the script is run without any arguments or parameters, this also allows you to change what happens when the script is run from the Powershell ISE. Get Local User Account Rights and output to text in console: Get Remote SQL Server User Account Rights: Get Local Machine and SQL Server User Account Rights: Output Local User Rights on Local Machine as CSV in ‘C:\Temp’: Output to Text in ‘C:\Temp’: PassThru object to allow manipulation / filtering: I like to collaborate and work on projects. My skills with Powershell allow me to quickly develop automated solutions to suit my customers, and my own needs. Email : [email protected] Website : https://blakedrumm.com My name is Blake Drumm, I am working on the Azure Monitoring Enterprise Team with Microsoft. Currently working to update public documentation for System Center products and write troubleshooting guides to assist with fixing issues that may arise while using the products. I like to blog on Operations Manager and Azure Automation products, keep checking back for new posts. My goal is to post atleast once a month if possible.
Stack Exchange NetworkStack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers. Q&A for work Connect and share knowledge within a single location that is structured and easy to search. Allow non-admin user to shutdown/reboot Server 2012Anyone know if a setting exists to allow a non-admin user to shutdown a server? Obviously I can set the "Allow Server to shutdown without logon" GPO but that is not quite the same thing. I am looking for a way to properly assign the shutdown right to a particular user if possible.
2 Answers 2You can assign this in either a GPO or Local Security Policy. The setting that you're looking for is in Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment > Shutdown the system 
use "force shutdown from a remote system" then you can build a script like shutdown -r -t 120 -m "hostname" to restart the system remotely.
You must log in to answer this question.Not the answer you're looking for browse other questions tagged windows-server-2012 user-permissions ..
Hot Network Questions
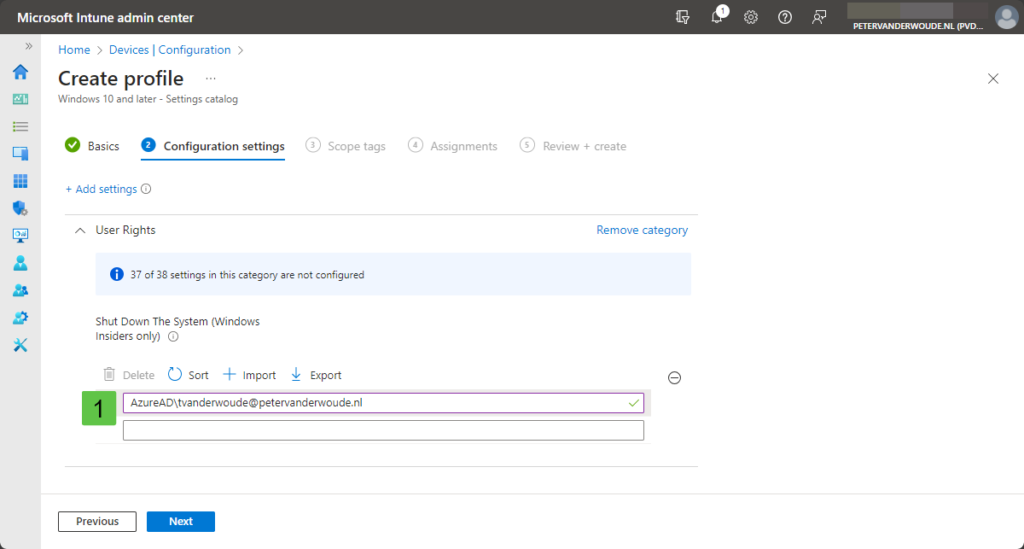
All about Microsoft Intune Peter blogs about Microsoft Intune, Microsoft Intune Suite, Windows Autopilot, Configuration Manager and more  Preventing users from shutting down specific devicesThis week is a short post about the ability to prevent users from shutting down, or restarting, specific devices. That is something already often used for specific servers, like domain controllers, to prevent users from shutting them down. There are, however, also good reasons why that might also be very useful and beneficial on specific devices. Think about devices that host critical business processes that can only be turned off, or restarted, during specific windows. For those devices the user right to shutdown that device, should only be provided to a few trusted users, or administrators. So, not just removing the shutdown, or restart, button, but actually removing the user right to perform a shutdown. Luckily, nowadays there is an easy method for configuring the list of users that are allowed to shutdown a specific Windows device. This post will provide some more details around that configuration, followed with the configuration steps. This post will end with showing the user experience. Note : Keep in mind that this post is focussed on the local options on the Windows device. Configuring preventing users from shutting down specific devicesWhen looking at preventing users from shutting down, or restarting, specific Windows devices, the UserRights section in the Policy CSP is the place to look. That section contains many of the different policy settings of the User Rights Assignment Local Policies , including the Shut Down The System ( ShutDownTheSystem ) policy setting. That policy setting can be used to configure the users that are allowed to locally shutdown, or restart, the device. The configuration of that policy setting is available via the Settings Catalog . The following eight steps walk through the creation of a Settings Catalog profile that contains the required setting to configure the local shutdown rights, by using the Shut Down The System policy setting.
Note : The setting mentions that it’s available for Windows Insiders only, but that’s not the experience so far. Experiencing users prevented from shutting down specific devicesAfter configuring the list with users that are allowed to shutdown the device, it’s time to look at the user experience. And there are many things that indicate the behavior and that the configuration is applied. That can be the actual applied configuration, as well as the experience of the user. Pieces of both are shown below in Figure 2. To start with the first, the applied configuration can be verified in the Local Security Policy by looking at Local Policies > User Rights Assignment . That includes the Shut down the system right (1) that includes the configured list of users and local groups that are allowed to shutdown the system. The applied configuration will make sure that the users cannot shutdown, or restart, the device. That can be verified by for example looking at the available power options for the users (2), or the ability to restart the device after the installation of updates (3). Besides that, even command actions will be prevented and give the user an access denied message. 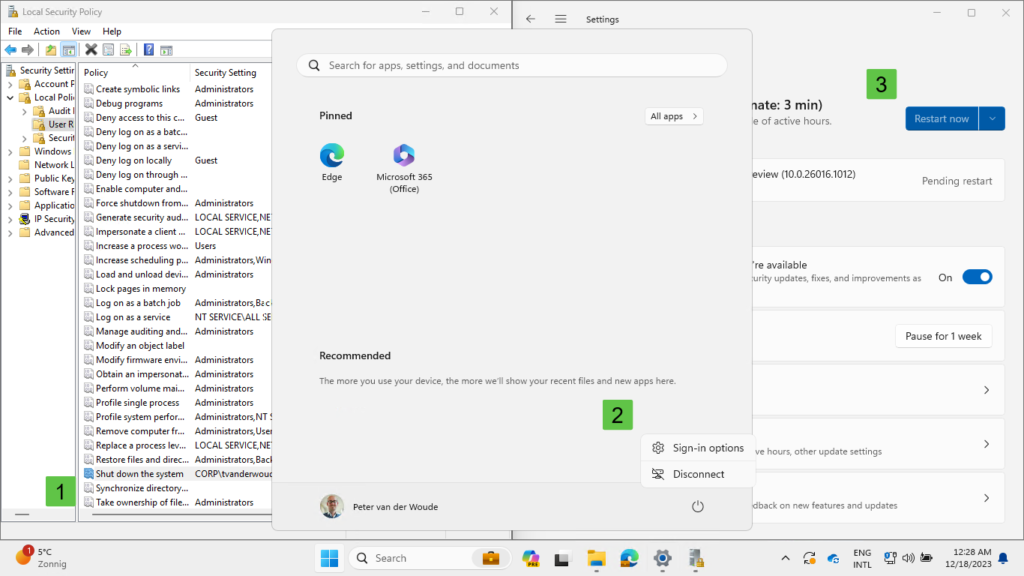 Note : This configuration was successfully tested on the latest Windows Insiders builds and on Windows 11 version 23H2. More informationFor more information about preventing users from restarting Windows, refer to the following docs.
 4 thoughts on “Preventing users from shutting down specific devices”
I don’t suppose you tested this on Win 11 22H2 as well did you by any chance? I’m not having much luck setting it yet, I’ve even tried using a SID rather than domain group name. Before I dig too deeply I’m unsure if it’s the Windows Insider thing mentioned that isn’t working on 22H2 – but does on 23H2, or if it’s something else. Hi Steve, I’ve successfully tested it on Windows 11 23H2 and Insider Builds. Regards, Peter Leave a Comment Cancel replyNotify me of follow-up comments by email. Notify me of new posts by email. This site uses Akismet to reduce spam. Learn how your comment data is processed . 
The Force shutdown from a remote system user right must only be assigned to the Administrators group.
Collectives™ on Stack OverflowFind centralized, trusted content and collaborate around the technologies you use most. Q&A for work Connect and share knowledge within a single location that is structured and easy to search. Get early access and see previews of new features. Local Security Policies, System Group Policy Objects, and Active Directory values not updating Secedit.exe Sec.cfgI am attempting to monitor the status of SeRemoteShutdownPrivilege and SeEnableDelegationPrivilege to determine if they have been updated/changed. When doing so, this configuration file doesn't seem to update. Are there any other locations where a variable would affect "Force shutdown form a remote system" and "Enable computer and user accounts to be trusted for delegation". I have already looked through Microsoft Registry key documentation. Here's the link I referred to: https://www.microsoft.com/en-us/download/details.aspx?id=25250 I have looked into using Get-GPRegistryValue, Get-GPOReport, and Get-GPO. The way I generated Sec.cfg was using "Secedit /export /cfg sec.cfg /log NUL". Thank you for any help that you can provide.
• For the ‘Force Shutdown from a Remote System’ setting to apply effectively on a client system, kindly check whether the below group policy regarding this setting has been applied or not by executing the command ‘gpresult /h gpreport.html’ on the elevated command prompt on the client system. In the report, please check whether the above said group policy setting has been applied successfully or not. Group policy setting: - On the Group Policy Server, check the below group policy setting by checking the ‘Default domain policy’ or that policy which controls the below setting: - To forcefully apply the domain group policy settings on the client system, execute the command ‘gpupdate /force’ on an elevated command prompt and restart the client system. Then check the client’s group policy report once again to check whether the setting has been applied or not. • Also, I would suggest you to please make the above said modifications on a baseline client system through local group policy editor and export the settings in an ‘.inf’ template for installation via powershell script . Check for the below settings information in the ‘.inf’ file and then execute the below command by modifying the values for ‘.inf’ file and ‘.db’ file as appropriate: - By doing the above, your issue should get resolved. Your AnswerReminder: Answers generated by artificial intelligence tools are not allowed on Stack Overflow. Learn more Sign up or log inPost as a guest. Required, but never shown By clicking “Post Your Answer”, you agree to our terms of service and acknowledge you have read our privacy policy . Not the answer you're looking for? Browse other questions tagged active-directory registry windows-server-2016 group-policy security-policy or ask your own question .
Hot Network Questions
This browser is no longer supported. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Force shutdown from a remote system
Describes the best practices, location, values, policy management, and security considerations for the Force shutdown from a remote system security policy setting. This security setting determines which users are allowed to shut down a device from a remote location on the network. This setting allows members of the Administrators group or specific users to manage computers (for tasks such as a restart) from a remote location. Constant: SeRemoteShutdownPrivilege Possible values
Best practices
Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment Default valuesBy default this setting is Administrators and Server Operators on domain controllers and Administrators on stand-alone servers. The following table lists the actual and effective default policy values for the most recent supported versions of Windows. Default values are also listed on the policy’s property page.
Policy managementThis section describes features, tools, and guidance to help you manage this policy. A restart of the computer is not required for this policy setting to be effective. Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on. This policy setting must be applied on the computer that is being accessed remotely. Group PolicyThis user right is defined in the Default Domain Controller Group Policy Object (GPO) and in the local security policy of workstations and servers. Settings are applied in the following order through a Group Policy Object (GPO), which will overwrite settings on the local computer at the next Group Policy update:
When a local setting is greyed out, it indicates that a GPO currently controls that setting. Security considerationsThis section describes how an attacker might exploit a feature or its configuration, how to implement the countermeasure, and the possible negative consequences of countermeasure implementation. VulnerabilityAny user who can shut down a device could cause a denial-of-service condition to occur. Therefore, this user right should be tightly restricted. CountermeasureRestrict the Force shutdown from a remote system user right to members of the Administrators group or other assigned roles that require this capability, such as non-administrative operations staff. Potential impactOn a domain controller, if you remove the Force shutdown from a remote system user right from the Server Operator group, you could limit the abilities of users who are assigned to specific administrative roles in your environment. Confirm that delegated activities are not adversely affected. Related topics
Additional resourcesThe Daily Show Fan Page Explore the latest interviews, correspondent coverage, best-of moments and more from The Daily Show. The Daily ShowS29 E68 • July 8, 2024 Host Jon Stewart returns to his place behind the desk for an unvarnished look at the 2024 election, with expert analysis from the Daily Show news team. Extended Interviews The Daily Show TicketsAttend a Live Taping Find out how you can see The Daily Show live and in-person as a member of the studio audience. Best of Jon Stewart The Weekly Show with Jon StewartNew Episodes Thursdays Jon Stewart and special guests tackle complex issues. Powerful Politicos The Daily Show ShopGreat Things Are in Store Become the proud owner of exclusive gear, including clothing, drinkware and must-have accessories. About The Daily Show |
COMMENTS
How to Allow or Prevent Shutdown/Reboot Options in Windows via GPO. You can set the permissions to restart or shutdown Windows using the Shut down the system parameter in the GPO section Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> User Rights Assignment.This GPO option allows you to specify which locally logged-on users can shut down an ...
1 Press the Win + R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy. 2 Expand open Local Policies in the left pane of Local Security Policy, and click/tap on User Rights Assignment. (see screenshot below step 3) 3 In the right pane of User Rights Assignment, double click/tap on the policy (ex: "Shut down the system") you want to add users and/or ...
Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on. Group Policy. This user right doesn't have the same effect as Force shutdown from a remote system. For more information, see Force shutdown from a remote system.
1. Press the Win+R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy. 2. Expand open Local Policies in the left pane of Local Security Policy, click/tap on User Rights Assignment, and double click/tap on the Shut down the system policy in the right pane. (see screenshot below) 3.
Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment > Shut Down the System. Double click on it > Select Users > Press Remove > Apply/OK.
How to do it: Run secpol.msc. Open Security Settings \ Local Policies \ User Rights Assignment. Double-click Force shutdown from a remote system in the right pane. Click Add User or Group. Enter the name INTERACTIVE in the text box and click Check names, then click OK, and OK again.
For info about the User Rights Assignment policy, Shut down the system, see Shut down the system. Security considerations. This section describes: How an attacker might exploit a feature or its configuration. How to implement the countermeasure. Possible negative consequences of countermeasure implementation. Vulnerability
To Allow Users or Groups to Shut Down Windows 10, Press Win + R keys together on your keyboard and type: secpol.msc. Press Enter. Local Security Policy will open. Go to User Local Policies -> User Rights Assignment. On the right, double-click the option Shut down the system. In the next dialog, click Add User or Group.
Provides an overview and links to information about the User Rights Assignment security policy settings user rights that are available in Windows. User rights govern the methods by which a user can log on to a system. User rights are applied at the local device level, and they allow users to perform tasks on a device or in a domain.
a) Open Local Security Policy. b)Expand Local Policies. c) Select User Rights Assignment>Right Pane of User Rights Assignment. d) Double Click on Shut down the system. e) Now select User (s) and /or group (s) that you don't want to be allowed to shut down the computer. No it's not working. You already posted this.
User Rights Assignment; Shut down the system. The Explaination of the privilege: Shut down the system. This security setting determines which users who are logged on locally to the computer can shut down the operating system using the Shut Down command. Misuse of this user right can result in a denial of service.
How to add a user group in the "Shut down the system" group policy in Windows Server by CMD or PowerShell. ... SecurityPolicyDsc PSGallery This module is a wrapper around secedit.exe which provides the ability to configure user rights assignments 1.3.2 Indented.SecurityPolicy PSGallery Security management functions and resources 0.0.12 ...
In the right pane of User Rights Assignment, double click on a listed Policy (ex: Shut down the system) that you wanted to add or remove a user or group, then go to step 3 and/or 4 below. (see screenshot above) 3. To Remove a User or Group from a User Rights Assignment Policy
Click Start Button, Type gpedit.msc in the search field. Browse to the following location: Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment\ Shut Down the System. Double Click on Shut down the System, Select the user group you want to Disable and hit Remove > Apply > OK.
Although in this section they are called user rights, these authority assignments are more commonly called privileges. Privileges are computer level actions that you can assign to users or groups. For the sake of maintainability you should only assign privileges to groups not to individual users. Each computer has its own user rights assignments.
Personal File Server - Get-UserRights.ps1 Alternative Download Link. or. Personal File Server - Get-UserRights.txt Text Format Alternative Download Link. In order to check the Local User Rights, you will need to run the above (Get-UserRights), you may copy and paste the above script in your Powershell ISE and press play.
0. use "force shutdown from a remote system" then you can build a script like shutdown -r -t 120 -m "hostname" to restart the system remotely. -r = restart. -t = time in seconds. -m = Target here you have to enter IP or hostname. Share. Improve this answer. edited Oct 13, 2016 at 14:56.
Select User Rights as category; Select Shut Down The System as setting; Specify the allowed users and local groups on separate lines (1) Figure 1: Overview of the configuration settings. On the Scope tags page, configure the required scope tags and click Next; On the Assignments page, configure the assignment for the specific devices and click Next
Fix Text (F-69811r1_fix) Configure the policy value for Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> User Rights Assignment >> "Force shutdown from a remote system" to only include the following groups or accounts:
Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment/Force shutdown from a remote system To forcefully apply the domain group policy settings on the client system, execute the command 'gpupdate /force' on an elevated command prompt and restart the client system. Then check the client's group ...
This reference topic for the IT professional provides an overview and links to information about the User Rights Assignment security policy settings user rights that are available in the Windows operating system. User rights govern the methods by which a user can log on to a system. User rights are applied at the local computer level, and they ...
Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on. ... On a domain controller, if you remove the Force shutdown from a remote system user right from the Server Operator group, you could limit the abilities of users who are assigned to specific administrative roles in your ...
The source for The Daily Show fans, with episodes hosted by Jon Stewart, Ronny Chieng, Jordan Klepper, Dulcé Sloan and more, plus interviews, highlights and The Weekly Show podcast.