

A Comprehensive Guide to Risk Assessment Methodology
August 16, 2023

Risk assessment methodology , an aspect of any risk management process , encompasses various approaches to determining the potential impact of identified risks.
This comprehensive guide aims to elucidate the different methodologies, spanning from quantitative, qualitative, semi-quantitative, asset-based, and vulnerability-based to threat-based.
Each methodology, distinct in its approach, bears its own strengths and limitations, thus necessitating careful selection based on the specific context and objectives of the risk assessment .
The subsequent sections delve into the nuances of each methodology, providing a detailed analysis of their application, usefulness, and potential drawbacks.
This exploration endeavors to equip readers with the necessary knowledge to make informed decisions when choosing the most suitable risk assessment methodology for their needs and circumstances.

What is a Risk Assessment Methodology
A risk assessment methodology is a systematic approach used to identify, evaluate, and manage potential hazards or risks in a given environment, playing a crucial role in the decision-making process.
This methodology is a key component of risk management , as it helps organizations prioritize their resources effectively.
The risk assessment process typically involves a qualitative method, which involves subjective judgment based on expert opinion, and a quantitative method, which is numerical and involves statistical data.
These methods form the basis of different types of risk analysis, which can range from simple hazard identification to complex risk modelling.
The purpose of the methodology is not only to identify potential risks but also to estimate potential impacts, thereby aiding in the development of robust mitigation strategies.
Business associates should take corrective actions to address negative risks and capitalize on positive risks. A list of risks can help with a deeper understanding and effects analysis, especially for core elements such as remote access, the supply chain, and the development life cycle.
Senior management at financial institutions should ensure that additional controls are in place to meet acceptable levels of risk at the organizational and executive levels.
A detailed report with additional guidance can provide a more accurate risk assessment and help determine risk acceptability criteria, including simple risk assessment and residual risk acceptance criteria.
Companies should consider risk avoidance and various risk treatment options to manage information security risk. Sources for risk analysis, including bicyclist risk assessment methods and critical risk elements, should be incorporated into the project risk assessment report.
The highest-level risks should be identified, with a plan for verification and effective action plans. Implementation plans and security assessment plans should be included in the security plan, with consideration for the impact cost and potential threat events.
Framework and guidance documents can be helpful for larger companies to establish a company culture that prioritizes risk management and addresses high-risk failure modes.
Experts recommend considering potential failures during development and using a digital template for risk assessments . Finally, it’s important to proofread and check for spelling, grammar, and punctuation errors before sharing or downloading the document.d Template
Quantitative
Quantitative approaches to evaluating potential hazards employ numerical data and statistical methods, providing precision and objectivity in the analysis.
This type of risk assessment methodology, or quantitative risk assessment , uses specific metrics such as risk matrix, risk levels, and risk values to measure a given risk’s potential consequences and financial impact.
– Quantitative Risk Assessment: – Risk Matrix: This tool prioritizes risks based on their likelihood and potential impact, thus enabling more focused risk management.
– Risk Levels and Values: These metrics provide numerical risk estimates, which can be used to determine the severity and financial implications of potential risks.
The quantitative risk analysis process is a critical component of comprehensive risk management, offering an empirical approach to understanding and mitigating risks.
Qualitative
Contrasting with the numeric approach, qualitative strategies involve a more subjective and interpretive evaluation of potential hazards, relying on expert judgment rather than strictly numerical data.
The qualitative risk assessment method is often employed to identify and categorize kinds of risks in a less structured, more exploratory manner.
The qualitative assessment is central to effective risk communication as it allows for nuanced descriptions of potential hazards and their effects.
Employing a qualitative analysis when assessing risk provides a comprehensive understanding of the various aspects of potential hazards, including their causes, impacts, and possible mitigation strategies.
In essence, the qualitative approach to risk assessment offers an in-depth, interpretive insight into potential risks beyond what can be ascertained from a purely numerical evaluation.
Semi-Quantitative
Semi-quantitative strategies offer a unique approach to investigating potential hazards by bridging the gap between numeric and interpretive evaluations.
This risk assessment guide outlines the semi-quantitative method, which combines aspects of both qualitative and quantitative techniques to provide a more comprehensive guide to risk assessment methodology.
It allows for evaluating risks based on numerical scores and descriptive categories, aiding the risk management process.
Semi-quantitative methods facilitate risk mitigation strategies by assigning a numerical value to the severity of potential threats. These methods improve the understanding of the potential consequences, enhancing the ability to manage and mitigate the threats.
Asset-Based
Asset-based approaches are of utmost importance in the field of hazard investigation. They provide a focused evaluation and identification of assets susceptible to potential threats.
This methodology is typically employed during the risk assessment phase of a formal risk assessment process.
The approach entails systematically identifying potential hazards associated with the asset and analyzing the residual risks . This data is then used to populate a risk management file, which serves as a comprehensive repository of risks associated with the asset.
Asset-based risk assessment methodology provides a structured framework for identifying potential risks and formulating appropriate mitigation strategies.
The method’s inherent focus on asset-specific hazards ensures a comprehensive and detailed risk profile, aiding overall risk management .

Vulnerability-Based
Shifting the focus from assets to vulnerabilities, the vulnerability-based approach to hazard investigation concentrates on the weaknesses that potential threats could exploit.
This security risk assessment method emphasizes identifying vulnerabilities within a system, which can be subjected to unauthorized access or potential incidents.
This risk analysis approach necessitates an in-depth evaluation of the system’s security controls and their effectiveness in mitigating risks. It involves determining the potential impact levels of various threats exploiting existing vulnerabilities.
The ultimate goal is to strengthen these weak points to prevent any potential breaches, thus enhancing the overall security posture.
This proactive measure is crucial in the ever-evolving landscape of security threats, ensuring a comprehensive and robust risk management strategy .
Threat-Based
Contrasting the vulnerability-based approach, the threat-based perspective of analyzing security prioritizes potential dangers that could compromise information systems’ integrity , confidentiality, or availability.
This methodology focuses not only on the assessment of risk but also on the business impact analysis of potential security incidents.
The threat-based approach involves rigorous penetration testing to simulate security risks and identify possible weak points. It anticipates environmental threats that can negatively affect the system and measures to prevent inappropriate access.
Understanding potential threats is vital in this approach as it helps create effective risk mitigation strategies.
Therefore, the threat-based methodology provides a more comprehensive and strategic approach to risk assessment in information systems, ensuring a secure and stable system.
Choosing the Right Methodology
Determining the most suitable approach for evaluating information system security necessitates a thorough understanding of the distinct characteristics and benefits of vulnerability and threat-based methodologies.
Selecting a comprehensive guide to risk assessment methodology is pivotal in the risk management cycle. It is the cornerstone for achieving an effective risk treatment process.
Factors influencing the choice of methodology include the nature of the entity undergoing evaluation, the resources available, and the desired level of detail in the risk evaluation.
Scalable risk assessment methods provide flexibility, accommodating varying scopes and complexities.
The chosen methodology’s sophistication level should match the system’s complexity under scrutiny.
Therefore, choosing the right methodology is a vital step in the approach to risk management , significantly influencing the effectiveness of the risk evaluation.
Frequently Asked Questions
What are the necessary qualifications to conduct a risk assessment.
Conducting a risk assessment necessitates a thorough understanding of the subject matter, analytical skills, and proficiency in data interpretation.
Relevant qualifications may include degrees in risk management , statistics, or related fields, supplemented by professional experience.
How frequently should a risk assessment be conducted in a business environment?
The frequency of conducting a risk assessment in a business environment depends on various factors, such as changes in operational processes, the introduction of new equipment, or after an incident or accident.
What is the typical cost associated with conducting a comprehensive risk assessment?
The cost of conducting a comprehensive risk assessment can vary widely, dependent on factors such as the industry, size of the organization, and complexity of operations. Typically, it ranges from $10,000 to $50,000.
How does the risk assessment methodology change in different industries?
Risk assessment methodologies vary across industries due to differing risk factors and regulatory requirements. Industries with higher inherent risks , such as mining or construction, may employ more robust and thorough assessment techniques.
What are some common mistakes to avoid when implementing a risk assessment methodology?
Common mistakes when implementing a risk assessment methodology include: overlooking potential risks, failing to update risk assessments regularly, not involving all stakeholders, and neglecting to incorporate risk mitigation strategies into business planning.

Knowing the pros and cons of each risk assessment method is crucial for making the right decision.
Quantitative, qualitative, semi-quantitative, asset-based, vulnerability-based, and threat-based methodologies each offer distinct advantages for different contexts.
It is essential to select a methodology that matches the precise needs of the risk assessment to guarantee a complete, precise, and valuable assessment of probable risks.

Chris Ekai is a Risk Management expert with over 10 years of experience in the field. He has a Master’s(MSc) degree in Risk Management from University of Portsmouth and is a CPA and Finance professional. He currently works as a Content Manager at Risk Publishing, writing about Enterprise Risk Management, Business Continuity Management and Project Management.
Information Security Risk Assessment
A Detailed Guide To Audit Risk Assessment For Effective Financial Management
Leave a Comment Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Reach out to understand more about Enterprise Risk Management, Project Management and Business Continuity.
© 2024 Risk Management

ConnectedGRC
Drive a Connected GRC Program for Improved Agility, Performance, and Resilience
BusinessGRC
Power Business Performance and Resilience
- Enterprise Risk
- Operational Risk
- Operational Resilience
- Business Continuity
- Observation
- Regulatory Change
- Regulatory Engagement
- Case and Incident
- Compliance Advisory
- Internal Audit
- SOX Compliance
- Third-Party Risk
Manage IT and Cyber Risk Proactively
- IT & Cyber Risk
- IT & Cyber Compliance
- IT & Cyber Policy
- IT Vendor Risk
Enable Growth with Purpose
AI-based Knowledge Centric GRC
- Integration
- Marketplace
- Developer Portal
Latest Release

Explore the right questions to ask before buying a Cyber Governance, Risk & Compliance solution.
Discover ConnectedGRC Solutions for Enterprise and Operational Resilience
- Enterprise GRC
- Integrated Risk Management
- CyberSecurity
- Corporate Compliance
- Supplier Risk and Performance
- Digital Risk
- IT and Security Compliance, Policy and Risk
- UK SOX Compliance
- Privacy Compliance
- IDW PS 340 n.F.
- Banking and Financial Services
- Life Sciences

Learn about the EU’s Digital Operational Resilience Act (DORA) and how you can prepare for it.
Explore What Makes MetricStream the Right Choice for Our Customers
Customer Stories
- GRC Journey
- Training & Certification
- Compliance Online

Robert Taylor from LSEG shares his experience on implementing an integrated GRC program with MetricStream
Discover How Our Collaborative Partnerships Drive Innovation and Success
- Our Partners
- Want to become a Partner?

Watch Lucia Roncakova from Deloitte Central Europe, speak on how the partnership with MetricStream provides collaborative GRC solutions
Find Everything You Need to Build Your GRC Journey and Thrive on Risk
Featured Resources
- Analyst Reports
- Case Studies
- Infographics
- Product Overviews
- Solution Briefs
- Whitepapers

Download this report to explore why cyber risk is rising in significance as a business risk.
Learn about our mission, vision, and core values

Gurjeev Sanghera from Shell explains why they chose MetricStream to advance on the GRC journey

6 Risk Assessment Methodologies Types and How to Choose?
Introduction.
Navigating the complex terrain of modern business demands a vigilant approach to protecting an organization’s sensitive information, which is constantly under the threat of various security risks. However, not all risks carry the same weight, and mitigation options vary in terms of both cost and efficacy. The dilemma then becomes: How does one navigate these choices to make well-informed decisions? Here is where risk assessment comes into play.
What is Risk Assessment?
Risk assessment is a systematic process of evaluating potential risks or uncertainties that could affect an organization's objectives, projects, operations, or assets. It involves identifying, analyzing, and prioritizing risks to determine their potential impact and likelihood of occurrence. The goal of risk assessment is to provide decision-makers with valuable information to make informed choices about risk mitigation strategies, resource allocation, and overall risk management .
A good risk assessment examines everything - market volatility, regulatory compliance , IT security, operational disruptions, financial fluctuations, and even natural disasters. These evaluations create a base for an organization to formulate a sturdy action plan.
So, when risks do crop up, businesses aren't left flat-footed; they're agile, adaptable, and resilient.
What are Risk Assessment Methodologies?
Risk assessment methodologies can be considered as your business's secret roadmap, guiding you through an unpredictable world, and ensuring you avoid all the potholes and pitfalls along the way.
They provide systematic, step-by-step procedures to identify, analyze, evaluate, and control potential hazards or threats that might disrupt a business’s functionality or growth.
This particular risk assessment process is essential, helping your company transform abstract concerns into concrete action items. It’s about looking at risks in black and white and choosing the best strategy to ensure you get from Point A to Point B with minimum damage. And just like there isn’t a one-size-fits-all suit, risk assessment methodologies vary, each catering to a different need and nature of risks.
Types of Risk Assessment Methodologies
Quantitative .
This methodology employs numerical data and statistical techniques to quantify risks. It involves the use of various mathematical models, simulations, and decision tree analysis to objectively calculate potential risks. This approach has its charm as it cuts through subjective opinions and potential biases by presenting cold hard facts. Risks are objectively measured, generally in financial terms, based on their potential cost to the organization and the probability of their occurrence. This kind of analytical clarity enables precise decision-making and facilitates easier comparisons between different risks. Quantitative methodology is indeed a practical tool, especially when financial loss and benefits must be meticulously calculated and analyzed. However, just like relying solely on a compass and measuring tape on a mountain trail can miss out on certain elements, quantitative risk assessment also has its limitations, specifically when dealing with non-quantifiable or more complex, subtle risks.
Qualitative
Unlike a hard-science approach, this method allows for judgment based on perception rather than numbers. It maps out possible risks based on subjectivity, where elements like risk severity, potential impact, and probability are ranked using ordinal scales (low, medium, high, or often numbers 1 to 5). Its real strength lies in the flexibility and adaptability that this method brings to the table. Indeed, this approach won't always provide the black-and-white, clear-cut results of a quantitative method, and the danger of bias does exist due to the level of subjectivity. Yet, this human-oriented approach might be your knight in shining armor when dealing with intricate, hard-to-quantify aspects such as reputational risks.
Semi-Quantitative
This approach manages to weave together elements of both qualitative and quantitative methods , possessing the simplicity and familiarity of the former, while allowing for more consistency and better comparative analysis through an injection of numbers. Here, risks are not just subjectively classified but are also numerically rated to obtain more specific risk scores. With these scores, it's like having a scale to weigh each risk factor according to its assigned value. As a result, the assessment provides more refined risk profiles than a purely qualitative approach. In this manner, a semi-quantitative methodology could be the choice for those wanting a broader risk image without drowning in an ocean of data or statistical uncertainty.
Asset-Based
With this method, every individual asset is closely inspected for possible risks, which might affect its functionality, value, or lifecycle. From physical assets like buildings or machines to intangible ones such as brand reputation or patents, each has unique vulnerabilities and threats associated with it. It typically involves four steps:
- Asset Identification: Identify and categorize critical assets, ranging from physical equipment to sensitive data
- Threat Identification: Identify potential threats that could impact the previously mentioned assets, covering scenarios like natural disasters, cyberattacks, or human error.
- Vulnerability Identification: Identify weaknesses that could be exploited by the identified threats, such as outdated software or inadequate security protocols.
- Risk Determination: Analyze the potential impact and likelihood of identified risks to prioritize and determine suitable risk response strategies.
The core of this method is identifying what is crucial to your organizational functionality, ensuring that if a threat does materialize, your most significant assets remain secure and your journey towards your organizational goals continues smoothly.
Vulnerability-Based
Your objective is to find where your organization could be compromised and to evaluate those points in light of their impact on your overall risk scenario. Vulnerabilities could be your business operations that are more prone to disruption, fragile IT systems that can easily be breached, or critical production machinery that lacks adequate preventive maintenance. You must keep a keen eye on both your physical and cyber assets. With the advancing digital landscape, threats could lurk within both domains.
When adopting this approach, identifying all assets is vital, since every business has various resources which are essential for its successful functioning. Post-asset identification, pinpoint the vulnerabilities and evaluate their potential impact, that is, the harm that would follow if a particular vulnerability were exploited. In essence, you're doing an 'integrity check' on your systems, wherein they become sturdier, and your peace of mind, as a business leader, magnifies.
Threat-Based
Threat-based risk assessment is a structured approach to evaluating and mitigating risks that focuses on identifying potential threats or hazards that could impact an organization's assets, operations, or objectives.
It functions by categorizing threats into intentional and unintentional categories, understanding each from an extensive standpoint. For example, consider intentional threats, including everything from organized cybercriminal groups trying to breach your company’s IT defenses to lone hackers manipulating vulnerabilities in the network. Unintentional threats, however, encompass natural disasters, data breaches due to employee negligence, and similar unforeseen incidents.

Factors to Consider When Choosing a Relevant Methodology
Business objectives.
Your organization is a unique entity with distinctive needs. Hence, a 'one-size-fits-all' risk assessment methodology may not be effective. Assess your needs based on your industry, size, culture, and the specific risk landscape you operate within.
Consider the breadth and depth of risk analysis you need. While some methodologies might provide an exhaustive understanding, they may not drill down into intricate details. Select a method that gives the right balance of broad overview and detail-driven insights.
Time and Resources
You need to account for the time, workforce, and financial resources available to you. This will help you choose between an automated tool versus a more manual process, each of which has its unique advantages.
Data Quality
Your decision is as good as the data backing it up. Select a methodology that can ensure accurate, reliable, and up-to-date information is consistently available for assessment.
Your team’s level of proficiency and the organization’s learning culture should guide your decision. An overly complex methodology could pose unnecessary challenges if your team lacks the expertise to operate it efficiently.
Scalability
Your business will evolve with time, and so should your risk assessment methodology. Choose a model that's as agile and adaptable as your ambitions.
As is often the case, your final choice should blend seamlessly into your broader strategic vision and contribute actively to it, becoming less of an afterthought and more of a defining attribute. Balancing rigor and fluidity, strategic direction, and adaptability, the right risk assessment methodology for your organization is a strong defense that aids in fostering an atmosphere of proactive risk management and goal-oriented growth for your business.
How to Choose the Best Risk Assessment Methodology
Top 7 risk management strategies with examples, what is a risk management framework and its components, how to create a successful risk management plan, essential elements of a successful integrated risk management program.

Subscribe for Latest Updates

Ready to get started?
How to Develop a Risk Management Methodology + 6 Popular Types to Choose From
Table of Contents
6 Risk Assessment Methodologies
Infosec risk management methodologies, the risk assessment process.

- April 11, 2023
Emily Bonnie
Senior Content Marketing Manager at Secureframe
Rob Gutierrez
Senior Compliance Manager at Secureframe
Managing risk is something every organization has to do — but there are a variety of risk evaluation approaches, each with its own applications and benefits.
What’s the most effective way for your organization to identify and reduce information security risk? How will you estimate likelihood and impact? What is your company’s acceptable level of risk?
This article will help you answer all of these questions and choose a risk management methodology that protects your organization.
6 common types of risk assessment methodologies
There are several popular approaches to risk assessments for organizations to choose from. Understanding these approaches can help you decide which is the best fit for your needs.
Qualitative risk assessment
In general, there are two approaches to risk assessment: qualitative and quantitative.
With a qualitative approach, you’ll go through different scenarios and answer “what if” questions to identify risks. A risk matrix is commonly used to assign each risk a likelihood and impact (i.e., ‘high,’ ‘medium,’ and ‘low’) score, allowing for easy prioritization. Risks that are both high probability and high impact are the highest priorities, and risks that are both low probability and low impact are the lowest priorities.

Quantitative risk assessment
A quantitative risk assessment approach uses data and numbers to define risk level. Quantitative risk analysis uses data to measure the probability and impact of individual risks. For example, potential cost or time delays can be predicted through Monte Carlo simulations. While this approach might be more precise, it also relies on accurate and complete data.
To illustrate the difference with an example, say your business is located in North Dakota. A qualitative risk assessment would say an earthquake is a low probability and low impact, so there’s little need to invest in seismic server racks. A quantitative risk assessment would use geologic data to conclude that there is a 2% chance of an earthquake over the next 10 years with estimated financial losses of $5k.
Using the Risk = Likelihood x Impact formula, you can then calculate an estimated risk exposure of approximately $100. Since the required seismic server racks are estimated at $15k, the risk falls within your accepted range.
Semi-quantitative risk assessment
A semi-quantitative risk assessment combines these two approaches. It assigns one parameter quantitatively and the other qualitatively.
To continue the earthquake example, a semi-quantitative approach would quantify the likelihood with precise data, such as the geological probability of an earthquake occurring. It would then assign a numerical impact score, say an 8 on a scale of 1-10. According to a semi-quantitative risk assessment, an earthquake would be high impact but very low probability.
Because the insights provided by semi-quantitative risk assessments are limited, they are most often used when the data needed to conduct a fully quantitative risk assessment is either incomplete or unreliable.
Asset-based risk assessment
Asset-based risk assessments focus exclusively on risks posed to an organization’s assets. These can include physical assets such as equipment and buildings, as well as company data and intellectual property.
For this type of risk assessment, organizations first create an asset register. Next, asset owners help identify risks, which are then prioritized based on likelihood and impact. Asset-based risk assessments are typically used when pursuing ISO 27001 certification .
Vulnerability-based risk assessment
This approach helps organizations pinpoint their highest-priority risks. Risk-based vulnerability management solutions typically use vulnerability scanning tools/services, artificial intelligence, and machine learning to identify risks that are both most likely to be exploited and have the highest potential negative impact on the business. These insights help cybersecurity teams focus on the most significant and urgent risks facing their organizations.
Threat-based risk assessment
While an asset-based risk management approach focuses on an organization’s most important assets, a threat-based approach examines the conditions that create and contribute to increased risk. What techniques are threat actors using, and how can you best safeguard against them?
As an example, an asset-based approach may identify the risks of weak password practices across an organization. The result may be implementing a password policy that requires the use of strong passwords or multi-factor authentication.
A threat-based approach would instead focus on social engineering practices and the likelihood of threat actors to target employees and convince them to share passwords or other sensitive information that can be exploited. The result of this assessment may be more frequent employee training around phishing attacks and safe password practices.
Recommended Reading
What Is Compliance Risk? + How To Minimize It
Risk management methodologies for information security
Because risk assessments are so important for businesses in the digital age, many organizations have created defined risk management frameworks for information security. This list includes some of the most popular and respected:
Created by the National Institute of Standards and Technology, the NIST Risk Management Framework (RMF) offers a 7-step process for integrating information security and risk management activities into the system development lifecycle:
- Step 1: Prepare to manage security and privacy risks
- Step 2: Categorize information processed, stored, and transmitted based on impact
- Step 3: Select NIST SP 800-53 controls to safeguard the system
- Step 4: Implement and document controls
- Step 5: Assess control performance
- Step 6: Senior leadership evaluates risk to authorize the system to operate
- Step 7: Continue to monitor controls and risks to the system
ISO 27005:2018
Developed by the International Organization for Standardization (ISO) to support ISO/IEC 27001, ISO/IEC 27005:2018 offers guidelines for managing information security risk. The document supports organizations in identifying, analyzing, evaluating, treating, and monitoring specific information security risks.
OCTAVE stands for Operationally Critical Threat, Asset, and Vulnerability Evaluation. It defines a comprehensive method for identifying, evaluating, and managing information security risks. OCTAVE involves three phases:
- Phase 1: Build Asset-Based Threat Profiles
- Phase 2: Identify Infrastructure Vulnerabilities
- Phase 3: Develop a Security Strategy
NIST SP 800-30 Revision 1
Also developed by the National Institute of Standards and Technology, 800-30 Revision 1 is a guide for conducting risk assessments. This document is one entry is a series of risk management and infosec guidelines developed by a joint task force with the Department of Defense, Intelligence Community, and Committee on National Security Systems. It expands on the guidance outlined in Special Publication 800-30 to include in-depth information on risk factors such as threat sources and events, vulnerabilities, impact, and likelihood of threat occurrence.
Whichever risk management approach or methodology you choose, company management should be closely involved in the decision-making process. They’ll be instrumental in determining your organization’s baseline security criteria and level of acceptable risk.
And by establishing your risk management methodology at the company level, every department will be able to follow the same cohesive process.
Recommended reading

How to Design Effective Key Risk Indicators + Best Practices
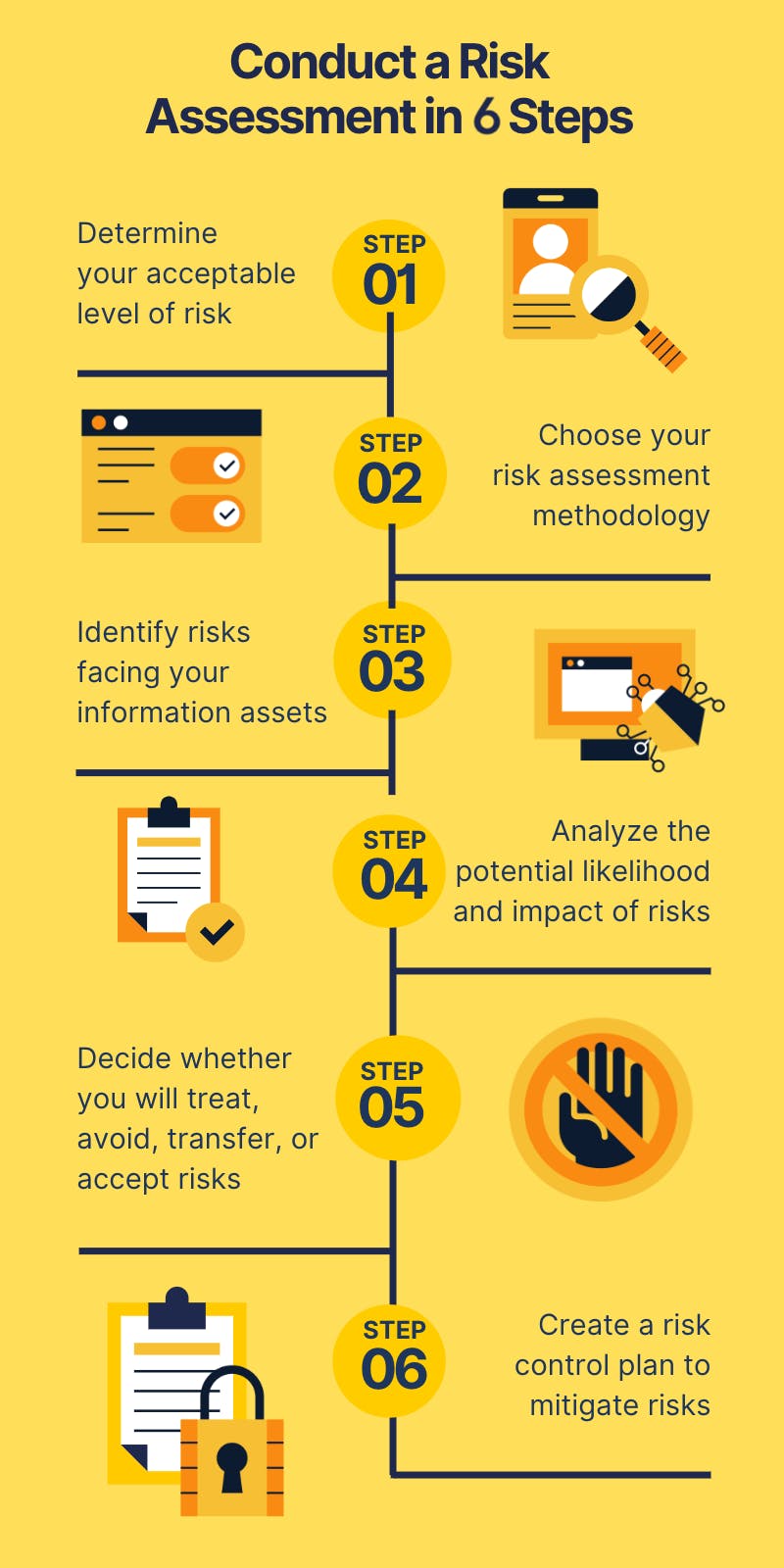
A 6-step risk assessment process
Conducting regular risk assessments is a critical step in keeping your organization safe from a breach and maintaining compliance with many security frameworks . Below we outline the risk management process in six basic steps.
Step 1: Determine your organization’s acceptable level of risk
Risk is an inevitability for all businesses. But with greater awareness and understanding of those risks, companies can identify ways to either resolve, reduce, or work around them to achieve their goals. Sometimes risk can even be turned into opportunity — so it’s important to have a risk management approach that balances risk awareness and strategic risk-taking.
Low risk can lead to stagnation and a lack of innovation. High risk can result in unnecessary losses in both time and money. Effective risk management finds a balance that allows organizations to achieve their goals while minimizing potential losses.
Defining an organization’s risk appetite typically involves a few key steps:
- Define your company’s strategic objectives. What is your organization working to achieve? How much risk are you willing and able to accept in order to achieve those goals?
- For each of the primary targets you’ve identified, decide the acceptable level of risk. undefinedundefinedundefinedundefinedundefined
- Communicate your risk appetite to company stakeholders. Leadership and management teams should work together to discuss risk appetite, mitigation, share feedback, and determine how it will impact day-to-day operations. Writing a risk appetite statement can clarify your strategy for leadership, employees, and other key stakeholders, and allows for more informed risk decisions throughout the company.
Risk tolerance and risk appetite are commonly used interchangeably, but they are not the same thing.
Risk appetite is how much risk your business is willing to accept before treating it. Risk appetite varies widely based on factors like your company’s industry, financial situation, competitive landscape, and company culture. What’s the cost-benefit analysis of each risk? If you have more resources, you may be open to accepting greater risk in order to fuel a faster pace of innovation, for example.
Risk tolerance is how much residual risk you’re willing to accept after treatment. Say you identify a risk that has a 40% probability of occurring, which falls outside your risk appetite. After treating the risk, you bring the probability of it occurring down to 10%. Is 10% residual risk acceptable for your business?
Step 2: Select a risk assessment methodology
Ask yourself the following questions:
- What are you hoping to gain from the assessment? A quantitative risk assessment can provide data-driven insights, while a qualitative assessment often offers greater efficiency.
- What’s the scope of the assessment? Decide if the risk assessment will be conducted across your entire organization or focus on a single department or team.
- What compliance or regulatory requirements do you need to comply with? Some information security standards such as ISO 27001 , SOC 2 , PCI , and HIPAA may have specific risk assessment procedures you’ll need to follow to satisfy requirements.
- What cost or time constraints do you need to work around? An accelerated timeline may require a qualitative assessment over a quantitative one. Organizations that lack the internal expertise to complete a risk assessment may need to hire a third party.
Step 3: Risk identification
Security risks are ever-changing, with new threats popping up seemingly every day. The only way to address risks is to first identify they're there.
Start with a list of information assets and then identify risks and vulnerabilities that could impact data confidentiality, integrity, and availability for each one. You’ll need to consider your hardware (including mobile devices), software, information databases, and intellectual property.
- Vulnerabilities are flaws in the state of your environment that could be exploited.
- Threats are the potential for someone or something to take advantage of a vulnerability.
- Risks are a measure of the likelihood that a given threat will take advantage of a given vulnerability and the impact it will have on the cardholder data environment.
For example, let’s consider a software system that hasn’t been updated with a new version meant to patch a cybersecurity vulnerability. That vulnerability is outdated software, the threat is that a hacker could infiltrate the system, and the cyber security risk is not ensuring software is up-to-date.
Consider these categories of threats and vulnerabilities:
- Digital: Not updating software with security patches
- Physical: Improper disposal of data
- Internal: Employees
- External: Hackers
- Environmental: Natural disaster
Step 4: Risk analysis
Once you’ve identified risks, determine the potential likelihood of each one occurring and its business impact. Remember that impact isn’t always monetary — it could be an impact on your brand’s reputation and customer relationships, a legal or contractual issue, or a threat to your compliance.
- Risk likelihood: Consider how likely it is for a threat to take advantage of a given risk. For example, if you experienced a data breach in the last year, your likelihood of another occurring would be high unless you remediated the vulnerability that caused the breach.
- Risk potential: Consider the damage a risk could pose to your organization. For example, improperly configured firewalls would have a high probability for unnecessary traffic to enter or exit information systems.
Assign each risk a likelihood and impact score. On a scale from 1-10, how probable is it that the incident will occur? How significant would its impact be? These scores will help you prioritize risks in the next step.
Step 5: Risk treatment
No business has unlimited resources. You’ll need to decide which risks you should spend time, money, and effort to address and which fall within your acceptable level of risk.
Now that you’ve analyzed the potential impact of each risk, you can use those scores to prioritize your risk management efforts. A risk matrix can be a helpful tool in visualizing these priorities (find a free risk register + risk matrix template here ).
A risk treatment plan records how your organization has decided to respond to the threats you identified in your security risk assessment.
Most risk assessment methodologies outline four possible ways to treat risk:
- Treat the risk with security controls that reduce the likelihood it will occur
- Avoid the risk by preventing the circumstances where it could occur
- Transfer the risk with a third party (i.e., outsource security efforts to another company, purchase insurance, etc.)
- Accept the risk because the cost of addressing it is greater than the potential damage
Step 6: Risk control and mitigation
Now it’s time to create an action plan and decide your risk mitigation options. Risk controls can include operational processes, policies, and/or technologies designed to reduce the likelihood and/or impact of a risk.
For example, the risk of accidental data loss can be mitigated by conducting regular information systems backups that are stored in different locations.
Each of your identified risks should have an assigned owner who’s responsible for overseeing any risk mitigation tasks, from assigning implementation deadlines to monitoring control effectiveness.
Fortify your organization against threats with Secureframe
However you choose to monitor and manage risk, it’s an ongoing process. An all-in-one GRC solution like Secureframe can help you evaluate security safeguards and identify weaknesses to provide a clear picture of your risk profile and security posture.
Secureframe makes it easy to build and maintain robust risk management processes:
- Monitor risks 24/7 : Continuous monitoring across your tech stack provides complete visibility into critical security and privacy issues. Track and update risk likelihood and impact as well as risk treatment plans.
- Track risks in a single platform : Maintain an up-to-date risk register as you introduce new products and services, your tech environment changes, or to incorporate findings from internal or external audits.
- Assign risk owners : Notification reminders to review and update risks on a regular basis ensure accountability.
Learn more about how Secureframe can help you build a strong, scalable security posture by scheduling a demo today.
Use trust to accelerate growth
Risk Assessment
Risk assessment definition.
A Risk Assessment is a systematic process used to identify, evaluate, and prioritize potential risks that could negatively impact an organization’s objectives, operations, or specific projects. This process helps organizations manage and mitigate these risks before they escalate into critical issues.
What is Risk Assessment?
Risk Assessment is the structured examination of uncertain situations wherein potential threats and their potential consequences are identified. This is done to determine appropriate interventions to eliminate or control these risks and prioritize them based on their likelihood and potential impact.
A risk assessment’s ultimate objective is to ensure individuals’ safety and maintain the operational functionality and reputation of organizations. It delves into the psychology of uncertainty. Assessors don’t just identify threats; they step into the shoes of stakeholders, anticipating anxieties, understanding biases, and gauging emotional impacts. According to Daniel Kahneman’s “Thinking, Fast and Slow” , human beings often exhibit biases in risk evaluation. Integrating cognitive psychology into risk assessment helps organizations better predict human responses to potential threats.
Also, Risk Assessment is a strategic tool that evolves with the times, adapting to new technologies and unpredictable market shifts (distinguish from Risk Register ). For instance, the rise of digital transformation has ushered in cyber threats that traditional risk assessment methods couldn’t have foreseen. As per the World Economic Forum’s Global Risks Report , cyberattacks and data breaches have consistently ranked among the top global risks. This demonstrates the ever-evolving nature of threats and underscores the need for assessments to adapt and be forward-thinking.
Risk Assessment Matrix
A Risk Assessment Matrix, also known as a Probability and Severity matrix, is a visual tool used to evaluate and prioritize risks based on the likelihood of their occurrence and the potential impact or severity of their consequences. The matrix helps organizations to identify which risks need immediate attention and which ones can be monitored or accepted.
Here’s how it generally works:
- Minor (Insignificant impact)
- Low (Limited impact)
- Medium (Moderate impact)
- High (Major/Severe impact)
- Extreme (Catastrophic impact)
When you plot risks on this matrix, you can categorize them based on their position:
- High Likelihood and High Impact : These are critical risks that require immediate attention and action.
- High Likelihood and Low Impact : These risks might happen frequently, but they don’t have a significant consequence. They still need attention, but perhaps not as urgently as the above category.
- Low Likelihood and High Impact : These risks don’t occur frequently, but if they do, they can cause significant harm. Contingency plans are often developed for these types of risks.
- Low Likelihood and Low Impact : These risks can generally be accepted or monitored, as they don’t happen often and don’t have a major impact.
By visually displaying risks in this manner, the Risk Assessment Matrix allows organizations to make informed decisions on where to allocate resources and how to best manage or mitigate identified risks. The matrix serves as a foundational tool in risk management processes across various industries, from project management to health and safety to cybersecurity.
The risk assessment matrix, while a cornerstone today, it has its critics. Some experts, as highlighted in Risk Analysis Journal , argue that its over-simplification can sometimes miss nuances. Balancing traditional matrices with modern analytical tools like AI-powered risk prediction can offer a more holistic assessment.
What are the Five Principles of Risk Assessment?
- Identify Hazards : This is the initial step where potential threats or hazards, both obvious and non-obvious, are identified.
- Risk Estimation: Decide who might be harmed and how. This entails determining which individuals or groups are at risk and understanding the potential harm they could face.
- Risk Evaluation: Evaluate the risks and decide on precautions. Here, the identified risks are ranked, and suitable measures to mitigate or eliminate them are proposed.
- Risk Control: Record your findings and implement measures to mitigate the identified risks. Any professional risk assessment should be documented. This serves as a record and can also serve as a guide for implementing control measures.
- Monitoring and Review: Continuously checking and updating the assessment. Risks change over time, making it crucial to review and update the assessment periodically.
While the five principles of Risk Assessment remain foundational, there’s an emerging sixth principle — ‘ Adaptive Forecasting .’ With the rise of real-time data analytics, organizations are now continually updating risk assessments, not just as a periodic exercise. A study from Harvard Business Review indicates that adaptive risk management can lead to quicker response times in fast-paced industries like finance and technology.
Risk Assessment Examples
- Business Operations : A company might assess risks associated with a new market entry, considering factors like political instability, currency fluctuations, or potential supply chain disruptions.
- IT and Cybersecurity : Businesses may perform risk assessments on their IT infrastructure to identify vulnerabilities that could be exploited by hackers or malware.
- Health and Safety : In industries like construction or manufacturing, risk assessments are conducted to identify potential hazards like machinery malfunctions or exposure to harmful substances.
- Environmental : Companies may evaluate risks related to environmental factors, such as potential spills or emissions that could harm the environment.
Risk Assessment Template
A risk assessment template is a standardized document or software used to simplify the risk assessment process. By following a template, organizations can ensure they are thorough in their assessment, covering all potential risks and following best practices.
Risk assessment is a pivotal component in any organization’s strategic and operational planning. It’s a proactive approach to identifying, understanding, and mitigating potential threats, ensuring safety, and fostering resilience. Risk assessment is fundamental to informed decision-making, whether it’s a business considering expansion or an industry navigating operational hazards.
Related Terms
- SMART Goal Setting
- Moscow Prioritization
- Stakeholders Analysis
- Product Design
- Minimum Viable Product (MVP)
- Customer Acquisition Cost (CAC)
Try Roadmunk for free

IMAGES
VIDEO