

Samsung Electronics—A Detailed Case Study

Devashish Shrivastava
Samsung is a South Korean electronic gadget manufacturer in Samsung Town, Seoul. Samsung Electronics was established by Lee Byung-Chul in 1938 as an exchanging organization.
We all know this information about Samsung. Don't we? But what we don't know? Do you know how much Samsung has grown in these years? What are the Future Plans of Samsung? How much Samsung invested in its R&D? What difficulties did the company face coming all this way? What is the history behind this multinational conglomerate?
Don't worry we got you covered. We have penned down a detailed Case Study on Samsung Electronics. Let's find out in this thoroughly studied Samsung case study.
Let's start the detailed case study from here.
Samsung entered the electronics industry in the late 1960s and the development and shipbuilding ventures in the mid-1970. Following Lee's demise in 1987, Samsung was divided into five business groups - Samsung Group, Shinsegae Group, CJ Group, Hansol Group and Joongang Group.
Some of the notable Samsung industrial subsidiaries include Samsung Electronics, Samsung Heavy Industries Samsung Engineering, and Samsung C&T (separately the world's 13th and 36th biggest development companies). Other notable subsidiaries include Samsung Life Insurance, Samsung Everland, and Cheil Worldwide.
Samsung has a powerful influence on South Korea's monetary advancement, legislative issues, media, and culture. Samsung has played a significant role behind the "Miracle on the Han River". Its subsidiary organizations produce around a fifth of South Korea's complete exports. Samsung's revenue was equivalent to 17% of South Korea's $1,082 billion GDP.
History of Samsung Electronics Samsung's Business Strategy Samsung Rides High In India Business Growth in India Future Plans of Samsung FAQ's
History of Samsung Electronics

1938 (Inception of Samsung)-
- In 1938, Lee Byung-Chul (1910–1987) of a huge landowning family in the Uiryeong region moved to nearby city Daegu and established Samsung Sanghoe.
- Samsung began as a little exchanging organization with forty representatives situated in Su-dong. It managed dried fish, privately developed staple goods and noodles. The organization succeeded and Lee moved its head office to Seoul in 1947.
- When the Korean War broke out, Lee had to leave Seoul. He began a sugar processing plant in Busan named Cheil Jedang. In 1954, Lee founded Cheil Mojik. It was the biggest woollen factory in the country.
- Samsung broadened into a wide range of territories. Lee wanted to build Samsung as a pioneer in a wide scope of enterprises.
- In 1947, Cho Hong-Jai, the Hyosung gathering's organizer, put resources into another organization called Samsung Mulsan Gongsa or the Samsung Trading Corporation with Samsung's founder Lee Byung-Chul. The exchanging firm developed into the present-day Samsung C&T Corporation .
- After few years in business, Cho and Lee got separated due to the differences in the management style. In 1980, Samsung acquired the Gumi-based Hanguk Jeonja Tongsin and entered the telecommunications market . During the initial days, it sold switchboards.
1987 (Demise of Lee Byung-Chul)-
- After Lee's demise in 1987, the Samsung Group was divided into four business gatherings—Samsung Group, Shinsegae Group, CJ Group, and the Hansol Group.
- One Hansol Group agent stated, "Just individuals uninformed of the laws overseeing the business world could think something so ridiculous," while also adding, "When Hansol got separated from the Samsung Group in 1991, it cut off all installment assurances and offer holding ties with Samsung subsidiaries."
- One Hansol Group source attested, "Hansol, Shinsegae, and CJ have been under autonomous administration since their particular divisions from the Samsung Group."
- One Shinsegae retail chain official executive stated, "Shinsegae has no installment certifications related to the Samsung Group." In 1982, it constructed a TV get-together plant in Portugal, a plant in New York in 1984, a plant in Tokyo in 1985 and an office in England in 1996.
2000 (Samsung in 20th Century)
- In 2000, Samsung opened a development center in Warsaw, Poland. It started with set-top-box technology before moving to TV and cell phones. The cell phone stage was created with accomplices and formally propelled with the first Samsung Solstice line of gadgets and different subordinates in 2008. It later emerged into the Samsung Galaxy line of gadgets that is Notes, Edge, and other models.
- In 2010, Samsung declared a ten-year development system based on five businesses. One of these organizations was to be centered around bio-pharmaceuticals in which ₩2,100 billion was invested.
- In the first quarter of 2012, Samsung Electronics turned into the world's biggest cell phone creator by unit deals, surpassing Nokia which had been the market chief since 1998.
- In 2015, Samsung was granted U.S. patents as compared to other organizations like IBM , Google , Sony, Microsoft , and Apple. Samsung got 7,679 utility licenses before 11 December 2015.
- On 2 August 2016, Samsung Electronics revealed the Galaxy Note7 smartphone, which went on sale on 19 August 2016. At the beginning of September 2016, it halted its selling of smartphones due to some problems with the smartphones. Samsung suspended the selling of the smartphones and recalled its units for inspection.
- This happened after certain units of the telephones had batteries with a deformity that made them produce extreme warmth, prompting flames and blasts. Samsung replaced the reviewed units of the telephones with a new version. It was later found that the new version of the Galaxy Note 7 also had the same battery deformity.
- Samsung recalled all Galaxy Note7 cell phones worldwide on 10 October 2016 and permanently ended its production on the same day.
Samsung's Business Strategy
Great business strategies have been applied by Samsung over the years. Not very far back, Samsung wasn't as famous as now. Samsung has now advanced so much that it is the principal contender of Apple Inc. Samsung is the biggest tech business by income and the seventh most significant brand today. The showcasing procedure it applied encouraged Samsung electronics to turn into an industry driving innovation organization.
The Samsung marketing strategy was one of the best systems at any point because it helped a cost-driven organization to change its structure and become a power producer. Due to the consistently changing tastes of purchasers in the innovation business, organizations needed to pursue the pace and offer dynamic and advancing devices to their clients. In this way, Samsung additionally needed to change to pick up the high ground available, and the new Samsung showcasing methodology was the way to advancement.
Some of the business strategies of Samsung Electronics are listed below:
Promotional Mix Of Samsung
Samsung has arrived at fantastic statures with its cell phones which helped the brand to turn into an image of value and unwavering quality for its purchasers.
Samsung Marketing Mix Pricing Strategy and Samsung Advertising Methodology are the two estimating techniques used by the organization. Other than its items, Samsung is celebrated for its customer support . However, item variety is the most dominant part of the promoting blend of Samsung.
- Skimming Price
Like Apple , Samsung uses skimming costs to pick up the high ground over its rivals. For example, Galaxy S6 and S6 Edge are the brand's new results of Samsung conveying the trademark "Next is Now" and guaranteeing that they are the best smartphone maker at any point made.
What will happen when different contenders will dispatch a cell phone with indistinguishable highlights? Straightforward. Samsung will bring down the cost and effectively steal the customers from its competitors.
- Focused Pricing
Samsung experiences issues in increasing an edge over its rivals with different items. Doubtlessly, Samsung is a credible brand. However, regarding home appliances, it can't be in any way, shape, or form outperform LG In the cameras segment and other home appliance units. Also, Samsung cannot compete with Canon and Nikon.
For Samsung to withstand this savage challenge, it's crucial to utilize aggressive valuing of its products. Moreover, Samsung is neither a newbie underway nor non-inventive. For the most part, it is often the first company to be innovative with its products and present a change among its competitors.
- Putting in Samsung Marketing Strategy
Samsung uses divert advertising strategies. Retailers who present the innovation chain will undoubtedly incorporate Samsung in their rundown on account of the firm being a world-celebrated brand. Samsung can likewise fill in as an option for the purchasers. The circulation is a convincing piece of the Samsung promoting methodology.
In specific urban communities, Samsung has an agreement with a solitary dissemination organization that circulates the items all through the city. For example, Mumbai is an incredible case where Samsung conveys its products through a solitary organization.
Samsung Rides High In India

The greatest leader by far in the smartphone business is Samsung Electronics, the world's greatest cell phone and TV producer.
Samsung is India's greatest, versatile brand. It is the developer of Reliance Jio's 4G LTE system — the greatest and busiest information system on the planet.
Discernments, advertise wars, openings, rivalry — now and then from conventional remote adversaries, from nearby upstarts, and emerging Chinese brands trouble Samsung.
Be that as it may, every time Samsung has had the option to fight off the dangers and hold its ground. It has been leading the market in the TV fragment for more than 12 years and in the versatile business for a long time after it toppled Nokia in 2012.
Riding The Smartphone Wave
As indicated by some statistical surveying firms following cell phone shipments, Chinese firm Xiaomi is creeping nearer — or has even surpassed Samsung after December 2017 quarter.
While for the entire year 2017, Samsung was No. 1 in the cell phone space, IDC information indicated Xiaomi drove the last quarter with 26.8% piece of the overall industry. Samsung was at 24.2%. Different players, for example, Vivo, Lenovo, and Oppo stayed at 6.5, 5.6, and 4.9%, separately.
Warsi, who has been working with Samsung for as far back as 12 years and has as of late been advanced as Global Vice President, is unflinching, "These difficulties offer us the chance to work more earnestly for our customers and with our accomplices.
Furthermore, shoppers love marks that emphasis on them," he says. "Samsung is India's No. 1 cell phone organization crosswise over sections — premium, mid and reasonable. That is what makes a difference."
Statistical surveying firm GfK tracks disconnected offers of handsets — which make up around 70% of the market — in which Xiaomi is attempting to make advances.
Samsung had a 42% worth piece of the overall industry in the general cell phone showcase in the nation in 2019 and 55% in the superior fragment as indicated by GfK. An industry official who would not like to be named says that India must be Samsung's greatest market by large volumes.
The thought currently is to become the cell phone business which gets more worth. As indicated by reports, Samsung India's incomes from cell phone deals in 2018-19 remained at an astounding INR 34,300 crore. That is over $5.5 billion and development of 27%. Samsung's nearest adversaries are talking about incomes of $1 billion in India, going up to $2 billion.
Samsung is the world's largest manufacturer of consumer electronics by revenue. As of 2019, Samsung Electronics is the world's second-largest technology company by revenue, and its market capitalization stood at US$301.65 billion, the 18th largest in the world.
Shopper Is At The Center

Samsung is a worldwide advancement powerhouse that leads the patterns. It profoundly put resources in India — 22 years of connections in the exchange, and tremendous interests in neighborhood R&D . It has around 10,000 architects working in research offices in India and is perhaps the greatest scout from the IITs.
"Samsung has a solid brand picture in India, as it has been available in various customer electronic portions with quality items for quite a while now. The brand is trusted because of its long history in the nation, dish India nearness, and a vigorous after deals support for buyers," says Shobhit Srivastava, explore expert at Counterpoint Research.
Indeed, even an item fizzle of the size of the Galaxy Note7 in September 2016 couldn't affect Samsung. While the organization was fast enough to get back to every one of the units that had been sold and cease the gadget totally, Samsung's activities and ensuing effective dispatches of leads like Galaxy S8, Note8, the Galaxy S9 and S9+, which were propelled in February, rescued the harm and raised the profile of the brand as a dependable organization. "They rushed to concede their error and that helped them interface with the perceiving clients of today far superior," says Koshy.
Make For India
Samsung's system 'Make for India', which resounds with the administration's ' Make in India ' activity, was conceived in the late spring of 2015. Samsung India's new President and CEO, H.C. Hong, had recently moved in from Latin America and was looked with the prompt tough assignment of fighting a firm challenge from two nearby versatile organizations that is Micromax and Intex.
Samsung's customer hardware business containing TVs, fridges, and other advanced machines were additionally confronting challenges from Sony and LG.
Around a similar time, the legislature of India propelled its 'Make in India' activity. "In this way, Mr. Hong revealed to us we have been doing Make in India effectively for two decades. What we should concentrate on widely to remain on top of things is Make for India (MFI)," says Dipesh Shah, Managing Director of Samsung R&D Institute in Bengaluru, the greatest R&D community for Samsung outside Korea.
Truth be told, the R&D focuses in India contribute intensely to the improvement of worldwide items, for example, Samsung's lead cell phones (Galaxy S9 and S9+). While different organizations focused on propelling their worldwide items in India, Samsung went about rethinking items for the nation at its R&D focuses.
India is significant for Samsung, thinking of the nation as the second biggest cell phone showcase on the planet today, and it is possibly the greatest undiscovered market for some advanced apparatuses. The entrance of iceboxes, clothes washers, microwaves, and forced air systems are appallingly low because of components like the accessibility of continuous power, social conduct, way of life, and earnings.
Business Growth in India

Samsung India crossed the INR 50,000 crore deals achievement in 2017 according to the simply distributed organization filings with the Registrar of Companies (RoC), uniting its situation as the nation's biggest unadulterated play purchaser products MNC. The Korean mammoth's all-out salary, including turnover and other pay, developed by 15.5% to INR 55,511.9 crore in FY 2017 from INR 48,053 crore in the earlier year regardless of Chinese organizations making genuine advances into the Indian cell phone advertise.
Samsung's cell phone business developed deals at 26.7% to INR 34,261 crore, while the home apparatus business developed by 12% to INR 6,395.6 crore. The organization's TV business stayed dormant at INR 4,481.2 crore even though Samsung held the market initiative.
The organization's net benefit developed at a quicker pace of 38% to INR 4,156.2 crore which industry examiners credited to more concentrate on premium models crosswise over cell phones and customer hardware having higher edges.
Samsung, in its filings, said the 'Make for India' activity, through which a large portion of the items was planned and created given the Indian customer's needs, has been an enormous achievement and a major factor behind the development.
All the units at Samsung India improved their gross productivity with the TV business dramatically increasing it and the home machine business nearly trebling it. The cell phone business was the biggest supporter of gross benefit having developed by 44% in FY17 at INR 5,005.9 crore.
Future Plans of Samsung

Samsung has arranged a new venture of around INR 2,500 crore to transform its India tasks into a center for parts business, two senior industry administrators said. The ventures could be increased further, they included. The Korean organization has set up two new parts fabricating substances in India—Samsung Display Co and Samsung SDI India—for the generation of cell phones and batteries.
Independently, Samsung's funding arm—Samsung Venture Investment Corp—has set up activities in India to support new companies in gadgets equipment and programming organizations. The segment organizations will supply items to both Samsung India and other cell phone merchants who as of now source parts from Samsung's abroad tasks.
Samsung sees a big opportunity for segment business considering the administration's push on 'Make in India' where expense on imported cell phone segments and purchaser hardware is going up, the administrators said.
Samsung is likewise pitching to the administration for fare impetuses so it can even fare segments from India. Samsung Display has just marked an update of comprehension with the Uttar Pradesh government for an INR 1,500 crore plant for assembling telephone show to be operational by one year from now April. The plant will come up in Noida, the administrators said.
Samsung SDI India has plans to set up an assembling unit in India for lithium-particle batteries after the organization was drifted a month ago, according to its administrative filings with the Registrar of Companies (RoC).
As per the administrators, Samsung SDI has plans to contribute another INR 900-1,000 crore and will settle the plans after counseling with the Center post general races. These speculations come after it introduced the world's biggest cell phone fabricating unit in India a year ago at an all-out cost of INR 4,915 crore. It is expected to be completed in 2020.
That's all for now. Share your learnings and findings. What did you learn from this article? Which information surprised or amused you the most? Feel free to reach us and share your feedback. We would love to hear from you. Do comment us in the comments section below. Happy Reading.
Who is the owner of Samsung Electronics?
Samsung Group is the owner of Samsung Electronics.
Who is the Founder of Samsung?
Samsung Electronics was established by Lee Byung-Chul (1910–1987) in 1938 as an exchanging organization.
Who is the current CEO of Samsung?
Kim, Ki Nam, Kim, Hyun Suk and Koh, Dong Jin are the current CEO of multinational conglomerate Samsung.
What does Samsung Electronics make?
Samsung Electronics produces smartphones, TV sets, laptops, solid-state drives, digital cinemas screens, etc.
Is Samsung a Chinese company?
Samsung is a South Korean electronic gadget manufacturer in Samsung Town, Seoul.
What is Samsung's strategy?
- Promotional Mix of Samsung
How large is Samsung Electronics?
Samsung is the world's largest manufacturer of consumer electronics by revenue. Samsung Electronics is the world's second-largest technology company by revenue, and its market capitalization stood at US$ 301.65 billion, the 18th largest in the world.
What are the future plans of Samsung Company?
Samsung has arranged a new venture of around INR 2,500 crore to transform its India tasks into a center for parts business, two senior industry administrators said.
Must have tools for startups - Recommended by StartupTalky
- Convert Visitors into Leads- SeizeLead
- Payment Gateway- Razorpay
- Spy on your Competitors- Adspyder
- Manage your business smoothly- Google Workspace
How Mobicule Utilise AI to Improve Debt Collection Process
This article has been contributed by Siddharth Agarwal, Founder and Managing Director, Mobicule Technologies Pvt Ltd. The recovery of loans is frequently the top priority for lenders in the field of lending because the risk of defaulting is constant. Lenders are increasingly using technology-driven solutions to help in the recovery
Top 12 Popular Cosmetic Brands in India
From ancient times to today, cosmetics have always been a part of our lives. Back then, they were all about natural sources, but now, it's a mix of natural and chemical compounds. Cosmetics cover everything from personal care to fragrances, helping us look and feel our best. Nowadays, makeup isn't
Coaching Institutions' Gross Marketing Technique
Unscrupulous advertising has become the standard in many industries because of the cutthroat nature of modern competition. Even the most sacred and innocent of all sectors, education, which shapes the nation's leaders of tomorrow, has begun to wear shades of grey. Students in today's academically competitive world are always looking
Top 10 Indian Companies by Market Valuation in 2024
India's economy and entrepreneurial spirit have flourished in recent years, leading to the emergence of the top 10 companies by market valuation as the leaders of the country's dynamic corporate landscape in 2024. These companies span various sectors and industries, showcasing their success and innovation and contributing to the country's
Remarkable Recovery: Samsung Crisis Management Case Study
Have you ever wondered how a global tech giant like Samsung managed to navigate a major crisis and bounce back stronger?
In the world of corporate governance, effective crisis management can be the difference between irreparable damage to a company’s reputation and a successful recovery.
In this blog post, we delve into a Samsung crisis management case study to learn about exploding batteries to the intricate strategies employed to restore trust.
Samsung’s journey offers valuable insights into the intricacies of crisis management in the digital age.
Join us as we explore the key lessons learned and best practices from this high-stakes situation, shedding light on the remarkable recovery efforts that propelled Samsung forward.
Let’s learn about sailing through tough times through Samsung crisis management case study
Background of Samsung History and growth of Samsung as a global conglomerate
Samsung, founded in 1938 by Lee Byung-chul, started as a small trading company in South Korea. Over the years, it steadily expanded into various industries, such as textiles, insurance, and retail.
In the 1960s, Samsung ventured into electronics, marking the beginning of its transformation into a global conglomerate.
With a focus on technological innovation and a commitment to quality, Samsung rapidly gained recognition for its consumer electronics products, including televisions and appliances.
Throughout the 1980s and 1990s, Samsung significantly diversified its business portfolio, entering the semiconductor, telecommunications, and shipbuilding industries.
This diversification strategy helped Samsung become a key player in multiple sectors, solidifying its position as a global leader. Notably, Samsung’s semiconductor division became one of the largest chip manufacturers in the world, supplying components to various electronic devices worldwide.
Samsung’s ascent continued in the 2000s, driven by its successful expansion into the mobile phone market. The introduction of the Galaxy series, powered by the Android operating system, catapulted Samsung to the forefront of the smartphone industry.
The company’s innovative designs, cutting-edge features, and aggressive marketing campaigns contributed to its rise as a major competitor to Apple’s iPhone.
With its global reach, Samsung has consistently ranked among the world’s largest technology companies, epitomizing South Korea’s economic prowess and technological advancements.
Samsung has also been considered one the best companies that successfully managed and implemented change initiatives.
Overview of Samsung’s position in the technology industry
In the consumer electronics segment, Samsung has established itself as a dominant force. Its diverse product lineup encompasses televisions, smartphones, tablets, wearables, home appliances, and audio devices.
The Galaxy series of smartphones, in particular, has enjoyed immense popularity and has emerged as a fierce competitor to other industry giants. Samsung’s televisions are also highly regarded for their cutting-edge display technologies, such as QLED and MicroLED.
The company’s advancements in semiconductor technology have contributed to faster computing speeds, increased storage capacities, and improved energy efficiency.
Samsung’s influence extends beyond consumer electronics and semiconductors. The company is actively involved in telecommunications infrastructure, including the development of 5G networks and the production of network equipment.
Samsung has also made notable strides in the realm of software solutions, including its own mobile operating system, Tizen, and various software platforms for smart devices.
Samsung Galaxy Note 7 Crisis
The Note 7 battery issue marked a significant crisis for Samsung, leading to a widespread recall of the flagship smartphone and causing considerable damage to the company’s reputation.
The crisis began in September 2016 when reports emerged of Note 7 devices catching fire or exploding due to faulty batteries. These incidents raised concerns about consumer safety and triggered a wave of negative publicity for Samsung.
Upon receiving initial reports of battery-related incidents, Samsung initially responded by issuing a voluntary recall of the Note 7 in September 2016. The company acknowledged the problem and expressed its commitment to addressing the issue promptly and effectively.
Samsung attributed the battery malfunctions to a manufacturing defect, specifically a flaw in the design that caused a short circuit.
To ensure customer safety, Samsung advised Note 7 owners to power down their devices and refrain from using them. The company swiftly implemented measures to exchange the affected devices, offering customers the option to either replace their Note 7 with a new unit or receive a refund.
Samsung also collaborated with mobile network operators and retail partners to facilitate the recall process.
In its initial response, Samsung took steps to communicate with customers and the public about the issue. The company published official statements expressing regret for the inconvenience caused and assuring customers of its commitment to resolving the problem. Samsung emphasized its dedication to quality and safety, promising to conduct thorough investigations and implement necessary improvements to prevent similar incidents in the future.
Media coverage and public perception during the crisis
During the Note 7 crisis, media coverage played a significant role in shaping public perception and amplifying the negative impact on Samsung’s brand.
The crisis received extensive coverage from both traditional media outlets and online platforms, leading to widespread awareness and public scrutiny. Here’s an overview of media coverage and its influence on public perception:
- News Outlets: Major news organizations across the globe reported on the Note 7 battery issue, highlighting incidents, the recall, and subsequent developments. Television news segments, newspapers, and online news articles extensively covered the crisis , emphasizing the potential safety risks and consumer concerns. The constant media attention contributed to the widespread dissemination of information and increased public awareness of the issue.
- Online Platforms and Social Media: Social media platforms played a pivotal role in the crisis, enabling the rapid spread of information and user-generated content. Users took to platforms such as Twitter, Facebook, and YouTube to share their experiences, express concerns, and criticize Samsung’s handling of the situation. Viral videos, photos, and personal accounts of Note 7 incidents gained traction, further fueling negative sentiment and influencing public perception.
- Expert Analysis and Opinions: Alongside news coverage, experts and industry analysts provided their insights and opinions on the crisis. Their assessments of Samsung’s response, the potential causes of the battery issue, and the implications for the company’s brand reputation contributed to the overall narrative. Expert opinions had the power to sway public perception and shape the understanding of the crisis.
- Consumer Forums and Discussion Platforms: Online forums and discussion boards dedicated to technology and consumer experiences became hubs for discussions surrounding the Note 7 crisis. Consumers shared their frustrations, exchanged information, and warned others about potential risks. These platforms served as gathering places for individuals affected by the crisis and amplified the negative sentiment surrounding Samsung’s brand.
Financial implications and losses incurred by Samsung
The Note 7 crisis had significant financial implications for Samsung, resulting in substantial losses for the company. Here are some of the key financial impacts experienced by Samsung as a result of the crisis:
- Recall and Replacement Costs: The recall and replacement process incurred significant costs for Samsung. The expenses involved in collecting and replacing over 2 million of Note 7 devices, including logistics, shipping, and refurbishment, were substantial. The costs also encompassed the testing and certification of replacement devices to ensure their safety. The total recall cost was estimated at $5.3 billion.
- Decline in Sales and Market Share: The crisis had a detrimental impact on Samsung’s sales and market share in the smartphone industry. As consumer confidence in the Note 7 and Samsung’s brand reputation declined, potential buyers shifted their preferences to alternative smartphone options. The decline in sales of the Note 7, coupled with the negative impact on the perception of other Samsung products, led to a loss of market share for the company.
- Stock Price Decline: The Note 7 crisis had an immediate impact on Samsung’s stock price. News of the battery issue, recalls, and subsequent negative media coverage led to a decline in Samsung’s stock value. Samsung shares fell approximately to 7 percent right after 2 months of the crisis.
Crisis Management Strategy Employed by Samsung
Following are the key aspects of Samsung Galaxy Note 7 crisis management strategy:
Immediate actions taken by Samsung to address the crisis
In the face of the Note 7 crisis, Samsung swiftly implemented a range of immediate actions to address the situation and mitigate the impact on consumers and the company’s brand reputation. Here are some of the key actions taken by Samsung:
- Voluntary Recall: As soon as reports of battery issues emerged, Samsung initiated a voluntary recall of the Note 7. This proactive step demonstrated the company’s commitment to consumer safety and willingness to take responsibility for the problem.
- Temporary Production Halt: To address the root cause of the battery issue, Samsung temporarily halted production of the Note 7. This decision aimed to prevent further distribution of potentially defective devices and allow for thorough investigations and corrective measures.
- Transparent Communication: Samsung made efforts to communicate openly and transparently about the crisis. The company issued official statements and press releases acknowledging the problem, expressing regret for the inconvenience caused, and reassuring customers of its commitment to resolving the issue. Transparent communication was crucial in maintaining trust and providing timely updates to affected consumers.
- Collaboration with Authorities: Samsung collaborated closely with regulatory authorities and industry experts to investigate the battery issue comprehensively. By engaging external expertise, the company aimed to identify the root cause and develop effective solutions. This collaboration demonstrated Samsung’s commitment to finding the best possible resolution.
- Customer Support and Safety Guidelines: Samsung provided clear instructions to consumers regarding the use of Note 7 devices, emphasizing the importance of safety. The company advised customers to power down their devices, participate in the recall, and utilize alternative devices in the interim. This approach prioritized customer safety and aimed to prevent further incidents.
- Increased Battery Testing and Safety Measures: Samsung implemented enhanced battery testing procedures and stringent safety measures to prevent similar incidents in the future. The company adopted more rigorous quality control processes, including additional safety certifications and testing standards, to ensure the highest levels of product safety.
Communication strategies employed by Samsung
Samsung employed various communication strategies to address the Note 7 crisis and manage the impact on its brand reputation. Effective communication was crucial in maintaining transparency, addressing consumer concerns, and rebuilding trust. Here are some of the communication strategies employed by Samsung:
- Official Statements and Press Releases: Samsung issued official statements and press releases to provide updates on the progress of the recall, investigations, and corrective actions. These statements expressed remorse for the inconvenience caused and reiterated the company’s commitment to customer safety. Clear and concise communication helped keep customers informed and reassured them that Samsung was actively working to resolve the issue.
- Direct Customer Communication: Samsung directly communicated with customers to provide instructions and updates on the recall process. The company utilized various channels such as email, SMS messages, and notifications through its official website and smartphone apps. This direct communication ensured that customers received important information and guidance regarding the recall and replacement program.
- Social Media Engagement: Samsung actively engaged with customers and the public on social media platforms, including Twitter, Facebook, and YouTube. The company responded to customer queries, addressed concerns, and provided updates on the progress of the recall. By engaging in two-way communication, Samsung demonstrated its willingness to listen, respond, and provide assistance to affected customers.
- Collaboration with Industry Experts: Samsung collaborated with industry experts, battery manufacturers, and regulatory authorities to investigate the root cause of the battery issue. This collaboration was communicated to the public, showcasing Samsung’s commitment to finding solutions and ensuring that the necessary expertise was involved in resolving the crisis.
- Advertisements and Marketing Campaigns: Samsung launched advertising and marketing campaigns focused on rebuilding trust and emphasizing its commitment to quality and safety. These campaigns highlighted Samsung’s dedication to addressing the issue and regaining consumer confidence. Advertisements often emphasized the company’s rigorous testing procedures and quality control measures to assure customers of the safety of its products.
- CEO Apology: Samsung’s CEO issued a public apology, taking personal responsibility for the crisis and expressing regret for the inconvenience and concern caused to customers. The CEO’s apology aimed to convey sincerity, empathy, and a commitment to rectifying the situation, while also reinforcing the company’s accountability and determination to regain trust. The apology was published on a full page in 03 major US newspapers – the Wall Street Journal, The Washington Post and The New York Times.
Collaborations with regulatory authorities and industry experts
Samsung worked closely with government agencies and regulatory bodies in various countries where incidents related to the Note 7 were reported. The company shared information, conducted investigations, and cooperated with authorities to ensure compliance with safety regulations and guidelines. Collaboration with government agencies helped align efforts to address the crisis and establish industry-wide safety standards.
In the United States, Samsung collaborated with the CPSC, an independent federal agency responsible for ensuring the safety of consumer products. Samsung worked together with the CPSC to investigate the battery issue and coordinate the recall process. This collaboration ensured that the recall efforts followed established safety protocols and provided consumers with accurate information.
Samsung collaborated with battery manufacturers to investigate the specific manufacturing defects that caused the battery issue. The company worked closely with these partners to analyze the battery designs, manufacturing processes, and quality control measures. By involving battery manufacturers in the investigation, Samsung aimed to identify the root cause and implement corrective actions to prevent similar issues in the future.
Samsung engaged independent testing labs to conduct thorough assessments of the Note 7 batteries and verify the effectiveness of corrective measures. These labs specialized in battery testing and certification, providing expertise and unbiased evaluation of the battery performance and safety. Collaboration with independent testing labs helped validate Samsung’s efforts to address the battery issue and instill confidence in the effectiveness of the solutions.
Post-Crisis Recovery and Rebuilding
Samsung implemented more stringent quality control measures across its product development and manufacturing processes. This included enhanced battery testing protocols, increased inspections, and stricter quality assurance standards. By demonstrating a commitment to producing reliable and safe products, Samsung aimed to rebuild customer trust.
Extended Warranty and Customer Support: Samsung extended warranty periods for existing and new devices, including the Note 7, to provide customers with added assurance. The company also enhanced its customer support services, ensuring that customers could easily access assistance, product information, and technical support. These initiatives aimed to demonstrate Samsung’s commitment to customer satisfaction and support.
Launch of subsequent product lines and their impact on brand perception
Following the Note 7 crisis, Samsung launched subsequent product lines, including flagship smartphones like the Galaxy S8 and subsequent iterations. These launches played a crucial role in shaping brand perception and rebuilding trust. Key factors that influenced brand perception and the recovery process include:
- Emphasis on Safety and Quality: Samsung placed a strong emphasis on safety and quality in its subsequent product launches. The company implemented rigorous testing procedures and introduced new safety features to ensure the reliability and safety of its devices. By highlighting these improvements, Samsung aimed to regain customer trust and reassure them of its commitment to producing high-quality products.
- Positive User Experience: Samsung focused on delivering positive user experiences with its new product lines. This included improvements in design, performance, and functionality to enhance customer satisfaction. By providing users with exceptional products, Samsung aimed to rebuild its reputation and generate positive word-of-mouth, contributing to brand recovery.
- Brand Messaging and Marketing: Samsung’s marketing efforts during subsequent product launches were carefully crafted to reinforce positive brand associations and regain customer trust. The company emphasized innovation, customer-centricity, and the commitment to quality and safety. Marketing campaigns highlighted features, benefits, and technological advancements to create a positive brand image and overcome the negative perceptions associated with the Note 7 crisis.
Final Words
Samsung’s handling of the Note 7 crisis serves as a case study in crisis management. Despite the significant financial and reputational setbacks, the company took proactive steps to address the crisis, regain customer trust, and prevent similar incidents in the future.
The Samsung crisis management case study highlights the importance of swift and transparent communication, customer-centric actions, and continuous improvement in product safety and quality. By effectively addressing the crisis, Samsung was able to navigate the challenging situation and rebuild its brand, reaffirming its position as a leading global technology company.
Overall, the Samsung crisis management case study provides valuable insights into how a company can recover from a major setback, restore customer trust, and strengthen its position in the market through strategic actions and a relentless commitment to customer satisfaction and product excellence.
About The Author
Tahir Abbas
Related posts.

Disruptive Change: Examples, Benefits and Risks

ITIL Change Management Roles and Responsibilities

04 Key Concepts of Hyper Learning for Organizational Change
Evaluating Risks and Decisions: A Samsung Case Study Essay
Introduction.
Samsung is a consumer electronics firm based in South Korea with a wide product range that includes computers and smartphones. Founded in 1938, as a grocery store, the company has since grown from a small family-owned enterprise to one of the largest in the world (Regan, 2018). This paper evaluates how the firm applies Enterprise Risk Management (ERM) in its corporate practices to manage risks and business decisions when operating internationally.
A Critical Reflection Based On ERM
The application of ERM policies depends on a myriad of factors. Three main frameworks for conducting reviews include Integrated Risk Management (IRM), IS031000, and COSO-ERM standards (Hessami, 2019). IRM standards seek to evaluate risk management processes based on four main criteria that evaluate financial, strategic, operational, and hazard risks affecting an organization (Coleman, 2018). Comparatively, IS031000 focuses on three main areas of evaluation – principles, frameworks, and processes (Rael, 2017). Comparatively, the COSO-ERM cube focuses on strategic, operational, reporting, and compliance risks as highlighted in figure 1 below.
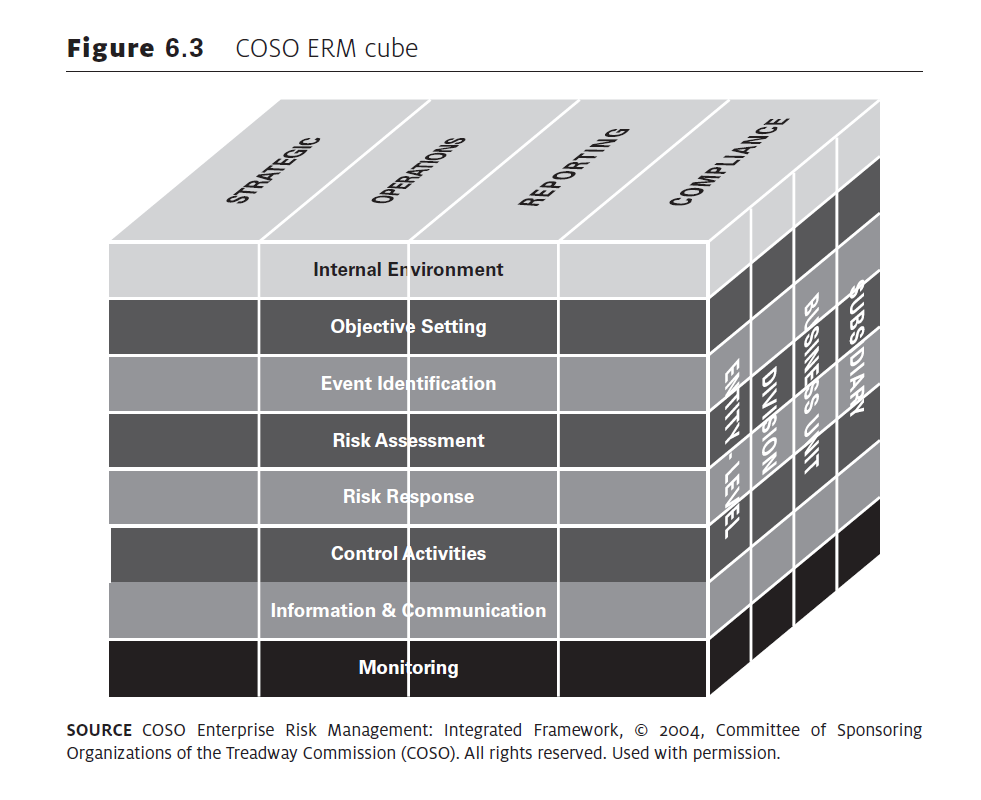
As highlighted in figure 1 above, the COSO-ERM model highlighted above evaluates a company’s internal environment through objective setting, event identification, risk assessment, risk response, control activities, information assessment, and monitoring. In the context of Samsung’s risk management plan, the COSO-ERM framework will be used to analyze the firm’s risks and decisions.
Internal Environment
For purposes of this review, Samsung’s internal environment is evaluated based on the efficacy of its management and leadership styles. Relative to its competitiveness in the global market, the South Korean firm has adopted a combination of western and Asian leadership styles to be successful (Samsung Inc., 2021). For example, its bold risk-taking appetite stems from the assimilation of western ideals in the company’s management framework. Alternatively, its treatment of workers is based on the Asian philosophy of fairness, equity, and hard work (Regan, 2018; Biberhofer et al., 2019). Broadly, the hybrid management and leadership philosophy adopted by Samsung is responsive to its risk management objectives.
Objective Setting
A company’s objectives influence the design of its key processes and activities. Samsung’s objective is to develop superior products and services that enhance societal value (Samsung Inc., 2021). Using the COSO-ERM framework to analyze this objective, quality emerges as a core consideration for the firm’s success in achieving this goal (Ensign, Fast and Hentsch, 2016; Grunert, 2017). The company also complies with existing laws and guidelines to make sure that its business processes are consistent with the global code of conduct for conducting multinational operations.
Event Identification
There are various sources of risk in the consumer electronics industry. Top of the list is the COVID-19 pandemic, which has disrupted supply chain patterns and created shortfalls in demand for goods that were hitherto non-essential. Trade wars pitting western and Asian companies are also significant sources of risk for Samsung (Baack, Czarnecka and Baack, 2018). Therefore, the COVID-19 pandemic and ongoing trade wars between western and Asian nations emerge as significant sources of risk for Samsung Electronics.
Risk Assessment
A comprehensive assessment of Samsung’s risk profile is provided in Table 1 below.
Table 1. Samsung’s risk assessment
According to the risk events highlighted in Table 1 above, two risk categories affect Samsung’s operations – COVID-19 and trade wars. The above risks have been ranked according to the risk profile matrix highlighted in figure 2 below and trade wars is the most impactful
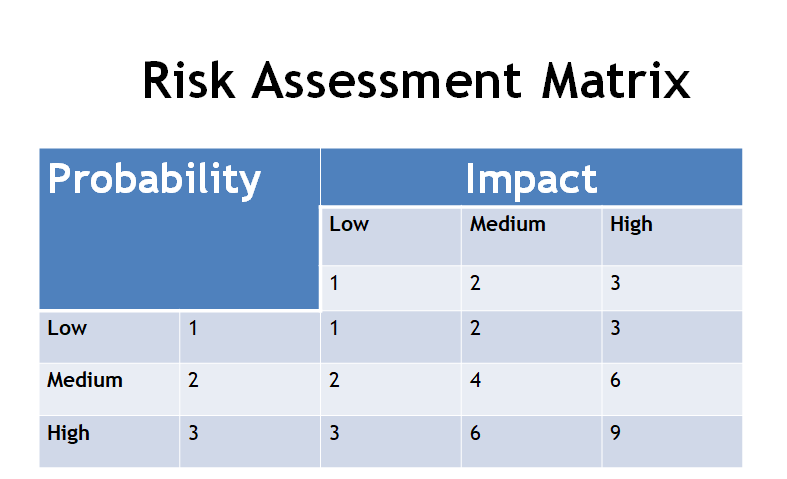
A company’s risk management attitude defines the kind of strategies it is likely to adopt in a risk management scenario. Relative to this statement, Samsung can initiate four major types of responses: tolerate, treat, transfer, or terminate a risk (Kumar, Rahman and Kazmi, 2016). Appropriate risk responses will be to treat and transfer the risks, respectively. Trade wars are transferable because they are initiated at an intergovernmental level and Samsung has little control over associated processes. Comparatively, risks associated with the COVID-19 pandemic should be “treated” because they can be mitigated through the deployment of robust health-based and prevention-oriented strategies (Archetti, 2021; Hutchins, 2018). Modalities for implementing these strategies are highlighted below.
Control Activities
According to the proposed strategies highlighted above, the appropriate risk response for managing risks caused by the COVID-19 pandemic is “treatment.” This is because the firm can develop health safeguards to protect its customers and employees from infections (Adhikari, 2018). Comparatively, risks associated with trade wars can be “transferred” because third-party actors, such as insurance companies, can develop products that protect the firm against this type of risk.
Information and Communication
Most companies use Information and Communication Technology (ICT) tools to carry out various functions, including risk management. Such is the case of Samsung because it uses ICT to carry out sustainable business operations by diversifying its risks across different portfolios (Samsung Securities, 2020; Makrides, Vrontis and Christofi, 2020). At the same time, the company uses ICT in risk identification and assessment because it provides a relatively accurate assessment of the same, relative to other evaluative models (Chopra, Avhad and Jaju, 2021). The risk posed by the adoption of this technology includes system breakdowns and the failure of some employees to understand how to use the company’s risk management software (Pesch et al., 2017). Nonetheless, this risk profile is low and the company has successfully used its ICT infrastructure to manage its risk management activities.
Risk Monitoring
In this paper, the main sources of risk for Samsung have been identified to be trade wars and the COVID-19 pandemic. These risks have implications on the organization if not effectively monitored (Regan, 2018). The two levels of risks should be evaluated weekly to understand their implications on the organization (Rael, 2017). The chief risk manager should collaborate with the Chief Executive Officer (CEO) to understand the implications of these risks on various aspects of the firm’s corporate and industry performance.
Role and Impact of Governance, Technology, and Resilience
Role of governance.
Companies have varied ways of managing their risk categories. Two major strategies are adopted by firms when managing risks is to (i) explain why they have not been addressed as stipulated in corporate governance reports or (ii) to comply with rules and guidelines stipulated in the corporate governance report (Rael, 2017). Samsung’s risk management approach should follow the second approach of explaining situations where corporate governance rules and policies have been followed, or not. This is because the two risk events identified in this document – COVID-19 and trade wars – change periodically, while the company’s corporate management rules are rigid (Grunert, 2017). Explaining the responses may be a useful way of navigating these changes.
Samsung’s CEO should take responsibility for the above actions by making sure that the company’s corporate management guidelines are followed. Alternatively, the firm’s Board of Directors should review the performance of the CEO by reviewing how the company’s overall risk management plan helps in the realization of its goals (Köbis, Soraperra and Shalvi, 2021). The process should be open and transparent to ensure there is sustainability of business process outcomes (Adhikari, 2018). By doing so, the process will be fair and receptive to all parties involved.
Impact of Governance
The impact of Samsung’s corporate governance policies on its risk management processes is vast because of their outreach and influence on various aspects of business performance. In the context of Samsung’s operations, corporate governance plays a critical role in moderating the relationship between managers and employees by defining the expectations and roles of each party (Haenlein et al., 2020; Köbis, Soraperra and Shalvi, 2021). From an organizational standpoint, the company’s corporate governance policies will play a critical role in standardizing operational procedures across various product divisions – especially in the way it manages risk (Rael, 2017). Apple Inc. and Huawei are Samsung’s competitors in the consumer electronics industry, which have developed and implemented similar corporate management policies with varied levels of success (Apple Inc. 2021; Adoko, 2017). From their experience, the failure to implement good corporate governance policies in managing a company’s risk events may result in increased inefficiency and unresponsiveness to the changing nature of a firm’s risk events (Adoko, 2017). Therefore, it is important to make sure that such policies are developed by consulting relevant parties.
Role of Technology
As highlighted in this document, ICT plays a critical role in determining how Samsung makes decisions regarding its risk management processes. Relative to this statement, some researchers suggest that ICT is the foundation for the development of innovation policies for use in the corporate setting (Dimic, Orlov and Äijö, 2019; Köbis, Soraperra and Shalvi, 2021). Nonetheless, given the sporadic nature of Samsung’s risk events – COVID-19 and trade wars – technology will play a critical role in formulating, implementing, and monitoring its risks (Adoko, 2017). Particularly, it will help to track risk events in real time, thereby allowing managers to be informed of their impact on organizations. Some technology tools, such as Skype and Zoom, will also be used to communicate appropriate risk management strategies to respective teams based on data collected from the above-mentioned risk tracking processes.
Impact of Technology
The use of ICT tools to undertake Samsung’s risk management processes will have financial and operational implications on the multinational. From a financial perspective, technology may lead to reductions in operational costs because of its inexpensive nature (Kumar, Rahman and Kazmi, 2016; Archetti, 2021; Hutchins, 2018). The firm may also need to automate some of its risk management processes, such as risk monitoring, to accommodate these changes (Kumar, Rahman and Kazmi, 2016; Archetti, 2021; Hutchins, 2018). Some companies have successfully adopted this strategy to manage their risks (Kemp, 2018; Palmatier and Sridhar, 2017). For example, Google and Apple have used machine-learning techniques to minimize their risk exposures because they provide an effective way of improving their overall risk management plans (Apple Inc., 2021; Kelleher, 2019). Overall, technology will have a positive impact on Samsung’s performance by improving its risk tracking and monitoring processes.
Role of Resilience
As highlighted in this document, risk events may have far-reaching implications on a company’s overall performance. Its resilience determines the effects that these events will have on its overall performance (Lewis, Ricard and Klijn, 2018). In this regard, resilience determines the ability of a company to adapt to the changing dynamics affecting its internal and external operations (Hernaus, Juras and Matic, 2021; Management Association, Information Resources, 2018). Samsung has demonstrated market resilience in the manner it manages its risk exposures (Regan, 2018). For example, by being resilient, the company has addressed its market and product challenges by recalibrating its business processes to mitigate known risks (Regan, 2018). In this regard, its resilience has played a critical role in affirming its position as a dominant company in the consumer electronics business.
Impact of Resilience
As highlighted above, Samsung’s resilience has had a positive effect on its overall business performance. For example, it has been able to address customer concerns in problematic product segments, such as the Samsung Galaxy Note, which caught fire when charging (Regan, 2018). Its resilience in the wake of such missteps has given competitors little room to exaggerate the company’s weaknesses (Bérard and Teyssier, 2018). Therefore, its resilience has helped it to maintain market dominance by countering negative information and experiences from customers and competitors. Based on the above examples, Samsung’s resilience is unmatched in the technology industry.
The insights highlighted in this paper have highlighted the role that ERM and corporate governance play in supporting Samsung’s risk management plan. Two strategies have been proposed for each risk category with the “treatment” option being associated with COVID-19 risks, while the “transfer” option is linked with risks associated with trade wars. It is proposed that the adoption of sound corporate governance policies and the implementation of a robust risk identification criterion will play a critical role in maintaining Samsung’s resilience in the competitive consumer electronics market.
Reference List
Adhikari, A. (ed.). (2018), Strategic Marketing Issues in Emerging Markets . New York, NY: Springer.
Adoko, O. P. (2017), Risk Management Strategies in Public-Private Partnerships . New York, NY: IGI Global.
Apple Inc. (2021). About us. Web.
Archetti, C. (2021), ‘When public relations can heal: an embodied theory of silence for public communication’, Public Relations Inquiry , Vol. 5, No. 1, pp. 1-13.
Baack, D. W., Czarnecka, B. and Baack, D. (2018), International Marketing . London: SAGE.
Bérard, C. and Teyssier, C. (eds.). (2018), Risk Management: A Lever for SME Development and Stakeholder Value Creation . London: John Wiley and Sons.
Biberhofer, P. et al. (2019), ‘Facilitating work performance of sustainability-driven entrepreneurs through higher education: the relevance of competencies, values, worldviews, and opportunities’, The International Journal of Entrepreneurship and Innovation , Vol. 20, No. 1, pp. 21–38.
Chopra, A., Avhad, V. and Jaju, S. (2021), ‘Influencer marketing: an exploratory study to identify antecedents of consumer behavior of millennial’, Business Perspectives and Research , Vol. 9, No. 1, pp. 77–91.
Coleman, L. B. (2018), Managing Organizational Risk Using the Supplier Audit Program: An Auditor’s Guide along The International Audit Trail . London: Quality Press.
Dimic, N., Orlov, V. and Äijö, J. (2019), ‘Bond–equity yield ratio market timing in emerging markets’, Journal of Emerging Market Finance , Vol. 18, No. 1, pp. 52–79.
Ensign, P. C., Fast, J. and Hentsch, S. (2016), ‘Can a technology enterprise transition from niche to wider market appeal in the turbulent digital media industry?’, Vikalpa , Vol. 41, No. 3, pp. 247–260.
Grunert, K. G. (ed.). (2017), Consumer Trends and New Product Opportunities in the Food Sector. Wageningen: Wageningen Academic Publishers.
Haenlein, M. et al. (2020), ‘Navigating the new era of influencer marketing: how to be successful on Instagram, TikTok, and Co.’, California Management Review , Vol. 63, No. 1, pp. 5–25.
Hernaus, T., Juras, A. and Matic, I. (2021), ‘Cross-echelon managerial design competencies: relational coordination in organizational learning and growth performance’, Business Research Quarterly , Vol. 6, No. 1, pp. 445-467.
Hessami, A. G. (eds.). (2019), Perspectives on Risk, Assessment and Management Paradigms . London: Books on Demand.
Hutchins, G. (2018), Supply Chain Risk Management: Completing In the Age of Disruption . London: Greg Hutchins.
Hutchins, G. (2019), Project Risk Management . London: CERM Academy for Enterprise Risk Management.
Kelleher, J. D. (2019), Deep Learning . Massachusetts: MIT Press.
Kemp, K. (2018), Misuse of Market Power: Rationale and Reform . Cambridge, MA: Cambridge University Press.
Köbis, C., Soraperra, I. and Shalvi, S. (2021), ‘The consequences of participating in the sharing economy: a transparency-based sharing framework’, Journal of Management , Vol. 47, No. 1, pp. 317–343.
Kumar, V., Rahman, Z. and Kazmi, A. A. (2016), ‘Assessing the influence of stakeholders on sustainability marketing strategy of Indian companies’, SAGE Open , Vol. 6, No. 2, pp. 987-1109.
Lewis, J. M., Ricard, L. M. and Klijn, E. H. (2018), ‘How innovation drivers, networking and leadership shape public sector innovation capacity’, International Review of Administrative Sciences , Vol. 84, No. 2, pp. 288–307.
Makrides, A., Vrontis, D. and Christofi, M. (2020), ‘The gold rush of digital marketing: assessing prospects of building brand awareness overseas’, Business Perspectives and Research , Vol. 8, No. 1, pp. 4–20.
Management Association, Information Resources. (ed.). (2018), Social Media Marketing: Breakthroughs in Research and Practice: Breakthroughs in Research and Practice . New York, NY: IGI Global.
Palmatier, R. W. and Sridhar, S. (2017), Marketing Strategy: Based on First Principles and Data Analytics. London: Macmillan International Higher Education.
Pesch, U. et al. (2017), ‘Niche entrepreneurs in urban systems integration: on the role of individuals in niche formation’, Environment and Planning A: Economy and Space , Vol. 49, No. 8, pp. 1922–1942.
Rael, R. (2017), Smart Risk Management: A Guide to Identifying and Calibrating Business Risks . London: John Wiley & Sons.
Regan, M. (2018), Samsung . New York, NY: ABDO.
Samsung Inc. (2021), Our mission and values . Web.
Samsung Securities. (2020), Strengthening risk management. Web.
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2023, February 28). Evaluating Risks and Decisions: A Samsung Case Study. https://ivypanda.com/essays/evaluating-risks-and-decisions-a-samsung-case-study/
"Evaluating Risks and Decisions: A Samsung Case Study." IvyPanda , 28 Feb. 2023, ivypanda.com/essays/evaluating-risks-and-decisions-a-samsung-case-study/.
IvyPanda . (2023) 'Evaluating Risks and Decisions: A Samsung Case Study'. 28 February.
IvyPanda . 2023. "Evaluating Risks and Decisions: A Samsung Case Study." February 28, 2023. https://ivypanda.com/essays/evaluating-risks-and-decisions-a-samsung-case-study/.
1. IvyPanda . "Evaluating Risks and Decisions: A Samsung Case Study." February 28, 2023. https://ivypanda.com/essays/evaluating-risks-and-decisions-a-samsung-case-study/.
Bibliography
IvyPanda . "Evaluating Risks and Decisions: A Samsung Case Study." February 28, 2023. https://ivypanda.com/essays/evaluating-risks-and-decisions-a-samsung-case-study/.
- Enterprise Risk Management (ERM): Overview
- The COSO ERM Framework
- Enterprise Risk Management and Default Risk
- Learning to Organise Risk Management in Organisations
- The Importance of Enterprise Risk Management in Today’s Organizations
- Mars Company: Enterprise Risk Management
- Strategic Marketing Issues in Emerging Markets
- Enterprise Risk Management as an Internal Control Framework
- Abbott Laboratories' Risk Management Interventions
- Risk Management: Definition, Types, and Future
- Dealing with Risk and Uncertainty in Business
- Risk Factors Affecting Bank Nordik’s Operations and Risk Management
- A Risk Management Plan For United Airlines
- Risk Management in a Technology Company: Huawei
- Risk Management in a Real Estate Developer Company: Evergrande Group
MBA Knowledge Base
Business • Management • Technology
Home » Business Analysis » Case Study: Samsung’s Innovation Strategy
Case Study: Samsung’s Innovation Strategy
The success of Samsung has been widely acknowledged in the last decade. Samsung, the world’s largest television producer and second largest mobile phone manufacturer, is also the largest firm of flash memory maker. Furthermore, Samsung was ranked by Fast Company Magazine to be third most innovative company in the consumer electronics. The company grew from a local industrial leader into a worldwide consumer electronics brand, with up to 261,000 employees, 14 public listed companies, 470 offices and facilities in 67 countries. Samsung was ranked as 11th world’s most innovative companies. It is one of the two Korean companies in the Top 20 companies. While Sony, the Japan’s biggest consumer electronics, was ranked as 10th, only one position above Samsung. This has brought questions among management gurus how this growing company could drive innovation to create success within a short time and remain innovative despite the difficulties of internationalization . In addition, it could overcome many well-built rivals from Japan and Europe.

Shared vision and top management commitment are the important component leading to create innovative atmosphere . In creating such organization, if leaders are not committed in their actions, innovation couldn’t be systematic in a company. Top executive’s role modelling is one of the main differences between innovative and non-innovative organizations. Moreover, employees should realize a company’s goals to align with their innovative effort. Samsung’s new management beliefs applied in the late 1990’s is “we will devote our human resources and technology to create superior products and services, thereby contributing to a better global society.” This shows the company’s strong willpower to contribute to the worldwide people’s prosperity in the 21st century. This message encourages every employee in the firm to innovate with the clear goal of being global superior producer.
Appropriate Structure
The innovative organization tends to have characteristics of organic structures with open and dynamics systems. At first, the reduction of organizational layer and downsizing are concerned as cost control . An increase in use of information technologies, such as email, internal blog, shared data repository, also leads to the need of eliminating middle management. The possible consequences for this are faster responsiveness to market, higher competitiveness, more flexibility, and reducing processes between divisions. This leads to flatter organisation that is not only the change of organisational structure but also the change of decision-making process . In order to avoid delays and support for rapid innovation, decisions should be delegated to the innovation team. The approval of top management is only needed at the checkpoints or gates of the innovation process. Furthermore, Innovation is not suitable with multi-level hierarchy as the new idea and radical innovation must pass through many approvals with high possibility of ideas being rejected. Moreover, this will discourage strong leaders, who try to overcome its cumbersome, but the slow-response organisation will eventually obstruct their abilities. For example, in 1989, Samsung had 3-7 steps for project approval. This took up 24 days for the proposal to go through 7 approvals to arrive final decision step from the president. On the contrary, proposal in 1995 needed maximum of 3 approvals decided on the same day. This change of the important process leads to speed of running business. Furthermore, the proposal form in 1995 is in English, this signified an attempt for globalization .
Key Individuals
With the goal of creating innovation in the company, Samsung needs the world-class human resources from both technical and business backgrounds. Its branding strategy is not only to create a brand that people trust and admire, but also to be a company that they desire to join. To foster this breakthrough R&D, Samsung set up worldwide objectives to catch the attention of the smartest people from around the world, and retain them. These people will be trained and implanted Korean and Samsung culture through one week of intensive Korean daily conversation class, one week of Orientation about company’s history, philosophy, and culture, and develop general management skills delivered by senior Samsung executives. The recruitment of world’s smartest innovators, inventors and designers are fundamental to the company’s success in creating the future technology.
Besides having the best people for the development of innovative capabilities, Samsung has a tool to identify the key players, such as Project leader, promoters, idea champions, or gatekeeper, in the organization. Experiential education programs that are enjoyable, innovative and effective have performed this identification task. For example in the Samsung Semiconductor unit, 90 managers were organised into groups and assigned to build up new equipment through the use of Lego blocks. The tool was just simple Lego blocks, but the equipment created in this experiment had to be functional. This activity, which required both creativity and teamwork, provided managers comprehension of the role each member played in team. Who is promoter, supporter, idea generator, and critical thinker are identified.
Effective Team-working
Currently, team-working increasingly reflects a deeper recognition that this method of working offers greater economic benefits. Cross-functional teams is an effective tool to bring in different knowledge sets needed for solving production problems, creating new businesses , or develop new strategies. Work as a team needs more participation, higher commitment, sharing knowledge and self-management . This is more organic and flexible approach that helps to initiate innovation implanting across organisational and national boundaries. For example, Automakers from USA and Japan collectively worked on the development of new car model. Committing to consumer trends, Samsung set up a group of about 30 businessmen called CNB (Create New Businesses) who had to discover long-term social and technological fashions and imagine new products, which fulfill promising demands. Samsung has harvested the fruits from its team-working and strong commitment to innovation , transforming low-quality producer to become a brand that create stylish mobile phone. In 2010, its sales of mobile phones were ranked as number one in the US market.
Long-term Commitment to Education
Invest in people is another key initiative needed to emphasize in the development of innovative organisation. Army without essential weapons cannot deliver its full potential. Those needed weapons are knowledge, which has to be developed by best practice training. Companies, such as Hewlett Packard, and Samsung, have committed in training and development programs to help spread innovation capability all over the organisation. Besides internal training programs, offering scholarship, postgraduate study opportunities and international work placement for its staff in 120 offices across 57 countries provide Samsung linkage with renowned universities, also bringing in knowledge and collaboration to the organisation. The by-product from doing so is incentives that help to attract and retain of the best and brightest inventor and businessperson from the global industry.
Extensive Communication
Communication is one of the factors causing failure in investing in ideas that go wrong since the beginning. These are those ideas that do not align with the company’s need. Communication within company about its strategy and customer demands is needed for the clear innovation pathways of researchers. Idea generated from either internal or external organisation must go through many steps of modification before adopting into a company. These steps become troubles for the huge companies. In the case of Samsung, idea management has been introduced to manage ideas from thinkers and distribute them all over the company. They will be evaluated by colleagues, supervisors, or assigned review staffs who add views, opinions and knowledge. In addition to internal communication, networking between firms is also key component in the creation of innovation . The network organisation is a group of several independent companies, which perform different tasks and contract one another. For example, one firm in the network focus on research and product design, another manufactures it, and a third does distribution. This approach gains a wide acceptance as it has strong rationale including rapid change of business environment , the cumbersome of large-size companies, importance of speed and flexibility. Moreover, partners’ collaboration helps to blend and complement different core competency in creating better innovation. Samsung has utilized this concept by building a team, called TechnoValley, undertaking only planning and marketing of product. Other partners in the network took care of technology, production, distribution, and promotion.
High Involvement in Innovation
Building a visionary company requires 1 percent vision and 99 percent alignment. In order to build a sustainable innovation culture, staffs have to practice innovation in everything they do. Practicing to tackle small challenge will make them ready for a bigger challenge. Samsung manager plays an important role in supporting this culture of practicing innovation by encouraging the innovation process and not pushing employees to short circuit the solution process.
External Forces
External forces shapes Samsung to become technology leaders. Previously, closed innovation was the model that Samsung Electronics followed. They invested in the best people and centralized their R&D unit. Today, Samsung cannot depend only on internal innovations, which may create the advanced operating system for mobile phone but not attractive one. Samsung open innovation center established to create striking design and user-friendly interface of Samsung mobile phone. It successfully engaged customers and suppliers in the innovation process at the early stage. Being based in Korea with large group of young technology-concerned consumers provides Samsung an innovative edge in consumer electronics including mobile phones. The replacement rate for mobile phones in Korea is estimated at 6-18 months, thanks to young Koreans who swiftly adapt new technology. Therefore, these trendy people have participated in testing and giving feedback, which provide significant information about customers’ desire. Korea, therefore, becomes an invaluable testing location for innovations prior to the companies unveil them on the world stage.
Creative Climate
Public reward for those who distinguish themselves as mains actor in innovation culture and who promote the value of innovation is the powerful tool to expand innovative thinking throughout the enterprise. There are many examples of escalating the visibility of innovation success, such as the company innovation award, inventor hall of fame. This illustrates the commitment a company have on its innovation and inspire employees by making them proud of their success. Idea management through the use of IT have increased the rate of product and process improvement, as contributions of ideas are traceable. It open up the communication all over the company and promote culture of sharing and creativity. Ideas are developed and talked widely not only in vertical but in horizontal fashion leading to innovative atmosphere. After the introduction of knowledge management solution in Samsung Electronics, there was a change in organizational climate. Employees have been become confident to be more suggestive, trustful, responsive to change, and eager to innovate. Forum and blog postings are the place for knowledge sharing where an automatic rewarding system is executed. The profitability of the products launched, have been chosen as the innovation performance indicators.
Learning Organization
Sharing knowledge and skill of employees brings about innovative performance. Samsung has identified two main challenges in the creation of learning organisation that are knowledge discovery and knowledge sharing. In the past, problems occurred due to lack of knowledge management, for example, lost of valuable knowledge from poor management, or repeating the same failures. To tackle such problems, organizational mechanisms and technological solutions to facilitate the innovation process in Samsung have been introduced. Firstly, Samsung Brainstorming Hours has been arranged to capture and spread ideas in any step of innovation process from idea generation to conversion and commercialization. This is not applied only in the new product development process, but also solving complex problems or business improvement. Two hours weekly meeting for cross-functional team in the room with tall windows, wireless connection, big-screen TV, snacks and drinks is designed to foster innovation process. This comfortable surroundings helps innovation workers to socialise with each other and share ideas. Secondly, company-wide simple but powerful blog has been introduced to encourage knowledge sharing and discovery. The blog helps employees understand and discuss ideas so as to extend previous knowledge continuously. Thirdly, knowledge warehouses have been built to have codifiable critical knowledge stored and accessible throughout Samsung Company. The “Lessons Learned System with Alert function” has been used to manage this knowledge and share it. For storing lesson learned, project managers has been trained about how and what knowledge to collect and given the project management manuals including many useful procedures such as how to write a closing report, how to create and store a project model, how to perform an After Action Review. In order to control overwhelming information, Alerts system notifies employees of newly stored knowledge that might be of interest and useful to their work.
Samsung has successfully transformed from local low quality manufacturer to a brand that produce admirable and stylish consumer electronics. Company performance has proven that Samsung has come to the right direction in last decade. The achievement of becoming innovative organisation started from the declaration to be the global leader in the industry in late 1990s. After the re-configuration and adopting team-working practice, Samsung organisation has been altered to be flexible and organic, leading to ability to develop innovative capability. In addition to the recruitment of the best people into the organization , Samsung has an experimental education tool to identify the key individuals, such as project leader, promoters, or gatekeeper, so as to blend different roles in creating innovation . These people are working under the well-designed knowledge management system and trustful and suggestive communication with the support of supervisors, fostering creative climate. Rewards system for innovative contributor, organisational mechanism and technological solutions has brought about the knowledge discovery and sharing throughout the company, creating learning organisation that sustains Samsung innovation competency.
Related Posts:
- Becoming a Successful Learning Organisation: Case Study of Apple
- Case Study of Cemex: Incorporating IT into Business
- SWOT Analysis of McDonald's
- Case Study: Reasons Behind the Collapse of Research in Motion (RIM)
- Case Study of Apple: Competitive Advantage Through Innovation
- Case Study on Business Strategies: Failure Stories of Gateway and Alcatel
- Case Study of Dyson: Competitive Advantage through Innovation
- Porters Five Forces Analysis of Samsung
- Case Study: L'Oreal's Customer- Based Brand Equity (CBBE) Model
- Case Study: The Daewoo Group and the Asian Financial Crisis
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
- Open access
- Published: 21 October 2019
Planting and harvesting innovation - an analysis of Samsung Electronics
- Seung Hoon Jang ORCID: orcid.org/0000-0001-7984-7383 1 ,
- Sang M. Lee 2 ,
- Taewan Kim 3 &
- Donghyun Choi 4
International Journal of Quality Innovation volume 5 , Article number: 7 ( 2019 ) Cite this article
22k Accesses
1 Citations
2 Altmetric
Metrics details
This study explores how firms manage the entire life cycle of innovation projects based on the framework of harvesting and planting innovation. While harvesting innovation seeks new products in the expectation of financial performance in the short term, planting innovation pursues creating value over a long time period. Without proper management of the process of planting and harvesting innovation, firms with limited resources may not be successful in launching innovative new products to seize a momentum in high tech industries. To examine this issue, the case of Samsung Electronics (SE), now an electronics giant originated from a former developing country, is analyzed. SE has shown to effectively utilize co-innovation to maintain numerous planting and harvesting innovation projects. Both researchers and practitioners would be interested in learning about how SE shared risks of innovation investment with external partners at the early stage of innovation cycles.
Introduction
Globalization and advances in technologies have made the global market extremely dynamic and competitive. While companies like Apple have created new customer value by introducing such products as iMac computer and iPhone, many other firms have failed to adapt to the fast-changing environment. Kodak, the creator of the film camera, became history since it failed to adapt to the digital era in a timely fashion. To compete successfully in the dynamic global market, organizations must continuously innovate ways to create value [ 1 ]. Thus, innovation has been an important topic to both management researchers and practitioners [ 2 ]. Many studies have explored the relationship between innovative activities and organizational performance [ 3 , 4 ]. The firm’s ability of managing innovative projects has been considered as a key dynamic capability, resulting in new product development [ 5 ]. Innovative activities of the firm have generally shown to positively impact organizational outcome.
Although a number of studies in this research stream have introduced various types of innovation based on learning styles [ 6 , 7 ] or objects [ 3 ], few have paid attention to the timing of financial return from innovation. Given the importance of financial payoff from innovation for firm survival and sustained competitive advantage, research on how a real business should manage both innovation and cash flow is critical. Thus, in this study, we intend to answer the following two research questions.
RQ1: Which classification of innovation can best explain the heterogeneous timing of financial payoff realization?
To answer this question, we applied a classification scheme of planting and harvesting innovation [ 8 , 9 ]. Planting innovation involves pursuing potential sources of competitive advantage, including original technology, which may create value in a long term perspective. In contrast, harvesting innovation aims to develop new ways to monetize planted innovation, including new products for market launching, in the expectation of commercial success in a relatively short term. The aim of this research stream is to determine how to implement planting and harvesting innovation and measure the results of ensuing innovative activities. From this perspective, this study examines how a real global firm manages both types of innovation.
RQ2: How are planting and harvesting activities of innovation actually implemented in a successful global business firm?
To answer this question, we focus on Samsung Electronics (SE) which has become the world’s largest electronics firm through successful planting and harvesting of innovation. While SE has developed many innovative new commercial products, it has focused on fundamental breakthrough technologies as the source of future growth momentum. This case may provide valuable implications for firms from developing economies. To compete in high tech industries, these businesses need to invest a large amount of capital to risky innovation projects. Otherwise, they may remain low value added entities, like assemblers or fast followers. The case of SE, like many other success stories, exhibits a possibility that multinationals originated from developing countries can become leading global firms based on their efforts and vision for breakthrough innovations.
Given the current turbulent global business environment, as observed by trade disputes between the USA and China and the recently disrupted supply of critical input resources from Japan to Korea, it is imperative for firms to develop core competences based on innovation. In the digital age, businesses must rely on innovation to enhance their dynamic capabilities [ 10 ] to enhance agility, flexibility, and resilience for value creation [ 1 ]. Thus, this study which focuses on the effective management of planting and harvesting innovation is expected to make important contributions to the literature.
This study examines how firms can implement innovation projects for both short- and long-term perspectives. For this purpose, we first reviewed the literature for major research streams of innovation. Then, a case method is used to examine how planting and harvesting of innovation have helped SE became a dominant global electronics firm, around 2012. In addition to secondary data, executive interviews reported in media also describe how SE employees implemented planting and harvesting innovation. The results of qualitative analyses are presented and articulated. Finally, the implications and limitations of this research are presented. The framework of planting and harvesting innovation provides a theoretical background on how firms can strive for both short-term cash flow and a long-term momentum despite their limited resources. Furthermore, the study results provide insights to practitioners through the case study of SE which struggled initially to save the cost of innovation by collaborating with external partners for planting and harvesting innovation.
Innovation under resource constraints
Planting versus harvesting innovation.
Researchers in various fields, including economics, sociology, and technology management, have been interested in innovation [ 11 ]. The characteristics of innovative outcomes have been investigated as a major research agenda [ 12 , 13 ]. As Damanpour and colleagues [ 14 ] suggested, the introduction of novel ideas or technologies is the core of innovation. According to Van de Ven [ 15 ], innovation can be described as “the development and implementation of new ideas by people who over time engage in transactions with others within an institutional order ([ 15 ], p590).” Several definitions of innovation have focused on how to apply creativity to business operations and processes [ 15 , 16 ]. These studies imply that the main focus of innovation research has been on whether the firm creates new tangible or intangible values.
However, innovation has shown to lead to varied results. The meta-analysis by Rosenbusch et al. [ 17 ] reported that different contexts explain heterogeneous outcomes resulting from innovation. Even if firms implement similar innovation projects, the result can be different due to environmental factors. In addition, innovation sometimes improves the value of marketing skills rather than creating new technical capabilities [ 18 , 19 ]. What these results imply is that characteristics of innovative activities are complex. Since a single concept cannot explain the nature and outcome of innovation, researchers need to consider diverse classifications to explain the phenomena of innovation. Given the importance of cash flow in business, a greater focus is required on the influence of innovation on the survival and prosperity of the firm. Even when firms obtain breakthrough technologies, they may not survive when they fail to create new products/services and resulting cash flow as discussed by Jang [ 8 ] and Jang and Grandzol [ 9 ]. Furthermore, the large amount of investment needed for innovative activities requires firms to prioritize and manage their projects based on the commercial potential. Thus, there is a need to search for a new framework that can provide better explanations on innovation with respect to this issue. The most existing classifications of innovation are not based on the timing of financial outcomes of innovative activities.
One of the typologies regarding this topic is the categorization of radical and incremental innovation based on the sharpness of change in innovative practices [ 20 ]. A more drastic transformation can be expected from radical innovation projects while a relatively slight newness can be added to existing technologies during the incremental innovation process. Since radical innovation can pursue both drastic breakthrough and immediate commercialization, there exists the disparity between the distinction of radical and incremental innovation, the main focus of this paper. Space shuttle can be considered as an example of radical innovation as the realization of reusable spacecraft but it is generally considered as a product for immediate use rather than a long-term growth momentum. Such discrepancy leads researchers to develop a new categorization of innovation based on the expected timing of financial outcome.
The Code-Division Multiple Access (CDMA) wireless technology is an interesting case for this point. The CDMA technology was developed by Qualcomm ( www.qualcomm.com ), but the commercial CDMA phones were first created and produced by Korean manufacturers, including SE and LG. While Qualcomm was interested in developing CDMA as planting innovation, SE and LG focused on commercializing the technology for harvesting that innovation. Qualcomm could benefit from licensing fees in the long term with the success of commercial products based on CDMA. In contrast, the short-term cash flow was derived by SE and LG as they sold more CDMA phones to individual consumers.
From this perspective, innovation can be categorized based on its relatedness to the firm’s performance in the short or long term [ 8 , 9 ]. While certain types of innovative activities may result in an increase of the firm resources engaged in the current competition, others can create value that has long-term potential. This approach modifies the definition of innovations by Gumusluoglu and Ilsev [ 21 ] as described in Jang [ 8 ] and Jang and Grandzol [ 9 ]. First, harvesting innovation can be described as the development of a new resource that can help launch new products/services in the short term. New products, such as Toyota Prius, would be a good example of this type of innovation. Planting innovation refers to the creation of potential firm resources that are based on the state-of-the-art innovation in the expectation of long-term financial benefits. For instance, the invention of hybrid engine technology “plants” potential for future value while the creation of a hybrid car like Prius “harvests” the results of the planting of that innovation.
There are several reasons why planting innovation may not result in new commercial products/services in the short term. First, there may be social constraints that would not allow the use of innovative technology, resulting in no market for new products/services. The commercial use of human stem cell research in the USA has been prohibited by the Food and Drug Administration [ 22 ]. Firms initiating planting innovation in this area cannot expect commercial success due to this regulation, except perhaps in other countries. Second, firms may need to wait for the advent of other complementing technologies for the commercialization process. Thus, firms face a high degree of uncertainty about the financial outcome of planting innovation in the long term, especially in the biotech industry. The development of a new technology usually has a high probability of failure. Therefore, planting innovation may not lead to financial gains in the short term even if firms succeed in developing a technology.
The characteristic of planting innovation makes it distinct from invention. Innovation requires entrepreneurial utilization of technological newness by definition, while invention includes scientific and/or technological breakthrough for discovery purposes [ 23 ]. Firms invest in planting innovation projects in the expectation of long-term profits. Although the result of planting innovation may directly create cash flows in the form of patent fee, firms usually wait until finding out how to apply the result of planting innovation. In contrast, harvesting innovation pursues short-term profits by launching new products or services. In the 1970s, the Palo Alto Research Center (PARC) at Xerox initiated the development of innovative technologies such as Ethernet (or LAN technology) and copper wire-based Ethernet communication [ 24 ]. Due to the lack of commercial intention of Xerox both short and long term, these developments can be classified as examples of invention rather than planting innovation.
Given the heterogeneous characteristics of planting and harvesting innovation, ambidexterity can be important in balancing such innovative activities. Studies on exploitative and explorative innovations have examined this issue [ 6 , 7 , 25 ]. Since pioneering efforts for new processes or technology involve much risk, firms need to optimize the return of their investment in both types of innovation. One possible approach is to utilize external capabilities through M&A, alliances, or industry-academia collaborations through open innovation. Such arrangements would allow firms to share the risk of innovation with other participants [ 1 ].
In addition, convergence has played a major role in explaining value added activities in modern firms [ 1 , 26 ]. Globalization has encouraged the convergence revolution which allows value creation from the synergy of diverse disciplines, industries including IT, biotechnology, and nanotechnology [ 26 ]. The co-innovation platform helps converge diverse types of innovations for value creation [ 1 ]. Multinationals participating in co-innovation are expected to collaborate with stakeholders, including suppliers, customers, partners, and outsiders. Therefore, outside stakeholders can be active partners who co-create shared goals.
Overall, the classification of innovation can contribute to research by providing clearer guidelines related to the timing of financial outcome of innovation. While planting innovation can result in potential resources for long-term value creation, harvesting innovation is intended to generate continuous cash flows to those engaged in the current market. Following the case of exploitative and explorative innovation, researchers in this field should also consider ambidexterity of the organization. By doing so, firms under resource constraints can be prepared for an optimal portfolio of innovation projects, resulting in better organizational performance in the long term.
- Case analysis
In this study, the case of Samsung Electronics (SE), now the largest electronic firm in the world from a former emerging economy, is examined to unveil the processes of harvesting and planting innovation and their results. Innovative activities have been the core strength of SE and are expected to continue creating value for SE. The Mission 2020 of Samsung ( http://www.samsung.com ) states that it will “inspire the world, create the world” through creative and innovative solutions. This implies that the firm intends to pursue innovation over time beyond the development of commercial products for short-term returns.
Several qualitative techniques are employed to investigate the SE case. First, we collected articles including executive interviews from 2000 to 2012. The articles were manually coded into planting and harvesting innovation frameworks after a careful review of contents. News reports were analyzed via local portal sites, including Lexis-Nexis ( http://www.lexisnexis.com ) and Naver ( www.naver.com ). Particularly, we searched Naver, the major Korean portal website, to collect news articles concerning SE research topics from 2002 to 2012. We chose this period, 2002 and 2012, to collect data for this study as this is when SE made the significant transformation to become a dominant global IT leader. The search keywords used were “Samsung Electronics” and “Innovation.” The search using the keywords assured the study to verify that all related articles are captured. After removing duplicates, we investigated the contents of 183 related news articles. Based on the analysis, all the key interviews of executives and managers at SE were collected and examined. In addition, the other secondary data sources like the websites of companies, universities, and local governments were examined.
Samsung Electronics
SE has been a major global player in electronics and related industries for over three decades. Hoovers ( www.hoovers.com ), a leading corporate information provider on large businesses, describes the overall state of this firm as the new “Electronics Samson.” In year 2015, it reported $171 billion revenue and $16 billion net profit. Its major products include digital electronics, semiconductors, and DVD players. Financial Times ranked Samsung Electronics as 19th in their 2015 FT Global 500 ( www.ft.com/ft500 ). It is beyond doubt that this firm has been successful in creating value for its customers.
The webpage of Samsung Electronics ( www.samsung.com ) and Samsung C&T ( www.samsungcnt.co.kr ) describes the history of Samsung Group and Electronics as follows. Samsung group was founded in 1938 as a small retail firm in Daegu, Korea. The founding chairman, Lee Byung-Chull, established Samsung-Sanyo Electronics to diversify the business in 1969. As the name implies, the firm collaborated with Japan’s electronics giant Sanyo. It began production of black-and-white TV sets for the first time in 1970, as an outsource manufacturer. After changing its name to Samsung Electronics, the firm began to produce color TV sets, video recorders, microwaves, and personal computers. It has rapidly developed as a global firm since it entered the semiconductor industry in the early 1980s. Since South Korea has recently been accepted as a developed economy [ 27 ], it can be said that SE began as an emerging market firm.
Given the fact that SE was founded only about five decades ago, the current performance and growth are astonishing. Despite the current status, the firm used to be considered as a fast follower [ 28 ]. SE had focused on producing existing products with better quality at lower prices than other global firms. It is an interesting research topic to examine how and why SE has evolved into a global giant in the electronics industry.
To provide an explanation on this issue, we investigated how SE has implemented innovation to achieve strategic objectives. In 2001, President of Booz Allen and Hamilton Korea stated that Korean firms need to pursue breakthrough innovations to adapt to new market environments [ 29 ]. In other words, SE as well as other major Korean manufacturers began to pursue innovation rather than continue to follow market leaders to survive in the dynamic global marketplace.
Harvesting innovation at Samsung Electronics
SE has engaged in various innovation activities to gain global competitive advantage. By doing so, the firm has been able to create value and benefit from new markets with expectations of stable cash inflows. For instance, SE developed new products like Rambus DRAM and Nand flash memory rather than increasing the accumulation rate of semiconductors [ 28 ]. Since these new products reflect the needs of customers, including PC or smartphone manufacturers, the innovation brought a large amount of profit in the short term. Given the astonishing results that SE has accomplished, its process of harvesting innovation has drawn much attention.
SE has continued implementing innovative activities steadily. The Value Innovation Program (VIP) Centre, setup in 1998, has played a key role in developing innovative new products at SE [ 28 , 30 , 31 ]. This Centre has shown to nurture creativity and broaden the ideas of R&D staff. As the chief researcher at SE stated, the introduction of value innovation methods has contributed to the creation of many new ideas [ 28 ]. Through this system, all participants were expected to overcome the trap of past success syndrome, leading to what is possible.
Blue Ocean Strategy (BOS) [ 32 ] has been the backbone of the harvesting innovation process at SE [ 30 ]. SE invited W. Kim, the main author of BOS, to train its executives. Senior executives have encouraged the dissemination of value innovation at SE based on the BOS approach [ 33 ]. SE strives to create value which its customers never even expected through value innovation for new products. SE’s value innovation includes value management and value creation [ 33 ]. While the former focuses on cost reduction and efficiency improvement, the latter aims to generate added value. Therefore, the firm searches for creative ideas rather than implementing traditional continuous improvement type programs.
SE has found practical tools to implement harvesting innovation based on BOS [ 31 ]. First, the VIP Centre has utilized the strategy canvas, a framework of implementing BOS [ 32 , 34 ]. In the Centre, managerial decisions on important projects have been made based on the value curve of each unit against competitors, resulting in new products like 40-inch LCD TV. In addition, the “7 Tools Method” practiced in Japan, which enables firms to empirically recognize value factors of their customers, was introduced [ 35 ]. For instance, a survey of 226 Japanese employees triggered the production of a laptop that works well even in a bad wireless environment. These types of techniques have helped SE create new products successfully by reflecting innate needs and requirements of individual and business customers.
It has been reported that all of the creative ideas from the VIP Centre have been reflected in the design and development of new products of SE [ 36 ]. As a result, innovativeness of the firm’s new products has been globally recognized as the numerous Innovation Awards of the Consumer Electronics Association (CEA) attest (see Table 1 ). These achievements prove that the innovative results of SE have been widely recognized by professionals in the field as well as ordinary customers. SE has succeeded in developing new products through harvesting innovation activities.
Planting innovation at Samsung Electronics
SE has also focused on the creation of innovative ideas which may not realize any meaningful revenue in the short term. The major results of planting innovation are original technologies which can result in competitive advantage and lead to future business success. The CEO of SE stressed the importance of “technology preparation management,” pursuing core technologies in order to respond to the convergence across technologies and products [ 37 ]. This statement exhibits the strong will of top management of SE to implement the planting innovation strategy.
The Samsung Advanced Institute of Technology (SAIT) has played a critical role in developing original technologies. The website ( www.site.samsung.com ) describes the research efforts currently in place. The Future IT and Convergence domain seeks technologies across real 3D processing, communication theory and network, multicore processing, data intelligence, and medical imaging. The New Materials and Nanotechnology domain aims at developing flexible electronics, solid state lighting, film ceramic crystal composite materials, micro-system integration, oxide materials and devices, spintronics, and nanostructure and materials research. The Energy and Environment domain focuses on energy storage, energy conversion, and environment fields. The Bio and Health domain explores gene analysis and point of care testing (POCT). Indeed, SE has encouraged researchers to create a broad range of intellectual capital for the purpose of leading future technologies.
Furthermore, it seems likely that SE seeks Chesbrough’s [ 2 , 38 ] open innovation to improve efficiency and effectiveness of planting innovation. By doing so, the firm can create innovative results with less burden in time and resources. The CEO mentioned that open innovation needs to be encouraged to shorten the technology life cycle and to enable convergence in the electronics industry [ 37 ]. Thus, SE senior managers have aggressively focused on the utilization of external ideas and capabilities [ 39 ].
M&A has been a major instrument to acquire external intellectual capital. SE has acquired several firms, including SanDisk, Amica (a Polish electronics firm) in 2009, and Transchip (a non-memory semiconductor manufacturer in Israel) in 2008 [ 40 ]. SE informed the board of directors of SanDisk about its intention of collaborative innovation orientation and human resource retention in SanDisk [ 41 ]. Such M&A activities have enabled SE to obtain proven and complimentary intellectual capital and dynamic capabilities, including R&D employees.
SE has also managed a broader range of intellectual capital without much investment by sharing their proprietary technologies with partners. For example, SE and IBM, two top US patent firms, established a cross-licensing agreement which allows the participants to utilize each other’s patents for innovation in 2011 [ 42 ]. These firms can share their patents without additional investment, resulting in a more stable basis for innovative activities. This type of contract enables SE to implement planting innovation with finite capabilities. Executives of SE and IBM also announced that the objective of cross-licensing lies in sharing intellectual capital in the expectation of continuous innovative outputs. In sum, SE has implemented planting innovation through SAIT internally and has utilized external capabilities through M&A and licensing for significant financial gains in the long run. SAIT has implemented several major research projects independently as well.
Ambidexterity and co-innovation
Since SE is implementing planting and harvesting innovation simultaneously, one major task is balancing both types of innovative activities. Otherwise, the firm may suffer from lack of financial cash flows or future leadership in the industry. Despite their brand image, major manufacturers of wristwatch had to overcome the loss of sales volume in the 1970s due to the revolutionary quarts movement technology [ 43 ]. Although US electronic giants initiated the transistor technology, Japanese manufacturers like Sony harvested the lion’s share of its benefits with their transistor radios [ 44 ].
The significance of inter-organizational cooperation in attaining competitive advantage cannot be ignored [ 45 ]. Thus, any organization, however large or global it may be, cannot be competitive for long without collaboration with other world-class partners. From this perspective, the success or failure of firms today lies in managing the relationships with other value chain partners and stakeholders [ 4 ].
Beyond the conventional exploration and open innovation focusing on the use of external resources, SE has been searching for the best way to simultaneously implement planting and harvesting innovation through co-innovation with stakeholders [ 1 ] (see Fig. 1 ). The main focus of the VIP Centre has been on how to encourage collaboration among internal departments. Resulting convergence across departments has enabled the firm to recognize the diverse viewpoints other than the opinions of core engineers. The VIP Centre director stated that those firms interested in value innovation need to adopt the cross-functional team (CFC) concept with a separate space to promote inter-departmental collaboration for value innovation [ 34 ]. This process is expected to encourage formal and informal sharing of ideas, opinions, and viewpoints since participants have more opportunities to communicate with many people. For instance, the CFC team consisting of marketers, designers, and engineers developed a new slim style laptop which caught the fancy of Japanese consumers [ 35 ]. Furthermore, the members of the Centre frequently collaborate with external partners [ 35 ].
Co-innovation at Samsung Electronics. Based on the information from SAIT ( www.SAIT.samsung.com ) and Kim’s [ 35 ] study
SAIT has played a significant role in connecting SE with external entities ( http://www.sait.samsung.co.kr ), such as universities, through the Global Research Outreach (GRO) program and other collaborators via the Collaborative Open Research Expert (CORE) program. These efforts have allowed the firm to share the risks inherent in planting innovation. Thus, the firm has been able to reduce the uncertainty involved in innovative practices and maximize its value with finite organizational resources.
Another example of collaboration lies in its value-chain management beyond the use of external capabilities. An association of Samsung’s collaborating vendors, Hyup-Sung-Hoe, has played a key role in co-innovation processes [ 46 ]. SE and collaborating vendors have participated in innovation activities, including sectional committee meetings. It is evident that SE’s innovation activities cover not only its own value chain but also that of its partners. Given the fact that current business activities must include vendors, the improvement of innovation capabilities of the entire value chain is essential for gaining competitive advantage. SE also considers the creation of new ventures with excellent technologies as another outcome of its open innovation strategy [ 47 ]. The firm manages its entire value chain to compete successfully, as opposed to conducting business with partners for short-term monetary rewards. Figure 1 presents SE’s value chain convergence activities.
SE has participated in the various industry-academia collaboration projects. This partnership has enabled SE to interact with partners to utilize their tangible and intangible resources. Particularly, research universities can provide professional human resources, research expertise, and infrastructure. In 2012, SE established the Centre for Intelligent Computing (CIC) with Seoul National University [ 48 ]. While the former supports the facilities and programs, the latter provides research ideas and its faculty resource. Such projects allow SE to benefit from the results of collaborative innovation while sharing the burden of investment. Furthermore, individual participants would likely to share ideas and opinions due to their “relationships” even after the official project is completed, beyond organizational boundaries. SE has also established the Samsung Talent Program (STP) with 14 Korean universities [ 48 ]. This program is intended to nurture and develop R&D employees to fit its needs.
The use of a co-innovation mechanism has played a key role in managing planting and harvesting innovation with limited organizational resources. SE has established networks with the various innovation partners, including diverse internal departments, academia, technicians, customers, and suppliers to collaborate and co-create for shared goals. In addition to external resources, the closely interconnected relationships among participants are expected to nurture collective intelligence. Overall, co-innovation allows SE to manage both types of innovation, harvesting and planting, while coping with its fast expanding global presence.
Firm performance
The innovation investment of Samsung Electronics has shown tremendous financial return as can be seen in Fig. 2 . The financial information from Daum ( www.daum.net ), a major portal site in Korea, exhibits that SE’s sales volume has dramatically increased since the early 2000s. As SE has paid more attention to harvesting innovation, its sales volume surged from 2001 to 2004. This implies that the firm continued its growth by actively pursuing innovative activities which created much financial gain in the short term.
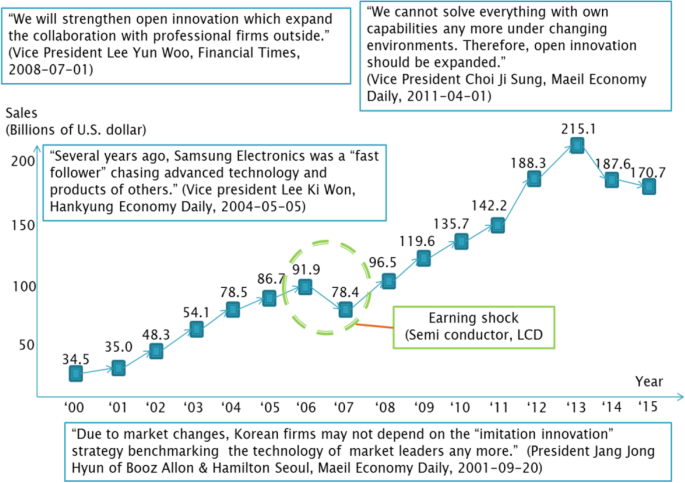
Annual revenue of Samsung Electronics. Based on the financial information from Daum ( www.daum.net ) and Hoovers ( www.hoovers.com ) and news articles from Naver ( www.naver.com )
The revenue of the firm diminished drastically in 2007 with the global financial crisis. This “earning shock” was due to the decrease of demands for LCDs and semiconductors [ 49 ]. The global economy was in recession for several years afterward. For example, in 2012, the Federal Reserve Bank announced that the net asset of median family in the USA decreased by 38.8% from December 2007 to June 2009 [ 50 ]. Given that the consumption of middle-class families in the USA has been the locomotive of global economy for decades, the effect of the macro-economic crisis would be challenging for many global firms.
SE executives began to search solutions for the creation of original technologies, while continuing its innovation harvesting efforts. Despite the global financial crisis, SE has continued its growth [ 50 ]. In 2017, the revenue was approximately $224 billion [ 51 ]. SE has steadily expanded its business after it introduced harvesting and planting innovation despite the hostile macro-economic environment and recent ownership succession.
Discussion and evaluation
This study investigated planting and harvesting innovation to answer the research question, “Which classification of innovation best explains the heterogeneous timing of revenue realization?” While harvesting innovation seeks commercial results in a relatively short term, planting innovation pursues the development of new ideas and technologies for a long term. For instance, a firm with the CDMA wireless technology may not succeed financially without the dispersion of CDMA phones. Given the finite amount of resources, firms need to efficiently balance planting and harvesting innovation. Otherwise, they would fail to develop both new products/services for market launching and original technologies for future market expansion while continuing their business activities.
A case analysis was employed to answer the second research question, “How are planting and harvesting activities of innovation implemented in a successful global business firm?” Samsung Electronics (SE) was chosen as a case study since it has become the largest electronics firm in the world but originated from a former emerging economy, South Korea. Despite its limitations, SE continued to grow by using innovation as a vehicle to move from an outsourcing firm to a global leader in innovation. It is a dramatic success story for a local firm in Korea which began its business in the 1970s. Since SE established innovation as the core of its business activities in its mission statement, it has implemented the dual strategy of planting and harvesting innovation.
SE has participated in various activities to develop innovative new technologies as well as products. The interviews reported were collected from news articles to analyze the stream of innovative activities of SE. Harvesting innovation has led to the initiation of a broad range of new products, allowing the firm to access global customers and also received world-renowned innovation awards. SE has also focused on planting innovation which can result in original technologies. Based on Blue Ocean Strategy, the Value Innovation Program (VIP) Centre has been primarily responsible for developing new products. The Samsung Advanced Institute of Technology (SAIT) pursues original technologies which can continuously support technological leadership in the years to come.
Co-innovation [ 1 ] has enabled SE to focus both planting and harvesting innovation activities with limited resources. External collaborators have contributed to the application of SE’s tacit knowledge for convergence that is difficult to imitate by competitors. The VIP Centre and SAIT have played a critical role in encouraging collaboration among innovation value chain partners, including academic researchers, technicians, vendors, and customers to co-create value. It has enabled the firm to pursue innovative outcomes while managing financial stability. The financial performance of SE exhibits that its innovation activities have resulted in a remarkable success.
Conclusions
The digital age is characterized by the increased complexity and uncertainty of the business environment [ 1 ]. In the environment of increasing velocity of change, business firms must develop dynamic capabilities through innovation to adapt to change with agility, flexibility, and speed [ 4 ]. There have been various innovation approaches in the literature: exploitative vs. explorative [ 7 ], disruptive [ 52 ] vs. non-disruptive [ 53 ], ambidexterity [ 54 ], and convergence innovation [ 55 ]. However, the purpose of innovation remains the same, which is to create new or added value by applying ideas or technologies in a fundamentally different way [ 1 ]. What is not widely known is that innovation is not one integrated process. Instead, there are several steps and cycles in innovation. Planting innovation involves creating new ideas, scientific breakthroughs, or new technologies. Planting seeds does not guarantee a good harvest. Many nurturing steps such as careful planning, risk taking, and entrepreneurship are needed to have a successful harvest. Thus, studying the most spectacular success transformation case of SE through its innovation process provides meaningful theoretical and practical insights and a contribution to the literature of innovation.
This study is not free from limitations. Although SE can be considered as one of global leading innovators originated from Korea, a success story from one of the poorest countries in the world to an advanced economy, the generalizability of the single case study can be limited as Tversky and Kahneman [ 56 ] suggested. Future researchers should conduct relevant studies in various contexts to overcome such limitation. In addition, the qualitative analysis tool of Gibbert et al. [ 57 ] can be used to lessen the concern on generalizability.
There are many factors that have contributed to the success of SE. In this study, we used the revenue as the reference of SE’s efforts of harvesting innovation. There could be many other factors that contributed to the performance of SE. However, we believe these factors all contributed to the combined efforts of SE in harvesting innovation.
In addition, it is also expected that future studies may apply more refined research methods to examine the process and consequences of planting and harvesting innovation. While we believe in the merits of the research method applied in this study, it is also possible that executives might have exaggerated the process and outcomes of their projects. Future researchers are expected to cross-check the results of planting and harvesting innovation by utilizing multiple research methods.
Despite the limitations, this research provides several meaningful implications. It uses a distinction of planting and harvesting innovation [ 8 , 9 ] to examine how a firm grows into a global leader despite its finite managerial and financial resources. While planting innovation aims to implement technological advancement as a potential source of long-term profits, harvesting innovation focuses on the development of new products for market expansion in the short term. The framework of planting and harvesting innovation is expected to provide a tool for managers to distribute limited funds for various types of innovation projects. It shall enable them to clarify whether the current focus of innovation investment lies in launching new innovative products or seeking competitive advantage for future profits. The case of Samsung Electronics exhibited that its innovation has focused on both short-term profits and technological innovation for the future growth momentum. Firms are recommended to follow this notion to compete successfully in high tech industries with limited financial, technological, and managerial competencies.
Collaboration is also required for firms seeking both planting and harvesting innovation. Given their shortage of resources and competencies, firms need to share the risks and the burdens of innovation projects with external partners. Following the case of Samsung, they are expected to cooperate with various entities, including research institutions, suppliers, customers, or new ventures. It enables firms to afford the cost of breakthrough innovation despite their finite resources and experiences. Collaboration helps these firms create innovation results for advanced as well as emerging economies.
This study also provides implications from methodological perspectives (Table 2 ). The use of indirect interviews from news articles allowed us to observe the opinions of SE executives over time. In addition, it can collect the opinions of executives at the time of innovative activities rather than asking current employees’ perceptions about what happened in the past. It provides future researchers with an effective method for exploratory research. The use of this underused but promising methodology can contribute to overcoming the limitations of research in the management field despite its possible limitations.
Practitioners can obtain lessons from the results of this study. They could observe how SE, a former emerging market firm, dispersed investment risks by collaborating with the various stakeholders to implement planting innovation. The convergence of internal and external ideas, from suppliers, academia, other businesses, and customers, is essential for the implementation of both types of innovation with finite resources. Furthermore, they need to nurture innovative capabilities of entire internal and external stakeholders as co-innovators. This shall allow firms to achieve the network effect of innovation.
As suggested by Lee [ 4 ], the main focus of innovation projects has been on how to benefit business activities in new ways. Lee [ 58 ] and Schniederjans and Schniederjans [ 59 ] also examined how practical operational issues like quality practices can be improved by innovation.
Availability of data and materials
The datasets used and/or analyzed during the current study are available from the corresponding author on reasonable request.
Abbreviations
Blue Ocean Strategy
Consumer Electronics Association
Cross-functional team
Centre for Intelligent Computing
Collaborative Open Research Expert
Global Research Outreach
Palo Alto Research Center
Point of care testing
Samsung Advanced Institute of Technology
Code-Division Multiple Access
Samsung Talent Program
Value Innovation Program
Lee SM, Lim SB (2018) Living innovation: from value creation to the greater good. Emerald Publishing, Bingley, U.K
Book Google Scholar
Chesbrough H (2003) Open innovation: the new imperative for creating and profiting from technology. Harvard Business School Publishing, Boston, MA
Google Scholar
Damanpour F, Walker RM, Avellaneda CN (2009) Combinative effects of innovation types and organizational performance: a longitudinal study of service organizations. J Manage Stud 46(4):650–675
Article Google Scholar
Lee SM (2018) Innovation: from small “i” to large “I”. Int J Quality Inno. 4(1). https://doi.org/10.1186/s40887-018-0022-4
Lawson B, Samson D (2001) Developing innovation capability in organizations: a dynamic capabilities approach. Int J Innov Manage 5(3):377–400
He Z-L, Wong P-K (2004) Exploration vs. exploitation: an empirical test of the ambidexterity hypothesis. Organ Sci 15(4):481–494
March J (1991) Exploration and exploitation in organizational learning. Organ Sci 2(1):71–87
Jang S H (2012) Ownership structure, absorptive capacity, and innovation: planting vs harvesting innovation (doctoral dissertation). Retrieved from http://digitalcommons.unl.edu/businessdiss/29/
Jang SH, Grandzol C (2014) Value co-creation in emerging economies: planting and harvesting innovation perspectives. Int J Serv Sci 5(3/4):171–181
Teece DJ (2014) The foundation of enterprise performance: dynamic and ordinary capabilities in an (economic) theory of firms. Acad Manage Perspect 28(4):324–338
Gopalakrishnan S, Damanpour F (1997) A review of innovation research in economics, sociology, and technology management. Omega 25(1):15–28
Nohria N, Gulati R (1996) Is slack good or bad for innovation? Acad Manage J 39(5):1245–1264
Johannessen JA, Olsen B, Lumpkin GT (2001) Innovation as newness: what is new, how new, and new to whom? Eur J Innov Manage 4(1):20–31
Damanpour F, Szabat KA, Evan WM (1989) The relationship between types of innovation and organizational performance. J Manage Stud 26(6):587–602
Van de Ven AH (1986) Central problems in the management of innovation. Manage Sci 32(5):590–607
Rogers M (1998) The definition and measurement of innovation. Working Paper. Melbourne Institute of Applied Economic and Social Research, Melbourne, Australia
Rosenbusch N, Brinckmann J, Bausch A (2011) Is innovation always beneficial? A meta-analysis of the relationship between innovation and performance in SMEs. J Bus Venturing 26(4):441–457
Stieglitz N, Heine K (2007) Innovations and the role of complementarities in a strategic theory of the firm. Strateg Manage J 28(1):1–15
Teece D (1986) Profiting from technological innovation: implications for integration, collaboration, licensing and public policy. Res Policy 15(6):285–305
Dewar R, Dutton J (1986) The adoption of radical and incremental innovations: an empirical analysis. Manage Sci 32(11):1422–1433
Gumusluoglu L, Ilsev A (2009) Transformational leadership, creativity, and organizational innovation. J Bus Res 62(4):461–473
Halme DG, Kessler DA (2006) FDA regulation of stem-cell based therapies. New Engl J Med 355(16):1730–1735
Schmookler J (1966) Invention and economic growth. Harvard Business School Press, Cambridge, MA
Chesbrough H, Rosenbloom RS (2002) The role of business model in capturing value from innovation: wvidence from Xerox Corporation’s technology spin-off companies. Ind Corp Change 11(3):529–555
Simsek Z (2009) Organizational ambidexterity: towards a multilevel understanding. J Manage Stud 46(4):597–624
Lee SM, Olson DL, Trimi S (2010) The impact of convergence on organizational innovation. Organ Dyn 39(3):218–225
Park Y, Lee JY, Hong S (2011) Effects of international entry-order strategies on foreign subsidiary exit. Manage Decis 49(9):1471–1488
Song D (2004a) Open the era of value innovation: (3) the case of Samsung Electronics. Hankyung Business Daily (April 19) Retrieved from http://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=101&oid=015&aid=0000701971
Hwang I (2001) No future for Korean firms: (1) technology imitation. Maeil Business Newspaper, September, 20 Retrieved from http://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=101&oid=009&aid=0000151003
Lee T (2005) [Searching blue ocean] Large firms: Samsung Electronics, be a consumer. Hankyung Business Daily, October 10 Retrieved from http://www.hankyung.com/news/app/newsview.php?aid=2005100701291
Lee T (2006) Korea innovation forum 2006: Samsung electronics VIP centre. Hankyung Business Daily, February 14 Retrieved from http://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=101&oid=015&aid=0000872791
Kim W, Maugborne W (2005) Blue ocean strategy: how to create uncontested market space and make the competition irrelevant. Harvard Business School Press, Boston, MA
Song D (2004b) Open the era of value innovation: (5) VI from executives. Hankyung Business Daily, May 5 Retrieved from http://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=101&oid=015&aid=0000706660
Song D (2005) Toward the blue ocean: an interview with Lee Dong Jin, a VIP centre Vice President at Samsung Electronics. Hankyung Business Daily, November 8 Retrieved from http://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=101&oid=015&aid=0000848475
Kim M (2004) The era of value innovation: (4) VI embedded in Samsung. Hankyung Business Daily, May 4 Retrieved from http://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=101&oid=015&aid=0000706224
Kim Y (2007) Samsung value innovation program (VIP) centre. Financial News, November 4 Retrieved from http://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=101&oid=014&aid=0000355858
Yang H (2008) Samsung Electronics Vice President Lee Yun Woo: initiate future core technologies. Financial News, July 1 Retrieved from http://www.fnnews.com/news/200807011810110422?t=y
Chesbrough H (2012) Open innovation: where we’ve been and where we’re going. Res Techno Manage 55(4):20–27
Lee D (2011) Samsung Electronics Vice President Choi Jisung: respond early to even natural disasters. Daily Maekyung, April 1 Retrieved from http://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=101&oid=009&aid=0002439029
Jin S (2009) Samsung takes over Polish Amica. Moneytoday December 22 Retrieved from http://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=101&oid=008&aid=0002254573
Kim B (2008) Samsung Electronics announces proposal for combination with SanDisk in letter to board of directors. Moneytoday, September 17 Retrieved from https://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=101&oid=008&aid=0002034388
Yonhap (2011) AsiaNet: Samsung Electronics and IBM announce patent cross-license agreement. February 9 Retrieved from https://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=104&oid=001&aid=0004904103
Barrett ME (2000) Time marches on: the worldwide watch industry. Thunderbird Int Bus Rev 42(3):349–372
Lynn LH (1998) The commercialization of the transistor radio in Japan: the functioning of an innovation community. IEEE T Eng Manage 45(3):220–229
Dyer JH, Singh H (1998) Relational view: cooperative strategy and sources of interorganizational competitive advantage. Acad Manage Rev 23(4):660–679
Kim C (2009a) Collaborating vendors benefit from Samsung Electronics. Maekyung Economy, August 23 Retrieved from http://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=101&oid=024&aid=0000026894
Kim M (2009b) Samsung embraces ventures. Munhwailbo, November 4 Retrieved from https://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=101&oid=021&aid=0002013900
Park Y (2012) Industry-academia collaboration, ‘upgrade.’ Economic Review. In: March 9 Retrieved from http://www.econovill.com/archives/39043
Park S (2007) The bad performance of Samsung Electronics in the first quarter, Why? Sekyeilbo, April 14 Retrieved from http://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=101&oid=022&aid=0000220925
Bae B, Go S (2012) The middle class in Korea and U.S. was demolished as the result of the global financial crisis in 2008. Kukminilbo, June 12 Retrieved from https://news.naver.com/main/read.nhn?mode=LSD&mid=sec&sid1=101&oid=005&aid=0000514948
Hoover’s Company Records (2019) Samsung Electronics Co., Ltd. In-depth Records, January 23 Retrieved from https://advance-lexis-com.proxy-bloomu.klnpa.org/api/document?collection=company-financial&id=urn:contentItem:5H1P-0GF1-JBPR-X276-00000-00&context=1516831
Christensen CM, Rayner M, McDonals R (2015) What is disruptive innovation? Harvard Bus Rev 93(12):44–53
Kim WC, Maubourgne R (2019) Nondisruptive creation: rethinking innovation and growth. MIT Sloan Manage Rev Spring:46–56
O’Reilly CA, Tushman ML (2013) Organizational ambidexterity: the past, present, and future. Acad Manage Perspect 27(4):324–338
Lee SM, Olson D (2010) Convergenomics: strategic innovation in the convergence era. Gower, Surrey, UK
Tversky A, Kahneman D (1986) Rational choice and the framing of decisions. J Bus 59(4):251–278
Gibbert M, Ruigrok W, Wicki B (2008) What passes as a rigorous case study? Strategic Manage J 29(13):1465–1474
Lee D (2015) The effect of operational innovation and QM practices on organizational performance in the healthcare sector. Int J Quality Inno 1(1). https://doi.org/10.1186/s40887-015-0008-4
Schniederjans D, Schniederjans M (2015) Quality management and innovation: new insights on a structural contingency framework. Int J Quality Inno 1(1). https://doi.org/10.1186/s40887-015-0004-8
Download references
There was no funding support for this study.
Author information
Authors and affiliations.
Zeigler College of Business, Bloomsburg University of Pennsylvania, Bloomsburg, USA
Seung Hoon Jang
Department of Management, University of Nebraska-Lincoln, Lincoln, USA
Sang M. Lee
Kania School of Management, University of Scranton, Scranton, USA
School of Air Transport and Logistics, Korea Aerospace University, Goyang, South Korea
Donghyun Choi
You can also search for this author in PubMed Google Scholar
Contributions
All authors contributed to the developing of the manuscript. All authors read and approved the final manuscript.
Corresponding author
Correspondence to Seung Hoon Jang .
Ethics declarations
Competing interests.
The authors declare that they have no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License ( http://creativecommons.org/licenses/by/4.0/ ), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
Reprints and permissions
About this article
Cite this article.
Jang, S.H., Lee, S.M., Kim, T. et al. Planting and harvesting innovation - an analysis of Samsung Electronics. Int J Qual Innov 5 , 7 (2019). https://doi.org/10.1186/s40887-019-0032-x
Download citation
Received : 25 April 2019
Accepted : 11 September 2019
Published : 21 October 2019
DOI : https://doi.org/10.1186/s40887-019-0032-x
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Planting innovation
- Harvesting innovation
- Co-innovation
- Multinationals

- About / Contact
- Privacy Policy
- Alphabetical List of Companies
- Business Analysis Topics
Samsung’s Generic Competitive Strategy & Growth Strategies

Samsung’s generic competitive strategy and intensive growth strategies set business goals for technological innovation as a critical factor in developing competitive advantages. Headquartered in Korea, the conglomerate competes with technology-intensive firms, such as Apple , Google (Alphabet) , Microsoft , Sony , and Intel , which create strong competitive forces, as determined through a Five Forces analysis of Samsung. The industry environment imposes aggressive competitive behavior that typically involves rapid technological innovation for product differentiation, as seen in the evolution of smartphones available in the global market. To effectively compete, Samsung’s generic competitive strategy and growth strategies must involve investment in technological innovation. The resulting competitive advantages enable the company to keep its competitive position as one of the best performers in the semiconductors, consumer electronics, and home appliances industries. Samsung’s generic competitive strategy and intensive strategies for growth are suited to the current business environment and the strategic positioning of the multinational organization’s operations.
The generic competitive strategy and intensive growth strategies of Samsung Group permeate its entire organization, influencing the strategic choices and implementations of its divisions and subsidiaries. The Group’s unitary leadership is responsible for the corporate strategic direction and competitive advantages of the conglomerate and its technology-focused subsidiaries. Samsung’s generic competitive strategy and intensive growth strategies are observable in product design, marketing strategies, and the business organizational development direction of subsidiaries.
Samsung’s Generic Competitive Strategy (Porter Model)
Samsung applies broad differentiation as its generic competitive strategy. Based on Michael E. Porter’s competitive strategy model, the strategic objective of broad differentiation is to maintain competitive advantage by providing unique (or differentiated) products targeting a wide market, which in this case is industry-wide, involving practically every person or group that buys smartphones, laptops, and other equipment. To achieve Samsung’s strategic plans for growth and expansion in the global market, this generic competitive strategy requires the application of product development as a main intensive growth strategy to compete with other technology firms.
Samsung’s investments in product development are a strategic implication of differentiation as its generic competitive strategy. For example, the company invests in technological innovation to support the competitive advantage of its products in the consumer electronics market. Another implication of this generic competitive strategy is Samsung’s marketing mix (4Ps) and related strategies that promote products as unique or different alternatives to the majority of competitors. This marketing approach and technological innovation sustain the corporation’s competitive advantages and value chain effectiveness in satisfying customers’ needs in consumer electronics, computing technology, and home appliances.
Other generic competitive strategies, such as cost leadership, differentiation focus, and cost focus, are also applied in Samsung’s operations, but to a limited extent. Cost focus leads to the company’s being the best-cost provider in some segments of the semiconductor and electronic components markets. The limited application of cost focus still comes with innovation standards that reflect Samsung’s main generic competitive strategy of broad differentiation. These generic strategies align with the company’s intensive growth strategies to succeed in sustaining the technology firm’s competitive advantages.
Samsung’s Intensive Growth Strategies (Ansoff Matrix)
Market Penetration (Primary) . Samsung’s revenue growth depends on market penetration as the primary intensive strategy. In Igor Ansoff’s matrix, the strategic objective of market penetration is to grow the technology business by increasing its revenues from the sale of current products in current markets, such as the European Union’s consumer electronics market, where the corporation already has operations. Competitive advantages and business strengths identified in the SWOT analysis of Samsung combat negative forces from competition in these markets. As an intensive growth strategy, market penetration depends on the effectiveness of the generic competitive strategy of broad differentiation, in terms of how the company creates technologically innovative products that are differentiated enough to attract target customers in current or existing markets.
Product Development (Secondary) . Considering the emphasis of product superiority in Samsung’s corporate mission and vision statements , product development is a major intensive growth strategy of the enterprise. A strategic objective of product development in this case is to grow the business through new products, such as new electronic gadgets. Also, this intensive strategy grows Samsung’s operations through iterative innovation, which leads to improved versions or variants of existing products. For example, the company regularly rolls out new smartphone models, similar to what competitors are doing in their product development strategy. The implementation of product development as an intensive growth strategy is based on Samsung’s generic competitive strategy of differentiation, which requires product development for uniqueness that differentiates the business from the competition. Economies of scope based on the conglomerate’s various subsidiaries support product development and competitive advantage by providing technological expertise and material inputs from the subsidiaries. Samsung’s organizational culture (work culture) affects human-resource support for operational effectiveness, value chain efficiencies, supply chain management, and other business activities that fulfill the strategic objectives of product development.
Market Development . The global scale of Samsung’s operations makes market development a minor intensive strategy for business growth. Market development’s strategic objective is to enter new markets using the company’s existing products, such as introducing new Galaxy tablets in Latin American markets after these products’ introduction in the United States. As an intensive growth strategy, market development’s success depends on product value and competitive advantage, which in this case comes with Samsung’s generic strategy of differentiation via technological innovation. For example, effective innovation for cutting-edge technological design makes the corporation’s products more competitive when rolled out in target markets. With this intensive growth strategy, introducing products to new markets may come with changes in the geographical units of Samsung’s organizational structure (company structure) .
Diversification . Samsung’s diversified business operations maintain multiple revenue channels and spread risk across industries and markets. This intensive growth strategy’s implementation is infrequent in the technology conglomerate, considering regulatory hurdles and other barriers. With the strategic objective of establishing new profitable businesses, the diversification strategy grows Samsung typically through acquisitions of smaller firms, such as Harman International Industries. The minor role designation of this intensive growth strategy limits the risks of establishing new business operations. In implementing diversification, the generic competitive strategy of differentiation is also applied for competitiveness and strategic alignment among Samsung subsidiaries’ business operations.
Some Considerations – Samsung’s Generic Competitive Strategy & Intensive Growth Strategies
Samsung’s generic competitive strategy and intensive growth strategies direct the organization’s growth and development. Differentiation plays a major role in building the company’s competitive advantage, although other generic competitive strategies, such as cost leadership and focus strategies, also support the technology enterprise and its competitiveness. Samsung’s operations management strategies and administration must align with the differentiation generic competitive strategy and the intensive growth strategies to support business growth while competing with aggressive multinational companies.
- López, D., & Oliver, M. (2023). Integrating innovation into business strategy: Perspectives from innovation managers. Sustainability, 15 (8), 6503.
- Samsung – Brand Identity .
- Samsung R&D Center .
- Samsung Catalyst Fund .
- Taherdoost, H. (2023). An overview of trends in information systems: Emerging technologies that transform the information technology industry. Cloud Computing and Data Science , 1-16.
- U.S. Department of Commerce – International Trade Administration – Software and Information Technology Industry .
- Copyright by Panmore Institute - All rights reserved.
- This article may not be reproduced, distributed, or mirrored without written permission from Panmore Institute and its author/s.
- Educators, Researchers, and Students: You are permitted to quote or paraphrase parts of this article (not the entire article) for educational or research purposes, as long as the article is properly cited and referenced together with its URL/link.
- Harvard Business School →
- Faculty & Research →
- June 2005 (Revised February 2009)
- HBS Case Collection
Samsung Electronics
- Format: Print
- | Pages: 26
More from the Authors
- Faculty Research
Global Strategic Management
- April 2013 (Revised November 2013)
Microsoft in Korea
The unfairness trap: a key missing factor in the economic theory of discrimination.
- Global Strategic Management By: Jordan I. Siegel
- Microsoft in Korea By: Jordan I. Siegel and Lynn Pyun
- The Unfairness Trap: A Key Missing Factor in the Economic Theory of Discrimination By: Jordan I. Siegel, Naomi Kodama and Hanna Halaburda
Table of Contents
Digital presence of samsung, digital marketing campaigns of samsung , marketing mix of samsung, swot analysis, results of samsung marketing strategy, conclusion , how samsung marketing strategy solidifies its brand value.

The global electronics powerhouse– Samsung began its journey as a low-tier manufacturing brand. A strong Samsung marketing strategy revolutionized its stance in the market, making it the No.1 smartphone producer worldwide. The tech giant ranks 4th in Forbes' list of the World's Largest Tech Companies. A perfect blend of digital marketing and innovation has established Samsung as a unique, high-quality brand worthy of customer loyalty.
Become a Certified Marketing Expert in 8 Months
Samsung's adept use of social currency has contributed to its success in digital marketing. Expanding its social media presence, Samsung provides customers and brand loyalists several chances to share their experiences with those in their circle.

Samsung YouTube Channel
To connect with the various segments of the population their products target, Samsung has social profiles on all of the major social networks, including
- Facebook: 162M
- Twitter: 12.5M
- YouTube: 6.24M
- Instagram: 4.5M
Samsung Facebook Page with 162 Million Likes
Moreover, Samsung has several profiles on each platform. For instance, Instagram has Samsung, Samsung India, Samsung UK, Samsung UA, Samsung Mobile and more.
The company adheres to the best digital marketing practices like SEO and quality content creation that solves customer problems.
Being a community-oriented brand that impacts audiences worldwide, Samsung introduces various marketing campaigns. The promising Samsung marketing strategy focuses on leveraging the power of exceptional marketing campaigns to promote its products and appeal to the audience.
Social media ads, sponsorships, and online advertising strengthened the brand. Some exceptional Samsung marketing campaigns are as follows:
- #YouMake Campaigns: It brings up a global marketing platform for consumers to take the lead with device customization. It brings a better way of personalization via customized control enabled by SmartThings IoT solutions. The #YouMake campaign offers continuous services and virtual benefits, encouraging customer participation by utilizing the best metaverse platforms.
- Growing Up: Another commercial on YouTube that made people reconsider their options. The company directly targeted its main competitor–Apple, and the video took the internet by storm.
Product, Price, Place, and Promotion–the 4Ps of the marketing mix constitute an integrated marketing model. Samsung’s marketing mix plan gives insights into the company’s success secret.
1. Product Mix
Delivering excellent results in recent years, Samsung products are well-known for their services and quick support. Samsung’s marketing mix in its product line is one of its major strong points. The products fall into the following categories:
- Mobile phones
- Televisions – LEDs, Plasma TV, LCDs, SMART TV, HDTV
- Refrigerators
- Air Conditioners
- Washing Machine
- IT – Printers, laptops, and accessories
2. Price Mix
Price mix is one of the strongest points in the Samsung marketing strategy. It offers two pricing schemes to satisfy its clients. The corporation adopts a price skimming tactic whenever it releases a new smartphone with the latest technology. Moreover, it reduces the price of that product when the competitors launch identical products.
3. Promotion Mix
Samsung attracts customers via advertising while employing the best tactics to push products through sales promotions.
The company employs several marketing vehicles both during the festive season and outside of it. It grants numerous discounts and incentives to business partners, encouraging them to sell Samsung products above the competition.
4. Place Mix
Samsung service dealers are responsible for corporate sales. Its selling point is its distribution. They distribute their goods via a single distribution business. They then distribute them to other locations.
SWOT analysis is one of the best ways to dive deeper into the Samsung marketing technique. It provides insights into Samsung’s strengths, weaknesses, opportunities, and threats concerning its marketing competitiveness.
Samsung’s Strengths
- It has held a strong position in the smartphone manufacturing industry for years. Climbing the ladder, Samsung ranks first on the world’s best smartphone manufacturers list.
- Significant investments in the innovative research and development sector have helped Samsung generate a diverse product offering compared to its competitors.
- Its transition to a customer-centric management system has brought about revolutionary changes.
- Its consistent efforts for sustainable development, such as the adoption of eco-packaging for TVs, give it the upper hand.
- Samsung leads the development of advanced technologies like AI, 5G, automotive and robotics.
- Lastly, it is rapidly expanding commercial marketing in India and China.
Samsung’s Weakness
- Despite expanding its operations in Asia, the company relies heavily on American markets.
- Samsung’s defective items, such as the Samsung Galaxy A20e and a malfunctioning foldable phone.
Samsung’s Opportunities
- Samsung can achieve tremendous development in the smartphone industry by setting the standard with innovative goods like foldable phones.
- As the world adopts 5G, Samsung has the know-how to capitalize on the opportunity.
- The company can hire exceptionally skilled professionals using its brand image.
Samsung’s Threats
- Samsung’s entanglement in controversies can jeopardize its business, such as the lawsuit filed by Apple for patent infringement.
- Xiaomi, Apple, and Huawei stand as major threats and technological competitors who can outsmart Samsung.
Samsung’s revamped marketing programs and competitive strategy implementation have significantly contributed to its huge success over the years.
Performing continuous market research, adding new features, serving customer pain points and employing special efforts to reduce costs, Samsung has paved the way for its success from the very beginning.
Its global value increased by more than 200% in a short span ranging from 2003 to 2008.
Samsung took over Sony–one of the most valuable consumer-electronics brands worldwide. Consequently, Samsung’s sales reached $119 billion by 2009. When the company introduced Samsung Galaxy and leveraged the power of digital platforms for promotions and marketing, its revenue grew to $218 billion in 2018.
Today, Samsung stands 5th on Interbrand’s list of Best Global Brands with a brand value of USD 74.6 billion. It has witnessed a 20% increase in comparison to the last year.
Sparking creativity worldwide, Samsung is the most profitable tech company. The robust Samsung marketing strategy has made it one of the most valuable brands today. Its smart digital marketing tactics set an excellent example of how to revamp your online business as a digital marketer.
Want to know more about Digital Marketing? Enroll on Simplilearn’s Digital Marketing Specialist Program and upskill yourself digitally.
Our Digital Marketing Courses Duration And Fees
Digital Marketing Courses typically range from a few weeks to several months, with fees varying based on program and institution.
Recommended Reads
Digital Marketing Career Guide: A Playbook to Becoming a Digital Marketing Specialist
A Case Study on Netflix Marketing Strategy
12 Powerful Instagram Marketing Strategies To Follow in 2021
Introductory Digital Marketing Guide
A Case Study on Apple Marketing Strategy
What is Digital Marketing and How Does It Work?
Get Affiliated Certifications with Live Class programs
Post graduate program in digital marketing.
- Joint Purdue-Simplilearn Digital Marketer Certificate
- Become eligible to be part of the Purdue University Alumni Association
- PMP, PMI, PMBOK, CAPM, PgMP, PfMP, ACP, PBA, RMP, SP, and OPM3 are registered marks of the Project Management Institute, Inc.
- SMB Technology
- Mobile Productivity
- Mobile Security
- Computing & Monitors
- Memory & Storage
- Digital Signage
- Trending Tech
- Hospitality
- Manufacturing
- Transportation
- Food & Beverage
- Live Events & Sports
- Spectaculars & DOOH
- Gaming & Esports
- White Papers
- Infographics
- Assessments & Calculators
- Case Studies
- About Samsung Insights
- Our Experts
Subscribe to Insights
Get the latest insights from Samsung delivered right to your inbox.
See our Privacy Policy
Samsung Business Insights
Mobile Case Studies
All mobile case studies.

Medtronic’s smartphone-based programmer enhances patient experience for incontinence treatment
Through collaboration with Samsung, Medtronic developed a new smart programmer using a Galaxy smartphone that puts incontinence therapy into patients hands.

Medtronic and Samsung Put DBS Therapy for Parkinson’s Disease in Patients’ Hands
To help clinicians and patients better optimize therapy, Medtronic needed user-friendly mobile devices to adjust the programming of Deep Brain Stimulation implants.

ATAK improves situational awareness for California fire department
The Corona Fire Department uses ATAK on Samsung smartphones and tablets to improve situational awareness and keep firefighters safe.

Savage Launches Digital Transformation With In-Cab Technology
Savage Services adopted Samsung rugged devices and mobile ELD apps to improve logistics performance, driver engagement and truck maintenance.

Tamarack’s Business Productivity Flies Higher with a Mobile Cloud-Based Solution
Aerospace innovators Tamarack gained a productivity boost through a mobile cloud-based solution partnership with Samsung and RedNight Consulting.

Samsung Galaxy S Smartphones and Librestream Onsight App Enhance Field Service Efficiency
Diebold, a financial self-service and security corporation, is improving field service by providing remote video collaboration for its field technicians.

Coldwell Banker: VR Brings an Immersive Look at Real Estate
Coldwell Banker decided that virtual reality (VR) would be incredibly useful to real estate agents. As part of a technology bundle, agents can use 3D imaging cameras, Samsung Galaxy smartphones and Gear VR headsets to provide an immersive experience.

Bethany Life Sees Reportable Events Drop with Behavior Management Long-Term Care Technology
Thanks to VisibleHand’s platform, Bethany Life is now able to take a more proactive approach to resident care and shift to a more prevention-based perspective.

Virtual Reality in Healthcare: How Inova Mount Vernon Hospital Puts Emergency Room Patients at Ease
Inova Mount Vernon Hospital now uses AppliedVR kits in two emergency departments, which are locked down using the Samsung Knox Custom Configurator so they only run the AppliedVR solution.

Thomson Reuters Boosts Eikon Application Security for Enterprise Financial Services Clients
Thomson Reuters needed a security solution that would strengthen the Eikon Mobile application without constricting the fluidity of performance, which could damage end-user experience.

- Predictive Analytics Workshops
- Corporate Strategy Workshops
- Advanced Excel for MBA
- Powerpoint Workshops
- Digital Transformation
- Competing on Business Analytics
- Aligning Analytics with Strategy
- Building & Sustaining Competitive Advantages
- Corporate Strategy
- Aligning Strategy & Sales
- Digital Marketing
- Hypothesis Testing
- Time Series Analysis
- Regression Analysis
- Machine Learning
- Marketing Strategy
- Branding & Advertising
- Risk Management
- Hedging Strategies
- Network Plotting
- Bar Charts & Time Series
- Technical Analysis of Stocks MACD
- NPV Worksheet
- ABC Analysis Worksheet
- WACC Worksheet
- Porter 5 Forces
- Porter Value Chain
- Amazing Charts
- Garnett Chart
- HBR Case Solution
- 4P Analysis
- 5C Analysis
- NPV Analysis
- SWOT Analysis
- PESTEL Analysis
- Cost Optimization
Samsung Electronics
- Strategy & Execution / MBA EMBA Resources
Next Case Study Solutions
- Intel Corp.--1968-2003 Case Study Solution
- Social Strategy at Cisco Systems Case Study Solution
- $19B 4 txt app WhatsApp...omg! Case Study Solution
- E Ink in 2005 Case Study Solution
- LinkedIn Corp., 2008 Case Study Solution
Previous Case Solutions
- Mobileye: The Future of Driverless Cars Case Study Solution
- Head Ski Co., Inc. Case Study Solution
- Undermining Staying Power: The Role of Unhelpful Management Theories Case Study Solution
- DreamCycles: Sustaining Growth Case Study Solution
- THEOTIS WILEY - Confidential Instructions for Erive's Vice-President of Business Development Case Study Solution

Predictive Analytics
May 2, 2024

Popular Tags
Case study solutions.

Case Study Solution | Assignment Help | Case Help
Samsung electronics description.
To maximize their effectiveness, color cases should be printed in color.When is it possible to create a dual advantage of being both low cost and differentiated? In this case, students assess whether Samsung Electronics has been able to achieve such a dual advantage, and if so, how this was possible. Moreover, Samsung Electronics' long-held competitive advantage is under renewed attack. Students also can assess how Samsung should respond to large-scale Chinese entry into its industry.

Case Description Samsung Electronics
Strategic managment tools used in case study analysis of samsung electronics, step 1. problem identification in samsung electronics case study, step 2. external environment analysis - pestel / pest / step analysis of samsung electronics case study, step 3. industry specific / porter five forces analysis of samsung electronics case study, step 4. evaluating alternatives / swot analysis of samsung electronics case study, step 5. porter value chain analysis / vrio / vrin analysis samsung electronics case study, step 6. recommendations samsung electronics case study, step 7. basis of recommendations for samsung electronics case study, quality & on time delivery.
100% money back guarantee if the quality doesn't match the promise
100% Plagiarism Free
If the work we produce contain plagiarism then we payback 1000 USD
Paypal Secure
All your payments are secure with Paypal security.
300 Words per Page
We provide 300 words per page unlike competitors' 250 or 275
Free Title Page, Citation Page, References, Exhibits, Revision, Charts
Case study solutions are career defining. Order your custom solution now.
Case Analysis of Samsung Electronics
Samsung Electronics is a Harvard Business (HBR) Case Study on Strategy & Execution , Texas Business School provides HBR case study assignment help for just $9. Texas Business School(TBS) case study solution is based on HBR Case Study Method framework, TBS expertise & global insights. Samsung Electronics is designed and drafted in a manner to allow the HBR case study reader to analyze a real-world problem by putting reader into the position of the decision maker. Samsung Electronics case study will help professionals, MBA, EMBA, and leaders to develop a broad and clear understanding of casecategory challenges. Samsung Electronics will also provide insight into areas such as – wordlist , strategy, leadership, sales and marketing, and negotiations.
Case Study Solutions Background Work
Samsung Electronics case study solution is focused on solving the strategic and operational challenges the protagonist of the case is facing. The challenges involve – evaluation of strategic options, key role of Strategy & Execution, leadership qualities of the protagonist, and dynamics of the external environment. The challenge in front of the protagonist, of Samsung Electronics, is to not only build a competitive position of the organization but also to sustain it over a period of time.
Strategic Management Tools Used in Case Study Solution
The Samsung Electronics case study solution requires the MBA, EMBA, executive, professional to have a deep understanding of various strategic management tools such as SWOT Analysis, PESTEL Analysis / PEST Analysis / STEP Analysis, Porter Five Forces Analysis, Go To Market Strategy, BCG Matrix Analysis, Porter Value Chain Analysis, Ansoff Matrix Analysis, VRIO / VRIN and Marketing Mix Analysis.
Texas Business School Approach to Strategy & Execution Solutions
In the Texas Business School, Samsung Electronics case study solution – following strategic tools are used - SWOT Analysis, PESTEL Analysis / PEST Analysis / STEP Analysis, Porter Five Forces Analysis, Go To Market Strategy, BCG Matrix Analysis, Porter Value Chain Analysis, Ansoff Matrix Analysis, VRIO / VRIN and Marketing Mix Analysis. We have additionally used the concept of supply chain management and leadership framework to build a comprehensive case study solution for the case – Samsung Electronics
Step 1 – Problem Identification of Samsung Electronics - Harvard Business School Case Study
The first step to solve HBR Samsung Electronics case study solution is to identify the problem present in the case. The problem statement of the case is provided in the beginning of the case where the protagonist is contemplating various options in the face of numerous challenges that Samsung Electronics is facing right now. Even though the problem statement is essentially – “Strategy & Execution” challenge but it has impacted by others factors such as communication in the organization, uncertainty in the external environment, leadership in Samsung Electronics, style of leadership and organization structure, marketing and sales, organizational behavior, strategy, internal politics, stakeholders priorities and more.
Step 2 – External Environment Analysis
Texas Business School approach of case study analysis – Conclusion, Reasons, Evidences - provides a framework to analyze every HBR case study. It requires conducting robust external environmental analysis to decipher evidences for the reasons presented in the Samsung Electronics. The external environment analysis of Samsung Electronics will ensure that we are keeping a tab on the macro-environment factors that are directly and indirectly impacting the business of the firm.
What is PESTEL Analysis? Briefly Explained
PESTEL stands for political, economic, social, technological, environmental and legal factors that impact the external environment of firm in Samsung Electronics case study. PESTEL analysis of " Samsung Electronics" can help us understand why the organization is performing badly, what are the factors in the external environment that are impacting the performance of the organization, and how the organization can either manage or mitigate the impact of these external factors.
How to do PESTEL / PEST / STEP Analysis? What are the components of PESTEL Analysis?
As mentioned above PESTEL Analysis has six elements – political, economic, social, technological, environmental, and legal. All the six elements are explained in context with Samsung Electronics macro-environment and how it impacts the businesses of the firm.
How to do PESTEL Analysis for Samsung Electronics
To do comprehensive PESTEL analysis of case study – Samsung Electronics , we have researched numerous components under the six factors of PESTEL analysis.
Political Factors that Impact Samsung Electronics
Political factors impact seven key decision making areas – economic environment, socio-cultural environment, rate of innovation & investment in research & development, environmental laws, legal requirements, and acceptance of new technologies.
Government policies have significant impact on the business environment of any country. The firm in “ Samsung Electronics ” needs to navigate these policy decisions to create either an edge for itself or reduce the negative impact of the policy as far as possible.
Data safety laws – The countries in which Samsung Electronics is operating, firms are required to store customer data within the premises of the country. Samsung Electronics needs to restructure its IT policies to accommodate these changes. In the EU countries, firms are required to make special provision for privacy issues and other laws.
Competition Regulations – Numerous countries have strong competition laws both regarding the monopoly conditions and day to day fair business practices. Samsung Electronics has numerous instances where the competition regulations aspects can be scrutinized.
Import restrictions on products – Before entering the new market, Samsung Electronics in case study Samsung Electronics" should look into the import restrictions that may be present in the prospective market.
Export restrictions on products – Apart from direct product export restrictions in field of technology and agriculture, a number of countries also have capital controls. Samsung Electronics in case study “ Samsung Electronics ” should look into these export restrictions policies.
Foreign Direct Investment Policies – Government policies favors local companies over international policies, Samsung Electronics in case study “ Samsung Electronics ” should understand in minute details regarding the Foreign Direct Investment policies of the prospective market.
Corporate Taxes – The rate of taxes is often used by governments to lure foreign direct investments or increase domestic investment in a certain sector. Corporate taxation can be divided into two categories – taxes on profits and taxes on operations. Taxes on profits number is important for companies that already have a sustainable business model, while taxes on operations is far more significant for companies that are looking to set up new plants or operations.
Tariffs – Chekout how much tariffs the firm needs to pay in the “ Samsung Electronics ” case study. The level of tariffs will determine the viability of the business model that the firm is contemplating. If the tariffs are high then it will be extremely difficult to compete with the local competitors. But if the tariffs are between 5-10% then Samsung Electronics can compete against other competitors.
Research and Development Subsidies and Policies – Governments often provide tax breaks and other incentives for companies to innovate in various sectors of priority. Managers at Samsung Electronics case study have to assess whether their business can benefit from such government assistance and subsidies.
Consumer protection – Different countries have different consumer protection laws. Managers need to clarify not only the consumer protection laws in advance but also legal implications if the firm fails to meet any of them.
Political System and Its Implications – Different political systems have different approach to free market and entrepreneurship. Managers need to assess these factors even before entering the market.
Freedom of Press is critical for fair trade and transparency. Countries where freedom of press is not prevalent there are high chances of both political and commercial corruption.
Corruption level – Samsung Electronics needs to assess the level of corruptions both at the official level and at the market level, even before entering a new market. To tackle the menace of corruption – a firm should have a clear SOP that provides managers at each level what to do when they encounter instances of either systematic corruption or bureaucrats looking to take bribes from the firm.
Independence of judiciary – It is critical for fair business practices. If a country doesn’t have independent judiciary then there is no point entry into such a country for business.
Government attitude towards trade unions – Different political systems and government have different attitude towards trade unions and collective bargaining. The firm needs to assess – its comfort dealing with the unions and regulations regarding unions in a given market or industry. If both are on the same page then it makes sense to enter, otherwise it doesn’t.
Economic Factors that Impact Samsung Electronics
Social factors that impact samsung electronics, technological factors that impact samsung electronics, environmental factors that impact samsung electronics, legal factors that impact samsung electronics, step 3 – industry specific analysis, what is porter five forces analysis, step 4 – swot analysis / internal environment analysis, step 5 – porter value chain / vrio / vrin analysis, step 6 – evaluating alternatives & recommendations, step 7 – basis for recommendations, references :: samsung electronics case study solution.
- sales & marketing ,
- leadership ,
- corporate governance ,
- Advertising & Branding ,
- Corporate Social Responsibility (CSR) ,
Amanda Watson
Leave your thought here

© 2019 Texas Business School. All Rights Reserved
USEFUL LINKS
Follow us on.
Subscribe to our newsletter to receive news on update.

Dark Brown Leather Watch
$200.00 $180.00

Dining Chair
$300.00 $220.00

Creative Wooden Stand
$100.00 $80.00
2 x $180.00
2 x $220.00
Subtotal: $200.00
Free Shipping on All Orders Over $100!

Wooden round table
$360.00 $300.00
Hurley Dry-Fit Chino Short. Men's chino short. Outseam Length: 19 Dri-FIT Technology helps keep you dry and comfortable. Made with sweat-wicking fabric. Fitted waist with belt loops. Button waist with zip fly provides a classic look and feel .

- Order Status
- Testimonials
- What Makes Us Different
Samsung Electronics Company Harvard Case Solution & Analysis
Home >> Harvard Case Study Analysis Solutions >> Samsung Electronics Company
Introduction
Samsung started its operations in the late 60’s. Over the period of time, Samsungdeveloped its stance in the television market by offering black and white TVs in the Korean market. After some time, the Vicepresidentforglobal marketing revealedthe overall brand strategy of Samsung in order to make itselfa global brand, leading to more sustainableoperations and long term brand building.
The company from itsinitiation focused on research and development techniques and invested heavily to capture the market opportunity. In addition, Samsung also invested in the different product categories, from TVs to mobile phones to recorder and thirdparty chip productions . All these strategies allowed Samsung to effectively pursue productdevelopment strategies that made it a strong and competitive player in the tech market.
However, in the current situation, withadvancement in technology and increasing market competition, Samsung has to devise a new strategy in order to sustain its position in the market and retain its market share along with the elevation of its market position as the top brand in the mind of customer. Therefore to deal with this, two alternatives have been proposed in order to enable Samsung elevate its position in theglobal marketand rank itself among the top ten global brands.
Problem statement
“ Samsung has elevated its position in the global market making itself a renowned brand, howeverreaching thetop10 rank in global market and sustaining it is a challenge for the company ”
Samsung Electronics Company Harvard Case Solution & Analysis
Justification
Since competition is increasing in the market, as Chinese brands are entering with strongerbrandstrategy along withcheaper immitigabletechnology, maintaining the valueproposition has become difficult for Samsung, making it a huge challenge for the company to elevate its position in the global market.
Qualitative Analysis
Swot analysis.
- The company has strong brand image and market recognition that allow the customer to quickly choose Samsung over other brands.
- The company has strong financial background. This allows the company to invest heavily in the research and development department and establish new and innovative product base in the market.
- The company has corporative culture based on merit.This allows the new talent to invest the energy and efforts to rise in position and on the other hand, allows the company to achieve its goals timely.
- The company has high brand equity and market yield as compared to other competitors.
- The company has well established brand strategy that allows it to pursue economies of scale.
- The company has weak global strategy to address the market changes and trends.
- The company overly depends on the DRAMs and since technology is imitable, it hinders the company’s stance in sustaining its competitive edge.
- The Chinese market players are emerging in the market, capturing the market of Samsung.
- The brand image of Samsung remains inferior to Ios, as it uses Google free platform of Android.
Opportunities
- The semi-conductor market is increasing on a high scale, allowing the company to pursue the market development and market penetration strategy.
- Since in the current scenario, DRAMs are at the peak level, there is no other alternative present for the technology, giving company exclusiveness in the market.
- The demand for DRAMS is ever rising in the market.................
This is just a sample partical work. Please place the order on the website to get your own originally done case solution.
Related Case Solutions & Analyses:

Hire us for Originally Written Case Solution/ Analysis
Like us and get updates:.
Harvard Case Solutions
Search Case Solutions
- Accounting Case Solutions
- Auditing Case Studies
- Business Case Studies
- Economics Case Solutions
- Finance Case Studies Analysis
- Harvard Case Study Analysis Solutions
- Human Resource Cases
- Ivey Case Solutions
- Management Case Studies
- Marketing HBS Case Solutions
- Operations Management Case Studies
- Supply Chain Management Cases
- Taxation Case Studies
More From Harvard Case Study Analysis Solutions
- True Leadership: Leading with Meaning
- Privatization of Anatolia National Telekom: NALI Confidential Instructions
- Lyonbiopole: The Challenge of Becoming a World-class Biotechnology Cluster
- Cost Benefit Analysis Paper
- Gracious Eloise: What Do Angels Want (A)
- Shui On: Branding Properties for Sustainable Growth in China
Contact us:
Check Order Status

How Does it Work?
Why TheCaseSolutions.com?

Samsung PESTEL Analysis

Before we dive deep into the PESTEL analysis, let’s get the business overview of Samsung. Samsung is a South Korean multinational conglomerate headquartered in Samsung Town, Seoul. It was founded in 1938 by Lee Byung-Chul as a trading company and has since diversified into various sectors, including electronics, heavy industries, construction, insurance, and entertainment.
Samsung has numerous subsidiaries and affiliated businesses, making it one of the world’s largest and most influential companies.
- Electronics: Samsung Electronics, a subsidiary of Samsung Group, is the world’s largest consumer electronics and semiconductors manufacturer. The company’s product portfolio includes smartphones, tablets, televisions, home appliances, and more. Samsung’s flagship smartphone series, the Galaxy line, is one of the top-selling devices globally.
- Semiconductors: Samsung Electronics is also a leading player in the semiconductor industry, particularly in memory chips (DRAM, NAND flash) and system LSI (Logic Chip). The company is a key supplier to numerous global tech giants, providing them with product components.
- Display technology: Samsung Display, another subsidiary, is a global leader in display technology, producing LCD, LED, and OLED panels for various devices, such as smartphones, TVs, and monitors.
- Heavy Industries: Samsung Heavy Industries is one of the world’s largest shipbuilders, primarily focusing on large-scale commercial vessels and offshore platforms for the oil and gas industries.
- Construction: Samsung C&T is globally involved in construction, engineering, and infrastructure projects. They have been responsible for constructing notable landmarks like the Burj Khalifa in Dubai and the Petronas Twin Towers in Malaysia.
- Finance and Insurance: Samsung operates in the financial sector through Samsung Life Insurance, Samsung Fire & Marine Insurance, and Samsung Card, providing various financial services and insurance products.
- Entertainment: The conglomerate has a presence in the entertainment industry through its subsidiary, SM Entertainment, which manages some of South Korea’s most popular K-pop artists and groups.
- Biopharmaceuticals: Samsung Biologics and Samsung Bioepis are subsidiaries focusing on developing and manufacturing biopharmaceutical products, including biosimilars and novel drugs.
Samsung’s business model is characterized by its focus on vertical integration, innovation, and a solid commitment to research and development. Despite facing challenges from competitors and geopolitical tensions, Samsung remains a dominant player in the global market.
For 2023, Samsung reported KRW 302.23 trillion ($231 billion) in annual revenue, a record high, and KRW 43.38 trillion ($33 billion) in operating profit.
Here is the PESTEL analysis of Samsung
A PESTEL analysis is a strategic management framework used to examine the external macro-environmental factors that can impact an organization or industry. The acronym PESTEL stands for:
- Political factors: Relate to government policies, regulations, political stability, and other political forces that may impact the business environment.
- Economic factors: Deal with economic conditions and trends affecting an organization’s operations, profitability, and growth.
- Sociocultural factors: Relate to social and cultural aspects that may influence consumer preferences, lifestyles, demographics, and market trends.
- Technological factors: Deal with developing and applying new technologies, innovations, and trends that can impact an industry or organization.
- Environmental factors: Relate to ecological and environmental concerns that may affect an organization’s operations and decision-making.
- Legal factors: Refer to the laws and regulations that govern businesses and industries.
By the way, here is a course that will help you stand out in the world of strategy. The Strategic Thinking program for CxO by Cambridge Judge Business School maps your competitive advantage and teaches advanced techniques to formulate, evaluate, and execute winning strategies. Generate winning strategies and learn how to renew them in times of crisis for a competitive advantage.
In this article, we will do a PESTEL Analysis of Samsung.
PESTEL Analysis Framework: Explained with Examples
- Government Policies : The policies of the governments where Samsung operates can significantly affect the company’s operations. For example, tax policies, labor laws, environmental regulations, trade restrictions and tariffs, and political stability can influence Samsung’s business strategies.
- Trade Agreements : Samsung, being a South Korean company, benefits significantly from the free trade agreements that South Korea has with other countries. These agreements can lower tariffs and make Samsung’s products more competitive internationally.
- Political Stability : Political stability in the countries where Samsung operates is crucial. Instability, such as political unrest, can disrupt Samsung’s operations and supply chain, causing uncertainty and potential losses.
- Intellectual Property Laws : Samsung’s success relies heavily on innovation and technological advancement, making intellectual property rights crucial. Political factors influence the strength and enforcement of these rights. These rights could harm Samsung’s competitiveness if they aren’t adequately protected.
- Regulatory Changes : Changes in technology standards, privacy laws, and data protection regulations can also impact Samsung. For example, changing user data and privacy regulations could affect how Samsung designs and markets its products.
- International Relations : As a multinational corporation, Samsung is affected by the international relations between South Korea and other countries. Political tensions or conflicts can lead to trade restrictions or boycotts that harm Samsung’s sales.
- Labor laws : Political decisions can impact labor laws, affecting Samsung’s workforce strategy.
- Global Economic Conditions : As a multinational corporation, Samsung is affected by the economic conditions of its countries. For instance, economic recessions or booms in these countries can influence consumer purchasing power and demand for Samsung’s products.
- Currency Exchange Rates : Since Samsung operates globally, fluctuations in currency exchange rates can impact the company’s profits. If the South Korean won strengthens against other currencies, Samsung’s products may become more expensive in international markets, potentially reducing sales.
- Inflation Rates : High inflation rates in certain countries can decrease the purchasing power of consumers, affecting the demand for Samsung products. On the other hand, low inflation may increase purchasing power and increase demand for Samsung’s products.
- Interest Rates : Interest rates can impact Samsung’s costs. For instance, if Samsung has taken loans for its operations or expansion, higher interest rates would increase the cost of those loans.
- Unemployment Rates : Higher unemployment rates typically lead to lower consumer spending, which can reduce demand for Samsung’s products. Conversely, lower unemployment rates might increase consumer spending and demand for Samsung’s products.
- Economic Policies : Government economic policies such as fiscal policy (taxation, government spending), monetary policy (interest rates, money supply), and industrial policy (subsidies, incentives for innovation) can influence Samsung’s operations and profitability.
- Economic Integration : Samsung benefits from the economic integration of different markets, such as the European Union or ASEAN, which can reduce trade barriers and increase market access.
- Consumer Confidence : The level of consumer confidence in the economy can affect their spending habits, impacting the demand for Samsung’s products.
- Samsung SWOT Analysis
By the way, to communicate our strategy effectively within the team, we all need a robust collaboration platform. Miro is the leading visual collaboration platform. Build anything together on Miro. It’s free and as easy to use as a whiteboard , but endlessly more powerful. Do use the Miro platform for strong communication within your team.
Sociocultural
- Consumer Attitudes and Behaviors : Different societies have different attitudes towards technology, its role in everyday life, and the speed at which they adopt new technologies. Understanding these attitudes is crucial for Samsung to effectively market its products and innovate.
- Lifestyle Trends : Changes in lifestyle trends can impact the demand for Samsung’s products. For example, an increasing emphasis on health and fitness may increase demand for wearable tech like Samsung’s smartwatches that offer health tracking features.
- Demographics : Demographic factors such as population, age structure, income levels, and education levels can influence the market for Samsung. For instance, younger populations might be more likely to adopt new technology products quickly.
- Cultural Differences : Different cultures have different preferences and needs, which Samsung needs to consider when designing and marketing its products. For example, color symbolism varies between cultures, which might affect Samsung’s color options in different countries.
- Social Norms and Values : The norms and values of a society can affect the acceptance and use of Samsung’s products. For instance, communities concerned about privacy may be more cautious about using smart devices.
- Education Levels : Higher education levels often correlate with higher technology adoption rates, which could increase the market for Samsung’s products.
- Environmental and Social Responsibility : Consumers are increasingly concerned about the social and environmental impact of the products they buy. Samsung’s commitment to environmental sustainability and ethical practices can influence consumers’ perceptions and purchasing decisions.
- Changing Work Patterns : With the increased remote working, there might be an increased demand for certain products like tablets, laptops, and smartphones.
Technological
- Technological Innovation : Technological innovation in the electronics industry is rapid. Samsung must continually invest in R&D to keep up with new technologies, from advancements in screen technology (like OLED and Micro-LED) to developments in artificial intelligence, 5G, IoT, etc.
- Technological Obsolescence : Given the rapid pace of technology change, products can become obsolete quickly. Samsung must manage its product lifecycle effectively to minimize losses from obsolete inventory and maintain its competitive edge.
- Adoption of New Technologies : How quickly and effectively Samsung can adopt and implement new technologies can impact its market position. This includes technologies used in its products and those used in manufacturing processes.
- Technological Infrastructure : The state of technical infrastructure in Samsung’s markets can affect its sales. For example, a region’s rollout of 5G networks can influence the demand for 5 G-capable smartphones.
- Digital Transformation : Advances in digital technologies are transforming how businesses operate. Samsung must adapt to these changes in e-commerce, digital marketing, remote working, and digital services.
- Cybersecurity : With increasing digitization and connectivity, cybersecurity threats are a significant concern. Samsung must ensure robust security features in its devices and protect its information systems from cyber threats.
- Regulatory Changes in Technology : Changes in technology-related regulations can impact Samsung. This includes regulations around data privacy, AI, digital rights, etc.
- Patents and Intellectual Property : Patents and IP rights are crucial in the tech industry. Samsung must navigate this landscape effectively to protect its innovations and avoid infringing on the rights of others.
Environmental
- Climate Change : Climate change can impact Samsung’s operations, especially its supply chain and manufacturing processes. For instance, climate-related disasters can disrupt the supply chain, and regulatory responses to climate change (like carbon pricing) could increase operational costs.
- Waste Management : Electronic waste is a significant environmental issue, and Samsung, as a major electronics manufacturer, is expected to manage this responsibly. This includes designing products for easier recycling and offering take-back programs for old devices.
- Energy Efficiency : There is increasing consumer and regulatory focus on the energy efficiency of electronic devices. Samsung must ensure its products are energy-efficient to comply with regulations and meet customer expectations.
- Resource Scarcity : Some electronic device resources are scarce or associated with environmental and social issues (like conflict minerals). Samsung must manage its resource use responsibly to ensure supply and protect its reputation.
- Pollution : Manufacturing processes in the electronics industry can contribute to pollution (like air and water pollution). Samsung must manage this to comply with environmental regulations and meet increasing consumer expectations for environmentally-friendly practices.
- Green Products : There is a growing demand for “green” products with a lower environmental impact. Samsung can tap into this demand by designing products with lower environmental impact, such as recycled materials.
- Environmental Regulations : Regulations related to environmental issues (like carbon emissions, e-waste, energy efficiency, etc.) can impact Samsung’s operations, product design, and marketability.
- Social Pressure : Consumers and society, in general, are increasingly concerned about environmental issues, and companies are expected to demonstrate their environmental responsibility. Samsung’s environmental reputation can influence its brand image and customer loyalty.
- Product Safety Regulations : Samsung must ensure that all its products meet safety regulations in every market. Failure to comply could result in product recalls, fines, and brand reputation damage.
- Intellectual Property Laws : As a tech company, Samsung must protect its innovations through patents, trademarks, and copyrights. It also needs to ensure it doesn’t infringe on the IP rights of others, which could lead to legal disputes.
- Employment Laws : Samsung must comply with labor and employment laws in its operating countries. This includes laws related to wages, working hours, health and safety, and discrimination.
- Data Protection and Privacy Laws : With many of its devices storing or processing personal data, Samsung must comply with data protection and privacy laws, such as the General Data Protection Regulation (GDPR) in the European Union.
- Environmental Laws : Samsung has to adhere to various environmental laws and regulations concerning waste disposal, recycling, energy use, and pollution. This is particularly relevant given Samsung’s role as a major electronics manufacturer.
- Anti-Trust Laws : Samsung must comply with antitrust and competition laws to prevent unfair business practices and promote fair competition.
- Trade Regulations : As a global company, Samsung is subject to various international trade regulations, including export controls, tariffs, and sanctions.
- Consumer Protection Laws : These laws protect consumers from unfair business practices. Samsung must adhere to these laws in all areas, including advertising, product safety, and customer service.
Check out the PESTEL Analysis of Global Businesses
Related posts.

Siemens PESTEL Analysis

Lush Cosmetics PESTEL Analysis

AstraZeneca PESTEL Analysis

Carrefour PESTEL Analysis

Jaguar Land Rover PESTEL Analysis

Virgin Atlantic PESTEL Analysis

HSBC PESTEL Analysis

Delta Air Lines PESTEL Analysis
Type above and press Enter to search. Press Esc to cancel.
Fern Fort University
Samsung electronics case study analysis & solution, harvard business case studies solutions - assignment help.
Samsung Electronics is a Harvard Business (HBR) Case Study on Strategy & Execution , Fern Fort University provides HBR case study assignment help for just $11. Our case solution is based on Case Study Method expertise & our global insights.
Strategy & Execution Case Study | Authors :: Jordan Siegel, James Jinho Chang
Case study description.
To maximize their effectiveness, color cases should be printed in color.When is it possible to create a dual advantage of being both low cost and differentiated? In this case, students assess whether Samsung Electronics has been able to achieve such a dual advantage, and if so, how this was possible. Moreover, Samsung Electronics' long-held competitive advantage is under renewed attack. Students also can assess how Samsung should respond to large-scale Chinese entry into its industry.
Competitive strategy, Cross-cultural management, Globalization, Technology
Order a Strategy & Execution case study solution now
To Search More HBR Case Studies Solution Go to Fern Fort University Search Page
[10 Steps] Case Study Analysis & Solution
Step 1 - reading up harvard business review fundamentals on the strategy & execution.
Even before you start reading a business case study just make sure that you have brushed up the Harvard Business Review (HBR) fundamentals on the Strategy & Execution. Brushing up HBR fundamentals will provide a strong base for investigative reading. Often readers scan through the business case study without having a clear map in mind. This leads to unstructured learning process resulting in missed details and at worse wrong conclusions. Reading up the HBR fundamentals helps in sketching out business case study analysis and solution roadmap even before you start reading the case study. It also provides starting ideas as fundamentals often provide insight into some of the aspects that may not be covered in the business case study itself.
Step 2 - Reading the Samsung Electronics HBR Case Study
To write an emphatic case study analysis and provide pragmatic and actionable solutions, you must have a strong grasps of the facts and the central problem of the HBR case study. Begin slowly - underline the details and sketch out the business case study description map. In some cases you will able to find the central problem in the beginning itself while in others it may be in the end in form of questions. Business case study paragraph by paragraph mapping will help you in organizing the information correctly and provide a clear guide to go back to the case study if you need further information. My case study strategy involves -
- Marking out the protagonist and key players in the case study from the very start.
- Drawing a motivation chart of the key players and their priorities from the case study description.
- Refine the central problem the protagonist is facing in the case and how it relates to the HBR fundamentals on the topic.
- Evaluate each detail in the case study in light of the HBR case study analysis core ideas.
Step 3 - Samsung Electronics Case Study Analysis
Once you are comfortable with the details and objective of the business case study proceed forward to put some details into the analysis template. You can do business case study analysis by following Fern Fort University step by step instructions -
- Company history is provided in the first half of the case. You can use this history to draw a growth path and illustrate vision, mission and strategic objectives of the organization. Often history is provided in the case not only to provide a background to the problem but also provide the scope of the solution that you can write for the case study.
- HBR case studies provide anecdotal instances from managers and employees in the organization to give a feel of real situation on the ground. Use these instances and opinions to mark out the organization's culture, its people priorities & inhibitions.
- Make a time line of the events and issues in the case study. Time line can provide the clue for the next step in organization's journey. Time line also provides an insight into the progressive challenges the company is facing in the case study.
Step 4 - SWOT Analysis of Samsung Electronics
Once you finished the case analysis, time line of the events and other critical details. Focus on the following -
- Zero down on the central problem and two to five related problems in the case study.
- Do the SWOT analysis of the Samsung Electronics . SWOT analysis is a strategic tool to map out the strengths, weakness, opportunities and threats that a firm is facing.
- SWOT analysis and SWOT Matrix will help you to clearly mark out - Strengths Weakness Opportunities & Threats that the organization or manager is facing in the Samsung Electronics
- SWOT analysis will also provide a priority list of problem to be solved.
- You can also do a weighted SWOT analysis of Samsung Electronics HBR case study.
Step 5 - Porter 5 Forces / Strategic Analysis of Industry Analysis Samsung Electronics
In our live classes we often come across business managers who pinpoint one problem in the case and build a case study analysis and solution around that singular point. Business environments are often complex and require holistic solutions. You should try to understand not only the organization but also the industry which the business operates in. Porter Five Forces is a strategic analysis tool that will help you in understanding the relative powers of the key players in the business case study and what sort of pragmatic and actionable case study solution is viable in the light of given facts.
Step 6 - PESTEL, PEST / STEP Analysis of Samsung Electronics
Another way of understanding the external environment of the firm in Samsung Electronics is to do a PESTEL - Political, Economic, Social, Technological, Environmental & Legal analysis of the environment the firm operates in. You should make a list of factors that have significant impact on the organization and factors that drive growth in the industry. You can even identify the source of firm's competitive advantage based on PESTEL analysis and Organization's Core Competencies.
Step 7 - Organizing & Prioritizing the Analysis into Samsung Electronics Case Study Solution
Once you have developed multipronged approach and work out various suggestions based on the strategic tools. The next step is organizing the solution based on the requirement of the case. You can use the following strategy to organize the findings and suggestions.
- Build a corporate level strategy - organizing your findings and recommendations in a way to answer the larger strategic objective of the firm. It include using the analysis to answer the company's vision, mission and key objectives , and how your suggestions will take the company to next level in achieving those goals.
- Business Unit Level Solution - The case study may put you in a position of a marketing manager of a small brand. So instead of providing recommendations for overall company you need to specify the marketing objectives of that particular brand. You have to recommend business unit level recommendations. The scope of the recommendations will be limited to the particular unit but you have to take care of the fact that your recommendations are don't directly contradict the company's overall strategy. For example you can recommend a low cost strategy but the company core competency is design differentiation.
- Case study solutions can also provide recommendation for the business manager or leader described in the business case study.
Step 8 -Implementation Framework
The goal of the business case study is not only to identify problems and recommend solutions but also to provide a framework to implement those case study solutions. Implementation framework differentiates good case study solutions from great case study solutions. If you able to provide a detailed implementation framework then you have successfully achieved the following objectives -
- Detailed understanding of the case,
- Clarity of HBR case study fundamentals,
- Analyzed case details based on those fundamentals and
- Developed an ability to prioritize recommendations based on probability of their successful implementation.
Implementation framework helps in weeding out non actionable recommendations, resulting in awesome Samsung Electronics case study solution.
Step 9 - Take a Break
Once you finished the case study implementation framework. Take a small break, grab a cup of coffee or whatever you like, go for a walk or just shoot some hoops.
Step 10 - Critically Examine Samsung Electronics case study solution
After refreshing your mind, read your case study solution critically. When we are writing case study solution we often have details on our screen as well as in our head. This leads to either missing details or poor sentence structures. Once refreshed go through the case solution again - improve sentence structures and grammar, double check the numbers provided in your analysis and question your recommendations. Be very slow with this process as rushing through it leads to missing key details. Once done it is time to hit the attach button.
Previous 5 HBR Case Study Solution
- Mobileye: The Future of Driverless Cars Case Study Solution
- Head Ski Co., Inc. Case Study Solution
- Undermining Staying Power: The Role of Unhelpful Management Theories Case Study Solution
- DreamCycles: Sustaining Growth Case Study Solution
- THEOTIS WILEY - Confidential Instructions for Erive's Vice-President of Business Development Case Study Solution
Next 5 HBR Case Study Solution
- Intel Corp.--1968-2003 Case Study Solution
- Social Strategy at Cisco Systems Case Study Solution
- $19B 4 txt app WhatsApp...omg! Case Study Solution
- E Ink in 2005 Case Study Solution
- LinkedIn Corp., 2008 Case Study Solution
Special Offers
Order custom Harvard Business Case Study Analysis & Solution. Starting just $19
Amazing Business Data Maps. Send your data or let us do the research. We make the greatest data maps.
We make beautiful, dynamic charts, heatmaps, co-relation plots, 3D plots & more.
Buy Professional PPT templates to impress your boss
Nobody get fired for buying our Business Reports Templates. They are just awesome.
- More Services
Feel free to drop us an email
- fernfortuniversity[@]gmail.com
- (000) 000-0000
- Privacy Policy
Samsung Case Study Analysis
The advancing technology has narrowed the knowledge boundary amongst the organizations, necessitating innovative approaches that would provide their goods and services with differentiating elements to give them cutting edge leverage. Analysis and identification of the changing trends of the customer requirements are essential ingredients to gain leverage against their rivals (Grant, 2007). In such a scenario, the five forces analysis of producer business becomes critical factors of a competitive advantage, which are: industry rivalry, bargaining power of suppliers, bargaining power of buyers; competition from substitute; and the threat of entry.
The industry rivalry amongst the producer businesses is an essential criterion for introducing cutting edge differentiating elements in the products to gain leverage. This is one of the primary motivating factors for Samsung Inc to be highly innovative in its products and development processes.

The quality and creative input within the product gives a huge advantage to the suppliers and puts him in a bargaining position. Samsung producing high-quality memory chips at relatively low cost has been able to bargain with its customers.
The bargaining power of buyers is reduced when there is a short supply of quality goods that have a high demand. In the case of Samsung, the buyers increasingly prefer them because of their quality products and their credibility of supplying goods timely.
Technological advancements have brought forth an explosion of information that is easily accessible to the public through the internet and other media like television, radio, mobile phones, etc. The competition from substitute become highly likely, and the company needs to adopt an innovative approach to its marketing . Samsung has successfully met this aspect by evolving flexible strategies like an innovative product like and introducing elements of surprise within the products as well within the marketing of the products and services.
Last but not least is the threat from new entrants of the business. Globalization has provided facilitating grounds for new entrants. Therefore, the existing firms must ensure that speed and flexibility become an intrinsic part of their strategy as they become essential ingredients for the products so that the organizations can timely and efficiently meet the fast-changing preferences of the customers.
Under the dynamic leadership of Kun Hee Lee, the company enjoyed a competitive advantage over its rivals in the world market, primarily because of the sharp business foresight and risk-taking capability. The Chairman’s long-term vision and ability to harness the potential of the customers’ shifting tastes have given them leverage in the highly competitive sector of semiconductor and electronic gadgets. The company became known for their revolutionary product lines of fairly low-cost quality. It was able to give stiff competition to electronic majors like Sony, Nokia, Phillips, etc. by the continuous development of new features in all its products.
Many factors contributed to the company’s continued leadership position in the world market. The foremost was its business model focusing on creative goods focused on speed. The business has concentrated on its research and development skills strategy to develop and improvise innovatively on Sony’s electrical and digital products, Phillips, Matsushita, and Nokia. Samsung’s ability to launch its products with added features with high speed was a huge success with the target population. Samsung had set up his professional teams to keep a close eye on the pulse of the people and was thus able to predict their demands and used to come up with new products and features that were envied by its rivals.
Samsung’s business strategy was its focused approach towards R&D and utilizing his human resource as capital investment. His team was able to develop a vast range within the same product because they were able to customize new products around their core design. He also introduced the concept of competing for product development teams, which were located at diverse locations, thus promoting competition with the group for innovation. Within the party, the merit-based promotion ensured that the best earned their dues. High potential employees were encouraged to MBA and Ph.D. in a foreign country on the company’s expenses so that the expert team could be indigenously developed and fostered for improved business performance.
Samsung has a great future because, in the changing paradigms of the business environment, it continuously strives to identify factors and issues that would help meet the challenges with efficiency and unmatched proficiency. There are two major areas where Samsung is able to stay ahead of the Chinese companies. The first one is its state of the art R&D, which significantly facilitates the development of new products through specialized product development teams. The latest products ensure that the constantly changing preferences of the customers are met timely, thus making sure that they maintain their leadership position. One can, therefore, conclude that one of the main factors that have facilitated the company to keep abreast with the changes and maintain a competitive edge over their rivals, in its market plan, it’s been able to check new strategies.
Samsung was a market leader in the semiconductor, electronics, and telecommunications accessories business in 2005. With 337 international operations spread in 58 countries and 212,000 safe workforces, overall revenue of the company reached $135 billion in 2004. The major cost drivers for Samsung have been its policy of innovation and state of the art R&D programs. The second most crucial factor has been the intrinsic belief of its CEO on the capabilities of its workforce and merit-based promotions that motivate the employees of all ages.
The fact that the Chief operating officer intrinsically believed in the potential of its rivals and through continuous vigil on its rivals’ business strategy and product line, he was able to anticipate their future course. Porter argues that a ‘company can outperform rivals only if it can establish a difference that it can preserve. It must deliver greater value to customers or create comparable value at a lower cost, or do both’ (Porter, 1980). This was the main reason that the CEO of Samsung was able to keep ahead of the Chinese firms and maintain its competitive edge in the area of semiconductors, microchips, and electronic goods.
Yes, because Samsung has understood that it needs to look at the various options of competitive advantage to respond appropriately so that it could maintain its leadership position within the semiconductor market. The sustainability of the product shelf life has lost relevance because the brands ensure the sustainability of their products through creative changes in the product that brings them at par with the latest technology and caters to the universal appeal for the product, making it perennially popular. Backed by a capable R&D team, the company has the requisite infrastructure and capabilities to design and produce innovative products. The Chinese firms have yet to acquire expert knowledge about core semiconductor units design and manufacturing technology. This gives a massive advantage to Samsung to go in for new products and create a niche market for them in the emerging modern economies like India, China, Brazil, etc. It is assumed that despite huge government concessions to Chinese firms in China, lack of adequate intellectual property laws would be a significant deterrent for other big companies to transfer technology. Samsung, therefore, would be right to continue innovative products and add-ons for existing as well as for new markets.
References;
- Grant, Robert M. (2007). Contemporary Strategic Analysis. (6th edition). Blackwell.
- Porter, Michael, E.(June 1, 1980). Competitive Strategy: Techniques for analyzing industries and competitors. NY: Free Press 1998
- Siegel, Jordon, and Chang, James Jinho. (2009). Samsung Electronics. Harvard Business School .
Related Posts
A case study on sustainable building, suspicious behaviors of malware in android, how epa links with the superfund in new..., nokia case study analysis, importance of public spaces in a neighbourhood of..., community based tourism in uganda and tanzania, mount st. helens hazardous simulations, the contradiction of homosexuality, walmart cross-cultural issues case study analysis, case study on leadership and management, leave a comment cancel reply.
Please enter an answer in digits: five × 4 =

- Free Case Studies
- Business Essays
Write My Case Study
Buy Case Study
Case Study Help
- Case Study For Sale
- Case Study Service
- Hire Writer
Samsung Case Analysis
Issues As South Korea’s largest conglomerate, Samsung includes Samsung Electronics, Samsung Heavy Industries, and Samsung Engineering ; Construction.
Started in 1938 as a company that produced agricultural products, the company began to focus on shipbuilding, chemicals, and textiles in 1970. Since after Samsung Electronics Company (SEC) was founded in 1969, Samsung acquired a semiconductor business and supplied global markets with massive quantities of commodity products. With the transformation that was led by the leadership of SEC Chairman Kun Hee Lee, Samsung rebuilt its image as a global business leader.
We Will Write a Custom Case Study Specifically For You For Only $13.90/page!
Following the chairman’s new management initiative, Samsung is now in a stage of investing in innovative and premium products to increase their brand value. Despite Samsung’s rapidly increasing global market share, the Samsung brand was not widely known outside of Korea until Samsung decided to recruit a Korea-born general manager, Eric Kim. With his effort to build the corporate brand image across the markets of 200 countries, Samsung was able to generate tremendous brand visibility worldwide with its DigitAll campaign.
While Samsung has experienced great success in marketing, some important issues remain to be addressed to increase their market share and brand power: ? ? ? ? Market share should be expanded by penetrating weaker markets; Marketing communications need to move more consumers into the “delights me” and “perfect fit” relationship categories; Less emphasis should be placed on youth and creativity, as that might be inappropriate; and A more complex customer segmentation should be marketed in its marketing planning.
Related posts:
- Marketing Strategy of Samsung Mobile
- Case Study on Samsung Electronics
- Samsung product development Case study
- Global Marketing case study-Samsung
- Samsung – Competitive Analysis
- Samsung Case
- Samsung Case Study
Quick Links
Privacy Policy
Terms and Conditions
Testimonials
Our Services
Case Study Writing Service
Case Studies For Sale
Our Company
Welcome to the world of case studies that can bring you high grades! Here, at ACaseStudy.com, we deliver professionally written papers, and the best grades for you from your professors are guaranteed!
[email protected] 804-506-0782 350 5th Ave, New York, NY 10118, USA
Acasestudy.com © 2007-2019 All rights reserved.

Hi! I'm Anna
Would you like to get a custom case study? How about receiving a customized one?
Haven't Found The Case Study You Want?
For Only $13.90/page
Samsung owes $142 mln in wireless patent case, jury says
- Medium Text

- Company Samsung Electronics Co Ltd Follow
Sign up here.
Reporting by Blake Brittain in Washington
Our Standards: The Thomson Reuters Trust Principles. New Tab , opens new tab

Thomson Reuters
Blake Brittain reports on intellectual property law, including patents, trademarks, copyrights and trade secrets, for Reuters Legal. He has previously written for Bloomberg Law and Thomson Reuters Practical Law and practiced as an attorney.
Read Next / Editor's Picks

Industry Insight Chevron

Mike Scarcella, David Thomas

Karen Sloan

Henry Engler

Diana Novak Jones

The not-so-silent type Vulnerabilities across keyboard apps reveal keystrokes to network eavesdroppers
阅读本报告的简体中文版摘要 | 閱讀本報告的繁體中文版摘要 | Read the Report on Github
Key findings
- We analyzed the security of cloud-based pinyin keyboard apps from nine vendors — Baidu, Honor, Huawei, iFlytek, OPPO, Samsung, Tencent, Vivo, and Xiaomi — and examined their transmission of users’ keystrokes for vulnerabilities.
- Our analysis revealed critical vulnerabilities in keyboard apps from eight out of the nine vendors in which we could exploit that vulnerability to completely reveal the contents of users’ keystrokes in transit. Most of the vulnerable apps can be exploited by an entirely passive network eavesdropper.
- Combining the vulnerabilities discovered in this and our previous report analyzing Sogou’s keyboard apps, we estimate that up to one billion users are affected by these vulnerabilities. Given the scope of these vulnerabilities, the sensitivity of what users type on their devices, the ease with which these vulnerabilities may have been discovered, and that the Five Eyes have previously exploited similar vulnerabilities in Chinese apps for surveillance, it is possible that such users’ keystrokes may have also been under mass surveillance.
- We reported these vulnerabilities to all nine vendors. Most vendors responded, took the issue seriously, and fixed the reported vulnerabilities, although some keyboard apps remain vulnerable.
- We conclude our report by summarizing our recommendations to various stakeholders to attempt to reduce future harm from apps which might feature similar vulnerabilities.
Introduction
Typing logographic languages such as Chinese is more difficult than typing alphabetic languages, where each letter can be represented by one key. There is no way to fit the tens of thousands of Chinese characters that exist onto a single keyboard. Despite this obvious challenge, technologies have developed which make typing in Chinese possible. To enable the input of Chinese characters, a writer will generally use a keyboard app with an “Input Method Editor” (IME). IMEs offer a variety of approaches to inputting Chinese characters, including via handwriting, voice, and optical character recognition (OCR). One popular phonetic input method is Zhuyin , and shape or stroke -based input methods such as Cangjie or Wubi are commonly used as well. However, used by nearly 76% of mainland Chinese keyboard users, the most popular way of typing in Chinese is the pinyin method , which is based on the pinyin romanization of Chinese characters.
All of the keyboard apps we analyze in this report fall into the category of input method editors (IMEs) that offer pinyin input. These keyboard apps are particularly interesting because they have grown to accommodate the challenge of allowing users to type Chinese characters quickly and easily. While many keyboard apps operate locally, solely within a user’s device, IME-based keyboard apps often have cloud features which enhance their functionality. Because of the complexities of predicting which characters a user may want to type next, especially in logographic languages like Chinese, IMEs often offer “cloud-based” prediction services which reach out over the network. Enabling “cloud-based” features in these apps means that longer strings of syllables that users type will be transmitted to servers elsewhere. As many have previously pointed out , “cloud-based” keyboards and input methods can function as vectors for surveillance and essentially behave as keyloggers. While the content of what users type is traveling from their device to the cloud, it is additionally vulnerable to network attackers if not properly secured. This report is not about how operators of cloud-based IMEs read users’ keystrokes, which is a phenomenon that has already been extensively studied and documented. This report is primarily concerned with the issue of protecting this sensitive data from network eavesdroppers.
In this report, we analyze the security of cloud-based pinyin keyboard apps from nine vendors: Baidu, Honor, Huawei, iFlytek, OPPO, Samsung, Tencent, Vivo, and Xiaomi. We examined these apps’ transmission of users’ keystrokes for vulnerabilities. Our analysis revealed critical vulnerabilities in keyboard apps from eight out of the nine vendors — all but Huawei — in which we could exploit that vulnerability to completely reveal the contents of users’ keystrokes in transit.
Between this report and our Sogou report , we estimate that close to one billion users are affected by this class of vulnerabilities. Sogou, Baidu, and iFlytek IMEs alone comprise over 95% of the market share for third-party IMEs in China, which are used by around a billion people . In addition to the users of third party keyboard apps, we found that the default keyboards on devices from three manufacturers (Honor, OPPO, and Xiaomi) were also vulnerable to our attacks. Devices from Samsung and Vivo also bundled a vulnerable keyboard, but it was not used by default. In 2023, Honor, OPPO, and Xiaomi alone comprised nearly 50% of the smartphone market in China.
Having the capability to read what users type on their devices is of interest to a number of actors — including government intelligence agencies that operate globally — because it may encompass exceptionally sensitive information about users and their contacts including financial information, login credentials such as usernames or passwords, and messages that are otherwise end-to-end encrypted. Given the known capabilities of state actors, and that Five Eyes agencies have previously exploited similar vulnerabilities in Chinese apps for the express purpose of mass surveillance, it is possible that we were not the first to discover these vulnerabilities and that they have previously been exploited on a mass scale for surveillance purposes.
We reported these issues to all eight of the vendors in whose keyboards we found vulnerabilities. Most vendors responded, took the issue seriously, and fixed the reported vulnerabilities, although some keyboard apps remain vulnerable. Users should keep their apps and operating systems up to date. We recommend that they consider switching from a cloud-based keyboard app to one that operates entirely on-device if they are concerned about these privacy issues.
The remainder of this report is structured as follows. In the “ Related work ” section, we outline previous security and privacy research that has been conducted on IME apps and past research which relates to issues of encryption in the Chinese app ecosystem. In “ Methodology ”, we describe the reverse engineering tools and techniques we used to analyze the above apps. In the “ Findings ” section, we explain the vulnerabilities we discovered in each app and (where applicable) how we exploited these vulnerabilities. In “ Coordinated disclosure ”, we discuss how we reported the vulnerabilities we found to the companies and their responses to our outreach. Finally, in “ Discussion ”, we reflect on the impact of the vulnerabilities we discovered, how they came to be, and ways that we can avoid similar problems in the future. We provide recommendations to all stakeholders in this systemic privacy and security failure, including users, IME and keyboard developers, operating systems, mobile device manufacturers, app store operators, International standards bodies, and security researchers.
Related work
There has been much work analyzing East Asian apps for their security and privacy properties. As examples from outside of China, researchers studied LINE , a Japanese-developed app, and KakaoTalk , a South Korean-developed app, finding that they have faults in their end-to-end encryption implementations. When it comes to Chinese software, the Citizen Lab has previously revealed privacy and security issues in several Chinese web browsers , and identified vulnerabilities in the Zoom video conferencing platform and the MY2022 Olympics app . Unfortunately, even developers of extremely popular apps often overlook implementing proper security measures and protecting user privacy.
Some work has been concerned specifically with the privacy issues with cloud-based keyboard apps. As the technology powering keyboard apps became more popular and sophisticated, awareness of the potential security risks associated with these apps grew. Two main areas of concern have received the most attention from security researchers when it comes to cloud-based keyboard apps: whether user data is secure in the cloud servers and whether it is secure in transit as it moves from the user’s device to a cloud server.
Some researchers have expressed concern over companies handling sensitive keystroke data and have made attempts to ameliorate the risk of the cloud server being able to record what you typed. In 2013, the Japanese government published concerns it had with privacy regarding the Baidu IME, particularly the cloud input function. Researchers have also been concerned with surveillance via other “cloud-based” IMEs , like iFlytek’s voice input. While there has been a push to develop privacy-aware cloud-based IMEs that would keep user data secret, they are not widely used. While it is concerning what companies might do with user keystroke data, our research pertains to the security of user keystroke data before it even reaches cloud servers and who else other than the cloud operator may be able to read it.
Other research has studied the leakage of sensitive information when user keystroke data is in transit between a user’s device to a remote cloud server. If not properly encrypted, data can be intercepted and collected by network eavesdroppers. In 2015 security researchers proposed and evaluated a system to identify keystroke leakages in IME traffic, revealing that at least one IME was transmitting sensitive data without encrypting it at all. Another investigation in the same year showed that the most popular IME, Sogou, was sending users’ device identifiers in the clear. In our 2023 report we exposed Sogou falling short once more, finding that Sogou allowed network eavesdroppers to read what users were typing—as they typed—in any application. All of these discoveries point to developers of these applications overlooking the importance of transport security to protect user data from network attackers.
While previous work studying the security of keystroke network data in transit investigates single keyboard apps at a time, our report is the first to holistically evaluate the network security of the cloud-based keyboard app landscape in China.
Methodology
We analyzed the Android and, if present, the iOS and Windows versions of keyboard apps from the following keyboard app vendors: Tencent, Baidu, iFlytek, Samsung, Huawei, Xiaomi, OPPO, Vivo, and Honor. The first three — Tencent, Baidu, and iFlytek — are software developers of keyboard apps whereas the remaining six — Samsung, Huawei, Xiaomi, OPPO, Vivo, and Honor — are mobile device manufacturers who either developed their own keyboard apps or include one or more of the other three developers’ keyboard apps preinstalled on their devices. We selected these nine vendors because we identified them as having integrated cloud recommendation functionality into their products and because they are popularly used. To procure the versions we analyzed, between August and November, 2023, we downloaded the latest versions of them from their product websites, the Apple App Store, or, in the case of the apps developed or bundled by mobile device manufacturers, by procuring a mobile device that has the app preinstalled on the ROM . In the case that we obtained the app as pre-installed on a mobile device, we ensured that the device’s apps and operating system were fully updated before beginning analysis of its apps. The devices we obtained were intended for the mainland Chinese market, and, when device manufacturers had two editions of their device, a Chinese edition and a global edition, we analyzed the Chinese edition.
To better understand whether these vendors’ keyboard apps securely implemented their cloud recommendation functionality, we analyzed them to determine whether they sufficiently encrypted users’ typed keystrokes. To do so, we used both static and dynamic analysis methods. We used jadx to decompile and statically analyze Dalvik bytecode and IDA Pro to decompile and statically analyze native machine code. We used frida to dynamically analyze the Android and iOS versions and IDA Pro to dynamically analyze the Windows version. Finally, we used Wireshark and mitmproxy to perform network traffic capture and analysis.
To prepare for our dynamic analysis of each keyboard app, after installing it, we enabled the pinyin input if it was not already enabled. The keyboards we analyzed generally prompted users to enable cloud functionality after installation or on first use. In such cases, we answered such prompts in the affirmative or otherwise enabled cloud functionality through the mobile device’s or app’s settings.
In our analysis, we assume a fairly conservative threat model. For most of our attacks, we assume a passive network eavesdropper that monitors network packets that are sent from a user’s keyboard app to a keyboard app’s cloud server. In one of our attacks, specifically against apps using Tencent’s Sogou API , we allow the adversary to be active in a limited way in that the adversary may additionally transmit network traffic to the cloud server but does not necessarily have to be a machine-in-the-middle ( MITM ) or spoof messages from the user in a layer 3 sense. In all of our attacks, the adversary also has access to a copy of the client software, but the server is a black box.
We note that, as neither Apple’s nor Google’s keyboard apps have a feature to transmit keystrokes to cloud servers for cloud-based recommendations, we did (and could) not analyze these keyboards for the security of this feature. However, we observed that none of the mobile devices that we analyzed included Google’s keyboard, Gboard, preinstalled, either. This finding likely results from Google’s exit from China reportedly due to the company’s failure to comply with China’s pervasive censorship requirements.
Among the nine vendors whose apps we analyzed, we found that there was only one vendor, Huawei, in whose apps we could not find any security issues regarding the transmission of users’ keystrokes. For each of the remaining eight vendors, in at least one of their apps, we discovered a vulnerability in which keystrokes could be completely revealed by a passive network eavesdropper (see Table 1 for details).
Pre-installed keyboard developer
Table 1: Summary of vulnerabilities discovered in popular keyboards and in keyboards pre-installed on popular phones. * Default keyboard app on our test device. † Both QQ Pinyin and Sogou IME are developed by Tencent; in this report we analyzed QQ Pinyin and found the same issues as we had in Sogou IME .
The ease with which the keystrokes in these apps could be revealed varied. In one app, Samsung Keyboard, we found that the app performed no encryption whatsoever. Some apps appeared to internally use Sogou’s cloud functionality and were vulnerable to an attack which we previously published . Most vulnerable apps failed to use asymmetric cryptography and mistakenly relied solely on home-rolled symmetric encryption to protect users’ keystrokes.
The remainder of this section details further analysis of the apps we analyzed from each vendor and, when present, their vulnerabilities.
We have previously analyzed one Tencent keyboard app, Sogou, in a previous report . We were motivated by our previous findings analyzing Sogou to analyze another Tencent keyboard app, QQ Pinyin. We analyzed QQ Pinyin on Android and Windows. We found that the Android version (8.6.3) and Windows version (6.6.6304.400) of this software communicated to similar cloud servers as Sogou and contained the same vulnerabilities to those which we previously reported in Sogou IME (see Table 2 for details).
Table 2: The versions of QQ Pinyin that we analyzed.
We analyzed Baidu IME for Windows, Android, and iOS. We found that Baidu IME for Windows includes a vulnerability which allows network eavesdroppers to decrypt network transmissions. This means third parties can obtain sensitive personal information including what users have typed. We also found privacy and security weaknesses in the encryption used by the Android and iOS versions of Baidu IME (see Table 3 for details).
Table 3: The versions of Baidu IME that we analyzed.
The Android version transmitted keystrokes information via UDP packets to udpolimeok.baidu.com and that the Windows and iOS versions transmitted keystrokes to udpolimenew.baidu.com . The two mobile versions that we analyzed, namely the Android and iOS versions, transmitted these keystrokes according to a stronger protocol, whose payload begins with the bytes 0x04 0x00. The Windows version transmitted these keystrokes according to a weaker protocol, whose UDP payload begins with the bytes 0x03 0x01. We henceforth refer to these protocols as the BAIDUv4.0 and BAIDUv3.1 protocols, respectively. In the remainder of this section we detail multiple weaknesses in the BAIDUv4.0 protocol used by the Android and iOS versions and explain how a network eavesdropper can decrypt the contents of keystrokes transmitted by the BAIDUv3.1 protocol.
Weaknesses in BAIDUv4.0 protocol
To encrypt keystroke information, the BAIDUv4.0 protocol uses elliptic-curve Diffie-Hellman and a pinned server public key ( pk s ) to establish a shared secret key for use in a modified version of AES .
Upon opening the keyboard, before the first outgoing BAIDUv4.0 protocol message is sent, the application randomly generates a client Curve25519 public-private key pair, which we will call ( pk c , sk c ). Then, a Diffie-Hellman shared secret k is generated using sk c and a pinned public key pk s . To send a message with plaintext P , the application reuses the first 16 bytes of pk c as the initialization vector (IV) for symmetric encryption, and k is used as the symmetric encryption key. The resulting symmetric encryption of P is then sent along with pk c to the server. The server can then obtain the same Diffie-Hellman shared secret k from pk c and sk s , the private key corresponding to pk s , to decrypt the ciphertext.
The BAIDUv4.0 protocol symmetrically encrypts data using a modified version of AES, which symbols in the code indicate Baidu has called AESv3 . Compared to ordinary AES, AESv3 has a built-in cipher mode and padding. AESv3’s built-in cipher mode mixes bytes differently and uses a modified counter (CTR) mode which we call Baidu CTR (BCTR) mode, illustrated in Figure 1.
Generally speaking, any CTR cipher mode involves combining an initialization vector v with the value i of some counter, whose combination we shall notate as v + i . Most commonly, the counter value used for block i is simply i , i.e., it begins at zero and increments for each subsequent block, and AESv3’s implementation follows this convention. There is no standard way to compute v + i in CTR mode, but the way that BCTR combines v and i is by adding i to the left-most 32-bits of v , interpreting this portion of v and i in little-endian byte order. If the sum overflows, then no carrying is performed on bytes to the right of this 32-bit value. The implementation details we have thus far described do not significantly deviate from a typical CTR implementation. However, where BCTR mode differs from ordinary CTR mode is in how the value v + i is used during encryption. In ordinary CTR mode, to encrypt block i with key k , you would compute
In BCTR mode, to encrypt block i , you compute
As we will see later, this deviation will have implications for the security of the algorithm.
While ordinarily CTR mode does not require the final block length to be a multiple of the cipher’s block size (in the case of AES, 16 bytes), due to Baidu’s modifications, BCTR mode no longer automatically possesses this property but rather achieves it by employing ciphertext stealing . If the final block length n is less than 16, AESv3’s implementation encrypts the final 16 byte block by taking the last (16 – n ) bytes of the penultimate ciphertext block and prepending them to the n bytes of the ultimate plaintext block. The encryption of the resultant block fills the last (16 – n ) bytes of the penultimate ciphertext block and the n bytes of the final ciphertext block. Note, however, that this practice only works when the plaintext consists of at least two blocks. Therefore, if there exists only one plaintext block, then AESv3 right-zero-pads that block to be 16 bytes.
Privacy issues with key and IV re-use
Since the IV and key are both directly derived from the client key pair, the IV and key are reused until the application generates a new key pair. This only happens when the application restarts, such as when the user restarts the mobile device, the user switches to a different keyboard and back, or the keyboard app is evicted from memory. From our testing, we have observed the same key and IV in use for over 24 hours. There are various issues that arise from key and IV reuse.
Re-using the same IV and key means that the same inputs will encrypt to the same encrypted ciphertext. Additionally, due to the way the block cipher is constructed, if blocks in the same positions of the plaintexts are the same, they will encrypt to the same ciphertext blocks. As an example, if the second block of two plaintexts are the same, the second block of the corresponding ciphertexts will be the same.
Weakness in cipher mode
The electronic codebook (ECB) cipher mode is notorious for having the undesirable property that equivalent plaintext blocks encrypt to equivalent ciphertext blocks, allowing patterns in the plaintext to be revealed in the ciphertext (see Figure 2 for an illustration).

While BCTR mode used by Baidu does not as flagrantly reveal patterns to the same extent as ECB mode, there do exist circumstances in which patterns in the plaintext can still be revealed in the ciphertext. Specifically, there exist circumstances in which there exists a counter-like pattern in the plaintext which can be revealed by the ciphertext (see Figure 3 for an example). These circumstances are possible due to the fact that (IV + i ) is XORed with each plaintext block i and then encrypted, unlike ordinary CTR mode which encrypts (IV + i ) and XORs it with the plaintext. Thus, when using BCTR mode, if the plaintext exhibits similar counting patterns as (IV + i ), then for multiple blocks the value ((IV + i ) XOR plaintext block i ) may be equivalent and thus encrypt to an equivalent ciphertext.
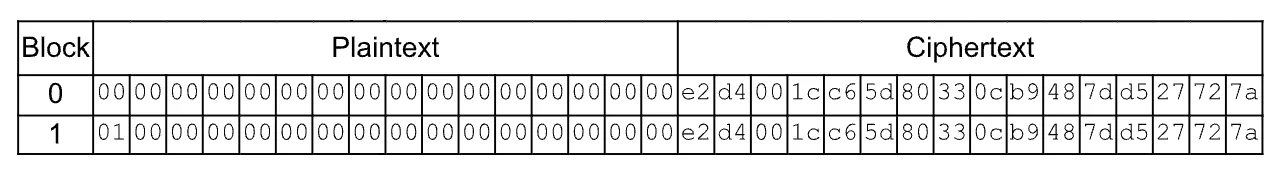
Other privacy and security weaknesses
There are other weaknesses in the custom encryption protocol designed by Baidu IME that are not consistent with the expected standards for a modern encryption protocol used by hundreds of millions of devices.
Forward secrecy issues with static Diffie-Hellman
The use of a pinned static server key means that the cipher is not forward secret , a property of other modern network encryption ciphers like TLS. If the server key is ever revealed, any past message where the shared secret was generated with that key can be successfully decrypted.
Lack of message integrity
There are no cryptographically secure message integrity checks, which means that a network attacker may freely modify the ciphertext. There is a CRC32 checksum calculated and included with the plaintext data, but a CRC32 checksum does not provide cryptographic integrity, as it is easy to generate CRC32 checksum collisions. Therefore, modifying the ciphertext may be possible. In combination with the issue concerning key and IV reuse, this protocol may be vulnerable to a swapped block attack.
Vulnerability in BAIDUv3.1 protocol
The BAIDUv3.1 protocol is weaker than the BAIDUv4.0 protocol and contains a critical vulnerability that allows an eavesdropper to decrypt any messages encrypted with it. The protocol in the versions of Baidu’s keyboard apps that we analyzed encrypts keystrokes using a modified version of AES which we call AESv2 , as we believe it to be the predecessor cipher to Baidu’s AESv3. When a keyboard app uses the BAIDUv3.1 protocol with the AESv2 cipher, we say that it uses the BAIDUv3.1+AESv2 scheme. Normally, AES when used with a 128-bit key performs 10 rounds of encryption on each block. However, we found that AESv2 uses only 9 rounds but is otherwise equivalent to AES encryption with a 128-bit key.
The BAIDUv3.1+AESv2 scheme encrypts keystrokes using AESv2 in the following manner. First, a key is derived according to a fixed function (see Figure 4). Note that the function takes no input nor references any external state and thus always generates the same static key k f = “ \xff\x9e\xd5H\x07Z\x10\xe4\xef\x06\xc7.\xa7\xa2\xf26 ”.
To encrypt a protobuf -serialized message, the BAIDUv3.1 protocol first snappy -compresses it, forming a compressed buffer. The 32-bit, little-endian length of this compressed message is then prepended to the compressed buffer, forming the plaintext. A randomly generated 128-bit key k m is used to encrypt the plaintext using AESv2 in ECB mode. The resulting ciphertext is stored in bytes 44 until the end of the final UDP payload. Key k f is used to encrypt k m using AESv2 in ECB mode. The resulting ciphertext is stored in bytes 28 until 44 of the final UDP payload.
We found that these encrypted protobuf serializations include our typed keystrokes as well as the name of the application into which we were typing them (see Figure 5).
A vulnerability exists in the BAIDUv3.1+AESv2 scheme that allows a network eavesdropper to decrypt the contents of these messages. Since AES is a symmetric encryption algorithm, the same key used to encrypt a message can also be used to decrypt it. Since k f is fixed, any network eavesdropper with knowledge of k f , such as from performing the same analysis of the app as we performed, can decrypt k m and thus can decrypt the plaintext contents of each message encrypted in the manner described above. As we found that users’ keystrokes and the names of the applications they were using were sent in these messages, a network eavesdropper who is eavesdropping on a user’s network traffic can observe what that user is typing and into which application they are typing it by taking advantage of this vulnerability.
We analyzed iFlytek (also called xùnfēi from the pinyin of 讯飞) IME on Android, iOS, and Windows. We found that iFlytek IME for Android includes a vulnerability which allows network eavesdroppers to recover the plaintext of insufficiently encrypted network transmissions, revealing sensitive information including what users have typed (see Table 4 for details).
Table 4: The versions of Xunfei IME analyzed.
The Android version of iFlytek IME encrypts the payload of each HTTP request sent to pinyin.voicecloud.cn with the following algorithm. Let s be the current time in seconds since the Unix epoch at the time of the request. For each request, an 8-byte encryption key is then derived by first performing the following computation:
The 8-byte key k is then derived from x as the lowest 8 ASCII-encoded digits of x , left-padded with leading zeroes if necessary, in big-endian order. In Python, the above can be summarized by the following expression:
The payload of the request is then padded with PKCS#7 padding and then encrypted with DES using key k in ECB mode. The value s is transmitted in the HTTP request in the clear as a GET parameter named “time”.
Since DES is a symmetric encryption algorithm, the same key used to encrypt a message can also be used to decrypt it. Since k can be easily derived from s and since s is transmitted in the clear in every HTTP request encrypted by k , any network eavesdropper can easily decrypt the contents of each HTTP request encrypted in the manner described above. (Since s is simply the time in single second resolution, it also stands to reason that a network eavesdropper would have general knowledge of s in any case.)
We found that users’ keystrokes were transmitted in a protobuf serialization and encrypted in this manner (see Figure 6). Therefore, a network eavesdropper who is eavesdropping on a user’s network traffic can observe what that user is typing by taking advantage of this vulnerability.
Finally, the DES encryption algorithm is an older encryption algorithm with known weaknesses, and the ECB block cipher mode is a simplistic and problematic cipher mode. The use of each of these technologies is problematic in itself and opens the Android version of iFlytek IME’s communications to additional attacks.
We analyzed Samsung Keyboard on Android as well as the versions of Sogou IME and Baidu IME that Samsung bundled with our test device, an SM-T220 tablet running ROM version T220CHN4CWF4. We found that Samsung Keyboard for Android and Samsung’s bundled version Baidu IME includes a vulnerability that allows network eavesdroppers to recover the plaintext of insufficiently encrypted network transmissions, revealing sensitive information including what users have typed (see Table 5 for details).
Table 5: The keyboards analyzed on our Samsung test device .
Samsung Keyboard (com.samsung.android.honeyboard)
We found that when using Samsung Keyboard on the Chinese edition of a Samsung device and when Pinyin is chosen as Samsung Keyboard’s input language, Samsung Keyboard transmits keystroke data to the following URL in the clear via HTTP POST:
http://shouji.sogou.com/web_ime/mobile_pb.php?durtot=339&h=8f2bc112-bbec-3f96-86ca-652e98316ad8&r=android_oem_samsung_open&v=8.13.10038.413173&s=&e=&i=&fc=0&base=dW5rbm93biswLjArMC4w&ext_ver=0
The keystroke data is contained in the request’s HTTP payload in a protobuf serialization (see Figure 7 below).
The device on which we were testing was fully updated on the date of testing (October 7, 2023) in that it had all OS updates applied and had all updates from the Samsung Galaxy Store applied.
Since Samsung Keyboard transmits keystroke data via plain, unencrypted HTTP and since there is no encryption applied at any other layer, a network eavesdropper who is monitoring a Samsung Keyboard user’s network traffic can easily observe that user’s keystrokes if that user is using the Chinese edition of the ROM with the Pinyin input language selected.
When using the global edition of the ROM or when using a non-Pinyin input language, we did not observe the Samsung keyboard communicating with cloud servers.
百度输入法 (“Baidu IME”, com.baidu.input)
We found that the version of Baidu IME bundled with our Samsung test device transmitted keystroke information via UDP packets to udpolimenew.baidu.com . This version of Baidu IME used the BAIDUv3.1 protocol that we describe in the Baidu section earlier but with a different cipher and compression algorithm as indicated in each transmission’s header. In the remainder of this section we explain how a network eavesdropper can, just like with AESv2, decrypt the contents of messages encrypted using a scheme we call BAIDUv3.1+AESv1 (see Table 6).
Table 6: Summary of ciphers used across different Baidu protocols.
Samsung’s bundled version of Baidu IME encrypts keystrokes using a modified version of AES which we name AESv1 , as we believe it to be the predecessor to Baidu’s AESv2. When encrypting, AESv1’s key expansion is like that of standard AES, except, on each but the first subkey, the order of the subkey’s bytes are additionally permuted. Furthermore, on the encryption of each block, the bytes of the block are additionally permuted in two locations, once near the beginning of the block’s encryption immediately after the block has been XOR’d by the first subkey and again near the end of the block’s encryption immediately before S-box substitution. Aside from complicating our analysis, we are not aware of these modifications altering the security properties of AES, and we have developed an implementation of this algorithm to both encrypt and decrypt messages given a plaintext or ciphertext and a key.
Samsung’s bundled version of Baidu IME encrypts keystrokes by applying AESv1 in electronic codebook ( ECB ) mode in the following manner. First, the app uses the fixed 128-bit key, k f = “ \xff\x9e\xd5H\x07Z\x10\xe4\xef\x06\xc7.\xa7\xa2\xf26 ”, to encrypt another, generated, key, k m . The fixed key k f is the same key the BAIDUv3.1 protocol uses for AESv2 (see Figure 4). The encryption of k m is stored in bytes 64 until 80 of each UDP packet’s payload. The key k m is then used to encrypt the remainder of a zlib-compressed message payload, which is stored at byte 80 until the end of the UDP payload. We found that the encrypted payload included, in a binary container format which we did not recognize, our typed keystrokes as well as the name of the application into which we were typing them (see Figure 8).
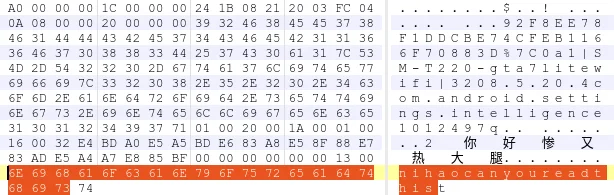
A vulnerability exists in the BAIDUv3.1+AESv1 scheme that allows a network eavesdropper to decrypt the contents of these messages. Since AES, including AESv1, is a symmetric encryption algorithm, the same key used to encrypt a message can also be used to decrypt it. Since k f is hard-coded, any network eavesdropper with knowledge of k f can decrypt k m and thus decrypt the plaintext contents of each message encrypted in the manner described above. As we found that users’ keystrokes and the names of the applications they were using were sent in these messages, a network eavesdropper who is eavesdropping on a user’s network traffic can observe what that user is typing and into which application they are typing it by taking advantage of this vulnerability.
Additionally, in the version of Baidu Input Method distributed by Samsung, we found that key k m was not securely generated using a secure pseudorandom number generator ( secure PRNG ). Instead, it was seeded using a custom-designed PRNG that we believe to have poor security properties, and, instead of using a high entropy seed, the PRNG generating k m was seeded using the message plaintext. However, even without these weaknesses in the generation of k m , the protocol is already completely insecure to network eavesdroppers as described in the previous paragraphs.
We analyzed the keyboards preinstalled on our Huawei Mate 50 Pro test device. We found no vulnerabilities in the manner of transmission of users’ keystrokes in the versions of Huawei’s keyboard apps that we analyzed (see Table 7 for details). Specifically, Huawei used TLS to encrypt keystrokes in each version that we analyzed.
Table 7: The versions of the Huawei keyboard apps analyzed.
We analyzed the keyboards preinstalled on our Xiaomi Mi 11 test device. We found that they all include vulnerabilities that allow network eavesdroppers to decrypt network transmissions from the keyboards (see Table 8 for details). This means that network eavesdroppers can obtain sensitive personal information, including what users have typed.
Table 8: The versions of the Xiaomi keyboard apps analyzed.
In this section we detail vulnerabilities in three different keyboard apps included with MIUI 14.0.31 in which users’ keystrokes can be, if necessary, decrypted, and read by network eavesdroppers.
百度输入法小米版 (“Baidu IME Xiaomi Version”, com.baidu.input_mi)
We found that Xiaomi’s Baidu-based keyboard app encrypts keystrokes using the BAIDUv3.1+AESv2 scheme which we detailed previously. When the app’s messages are decrypted and deserialized, we found that they include our typed keystrokes as well as the name of the application into which we were typing them (see Figure 9).
Like we explained previously, a vulnerability exists in the BAIDUv3.1+AESv2 scheme that allows a network eavesdropper to decrypt the contents of these messages. As we found that users’ keystrokes and the names of the applications they were using were sent in these messages, a network eavesdropper who is eavesdropping on a user’s network traffic can observe what that user is typing and into which application they are typing it by taking advantage of this vulnerability.
搜狗输入法小米版 (“Sogou IME Xiaomi Version”, com.sohu.inputmethod.sogou.xiaomi)
The Sogou-based keyboard app is subject to a vulnerability which we have already publicly disclosed in Sogou IME (搜狗输入法) in which a network eavesdropper can decrypt and recover users’ transmitted keystrokes. Please see the corresponding details in this report for full details. Tencent responded by securing Sogou IME transmissions using TLS, but we found that Xiaomi’s Sogou-based keyboard had not been fixed.
讯飞输入法小米版 (“iFlytek IME Xiaomi Version”, com.iflytek.inputmethod.miui)
Similar to iFlytek’s own IME for Android, we found that Xiaomi’s iFlytek keyboard app used the same faulty encryption. We found that users’ keystrokes were sent to pinyin.voicecloud.cn and encrypted in this manner.
{“p”:{“m”:53,”f”:0,”l”:0},”i”:”nihaoniba”}
Therefore, a network eavesdropper who is eavesdropping on a user’s network traffic can observe what that user is typing by taking advantage of this vulnerability (see Figure 10).
We analyzed the keyboard apps preinstalled on our OPPO OnePlus Ace test device. We found that they all include vulnerabilities that allow network eavesdroppers to decrypt network transmissions from the keyboards (see Table 9 for details). This means that network eavesdroppers can obtain sensitive personal information, including what users have typed.
Table 9: The versions of the OPPO keyboard apps analyzed.
In this section we detail vulnerabilities in two different keyboard apps included with MIUI 14.0.31 in which users’ keystrokes can be, if necessary, decrypted, and read by network eavesdroppers.
百度输入法定制版 (“Baidu IME Custom Version”, com.baidu.input_oppo)
We found that OPPO’s Baidu-based keyboard app encrypts keystrokes using the BAIDUv3.1+AESv2 scheme which we detailed previously. When the app’s messages are decrypted and deserialized, we found that they include our typed keystrokes as well as the name of the application into which we were typing them (see Figure 11).
搜狗输入法定制版 (“Sogou IME Custom Version”, com.sohu.inputmethod.sogouoem)
The Sogou-based keyboard app is subject to a vulnerability which we have already publicly disclosed in Sogou IME (搜狗输入法) in which a network eavesdropper can decrypt and recover users’ transmitted keystrokes. Please see the corresponding details in this report for full details. Tencent responded by securing Sogou IME transmissions using TLS, but we found that OPPO’s Sogou-based keyboard had not been fixed.
We analyzed the keyboard apps preinstalled on our Vivo Y78+ test device. We found that the Sogou-based one includes vulnerabilities that allow network eavesdroppers to decrypt network transmissions from the keyboards (see Table 10 for details). This means that network eavesdroppers can obtain sensitive personal information, including what users have typed.
Table 10: The versions of the Vivo keyboard apps analyzed.
The Sogou-based keyboard app is subject to a vulnerability which we have already publicly disclosed in Sogou IME (搜狗输入法) in which a network eavesdropper can decrypt and recover users’ transmitted keystrokes. Please see the corresponding details in this report for full details. Tencent responded by securing Sogou IME transmissions using TLS, but we found that Vivo’s Sogou-based keyboard had not been fixed.
We analyzed the keyboard apps preinstalled on our Honor Play7T test device. We found that the Baidu-based one includes vulnerabilities that allow network eavesdroppers to decrypt network transmissions from the keyboards (see Table 11 for details). This means that network eavesdroppers can obtain sensitive personal information, including what users have typed.
Table 11: The versions of the Honor keyboard apps analyzed.
We found that Honor’s Baidu-based keyboard app encrypts keystrokes using the BAIDUv3.1+AESv2 scheme which we detailed previously. When the app’s messages are decrypted and deserialized, we found that they include our typed keystrokes as well as the name of the application into which we were typing them (see Figure 12).
As of April 1, 2024, “Baidu IME Honor Version”, the default IME on the Honor device we tested, is still vulnerable to passive decryption. We also discovered that on our Play7T device, there was no way to update “Baidu IME Honor Version” through the device’s app store. In responding to our disclosures, Honor asked us to disclose to Baidu and that it was Baidu’s responsibility to patch this issue.
Other affected keyboard apps
Given our limited resources to analyze apps, we were not able to analyze every cloud-based keyboard app available. Nevertheless, given that these vulnerabilities appeared to affect APIs that were used by multiple apps, we wanted to approximate the total number of apps affected by these vulnerabilities.
We began by searching VirusTotal , a database of software and other files that have been uploaded for automated virus scanning, for Android apps which reference the string “get.sogou.com”, the API endpoint used by Sogou IME, as these apps may require additional investigation to determine whether they are vulnerable. Excluding apps that we analyzed above, this search yielded the following apps:
com.sohu.sohuvideo
com.tencent.docs
com.sogou.reader.free
com.sohu.inputmethod.sogou.samsung
com.sogou.text
com.sogou.novel
com.sogo.appmall
com.blank_app
com.sohu.inputmethod.sogou.nubia
com.sogou.androidtool
com.sohu.inputmethod.sogou.meizu
com.sohu.inputmethod.sogou.zte
sogou.mobile.explorer.hmct
sogou.mobile.explorer
com.sogou.translatorpen
com.sec.android.inputmethod.beta
com.sohu.inputmethod.sogou.meitu
com.sec.android.inputmethod
sogou.mobile.explorer.online
com.sohu.sohuvideo.meizu
com.sohu.inputmethod.sogou.oem
com.sogou.map.android.maps
sogou.llq.online
com.sohu.inputmethod.sogou.coolpad
com.sohu.inputmethod.sogou.chuizi
com.sogou.toptennews
com.sogou.recmaster
com.meizu.flyme.input
We have not analyzed these apps and thus cannot conclude that they are necessarily vulnerable, or even keyboard apps, but we provide this list to help reveal the possible scope of the vulnerabilities that we discovered. When we disclosed this list to Tencent, Tencent requested an additional three months to fix the vulnerabilities before we publicly disclosed this list, suggesting credence to the idea that apps in this list are largely vulnerable. Similarly, after excluding apps that we had already analyzed, the following are other Android apps which reference the strings “udpolimenew.baidu.com” or “udpolimeok.baidu.com”, the API endpoints used by Baidu Input Method:
- com.adamrocker.android.input.simeji
- com.facemoji.lite.xiaomi.gp
- com.facemoji.lite.xiaomi
- com.preff.kb.xm
- com.facemoji.lite.transsion
- com.txthinking.brook
- com.facemoji.lite.vivo
- com.baidu.input_huawei
- com.baidu.input_vivo
- com.baidu.input_oem
- com.preff.kb.op
- com.txthinking.shiliew
- mark.via.gp
- com.qinggan.app.windlink
- com.baidu.mapauto
These findings suggest that a large ecosystem of apps may be affected by the vulnerabilities that we discovered in this report.
Coordinated disclosure
We reported the vulnerabilities that we discovered to each vendor in accordance with our vulnerability disclosure policy . All companies except Baidu, Vivo, and Xiaomi responded to our disclosures. Baidu fixed the most serious issues we reported to them shortly after our disclosure, but Baidu has yet to fix all issues that we reported to them. The mobile device manufacturers whose preinstalled keyboard apps we analyzed fixed issues in their apps except for their Baidu apps, which either only had the most serious issues addressed or, in the case of Honor, did not address any issues (see Table 12 for details). Regarding QQ Pinyin, Tencent indicated that “with the exception of end-of-life products, we aim to finalize the upgrade for all active products to transmit EncryptWall requests via HTTPS by the conclusion of Q1 [2024]”, but, as of April 1, 2024, we have not seen any fixes to this product. Tencent may consider QQ Pinyin end-of-life as it has not received updates since 2020, although we note that it is still available for download. For timelines and full correspondence of our disclosures to each vendor, please see the Appendix .
* Default keyboard app on our test device. † Both QQ Pinyin and Sogou IME are developed by Tencent; in this report we analyzed QQ Pinyin and found the same issues as we had in Sogou IME .
Table 12: Status of vulnerabilities after disclosure as of April 1, 2024.
To summarize, we no longer have working exploits against any products except Honor’s keyboard app and Tencent’s QQ Pinyin. Baidu’s keyboard apps on other devices continue to contain weaknesses in their cryptography which we are unable to exploit at this time to fully decrypt users’ keystrokes in transit.
Barriers to users receiving security updates
Users can receive updates to their keyboard apps on their phones’ app stores, and such updates typically install in the background without user intervention. In our testing, updating keyboard apps was typically performed without friction. However, in some cases, a user may need to also ensure that they have fully updated their operating system before they will receive the fixes to our reported vulnerabilities for their keyboard app through the app store. In the case of the Honor device we tested, there was no update mechanism for the default keyboard used by the operating system through the app store. Honor devices bundled with a vulnerable version of the keyboard will remain vulnerable to passive decryption. In the case of the Samsung Galaxy Store, we found that on our device a user must sign in with a Samsung account before receiving security updates to their keyboard app. In the case the user does not have a Samsung account, then they must create one. We believe that installing important security updates should be frictionless, and we recommend that Samsung and app stores in general not require the registration of a user account before receiving important security updates.
We also learned from communication with Samsung’s security team that our test device had been artificially stuck on an older version of Baidu IME (version 8.5.20.4) compared to the one in the Samsung Galaxy Store. This is because, although the test device was using a Chinese ROM, we were prevented from receiving updates to Baidu IME because the app was geographically unavailable in Canada, where we were testing from. Samsung addressed this issue by adding Baidu’s keyboard app to the global market. Generally speaking, we recommend that Samsung and other app stores do not geoblock security updates to apps that are already installed.
Language barriers in responsible disclosures
We suspect that a language barrier may have prevented iFlytek from responding to our initial disclosure in English. After we did not receive a response for one month, we re-sent the same disclosure e-mail, but with a subject line and one-sentence summary in simplified Chinese. iFlytek responded within three days of this second email and promptly fixed the issues we noted. All future disclosure emails to the Chinese mobile device manufacturers were then written with Chinese subject lines and a short summary in Chinese. Though obvious in hindsight, we encourage security researchers to consider if the company to which they are disclosing uses a different language than the researcher. We suggest submitting vulnerability disclosures, at the very least, with short summaries and email subject lines in the official language of the company’s jurisdiction to prevent similar delays as we may have encountered in disclosure timelines.
Limitations
In this report we detail vulnerabilities relating to the security of the transmission of users’ keystrokes in multiple keyboard apps. In this work we did not perform a full audit of any app or make any attempt to exhaustively find every security vulnerability in any software. Our report concerns analyzing keyboard apps for a class of vulnerabilities that we discovered, and the absence of our reporting of other vulnerabilities should not be considered evidence of their absence.
In this section we discuss the impact of the vulnerabilities that we found, speculate as to the factors that gave rise to them, and conclude by introducing possible ways to systemically prevent such vulnerabilities from arising in the future.
Impact of these vulnerabilities
The scope of these severe vulnerabilities cannot be overstated: until this and our previous Sogou report , the majority of Chinese mobile users’ keystrokes were decryptable by network adversaries. The keyboards we studied comprise over 95% of the third-party IME market share, which is estimated to be over 780 million users by marketing agencies. In addition, the three phone manufacturers which pre-installed and by default used vulnerable keyboard apps comprise nearly 50% of China’s smartphone market.
The vulnerabilities that we discovered would be inevitably discovered by anyone who thinks to look for them. Furthermore, the vulnerabilities do not require technological sophistication to exploit. With the exception of the vulnerability affecting many Sogou-based keyboard apps that we previously discovered , all of the vulnerabilities that we covered in this report can be exploited entirely passively without sending any additional network traffic. This also means any existing logs of network data sent by these keyboards can be decrypted in the future. As such, we might wonder, are these vulnerabilities actively under mass exploitation?
While many governments may possess sophisticated mass surveillance capabilities, the Snowden revelations gave us unique insight into the capabilities of the United States National Security Agency (NSA) and more broadly the Five Eyes . The revelations disclosed , among other programs, an NSA program called XKEYSCORE for collecting and searching Internet data in realtime across the globe (see Figure 13). Leaked slides describing the program specifically reveal only a few examples of XKEYSCORE plugins. However, one was a plugin that was written by a Five Eyes team to take advantage of vulnerabilities in the cryptography of Chinese-developed UC Browser to enable the Five Eyes to collect device identifiers, SIM card identifiers, and account information pertaining to UC Browser users (see Figure 14 for an illustration).
The similarity of the vulnerability exploited by this XKEYSCORE plugin and the vulnerabilities described in this report are uncanny, as they are all vulnerabilities in the encryption of sensitive data transmissions in software predominantly used by Chinese users. Given the known capabilities of XKEYSCORE, we surmise that the Five Eyes would have the capability to globally surveil the keystrokes of all of the keyboard apps that we analyzed with the exception of Sogou and the apps licensing its software. This single exception exists because Sogou cannot be monitored passively and would require sending packets to Sogou servers. Such communications would be measurable at Sogou’s servers and at other vantage points, potentially revealing the Five Eyes’s target(s) of surveillance to Sogou or Chinese network operators. Therefore, targets of outdated Sogou software would be undesirable victims of mass surveillance, even if such non-passive measurements were within the known capabilities of XKEYSCORE or other Five Eyes programs.
Given the enormous intelligence value of knowing what users are typing, we can conclude that not only do the NSA and more broadly the Five Eyes have the capabilities to mass exploit the vulnerabilities we found but also the strong motivation to exploit them. If the Five Eyes’ capabilities are an accurate reflection of the capabilities and motivations of other governments, then we can assume that many other governments are also capable and motivated to mass exploit these vulnerabilities. The only remaining question is whether any government had knowledge of these vulnerabilities. If they did not have such knowledge before our original report analyzing Sogou, they may have acquired after it in the same way that our original research inspired us to look at similar keyboard apps for analogous vulnerabilities. Unfortunately, short of future government leaks, we may never know if or to what extent any state actors mass exploited these vulnerabilities.
Even though we disclosed the vulnerabilities to vendors, some vendors failed to fix the issues that we reported. Moreover, users of devices which are out of support or that otherwise no longer receive updates may continue to be vulnerable. As such, many users of these apps may continue to be under mass surveillance for the foreseeable future.
How did these vulnerabilities arise
We analyzed a broad sample of Chinese keyboard apps, finding that they are almost universally vulnerable to having their users’ keystrokes being decrypted by network eavesdroppers. Yet there is no common library or a single implementation flaw responsible for these vulnerabilities. While some of the keyboard apps did license their code from other companies, our overall findings can only be explained by a large number of developers independently making the same kind of mistake. As such, we might ask, how could such a large number of independent developers almost universally make such a critical mistake?
One attempt to answer this question is to suggest that these were not mistakes at all but deliberate backdoors introduced by the Chinese government. However, this hypothesis is rather weak. First, user keystroke data is already being sent to servers within Chinese legal jurisdiction, and so the Chinese government would have access to such data anyways. Second, the vulnerabilities that we found give the ability not just to the Chinese government to decrypt transmitted keystrokes but to any other actor as well. In an ideal backdoor, the Chinese government would want the desirable property that only they have access to the backdoor. Finally, the Chinese government has made strides to study and improve the data security of apps developed and used in China, attempting to prevent and fix the very sort of vulnerabilities which we discovered. For instance, a 2020 report from CNCERT/CC found that 60 percent of the 50 banking applications that they investigated did not encrypt any user data transmitted over the network, among a litany of other common security issues.
Were Chinese app developers skeptical of using cryptographic standards perceived as “Western”? Countries such as China and Russia have their own encryption standards and ciphers . To our knowledge none of the faulty encryption implementations that we analyzed adhered to any sort of known standard in any country, and each appeared to be home-rolled ciphers. However, it is possible that Asian developers are less inclined to use encryption standards that they fear may contain backdoors such as the potential Dual_EC_DRBG backdoor .
Perhaps Chinese app developers could be skeptical of standards such as SSL/TLS as well. The TLS ecosystem has also only become nearly-universal in the past decade . Especially before broad oversight of certificate authorities became commonplace, there were many valid criticisms of the SSL/TLS ecosystem. In 2011, digital rights organizations EFF and Access Now were both concerned about the certificate authority (CA) infrastructure underpinning SSL/TLS transport encryption. Even today, the vast majority of root certificates trusted by major OSes and browsers are operated by certificate authorities based in the Global North. We also note that all of the IMEs containing vulnerabilities were first released before 2013 and likely had a need for secure network transmission before SSL/TLS became the de-facto standard for strong transport encryption.
Still, it has been a decade since the Snowden leaks demonstrated the global, urgent, and practical need for strong encryption of data-in-transit in 2013, and the TLS ecosystem has largely stabilized, with CA root lists of many major browsers and OSes controlled by voting bodies and certificate transparency deployed. As of 2024, almost 95% of web traffic from users of Firefox in the United States is traveling over HTTPS . In addition, the speed in which both iFlytek and Sogou switched to TLS demonstrates that making the change to standard TLS is not necessarily a time or resource issue. Even if skepticism towards SSL/TLS explains the reluctance to adopt it in the early 2010s, we are not sure why there is much more inertia in the Chinese Internet ecosystem against making the switch to TLS.
Finally, mobile devices and other operating systems are still incapable of guaranteeing the security of data under transmission, despite iOS and Android having introduced restrictions into their APIs. For instance, iOS 9 implemented App Transport Security , a policy placing restrictions on the ability to transmit data without TLS. However, there are two limitations of this technology. First, an app can specify exceptions to this policy in its Info.plist resource. Second, the policy affects high level APIs and leaves communications over lower level socket-based APIs unregulated. Similar to iOS, Android 9 disables cleartext traffic using certain high level APIs by default , but an app may exclude specific domains or avoid the policy by using lower level APIs.
Can we systemically address these vulnerabilities?
Individually analyzing apps for this class of vulnerabilities and individually reporting issues discovered is limited in the scale of apps that it can fix. First, while we can attempt to manually analyze some of the most popular keyboard apps, we will never be able to analyze every app at large. Second, we might not be able to predict which apps to look at in the first place. For instance, before we analyzed Sogou and the keyboard apps featured in this report, we never would have expected that their network transmissions would be so easily vulnerable to interception. In light of the limitations of the methods that we employed in this report, in the remainder of this section we discuss possibilities for how we might systematically or wholesale address apps which transmit sensitive data over networks without sufficient encryption.
By security researchers paying more attention to the Chinese Internet
There appears to be a general failure of researchers to analyze Chinese apps and the Chinese Internet ecosystem at large, despite its size and influence. The Google Play Store and Apple App Store ecosystems, for instance, are commonly studied by privacy researchers, but many Chinese app stores are overlooked, despite that many popular Chinese apps have more users than their counterparts on the Google Play Store. While the vulnerabilities that we discovered were not all trivial to find and many took substantial analysis to attack, most would have been inevitably discovered by any researcher analyzing these apps for data security. A researcher studying network traffic from users of Chinese devices could also have identified strange, non-standard traffic.
By using app store enforcement
One might call on app stores to enforce the use of sufficient encryption to protect sensitive data in transit. App stores already have a number of rules that they enforce through a combination of automated and manual review. Calling on app stores to enforce sufficient encryption of in-transit sensitive data is tempting given the resources of the companies operating the app stores. However, failing any other innovation, the same scaling issues that apply to other researchers studying these apps will apply to those working for these companies.
By using device permission models
On Android devices, installing any keyboard, regardless of whether or how it communicates with servers over the Internet, brings up a pop-up with the following text:
This input method may be able to collect all the text you type, including personal data like passwords and credit card numbers.
The wording of these warning messages is overbroad and does not necessarily help users distinguish between keyboards that transmit keystrokes over the network, keyboards that transmit keystrokes insecurely (using something other than standard TLS) over the network, and keyboards that do not transmit any data at all.
iOS devices, on the other hand, sandbox their keyboards by default. There is a “Full Access” or “open access” permission that must be explicitly granted to keyboards before they have network access, among other privileges. Without this permission, third-party keyboards cannot transmit network data . We recommend Android also adopt a more fine-grained permission model for keyboards.
Furthermore, the vulnerable apps that we studied transmit data using low level socket APIs versus higher level APIs that require the usage of TLS or HTTPS. One might desire that separate system calls be designed for TLS or HTTPS traffic in addition to the lower level socket system calls so that devices could implement an UNSAFE_INTERNET permission that would be required for apps to use the lower level system calls while still allowing TLS-encrypted traffic for apps that do not have this permission.
While this approach may have some merit, it also has certain drawbacks. It makes sense for situations where apps are untrustworthy and the operating system is completely trustworthy, but there are common situations where the operating system could be not as or even less trustworthy than apps that it is running. One common case would be a user who is running an up-to-date app on an out of date operating system, possibly because the user’s device is no longer receiving operating system updates. In such a case, the app’s implementation of TLS is more likely to be secure than that of the operating system. Furthermore, a user’s operating system may be compromised by malware or otherwise be untrustworthy in itself. Introducing a TLS system call would centralize the encryption of all sensitive data and grant the operating system easy visibility into all unencrypted data. In any case, innovating in areas of encryption is an important right of application developers, and it may not make sense to stifle apps like Signal because of their use of end-to-end or other novel encryption by requiring them to obtain an UNSAFE_INTERNET permission.
One might alternatively desire for apps at large to not be able to access the Internet at all. Instead of an UNSAFE_INTERNET permission, what about introducing an INTERNET permission to govern all Internet socket access, similar to the “Full Access” permission which iOS already applies to keyboard apps? Android devices in fact already have such a permission that apps must request to use Internet (AF_INET) sockets, but it is not a permission that is exposed to ordinary users either in the Google Play Store or through any stock Android user interface, and it is automatically granted when installing an app. Unfortunately, given all of the interprocess communication (IPC) vehicles on modern smart devices, restricting Internet socket access may not guarantee that the app could not communicate over the Internet (e.g., through Google Play services). GrapheneOS , an open source Android-based operating system, implements a NETWORK permission. However, denying this permission can lead to surprising results where apps can still communicate with the Internet via IPC with other apps. As such, we recommend that both the developers of Android and iOS work toward a meaningful INTERNET permission that would adequately inform users of whether an app communicates over the Internet.
By international standards bodies better engaging with Chinese developers
We encourage International standards bodies like the IETF to continue to engage and outreach Chinese Internet companies and engineers in good faith to further reduce friction in cross-linguistic knowledge transfer. The presence of these similar but independent vulnerabilities demonstrate that there is a friction in the transfer and implementation of knowledge between the English-speaking cryptography community and the Chinese cryptography community. For instance, Schneier’s Law or the oft-repeated mantra “don’t roll your own crypto” may be common knowledge to cryptographers trained in English, but perhaps lost in translation. A lag across linguistic boundaries means that general information like the recent stabilization of TLS and webPKI infrastructure may travel more slowly, and updating encryption software to reflect new information may lag even further behind. One other possible example of this phenomenon is that, according to Firefox Telemetry , up until 2020, the Japanese Internet ecosystem also significantly lagged behind the global average in HTTPS adoption.
Although protocols put out by IETF and other International standards bodies can be far from bulletproof , these bodies can still help facilitate international communication about the current state-of-the-art in protocol encryption. The burden of cross-linguistic and cross-cultural exchange on technical standards falls on global standards bodies. Western media outlets and researchers tend to uniformly attribute the actions and participation of private Chinese companies within standards bodies to government actors seeking sovereignty over Internet standards. While skepticism may be warranted in certain cases , there is also research that challenges a simplistic and overbroad narrative. As a single data point, we note that we did not find these issues in Huawei’s keyboards, whose employees are often noted as especially active participants in IETF standard-setting.
By using automated static or dynamic analysis
There has been a failure of automated tools to detect insecure traffic at large. Longitudinal TLS telemetry has largely been focused on web-based perspectives (i.e., how many domains support TLS or how many web connections are encrypted by TLS ?), and the mobile perspective is often overlooked, despite the increasing dominance of mobile traffic globally. Although there are some research projects that survey TLS usage in Android mobile apps at scale, there is no public longitudinal data from these projects (i.e., they are run as one-off studies), and many focus on the Google Play’s Android ecosystem, thereby excluding the Chinese mobile Internet. There is perhaps a need for public longitudinal TLS telemetry for popular mobile applications globally, via automated static or dynamic analysis at scale.
By using attestations in app stores
Another way for users to gain visibility into the security and privacy properties of their apps is through the use of developer attestations, such as the ones that appear in data safety sections in many popular app stores. Both the Apple App Store and the Google Play Store collect and display such attestations to varying extents, including attestations as to what data an app collects (if any) and with whom it is shared (if anyone). Additionally, the Play Store allows developers the opportunity to attest to performing “encryption in transit” (see Figure 15 for an example). These attestations allow users to clearly see what security and privacy properties an app’s developer claims it to have and, like privacy policies, they provide means of redress if violated.
We wanted to evaluate whether the apps that we analyzed lived up to their attestations concerning their encryption in the app stores in which they are available. Among the apps that we analyzed, only Baidu IME was available in the Play Store. At the time of this writing, it does not attest to its data being encrypted in transit. Although other apps that we analyzed were available in Apple’s App Store, to our knowledge, this store does not display an attestation for whether the app encrypts data in transit. As such, across both the Google Play and the Apple App stores, attestations were insufficient for compelling the keyboard apps’ developers to implement proper encryption or in providing users any opportunity for redress.
In light of the above findings, we believe that users would benefit from the following recommendations: (1) that app store operators require developers to attest to whether or not an app encrypts data in transit, (2) that app store operators display not only when developers attest to all data being encrypted in transit but also display a warning when they fail to, and (3) that app store operators require apps in certain sensitive categories, such as keyboard apps, to either positively attest to encrypting all data in transit or to attest to not transmitting any data at all.
Since most of the apps that we found perform some type of encryption, even if it were wholly inadequate, one might wonder if attesting that data is merely “encrypted” is enough, since the data arguably did have some manner of encryption applied to it during transit. The Play Store provides some guidance on this topic. Under the question — “How should I encrypt data in transit?” — the documentation notes : “You should follow best industry standards to safely encrypt your app’s data in transit. Common encryption protocols include TLS (Transport Layer Security) and HTTPS.”
Another issue with attestations is that they provide no guarantee that an app behaves as its developers attest, as developers can, after all, make false attestations. While we wish that attestations could guarantee that an app sufficiently implements proper cryptography to the same extent that a permission system can guarantee an app does not use a microphone, false attestations provide an opportunity for redress. For instance, apps which are found to violate attestations would be subject to removal from app stores. Furthermore, apps which violate attestations could be subject to fines by regulatory bodies such as the FTC. Finally, apps which violate the attestation could be liable to civil suits.
While the apps we analyzed were predominantly available from Chinese app stores, we equally recommend that Chinese app stores adopt these recommendations in addition to the Apple App Store and the Google Play Store. Moreover, while this report focuses on the problem of poor encryption practices as it applies to Chinese apps, the problem to varying extents applies to apps of all other provenances.
Summary of recommendations
We conclude our report by summarizing our recommendations to multiple stakeholders.
Recommendations to security researchers
- Researchers should analyze more apps from the East Asian app ecosystem and from other popular ecosystems which may be outside of their own locale.
- Researchers should develop better static and dynamic analysis techniques to recognize the types of vulnerabilities that we discovered in this report at scale.
- Researchers submitting vulnerability disclosures to a company should include short summaries and email subject lines in the official language of the company’s jurisdiction.
Recommendations to international standards bodies
- International standards bodies should continue to engage with security engineers from Chinese Internet companies.
Recommendations to app store operators
- App stores should not require account registration as a condition to receive security updates.
- App stores should not geoblock security updates.
- App stores should allow developers to attest to all data being transmitted with encryption, similar to the ability in the Google Play Store.
- App stores should display not only when developers attest to all data being encrypted in transit but also display a warning when they fail to.
- App stores should require apps in certain sensitive categories, such as keyboard apps, to either positively attest to encrypting all data in transit or to attest to not transmitting any data at all.
Recommendations to keyboard app developers
- Use well-tested and standard encryption protocols, like TLS or QUIC.
- Make every attempt to provide features on-device without requiring transmitting sensitive data to cloud servers.
Recommendations to mobile operating system developers
- Android should implement sandboxing by default for keyboard apps, similar to iOS, that prevents a keyboard from transmitting network traffic among other activities until a user grants the app full access.
- The developers of Android and iOS should work toward a meaningful INTERNET permission that would adequately inform users of whether any app communicates over the Internet.
Recommendations to device manufacturers
- Conduct security audits of third-party keyboards that you intend to pre-install by default on your operating systems.
Recommendations to users
- Users of Honor’s pre-installed keyboard or users of QQ pinyin should switch keyboards immediately.
- Users of any Sogou, Baidu, or iFlytek keyboard, including the versions that are bundled or pre-installed on operating systems, should ensure their keyboards and operating systems are up-to-date.
- Users of any Baidu IME keyboard should consider switching to a different keyboard or disabling the “cloud-based” feature.
- Users with privacy concerns should not enable “cloud-based” features on their keyboards or IMEs or should switch to a keyboard that does not offer “cloud-based” prediction.
- iOS users with privacy concerns should not enable “Full Access” for their keyboards or IMEs.
Acknowledgments
We would like to thank Jedidiah Crandall, Jakub Dalek, Pellaeon Lin, and Sarah Scheffler for their guidance and review of this report. Research for this project was supervised by Ron Deibert.
Known affected software
We recommend that all users keep their operating systems and apps, including keyboard apps, up to date. If you use any of the following software, we especially recommend you update to the most recent version of your OS and application. As of April 1, 2024, the following software has fixes available:
Separately installed, third-party keyboards
- Sogou IME / 搜狗输入法 for Android and Windows
- Baidu IME / 百度输入法 for Windows (this software has only been partially fixed, see below)
- iFlytek IME / 讯飞输入法 for Android
Pre-installed on Samsung devices with Chinese edition ROM
- Samsung Keyboard
- Baidu IME / 百度输入法
Pre-installed on Xiaomi devices with Chinese edition ROM
- Sogou IME Xiaomi Version / 搜狗输入法小米版
- iFlytek IME Xiaomi Version / 讯飞输入法小米版
Pre-installed on OPPO devices with Chinese edition ROM
- Sogou IME Custom Version / 搜狗输入法定制版
Pre-installed on Vivo devices with Chinese edition ROM
The following software does not use TLS and may still contain weaknesses:
- Baidu IME / 百度输入法 for Android, Windows, and iOS
- Baidu IME Xiaomi Version / 百度输入法小米版
- Baidu IME Custom Version / 百度输入法定制版
The following software has not been fixed and is easily exploitable, and we suggest that users switch to another keyboard entirely:
- QQ Pinyin IME / QQ拼音输入法 for Android and Windows
Pre-installed on Honor devices with Chinese edition ROM
- Baidu IME Honor Version / 百度输入法荣耀版
Disclosure timelines
We sent the following via email:
To: [email protected], [email protected]
Subject: Security issue in Baidu Input Method
To Whom It May Concern:
The Citizen Lab is an academic research group based at the Munk School of Global Affairs & Public Policy at the University of Toronto in Toronto, Canada.
We analyzed Baidu Input Method as part of our ongoing work analyzing popular mobile and desktop apps for security and privacy issues. We found that Baidu Input Method for Windows includes a vulnerability which allows network eavesdroppers to decrypt network transmissions. This means third parties can obtain sensitive personal information including what users have typed. We also found privacy and security weaknesses in the encryption used by the Android and iOS versions of Baidu Input Method. To address these issues, we suggest using HTTPS or TLS rather than custom-designed network protocols. For further details, please see the attached document .
The Citizen Lab is committed to research transparency and will publish details regarding the security vulnerabilities it discovers in the context of its research activities, absent exceptional circumstances, on its website: https://citizenlab.ca/ .
If no response is received to this disclosure, the Citizen Lab will publish details regarding the security vulnerability on its website after 15 calendar days from the date of this communication. In other words, where there is no response from you, Citizen Lab will publish details regarding the vulnerability after October 18 2023.
If a substantive response is received (which excludes, for example, an auto reply) to this disclosure within 15 calendar days from the date of this communication, the Citizen Lab will provide you with 45 calendar days from the date of this communication to fix (whether in whole or in part) the vulnerability before publicly disclosing the issue. In other words, where we do receive a substantive response from you, the Citizen Lab will publish details regarding the vulnerability after November 17 2023.
We reserve the right to publish details regarding the vulnerability to the general public before the expiry of the 45 calendar days set out above in the following situations: (1) you have disclosed the vulnerability to the general public, (2) you have patched the vulnerability, (3) you have taken the position that there is no security vulnerability, or (4) the Citizen Lab observes the vulnerability is under active exploitation.
All communications associated with this disclosure may be included in the Citizen Lab’s public disclosure of this vulnerability.
Please communicate what steps you will take to address the vulnerability that we have described, and please provide the timeline you decide upon for the implementation of fixes.
Finally, upon implementation of any fixes, we ask that you communicate the full extent of the vulnerability to the Citizen Lab.
Should you have any questions about our findings please let us know. We can be reached at this email address: [email protected].
The Citizen Lab
Subject: Security issues in Baidu Input Method / 百度输入法高危漏洞
多伦多大学的研究人员发现许多手机预装的百度输入法存在高危漏洞,让网络攻击者可以直接看到用户输入的内容。同时也发现百度输入法的安卓版、iOS版、和Windows版存在另外与安全相关的问题,建议切换到TLS。本文用英文解释了研究人员发现漏洞的细节。
We analyzed Baidu Input Method as part of our ongoing work analyzing popular mobile and desktop apps for security and privacy issues. We found multiple third-party apps using the Baidu Input Method API include a vulnerability which allows network eavesdroppers to decrypt network transmissions. This means third parties can obtain sensitive personal information including what users have typed. We also found privacy and security weaknesses in the encryption used by the Windows, Android, and iOS versions of Baidu Input Method. To address these issues, we suggest using HTTPS or TLS rather than custom-designed network protocols. For further details, please see the attached document.
If no response is received to this disclosure, the Citizen Lab will publish details regarding the security vulnerability on its website after 15 calendar days from the date of this communication. In other words, where there is no response from you, Citizen Lab will publish details regarding the vulnerability after December 7 2023.
If a substantive response is received (which excludes, for example, an auto reply) to this disclosure within 15 calendar days from the date of this communication, the Citizen Lab will provide you with 45 calendar days from the date of this communication to fix (whether in whole or in part) the vulnerability before publicly disclosing the issue. In other words, where we do receive a substantive response from you, the Citizen Lab will publish details regarding the vulnerability after January 6 2024.
Subject: Security issues in Honor keyboard / 荣耀百度输入法高危漏洞
总结:多伦多大学的研究人员发现荣耀预装的百度输入法使用的加密协议有高危漏洞,让网路攻击者可以直接看到用户输入的内容。本文用英文解释了研究人员发现高危漏洞的细节。
We analyzed Honor pre-installed keyboard apps as part of our ongoing work analyzing popular mobile and desktop apps for security and privacy issues. We found that the Baidu-based one includes vulnerabilities that allow network eavesdroppers to decrypt network transmissions. This means third parties can obtain sensitive personal information including what users have typed. To address these issues, we suggest using HTTPS or TLS rather than custom-designed network protocols. For further details, please see the attached document.
If no response is received to this disclosure, the Citizen Lab will publish details regarding the security vulnerability on its website after 15 calendar days from the date of this communication. In other words, where there is no response from you, Citizen Lab will publish details regarding the vulnerability after December 7 2023
If a substantive response is received (which excludes, for example, an auto reply) to this disclosure within 15 calendar days from the date of this communication, the Citizen Lab will provide you with 45 calendar days from the date of this communication to fix (whether in whole or in part) the vulnerability before publicly disclosing the issue. In other words, where we do receive a substantive response from you, the Citizen Lab will publish details regarding the vulnerability after January 6 2024
We received the following email:
From: security <[email protected]>
Subject: 答复: Security issues in Honor keyboard / 荣耀百度输入法高危漏洞
DEAR Citizen Lab
Thank you very much for your concern about the security of Honor.
Honor always attaches great importance to the security of products and services. In order to respond to your security concerns immediately,
we have set up a professional vulnerability response team to serve you and set up an email ([email protected]) for quick response.
We are analyzing the impact of these security issue and will reach a conclusion as soon as possible.
Once again thank you for your concern about the security of Honor. If you have any questions, feel free to contact us through this email at any time.
Honor Security Response Center
Thank you very much for your report and your patience.
After our analysis. Baidu is a vendor of Honor, we relied on the vendor to patch this issue. We recommend that you submit this issue to Baidu and negotiate a disclosure plan with Baidu.
We sent the following email:
To: security <[email protected]>
Subject: Re: Security issues in Honor keyboard / 荣耀百度输入法高危漏洞
Dear Honor Security Response Center,
We have tried disclosing these issues to Baidu, but Baidu has been so far unresponsive to our disclosures.
We would like to note that our Honor Play7T device is still using an older version (v8.2.501.1) of the com.baidu.input_hihonor app. While the latest version of Baidu’s keyboard does not address all of the issues that we have reported, it does contain fixes for the most serious issues. Therefore, we recommend updating the com.baidu.input_hihonor app to the latest version of Baidu’s keyboard.
Subject: Security issue in Xunfei Input Method
We analyzed Xunfei Input Method on Android as part of our ongoing work analyzing popular mobile and desktop apps for security and privacy issues. We found that Xunfei Input Method for Android includes a vulnerability which allows network eavesdroppers to recover the plaintext of insufficiently encrypted network transmissions, revealing sensitive information including what users have typed.
For further details, please see the attached document.
If no response is received to this disclosure, the Citizen Lab will publish details regarding the security vulnerability on its website after 15 calendar days from the date of this communication. In other words, where there is no response from you, Citizen Lab will publish details regarding the vulnerability after September 23, 2023.
If a substantive response is received (which excludes, for example, an auto reply) to this disclosure within 15 calendar days from the date of this communication, the Citizen Lab will provide you with 45 calendar days from the date of this communication to fix (whether in whole or in part) the vulnerability before publicly disclosing the issue. In other words, where we do receive a substantive response from you, the Citizen Lab will publish details regarding the vulnerability after October 23, 2023.
We analyzed Xunfei Input Method on Android as part of our ongoing work analyzing popular mobile and desktop apps for security and privacy issues. We found that Xunfei Input Method for Android includes a vulnerability which allows network eavesdroppers to recover the plaintext of insufficiently encrypted network transmissions, revealing sensitive information including what users have typed. For further details, please see the attached document .
On September 8 2023 we attempted to disclose these vulnerabilities to [email protected], an email address listed on the product’s Web page, but we have not received a response. If you are not able to process vulnerability disclosures for this product, please ensure that this disclosure is delivered to someone who can.
If no response is received to this disclosure, the Citizen Lab will publish details regarding the security vulnerability on its website after 15 calendar days from the date of this communication. In other words, where there is no response from you, Citizen Lab will publish details regarding the vulnerability after October 10, 2023.
If a substantive response is received (which excludes, for example, an auto reply) to this disclosure within 15 calendar days from the date of this communication, the Citizen Lab will provide you with 45 calendar days from the date of this communication to fix (whether in whole or in part) the vulnerability before publicly disclosing the issue. In other words, where we do receive a substantive response from you, the Citizen Lab will publish details regarding the vulnerability after November 9, 2023.
To: [email protected], [email protected]
Subject: 讯飞输入法高危漏洞
多伦多大学的研究人员发现讯飞输入法使用的加密协议存在高危漏洞,让网路攻击者可以直接看到用户输入的内容。本文用英文解释了研究人员发现高危漏洞的细节。
On September 8 2023 we attempted to disclose these vulnerabilities to [email protected], and on September 25 2023 we attempted to disclose these vulnerabilities to [email protected]. We have not received a response to these emails. If you are not able to process vulnerability disclosures for this product, please ensure that this disclosure is delivered to someone who can.
Subject: Feedback on Xunfei Input Method issue
Hello The Citizen Lab,
Sorry for the delay.
Thank you for your detailed report and responsible disclosure on this issue.
We have analyzed your report and confirmed this is mainly due to server-side improper configuration in Xunfei Input Method that causes data transmission to use the HTTP protocol which can be eavesdropped. For the DES encryption algorithm used, is the result of considering the trade-off between performance and security under massive requests condition. As you mentioned in the mitigation part, data transmission is secure under the HTTPS protocol.
We implemented the fix on November 4th, that is, changing the improperly configured HTTP protocol on the server side to HTTPS, and it has taken effect.
November 4, 2023: Latest report received
November 4, 2023: Fix implemented
Because this is an improper configuration on the server side, the client will not be affected after the server is fixed. So there is no specific APK version extent of the vulnerability.
Best Regards,
Iflytek Team
Subject: Security issues in OPPO keyboards / OPPO预装的输入法高危漏洞
总结:多伦多大学的研究人员发现OPPO所有预装的中文输入法使用的加密协议有高危漏洞,让网路攻击者可以直接看到用户输入的内容。本文用英文解释了研究人员发现高危漏洞的细节。
We analyzed OPPO pre-installed keyboard apps as part of our ongoing work analyzing popular mobile and desktop apps for security and privacy issues. We found two that include vulnerabilities that allow network eavesdroppers to decrypt network transmissions. This means third parties can obtain sensitive personal information including what users have typed. To address these issues, we suggest using HTTPS or TLS rather than custom-designed network protocols. For further details, please see the attached document.
From: OPPO安全中心 <[email protected]>
Subject: 回复: Security issues in OPPO keyboards / OPPO预装的输入法高危漏洞
The Citizen Lab:
The email has been received. We will transfer it to the corresponding team for content analysis and confirmation. We will reply to the content in a timely manner. Thank you very much for your feedback!
Dear Citizen Lab Team,
Thank you once again for your attention and contribution to the safety of our products.
In response to the security vulnerability you reported, our OPPO Security Team has swiftly taken a series of measures. We particularly emphasize that for the Sogou Input Method OPPO Custom Edition, the related security issues have been comprehensively resolved and fixed on the latest ColorOS 14 system.
However, considering the wide range of our product models and numerous versions, to ensure that every device receives equal levels of security updates and maintenance, we need more time to thoroughly implement these fixes. Our team is working hard to ensure that all devices running older versions of ColorOS will also receive this important update as soon as possible.
In the meantime, the repair work for the Baidu Input Method OPPO Custom Edition is also proceeding intensely. Currently, this application is still in the internal testing phase. Our engineers are making every effort to ensure that it meets our high standards in terms of security and stability. Our goal is to complete the testing and release the update as soon as possible, ensuring the safety of all our users. We plan to comprehensively update and push both Baidu and Sogou Input Method OPPO Custom Editions by Q1 2024.
We understand that as a technology company, protecting the security and privacy of user data is our primary task. Therefore, OPPO is always committed to continuously improving the security performance of our products and services. We will continue to maintain close cooperation with security research institutions like Citizen Lab, working together to enhance the security standards of the entire industry.
Should you have any questions about our security measures or progress, please feel free to contact us.
Thank you again for your understanding, support, and cooperation.
OPPO Security Team
It has been over a week since our response. I am not sure if this has answered your questions. If you need further assistance, please contact me!
December 18 2023We sent the following via email:
Subject: Re: Security issues in OPPO keyboards / OPPO预装的输入法高危漏洞
Dear OPPO Security Team,
Thank you for your response. We are happy to hear that fixes are underway for your products. Our test device runs ColorOS 13.1, so we are currently unable to test the fix for Sogou Input Method OPPO Custom Edition for ColorOS 14, but please notify us when you have released the fix for ColorOS 13.1 so that we can test it.
Similarly, please let us know when the fix for Baidu Input Method OPPO Custom Edition is available so that we can test it as well.
Sincerely thank you for your attention and contribution to the safety of our products.
Regarding the two time points mentioned in the email, we will inform you via email when the actual repair is made. You are also welcome to conduct testing to help us improve the security level of OPPO products and services.
OPPO Security Emergency Response Center
Subject: Security issue in Samsung Keyboard
We analyzed Samsung Keyboard on Android as part of our ongoing work analyzing popular mobile and desktop apps for security and privacy issues. We found that Samsung Keyboard for Android includes a vulnerability which allows network eavesdroppers to recover the plaintext of insufficiently encrypted network transmissions, revealing sensitive information including what users have typed. For further details, please see the attached document.
If no response is received to this disclosure, the Citizen Lab will publish details regarding the security vulnerability on its website after 15 calendar days from the date of this communication. In other words, where there is no response from you, Citizen Lab will publish details regarding the vulnerability after October 31, 2023.
If a substantive response is received (which excludes, for example, an auto reply) to this disclosure within 15 calendar days from the date of this communication, the Citizen Lab will provide you with 45 calendar days from the date of this communication to fix (whether in whole or in part) the vulnerability before publicly disclosing the issue. In other words, where we do receive a substantive response from you, the Citizen Lab will publish details regarding the vulnerability after November 30. 2023.
From: Samsung Mobile Security <[email protected]>
Subject: RE: Security issue in Samsung Keyboard
Dear Citizen Lab,
We appreciate you for bringing this issue to our attention.
We have forwarded this issue to our development team and we will work with them to immediately investigate this issue.
And we will let you know when we have further updates or questions regarding this issue.
In the meantime, if you are interested in our rewards program, you may also visit our official site below and report this through our rewards program.
Also note that you need to submit through “Create Report” in below page in order to be eligible for the rewards program:
https://security.samsungmobile.com/securityReporting.smsb
Thank you very much.
Very Respectfully,
Samsung Mobile Security
Subject: RE: RE: Security issue in Samsung Keyboard
Dear Citizen Lab,
We’d like to share an update on this report.
We had immediately shared this report with Sogou; and we’re closely working with Sogou team to receive a patch so that we can update the Chinese HoneyBoard.apk by the end of November.
When the expected schedule is determined, we will provide an update immediately.
Subject: RE: RE: RE: Security issue in Samsung Keyboard
We’d like to share updates on this report again.
We have completed our analysis and started rolling patches of Samsung Keyboard for Chinese models since November 21.
Due to different versions of Samsung Keyboard by One UI version, there are various versions of Samsung Keyboard updated for this issue as listed below:
– One UI 5.1.1 : 5.7.00.45, One UI 5.1 : 5.6.10.42, One UI 5.0 : 5.6.00.52
– One UI 4.1.1 : 5.5.00.58, One UI 4.1 : 5.4.85.5, One UI 4.0 : 5.4.60.49
– One UI 3.1.1, One UI 3.1/One UI 3.0 : 5.3.70.1
Depending on the version of One UI of the device, appropriate Samsung Keyboard version can be downloaded and updated from Galaxy Store.
As the planned disclosure is just around the corner, we expect that you might have completed preparing the article to be disclosed. So, we’d greatly appreciate if you share the article with us ahead of the disclosure.
Subject: Re: RE: RE: Security issue in Samsung Keyboard
Dear Samsung Mobile Security,
Thank you for your response. We have not yet observed the app update on our test device, which is still running version 5.7.00.35 of the Samsung Keyboard. Should we have received the update by now? If not, can you provide a timeline for when we should expect the update?
Subject: RE: Re: RE: RE: Security issue in Samsung Keyboard
When we checked the device you tested, SM-T220/T220ZCS4CWF4, we confirmed that it is based on OneUI 5.1.
However, the version 5.7.00.35 of Samsung Keyboard you shared is for OneUI 5.1.1.
So, we’d like to ask whether you installed the Samsung Keyboard APK using side loading or not.
And please can you try again to update Samsung Keyboard since the update schedule might be different with your regions, carrier or device model.
You can also check the update with keyboard settings below.
– Keyboard -> settings -> Samsung Keyboard Information
To: Samsung Mobile Security <[email protected]>
Subject: Re: Re: RE: RE: Security issue in Samsung Keyboard
Thank you for your response. We first observed version 5.7.00.45 of Samsung Keyboard on December 6, and we can confirm that it fixes our reported issue. With regards to the discrepancy you noted between the originally reported version of OneUI (5.1) and our most recently reported version (5.1.1), this is because we have updated the device to 5.1.1 since our original disclosure.
However, we have an additional security issue to disclose to you in a different keyboard bundled with the SM-T220 device: Baidu Input Method ( please see the attached document ). We believe that the version of Baidu Input Method included on the SM-T220 device is out of date compared to the version available directly from Baidu’s Website, and we observed that the app does not seem to have updates available for it in the Galaxy Store. Unlike the version included on the SM-T220 device, the version of Baidu Input Method available on Baidu’s website uses a stronger encryption protocol that is not trivially broken, but it still has weaknesses which we have previously reported to Baidu ( see additional attached document for the weaknesses in the latest version ). Baidu to this date has been unresponsive to our disclosures.
If no response is received to this disclosure, the Citizen Lab will publish details regarding the security vulnerability on its website after 15 calendar days from the date of this communication. In other words, where there is no response from you, Citizen Lab will publish details regarding the vulnerability after December 27 2023.
If a substantive response is received (which excludes, for example, an auto reply) to this disclosure within 15 calendar days from the date of this communication, the Citizen Lab will provide you with 45 calendar days from the date of this communication to fix (whether in whole or in part) the vulnerability before publicly disclosing the issue. In other words, where we do receive a substantive response from you, the Citizen Lab will publish details regarding the vulnerability after January 26 2024.
Subject: RE:(5) Security issue in Samsung Keyboard
Thank you for sharing additional report regarding Samsung Keyboard.
We always appreciate your valuable reports and we will let you know when we have further updates or questions regarding this issue.
Subject: RE:(6) Security issue in Samsung Keyboard
While reviewing the report about Baidu IME, we’d like to ask you to share us an exact version information of the device you tested.
Subject: Re: (6) Security issue in Samsung Keyboard
Our device is a Galaxy Tab A7 Lite (SM-T220). The tablet was initially One UI 5.1 (T220ZCS4CWF4/T220CHN4CWF4) which we have OTA-updated to T220ZCU4CWI3/T220CHN4CWI3 and then T220ZCS5CWK1/T220CHN5CWK1 as the updates became available for our device. The version of Baidu Input Method was 8.5.20.4 and is reportedly stored in /data/app/BaiduInput/BaiduInput.apk. Please also see the attached screenshots ( 1 , 2 , 3 , 4 ).
From: [email protected]
Subject: (7) Security issue in Samsung Keyboard
We’d like to share an update on the report about BaiduIME.
Our analysis showed that patched BaiduIME had already been registered to Google PlayStore and Chinese Galaxy Store.
However, the device you tested is a Chinese model which doesn’t preload any Google Application including PlayStore. And, in accordance with the store policy, Chinese devices outside of China region cannot access to Chinese Galaxy Store. Our investigation shows that accessing the store from outside of China was the reason your device couldn’t receive any update of BaiduIME.
Subsequently, we have worked with Baidu to provide the latest version of BaiduIME to the Global Galaxy Store, and we confirm that the latest patched BaiduIME has been registered to Global Galaxy Store.
So we’d like to get your confirmation whether the vulnerability was addressed after updating BaiduIME on your side.
Subject: Re: (7) Security issue in Samsung Keyboard
Thank you for your response. We can confirm on our test device that the app is updating to a more recent version and that it uses a newer cryptographic protocol that is not as trivially broken. However, even the newer cryptographic protocol used in the updated version from the Galaxy Store and even in the latest version of Baidu Input Method available on Baidu’s website still contains weaknesses. We have previously reported to Baidu (see attached document for the weaknesses in the latest version). Baidu to this date has been unresponsive to our disclosures.
In an upcoming report, we plan to publish these issues discovered in the version of Baidu Input Method distributed by Samsung and which occur more broadly in Baidu Input Method’s custom protocol governing the privacy of millions of users’ keystrokes. Our recommendation would be for Baidu Input Method to utilize a standard, well-tested network encryption protocol such as HTTPS, TLS, or QUIC rather than their own custom protocol, which is not on par with modern cryptographic standards. Sogou and other vendors have switched to TLS to encrypt keystrokes in their keyboard apps following our reporting of similar issues to them.
Subject: Re: (8) Security issue in Samsung Keyboard
Thank you very much for working with us on this issue.
We will check about it and update you soon.
In the meantime, since your finding is analyzed with version 11.7.19.9, please can you confirmed that BaiduIME(version 12.1.6.1) in Galaxy Store also affected with this vulnerability?
Thank you for your response. We have also analyzed 12.1.6.1 which we downloaded from the Galaxy Store and found that it uses the same weak cryptographic protocol.
Subject: RE: Re: (8) Security issue in Samsung Keyboard
We appreciate you for sharing an update with us.
As you mentioned, it’s a common vulnerability of Baidu for Android, iOS and Windows, and we are worried that pointing out and mentioning Samsung in your upcoming report could be misleading as if there is a greater risk in Samsung devices.
We also asked Baidu to share any update on your finding, but we also haven’t heard any update from them either. As such, we have concerns of mentioning Samsung in your report of Baidu application.
We hope you understand our concerns and reflect them in your report.
When we have any update from Baidu, we will immediately share it with you.
We submitted the following through the Tencent Security Portal:
As part of our ongoing work analyzing popular mobile and desktop apps for security and privacy issues, we previously reported vulnerabilities in Sogou Input Method which enabled network eavesdroppers to decrypt transmitted keystroke data. See here for the details of the previous report: https://en.security.tencent.com/index.php/report/detail/73788 . We have since found similar vulnerabilities in related products which also transmit keystroke data to Sogou servers, which we detail below.
# QQ Pinyin
We analyzed QQ Pinyin on Android and Windows. We found that the Windows version (6.6.6304.400) and Android version (8.6.3) of this software contain similar vulnerabilities to those which we previously reported in Sogou Input Method.
# Samsung Keyboard (com.samsung.android.honeyboard)
We analyzed Samsung Keyboard (com.samsung.android.honeyboard) version 5.6.10.26 for Android and found that it transmits keystroke data to http://shouji.sogou.com completely in the clear without any encryption. We have also reported this issue to Samsung, who indicated that they are already working with the Sogou team on patching this issue.
# 搜狗输入法小米版 (com.sohu.inputmethod.sogou.xiaomi)
We analyzed 搜狗输入法小米版 (com.sohu.inputmethod.sogou.xiaomi) version 10.32.21.202210221903 for Android and found that it contains similar vulnerabilities to those which we previously reported in Sogou Input Method. We are also in the process of disclosing this issue to Xiaomi.
# 搜狗输入法定制版 (com.sohu.inputmethod.sogouoem)
We analyzed 搜狗输入法定制版 (com.sohu.inputmethod.sogouoem) version 8.32.0322.2305171502 for Android and found that it contains similar vulnerabilities to those which we previously reported in Sogou Input Method. We are also in the process of disclosing this issue to Oppo.
# 搜狗输入法定制版 (com.sohu.inputmethod.sogou.vivo)
We analyzed 搜狗输入法定制版 (com.sohu.inputmethod.sogou.vivo) version 10.32.13023.2305191843 for Android and found that it contains similar vulnerabilities to those which we previously reported in Sogou Input Method. We are also in the process of disclosing this issue to Vivo.
# Other apps
The following are other Android apps which reference the string “get.sogou.com”, the API endpoint used by Sogou Input Method, which may require additional investigation:
Note that we are not reporting that we have discovered vulnerabilities in the above list of apps. We are merely providing this list for your convenience so that you may more easily investigate and fix issues in other apps which may be using the Sogou Input Method API in an insecure manner.
# Background
The Citizen Lab is committed to research transparency and will publish details regarding the security vulnerabilities it discovers in the context of its research activities, absent exceptional circumstances, on its website: https://citizenlab.ca/.
# Next steps
Please communicate what steps you will take to address the vulnerability that we have described, and please provide the timeline you decide upon for the implementation of fixes. Finally, upon implementation of any fixes, we ask that you communicate the full extent of the vulnerability to the Citizen Lab. Should you have any questions about our findings please let us know. We can also be reached at this email address: [email protected].
We received the following through the Tencent Security Portal (we also received it via an email):
To Whom It May Concern,
We are in receipt of your communication dated November 23, 2023, and appreciate Citizen Lab’s reporting of potential vulnerabilities in Sogou Input Method and related products, and agreement to withhold any public disclosure through at least January 6, 2024 to avoid malicious exploits and to ensure that the matter may be investigated and, to the extent necessary, patched.
We confirm that the vulnerability related to a CBC padding oracle attack had been fixed at the time of Citizen Lab’s previous report. In the meantime, we have been working with our partners to ensure upgraded versions will send EncryptWall requests using HTTPS.
We are actively reviewing the remaining products listed in your communication and aim to provide further updates in a timely manner. We value our industry partners and security researchers working with us in a responsible and coordinated manner to mitigate risks and uphold system security and user privacy to keep businesses and users safe.
Sogou Input Method Team
We received the following email (a similar message was received via the Tencent Security Portal):
From: security(腾讯安全应急响应中心) <[email protected]>
Subject: Reply:From Sogou Input Method team
Further to our December 6, 2023, e-mail, we write to provide an update regarding the reported vulnerabilities in Sogou Input Method and related products referenced in your report dated November 23, 2023. Please note that the reported vulnerability related to a CBC padding oracle attack had already been fixed at the time of Citizen Lab’s previous report in August.
We can confirm that we have issued and provided upgraded versions that send EncryptWall requests using HTTPS, for the following products identified as having potential vulnerabilities:
Regarding QQ Pinyin on Windows and other Android apps that utilize the string “get.sogou.com,” with the exception of end-of-life products, we aim to finalize the upgrade for all active products to transmit EncryptWall requests via HTTPS by the conclusion of Q1, and respectfully request Citizen Lab to refrain from any public disclosure during this time to prevent potential malicious exploits.
We value our industry partners and security researchers who work with us to keep businesses and users safe by helping to mitigate risk, maintain system security, and protect user privacy.
To: security(腾讯安全应急响应中心) <[email protected]>
Subject: Re: Reply:From Sogou Input Method team
Dear Sogou Input Method Team,
Thank you for your January 5 2024 email.
We can confirm that we will not publicly disclose our findings before March 31 2024
Citizen Lab
Subject: Security issues in Vivo keyboard / 维沃搜狗输入法高危漏洞
总结:多伦多大学的研究人员发现维沃预装的搜狗输入法使用的加密协议有高危漏洞,让网路攻击者可以直接看到用户输入的内容。本文用英文解释了研究人员发现高危漏洞的细节。
We analyzed Vivo pre-installed keyboard apps as part of our ongoing work analyzing popular mobile and desktop apps for security and privacy issues. We found that the Sogou-based one includes vulnerabilities that allow network eavesdroppers to decrypt network transmissions. This means third parties can obtain sensitive personal information including what users have typed. To address these issues, we suggest using HTTPS or TLS rather than custom-designed network protocols. For further details, please see the attached document .
Subject: Security issues in Xiaomi keyboards / 维沃搜狗输入法高危漏洞
总结:多伦多大学的研究人员发现小米所有预装的中文输入法使用的加密协议有高危漏洞,让网路攻击者可以直接看到用户输入的内容。本文用英文解释了研究人员发现高危漏洞的细节。
We analyzed three Xiaomi keyboard apps as part of our ongoing work analyzing popular mobile and desktop apps for security and privacy issues. We found that they all include vulnerabilities that allow network eavesdroppers to decrypt network transmissions. This means third parties can obtain sensitive personal information including what users have typed. To address these issues, we suggest using HTTPS or TLS rather than custom-designed network protocols. For further details, please see the attached document .
If no response is received to this disclosure, the Citizen Lab will publish details regarding the security vulnerability on its website after 15 calendar days from the date of this communication. In other words, where there is no response from you, Citizen Lab will publish details regarding the vulnerability after November 18 2023.
If a substantive response is received (which excludes, for example, an auto reply) to this disclosure within 15 calendar days from the date of this communication, the Citizen Lab will provide you with 45 calendar days from the date of this communication to fix (whether in whole or in part) the vulnerability before publicly disclosing the issue. In other words, where we do receive a substantive response from you, the Citizen Lab will publish details regarding the vulnerability after December 18 2023.
Privacy Policy
Unless otherwise noted this site and its contents are licensed under a Creative Commons Attribution 2.5 Canada license.

IMAGES
VIDEO
COMMENTS
Let's start the detailed case study from here. Samsung entered the electronics industry in the late 1960s and the development and shipbuilding ventures in the mid-1970. Following Lee's demise in 1987, Samsung was divided into five business groups - Samsung Group, Shinsegae Group, CJ Group, Hansol Group and Joongang Group.
In this blog post, we delve into a Samsung crisis management case study to learn about exploding batteries to the intricate strategies employed to restore trust. Samsung's journey offers valuable insights into the intricacies of crisis management in the digital age. Join us as we explore the key lessons learned and best practices from this ...
management will do a deep analysis of the org anization's mission, vision and the way to. use the resources to meet the objectives. Strategic planning is often done by the top management in an ...
This case study describes how Samsung Electronics transformed into a world-class company and the strategic challenges it faces as it looks to sustain its success in both developed and emerging markets. It has been 20 years since Lee Kun-Hee announced the New Management initiative that played a crucial role in transforming Samsung from a second-tier
Executive Summary This study evaluates the corporate strategy of Samsung Electronics, a multinational company, with operations in 80 counties, and a global market leader in several business ...
Table 1. Samsung's risk assessment. According to the risk events highlighted in Table 1 above, two risk categories affect Samsung's operations - COVID-19 and trade wars. The above risks have been ranked according to the risk profile matrix highlighted in figure 2 below and trade wars is the most impactful. Figure 2.
Case Study: Samsung's Innovation Strategy. The success of Samsung has been widely acknowledged in the last decade. Samsung, the world's largest television producer and second largest mobile phone manufacturer, is also the largest firm of flash memory maker. Furthermore, Samsung was ranked by Fast Company Magazine to be third most innovative ...
The Wall brings design at the Hyundai America Technical Center to life. 1-10 of 105 Results. 1 2 3 … 11. In-depth case studies of Samsung business technology deployments.
This study explores how firms manage the entire life cycle of innovation projects based on the framework of harvesting and planting innovation. While harvesting innovation seeks new products in the expectation of financial performance in the short term, planting innovation pursues creating value over a long time period. Without proper management of the process of planting and harvesting ...
Other generic competitive strategies, such as cost leadership, differentiation focus, and cost focus, are also applied in Samsung's operations, but to a limited extent. Cost focus leads to the company's being the best-cost provider in some segments of the semiconductor and electronic components markets. The limited application of cost focus ...
In this case, students assess whether Samsung Electronics has been able to achieve such a dual advantage, and if so, how this was possible. Moreover, Samsung Electronics' long-held competitive advantage is under renewed attack. Students also can assess how Samsung should respond to large-scale Chinese entry into its industry.
When the company introduced Samsung Galaxy and leveraged the power of digital platforms for promotions and marketing, its revenue grew to $218 billion in 2018. Today, Samsung stands 5th on Interbrand's list of Best Global Brands with a brand value of USD 74.6 billion. It has witnessed a 20% increase in comparison to the last year.
Samsung's Mobile team does so at least twice a year. With mounting pressure from lower-quality competitors and a rapidly changing global marketplace, it's critical to understand the complex galaxy of variables that can impact success. ... Read this case study to learn how Samsung is able to successfully address critical business decisions ...
All Mobile Case Studies. 1-10 of 16 Results. 1 2. ... Posts on this site reflect the personal views of each author and do not necessarily represent the views and opinions of Samsung Electronics America. Regular contributors are compensated for their time and expertise. All information shared on this website is for educational purposes only.
Samsung Newsroom (2016). Samsung Electronics Unveils Transformative Innovations for Smarter Living at the Southeast Asia Forum 2016. Retrieved February 1, 2016, from https:// news.samsung.com ...
STEP 1. Problem Identification in Samsung Electronics case study. STEP 2. External Environment Analysis - PESTEL / PEST / STEP Analysis of Samsung Electronics case study. STEP 3. Industry Specific / Porter Five Forces Analysis of Samsung Electronics case study. STEP 4.
Samsung Electronics Company Case Solution,Samsung Electronics Company Case Analysis, Samsung Electronics Company Case Study Solution, Introduction Samsung started its operations in the late 60's. Over the period of time, Samsungdeveloped its stance in the television market by offering
Samsung PESTEL Analysis. Before we dive deep into the PESTEL analysis, let's get the business overview of Samsung. Samsung is a South Korean multinational conglomerate headquartered in Samsung Town, Seoul. It was founded in 1938 by Lee Byung-Chul as a trading company and has since diversified into various sectors, including electronics, heavy ...
In today's world, Samsung is one of the leading companies in electronics. Students are often asked to prepare case studies on its growing business. The purpose of the case study is to provide a…
Business Analysis Case Study Introduction. Samsung is one of the well-known companies in South Korea and is the abbreviation of Samsung Group, Korea's largest enterprise group. The Samsung Group is Korea's largest multinational conglomerate and can be regarded as one of the 'World's Most Admired Companies. The Samsung Group includes a number of ...
Step 2 - Reading the Samsung Electronics HBR Case Study. To write an emphatic case study analysis and provide pragmatic and actionable solutions, you must have a strong grasps of the facts and the central problem of the HBR case study. Begin slowly - underline the details and sketch out the business case study description map.
Samsung Case Study: Samsung is one of the most successful corporations which offer a wide choice of products and services, mostly based on electronics, finance, building and industry. ... Analysis of Samsung's business strategy and competitive advantage Porter's 5 forces model in Exhibit 1 is […] Samsung - Competitive Analysis.
Samsung Case Study Analysis. The advancing technology has narrowed the knowledge boundary amongst the organizations, necessitating innovative approaches that would provide their goods and services with differentiating elements to give them cutting edge leverage. Analysis and identification of the changing trends of the customer requirements are ...
Some Chinese competitors are catching up to Samsung in the smartphone market. Between 2014 and 2015 Huawei's share grew by 48.1%, and Xiaomi's share grew by 29.4%. Samsung is heavily dependent upon consumer electronics sales in markets with limited potential for growth, such as the United States and Europe, for much of its revenue.
With the transformation that was led by the leadership of SEC Chairman Kun Hee Lee, Samsung rebuilt its image as a global business leader. We Will Write a Custom Case Study Specifically. For You For Only $13.90/page! order now. Following the chairman's new management initiative, Samsung is now in a stage of investing in innovative and premium ...
Samsung Electronics owes patent owner G+ Communications $142 million for infringing G+ patents related to 5G wireless technology in its Galaxy smartphones, a Texas federal jury said on Wednesday.
In this report, we examine cloud-based pinyin keyboard apps from nine vendors (Baidu, Honor, Huawei, iFlyTek, OPPO, Samsung, Tencent, Vivo, and Xiaomi) for vulnerabilities in how the apps transmit user keystrokes. Our analysis found that eight of the nine apps identified contained vulnerabilities that could be exploited to completely reveal the contents of users' keystrokes in transit.