An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Springer Nature - PMC COVID-19 Collection


Comprehensive analyses of image forgery detection methods from traditional to deep learning approaches: an evaluation
Preeti sharma.
1 School of Computer Science, University of Petroleum and Energy Studies (UPES), Dehradun, 248007 India
Manoj Kumar
2 Faculty of Engineering and Information Sciences, University of Wollongong in Dubai, Dubai Knowledge Park, Dubai, United Arab Emirates
Hitesh Sharma
Associated data.
Data is available on request.
The digital image proves critical evidence in the fields like forensic investigation, criminal investigation, intelligence systems, medical imaging, insurance claims, and journalism to name a few. Images are an authentic source of information on the internet and social media. But, using easily available software or editing tools such as Photoshop, Corel Paint Shop, PhotoScape, PhotoPlus, GIMP, Pixelmator, etc. images can be altered or utilized maliciously for personal benefits. Various active, passive and other new deep learning technology like GAN approaches have made photo-realistic images difficult to distinguish from real images. Digital image tamper detection now focuses on determining the authenticity and consistency of digital photos. The major research problems use generic solutions and strategies, such as standardized data sets, benchmarks, evaluation criteria and generalized approaches.This paper overviews the evaluation of various image tamper detection methods. A brief discussion of image datasets and a comparative study of image criminological (forensic) methods are included in this paper. Furthermore, recently developed deep learning techniques along with their limitations have also been addressed. This study aims to comprehensively analyze image forgery detection methods using conventional and advanced deep learning approaches.
Introduction
Digital image forgery is a very challenging domain that deals with the tempering and manipulation of digital images. It has become a major concern for the whole society. Merriam-Webster described it as “falsely and fraudulently changing a digital picture,” an idea that dates back to 1840. It reproduces images with different parameter values [ 65 ]. Serious cases of image forgery are increasing, and this alarms the law and order systems of the world [ 30 ]. There are numerous image editing, enhancing, correction, modification, and recreation tools readily available, which encourages the commission of criminal acts.
In fields like forensic investigation, criminal investigation, intelligence systems, medical imaging, insurance claims, and journalism, digital images become critical evidence. This emphasizes the importance of maintaining and detecting the image’s authenticity. As a result, image forgery detection techniques are gaining concern and importance in society [ 11 ]. Two incidences of image forgery are discussed in Figs. 1 [ 90 ] and 2 [ 7 ] and are included here to describe the severity of the issue (Fig. (Fig.2 2 ).

The doctored image depicting Jeffrey Wong Su En while receiving the award from Queen Elizabeth II, published in Malaysian dailies, and the original picture of Ross Brawn receiving the Order of the British Empire from the Queen ( b )

A photo from a 2014 art project in Germany that was shared on Facebook in 2020 to falsely claim that the people in the photo were Chinese coronavirus victims
The incidence listed in Fig. Fig.1 1 is result of a deep learning-based technology called Deepfakes. It is a latest technology that uses GAN (Generative Adversarial Networks) for making fake images/videos by exchanging one person’s face with another. Forged faces and videos are extensively disseminated on the Internet, moral, societal, and security issues (such as fake news and fraud) may occur. Face manipulation can be accomplished through (i) full face synthesis, (ii) identity exchange, (iii) attribute manipulation, and (iv) expression. GANs are unsupervised generative models that learn the data distribution which are built up of two neural networks, one trained to generate data and the other to distinguish fake from genuine data (thus the “adversarial” element of the model). As new forms of GANs arise at an increasing rate, forensics models’ capacity to recognise new types of forged images is growing more difficult. The ultimate requirement of forensics model generalisation ability is investigated in this paper. When they are required to work with unknown sources/datasets, however, their performance suffers. This problem necessitates the development of a general face forgery detection model that is independent of the software used. The field of digital forensics research is finally focusing on solving more generic problems. As a result, it appears that universal solutions and strategies, such as the creation of standardized data sets, benchmarks, and evaluation criteria, will be presented in order to achieve the new frameworks while reducing the risk of digital forgeries.
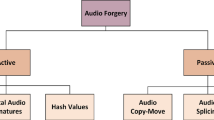
Studies on image forgery suggest that crimes of this nature are mostly done to (1) circulate misleading/false information, (2) gain political influence, and (3) generate unethical publicity and advantages. The propagation of incorrect information needs to be stopped, or some solution is urgently required to address it. Image forensic is a field of digital forensic that deals with image forgery detection and validation. It is an emerging field that seeks to establish the origin and validity of digital media. It works for the detection of the originality of images or videos so that major ramifications on a national and worldwide level due to forgery can be controlled. Digital image forensic ensures the integrity and validity of enormous amounts of data before using them in a variety of circumstances, such as courts of law, forensic, social media, medical fields, etc. that are becoming increasingly vital. It provides techniques divided into two main classes of image forgery detection: a. active image forgery or non-blind image forgery detection; and b. passive or blind image forgery detection, as shown in Fig. 3 .

Active and Passive Techniques for image forgery detection
The active class of forgery detection uses two techniques: digital signature and digital watermarking. These approaches require some prior picture information, which could have been embedded in the image at the moment of capture, during image acquisition, or at a later point. In practice, photos created for forensic investigation, such as fingerprint photos, criminal photos, crime scene photos, and so on, are very unlikely to have a watermark or signature. As a result, active forgery detection techniques have proven to be very useful for forensic examination of digital images. These are not very useful for forensic investigation of digital images. On the other hand, passive forgery detection doesn’t require any pre-embedded information about the image. It works by detecting intrinsic aspects of the image based on the sort of doctoring or identification of the source of the image. This work provides almost a complete guidance of all traditional and modern techniques of forgery detection discussed by different authors. It gives an idea about image forgery, its types, techniques, available datasets, applications, limitations, and its advancement to deep learning at present. This paper provides a good foundation for new researchers to start in this domain and also, the findings discussed as part of the conclusion at the end of the paper would become promising areas of futuristic research.
The remaining section of this review study discusses the classification of active image forgery detection techniques in Section 2 . Section 3 discusses the classification of passive forgery detection techniques and comparative studies of the work done in this field, starting from conventional approaches towards current deep learning approaches. In Section 4 , details about popularly used image forgery datasets and the limitations of existing deep learning-based approaches are also discussed. Section 5 presents new emerging deep learning-based methods that are currently used in the field of image forensics and the discussion section shows the impact of the study in broader way is included in Section 6 and finally, the conclusion is presented in Section 7 .
Classification of active image forgery detection
Active image forgery detection involves two major approaches digital watermarking and signatures. These are two techniques used in active forensic techniques to inject legitimate information into images. When there is a doubt regarding the validity of a picture, the embedded authentication information is retrieved to establish the image’s authenticity [ 7 ]. It is followed by the limitation of multiple processing steps of digital images. Digital Watermarking and Digital Signature are two basic methods used for Active Image Forgery Detection.
Digital watermarking
To identify the watermark, apply to pixel data the maximum length of the linear shift register sequence and compute the sequence’s spatial cross-correlation function as well as the picture that is watermarked [ 61 ]. This information is added or attached with dynamic picture validation that ensures a validation code at the time the image is produced or transferred. However, fake image capturing or processing tools can alter this information. When a fake photograph resembling an original image is recreated using image editing tools, it either lacks this information or else contains it. Ferrara et al. [ 24 ] projected a new forensic tool centered on the interpolation procedure for assessing the original image and forged portions. During forgery detection, the conditional co-occurrence probability matrix (CCPM) is used for detecting third-order statistical features that can also be used to detect picture splicing. Li et al. [ 56 ] devised a new method for the detection of copy-move forgeries in which the circular blocks were extracted using the Local Binary Pattern (LBP). It is claimed here that detecting forgeries at different angles of the rotated region is extremely challenging. Hussain et al. [ 37 ] proposed a multiresolution Weber Local Descriptors (WLD) method for detecting picture forgeries based on chrominance component characteristics. To identify forgeries, the Support Vector Machine (SVM) classifier and the WLD histogram components are used.
Digital signature
One of the most common ways to detect picture forgery or manipulation is through digital signatures. A digital signature is used to represent the validity of a digital document using a mathematical structure. This is an owner and application-specific utility that embeds authentic user and device information.
This information is added or attached with dynamic picture validation that ensures a validation code at the time the image is produced or transferred. A robust bit is taken from the original picture in the digital signature. A 16*16 pixel block is used to divide a picture. Random matrices of size N with elements evenly divided in the interval [0, 1] are generated using a secret key k. Every random matrix is subjected to a low pass filter regularly to N random smooth patterns. By applying the signing procedure to a digital picture, the system generates a digital signature.
The following are the qualities of a digital signature:
- It is only the sender who can sign the original image and the recipient who can only confirm that signature.
- The signature cannot be falsified by unauthenticated users.
- It provides integrity and avoids
Doke et al. [ 20 ] proposed a low phase filter method for acquiring an X random pattern for each random matrix recurrently. Through the signing operation on the image, the model generates a digital signature. The following phases are included in the image signing operation:
- Images are decomposed using parameterized wavelet features.
- Remove the standard digital signature.\
- Cryptographically, the crypto signature is produced by using the private key and hashing the extracted standard digital signature.\
- The client receives digital images as well as a cryptographic signature.
Ginesu et al. [ 31 ] presented a novel mutual image-based authentication framework. It is a challenge-response scheme that uses a visual password and image scrambling. The software’s application window is divided into k grids, each with h cells. Throughout the user must correctly identify images to pass the image/s selection procedure the k pass image/s chosen at random from the N JPEG images database.
Experimentation
This section discusses about classification of Passive Image Forgery Detection . It is the most evolving detection scheme that deals with image forgery these days. Picture forensics, also known as passive or blind image forensics, is a method of determining image authenticity and source without depending on pre-extraction or pre-embedded data [ 116 ]. It includes five methods: Pixel-based detection, Format-based detect physical-based detection, Camera-based detection, and Geometry-based detection. These methods further include several detection techniques shown in Figs. 4 and and5 5 .

Passive image forgery detection techniques

Classification of various methods of image forgery detection techniques
These are the popular image tampering tricks (device-independent) used to modify/recreate an image for accomplishing evil/criminal intention [ 15 ]. Different image processing tools are used to serve the purpose. Passive processes are given into shape with one or more images. The fake image thus produced, although looks authentic, contains intricate traces of inconsistencies, such as overlapping loss of information, distortions, and other artifact fingerprints as clues for Image Forensics.
Pixel based forgery detection
Pixel-based classification is performed on a pixel-by-pixel basis, using only the spectral information available for that specific pixel. Pixel-based techniques are frequently used to extract low-level features, where the image is classified based on spectral information, and pixels in the overlapping region are misclassified due to class confusion. Copy-move, Image splicing, Image resampling, and Image retouching are major classes of pixel-based forgeries. Various methods for their detection are devised in many previous types of research and are still a hot research area especially using Deep Learning Approaches.
Copy and move based methods
It is one of the most common image tampering techniques, and it’s also one of the most difficult to spot because the cloned image is taken from the same image. A section of an image is copied and pasted to another part of the same picture in Copy-Move image forgery [ 2 ]. It consists of two attacks: class-1copy-move forgery and class 2 copy and creates a forgery. Figure Figure6a 6a and and6b 6b show an example of class 1 and class 2 attacks [ 30 , 37 ].The methods deployed for Copy-Move forgery detections are block-based and key point-based listed below [ 2 ].

a : Copy-Move image forgery (Class-1 type). b : Copy- Create image forgery (Class-2 type)
This technique is frequently used as a process of evil intended image manipulation to change the image message or conceal its portion(s) with the help of another image(s)/digital effects. Image editing features, such as copy, move, duplicate, clone, image merging, and filters are used.
As a result, the fake image bears distinctive traces of distortion, digital correction, overlapping, and other enhancing effects. Also, the size and shape of the doctored portion can be analyzed to record the image forgery. Lu et al. [ 60 ] proposed a new scheme that makes use of the circular domain coverage (ECDC) algorithm. The proposed scheme combines forgery detection methods based on blocks and key points. First, from an entire image, speed-up robust features (SURF) in log-polar space and scale-invariant feature transform (SIFT) are extracted. Second, generalized two nearest neighbors (g2NN) are used to generate a large number of matched pairs. To detect tampered regions Popescu et al. [ 80 ] worked upon principal components analysis (PCA) as a feature. Yao et al. [ 114 ] detect copy-move forgery using non-negative matrix Factorization. Non-negative matrix factorization (NMF) coefficients are extracted from a list of all blocks after the image is partitioned into fixed-size overlapped blocks. It is worth mentioning that all of the coefficients are quantized before matching, which means that a sub-image can be interpreted with a small amount of data. Rani et al. [ 85 ]. This research proposes a pixel-based forgery detection framework for copy-move and splicing-based forgeries. Initially, image data is pre-processed to improve the textural information. For the identification of bogus picture regions, the suggested method estimates multiple attributes using augmented SURF and template matching. The estimated key parameters are compared to the determined threshold value. The CASIA forged picture dataset is used in the evaluation. The upgraded SURF approach has a forgery detection accuracy of 97%, while template matching has a fraud detection accuracy of 100%.
Image-retouching forgery detection methods
It is a very useful approach in magazines and photography in films. Although such modifications are to beautify the image and hence not counted for forging. But we are including it here as it includes changes/manipulations with the originality of the image. The image is upgraded to beautify it, and only particular parts are altered (like removing wrinkles) to produce the final shot. In Fig. 7a , part shows the retouched image while (b) part shows the original image.

a Retouched image and b original image
These are common enhancement techniques that are comparatively harmless and considered less malicious than other forgery methods. Such manipulations are done using good photo retouching tools to correct or improve a whole image or its portion. They are commonly used as accepted image editing tools in print/web media. Fine retouching works, such as ton correction, saturation, sharpness, or noise corrections, are so precise that such variations cannot be identified unless checked using sophisticated tools. Xing et al. [ 111 ] describe a new algorithm based on an 8-neighborhood quick sweeping technique. The experimental result shows that there is a significant increase in the rate of the image inpainting while maintaining-quality effect. Sundaram et al. [ 111 ] presented a review consisting of methods by Wang et al. proposed a universal picture construction in which three critical parameters, such as Area, Shape, and Perimeter, are presented (ASP). Then, by the ASP principles, a Pyramid model based on downsampling in painting (PDI) was presented. The results of the experiments show that by incorporating the PDI model, the performance of existing techniques can be drastically improved. In addition, according to a paper by Bo et al., an image inpainting technique based on a self-organizing map (SOM) is used to find the useful structure information of a ruined image. Kumar et al. [ 50 ] examined different pixel- and physics-based counterfeit detection algorithms, as well as a comparative examination of these techniques. Furthermore, imaging devices and processing procedures, no matter how varied they are, contain a constant pattern in the image that, if interfered with, will introduce a departure from the original pattern. This divergence allows one to detect image counterfeiting. It has more accurate forgery detection and has more homogeneous lit surfaces. Some of the methods can be referred from [ 43 , 66 ].
Image splicing or photomontage forgery detection methods
It is a frequent kind of digital image alteration. Image splicing, often known as image composition, is one kind of tampering. Image splicing is defined as a technique that copies and pastes areas from identical or distinct sources [ 30 ]. With this method, an image is recreated/transformed by merging many image(s). The method is also known as image composition in which primary information of each image used in splicing is lost/distorted/damaged as shown in Fig. 8 .

Image splicing forgery
The spiciness has two broad classifications and that are (1) Boundary-based Splicing and (2) Region-based Splicing. Forensics approaches are used to identify the tampering tools as well as the nature/zones of distortions present in these fake images. Fan et al. [ 23 ] estimate the illuminance of each horizontal and vertical band; they proposed combining five low-level statistics-based algorithms. Based on local illumination estimation, inconsistencies in the illuminant color in the object region were used to detect region splicing frauds. Lyu et al. [ 96 ] use of local noise inconsistencies to detect small regions damaged by local noise is presented as a blind forgery detection approach. The approach employs no overlapping blocks and high pass diagonal wavelet coefficients at the highest resolution. To detect spliced forgery, the image was segmented based on homogeneity criterion into many homogeneous sub-regions using a basic area merging technique. The approaches work well on images with uniform noise levels, but they fail when the verified image has the same. Pan et al. [ 74 ] make use of local noise inconsistencies to detect small regions damaged by local noise is presented as a blind forgery detection approach. The approach employs non-overlapping blocks and high pass diagonal wavelet coefficients at the highest resolution. To detect spliced forgery, the image was segmented based on homogeneity criterion into many homogeneous sub-regions using a basic area merging technique. The approaches work well on images with uniform noise levels, but they fail when the verified image has the same.
Image resampling forgery detection
It is based on the concept that geometric modifications like stretching, flipping, skewing, rotation scaling, etc. are made to some particular sections in need to generate an amazing forged image. The interpolation stage is crucial in the resampling process since it introduces significant statistical changes. The picture is resampled, which introduces unique periodic correlations. These connections can be put to good use [ 42 ]. Figure Figure9 9 shows an example of the image resampling method [ 82 ]. Wang et al. [ 111 ] represented that supervised learning is a powerful and universal approach to deal with the twin challenges of unknown picture statistics and unknown stenographic codes. A pivotal piece of the learning procedure is the determination of low-dimensional instructive features. Liu et al. [ 57 ] studied the relationship between surrounding Discrete Cosine Transform (DCT) coefficients and suggested a method for detecting enlarged JPEG images and spliced images, both of which are commonly exploited in photo counterfeiting. The neighboring joint density features of the DCT coefficients are extracted in detail, and the features are then detected using Support Vector Machines (SVM) (Tables (Tables1, 1 , ,2, 2 , ,3, 3 , ,4 4 and and5 5 ).

Image resampling forgery
Pixel Based Image Forensics: Copy-Move/Splicing/Resampling
Compression Based Image Forensics: (JPEG Compression/ Double JPEG Compression/Multiple Compression/JPEG Blocking)
Camera-Based Image Forensics: Chromatic aberration/Color Filter Array/Source camera abbreviation/Sensor imperfection
Physics-Based Image Forensics: Light Direction (2D), (3D) and Light Environment
Geometric Based Image Forensics: Camera Intrinsic parameters/Metric Measurement/Multi-view Geometry
Compression based forgery detection
Forgery detection can be made difficult by the alteration of a forged image for compression and other purposes. Forgery detection is difficult using JPEG picture compression. JPEG stands for Joint Photographic Experts Group. However, some JPEG compression features are used in forensics analysis to detect tampering traces [ 79 ]. JPEG quantization based, double JPEG compression based, multiple JPEG compression based, and JPEG blocking based approaches are all examples of these techniques. Specific compression algorithms introduce statistical correlation, which is useful for detecting image counterfeiting. Huang [ 76 ] described a technique for detecting double JPEG compression that makes use of a quantization matrix. Kee et al. [ 30 ] described a method for determining whether or not a picture has been edited by using the camera signature of a JPEG image.
In light of the belief that when the block-wise DCT is handled in line with the primary JPEG compression grid, its coefficients will display an integer periodicity. Bianchi et al. suggested an approach for detecting non-aligned double JPEG compression. For modeling of images, Rani et al. [ 84 ] develop a steganalysis metric based on a Gaussian distribution. The distribution of DCT coefficients is modeled using a Gaussian distribution model, and a ratio of two Fourier coefficients of the distribution of DCT coefficients is quantified. This derived steganalysis metric is compared to three stenographic methods: LSB (Least Significant Bit), SSIS (Spread Spectrum Image Steganography), and the Steg-Hide tool, which is based on a graph-theoretic approach. Different classification approaches, such as SVM, are used to classify picture features datasets.
JPEG quantization method
The image that we will supply in JPEG (joint photographic expert group) format, in which the initial image is converted into an RGB image to brightness or chromatic space. These figures fluctuate depending on the low and high points. These JPEG compression speeds are represented by 192 values that show the channels of the RGB color system. The quantization that the DCT achieves Methods of (discrete cosine transformation) [ 95 ].
Double JPEG quantization and JPEG blocking method
Images must be uploaded into a program that will be used to manipulate them, and then saved again. We can infer from the fact that the vast majority of photographs are stored in JPEG encoding that only genuine images are stored in JPEG encoding.Encoding JPEG images in lossy mode results in particular patterns that do not appear in photos that are compressed in a single pass. Double JPEG compression creates patterns that can be exploited as indicators of manipulation or tampering [ 33 , 72 ]. The Discrete Cosine Transform is the foundation of JPEG compression. As the JPEG image is made up of 8 × 8-pixel image blocks that have been converted and quantized independently, the patterns emerge at the boundary of nearby blocks in the form of horizontal and vertical edges. A doctored image may have these blocking patterns altered. To reduce file size in Y’CbCr color space, these JPEG blocks use a typical factor for digital image compression: 8 by 8-pixel blocks [ 117 ].
-based forgery detection
When we capture a photo with a digital camera, the image passes from the sensor to the memory, where it goes through a series of processing stages that include quantization, color correlation, gamma correction, white balancing, filtering, and JPEG compression. These processing phases, from image capture to image stored in memory, may vary depending on the camera model and camera antiques. These methods are based on this standard. Chromatic aberration, color filter array, camera response, and sensor noise are the four types of approaches that can be used [ 7 ]. Geradts [ 29 ] stated that if a portion of an image has a common intensity of lighting faults in pixels, they are only visible in darker or lighter areas. Because of the varying wavelengths of light, the lens bent it to different degrees. Defects in pixels are caused by temperature. A few post-processing manipulations, such as image, contrast, compression, blurring, and so on, can also help to eliminate incorrect pixels. Due to the exorbitant expense of many sensors, several manufacturers employed only one sensor to capture a natural color scene. As a result, color filter arrays (CFA) are frequently used in sensors to restrict the wavelength band that reaches the CCD array. Few projection algorithms have been proposed for full-resolution color vision reconstruction [ 83 ]. Some artifacts in cameras can be used to enhance photographs taken with conventional cameras. This type of picture forensics can be done using a variety of approaches. Typical cameras are being replaced by low-cost cameras. Images are captured in everyday life using cameras from companies such as Leica, Sony, Fujifilm, Pentax, Panasonic, Canon, Nikon, and others that use wavelengths that reach inside a CCD array.
Chromatic aberration
Chromatic aberration occurs from an optical system’s failure to concentrate light perfectly on different wavelengths. Lateral chromatic aberration, as an expansion/contraction of the color channels with each other, expresses itself in a first_order approximation. This aberration is often disrupted and cannot be constant in the entire image while manipulating an image [ 38 ]. One disadvantage of this method is that to obtain a global assessment of the entire image, the majority of the image must be real. On the other hand, if a large portion of the image is forged, the overall estimation of the image is wrong and may produce false findings. It also produces good results when the image is of high quality since chromatic aberration may be better modeled with high-quality photographs [ 69 ].
Color filter Array
A digital color image is made up of three channels, each of which contains samples from several color bands, such as red, green, and blue. The vast majority of digital cameras come with either a single charge-coupled device (CCD) or a pair of complementary charge-coupled devices (CCDs) color sensors using a metal-oxide-semiconductor (CMOS). A color filter array is used to create images (CFA) [ 81 ]. The most commonly seen Bayer array is a three-color CFA that is widely used that uses three color filters Red, Blue, and Green [ 104 ].
Source camera abbreviation
Digital image source identification is a type of technology that determines the picture source only based on the image itself, without any knowledge of the image creation equipment. Signal processing is used to do this. The forensic investigator can use the source camera identification to figure out what kind of camera was used to capture the image under inquiry. When digital content is presented as a silent witness, it is critical [ 112 ].
Sensor imperfection
Many forensic applications, such as matching an image to a specific camera, revealing malicious image manipulation and processing, and determining an approximate age of a digital photograph. Imperfections of digital imaging sensors can serve as unique identifiers, just as human fingerprints or skin blemishes. Defects caused by manufacturing flaws, physical processes occurring inside the camera, and environmental factors are among the many types of defects that forensic analysts are interested in [ 26 ].
Physics-based forgery detection
Natural images are typically taken in a variety of lighting situations. As a result, in splicing processes, the lighting of a forged zone may differ from the original (where two or more images are used to create a forged image). In physics-based approaches, light source discrepancies between certain objects in the scene are employed to reveal tampering evidence. Images are blended at the time of modification in this process, which is captured under a variety of lighting conditions. It can be difficult to match up the lighting state when using these photographs. The blended photos illumination discrepancy could be used to demonstrate the tempered areas of image counterfeiting. For the first time, Stojkovic et al. [ 98 ] proposed a solution to these problems. They devise a method for evaluating the side of a lighting source in the first degree of freedom to demonstrate the effects of tampering. Kumar et al. [ 53 ] proposed an approach that works for photographs with any sort of item present in the scene, i.e. it is not restricted to human faces and image selection of same intensity regions. The suggested technique identifies the manipulated object and returns the angle of incidence concerning the light source direction by analyzing the lighting parameters. On an image dataset composed of various sorts of modified images, the exhibited solution achieves a forgery recognition rate of 92%.
Light environment
It is a physics-based image forgery detection that looks for lighting anomalies in complex natural lighting. When splicing items from multiple photos, it’s tough to achieve physically constant illumination, and research demonstrates that such errors are difficult to detect with human eyes [ 73 ]. Lighting-based forensic can be categorized as simple directional lighting, 2D complex lighting and 3 D complex lighting discussed further in Light Direction (2D and 3D) . The last two methods work by first recovering the lighting environment, which is represented by a group of spherical harmonics coefficients, and then comparing the coefficients estimated from different parts of the image [ 22 ]. The lighting in the scene is sophisticated, in that a large number of lights can be put in arbitrary positions, resulting in a variety of complex lighting situations. Nirmalkar et al. [ 72 ] explain how to estimate a low-parameter representation of such complex illumination conditions. Kumar et al. [ 54 ] suggested a strategy for detecting image alteration utilizing complicated lighting-based analysis. For photos obtained under one or more light sources, this approach yields satisfactory counterfeit detection results. We calculated elevation angles for certain objects about various light sources in the scene. The approach discovers light sources and elevation angles by using pixels from a certain location. The acquired results from the suggested technique are compared to verify the resilience to identifying tampering in synthetic images while taking precomputed and source direction into account.
Light direction (2D)
This method deals with the estimation of the area in which the light source’s 2D location is located. This area is referred to as the “Light Zone” (LZ). This calculation is based on the shadow area that has been calculated for the current image. Shadow segmentation is based on the previously estimated shadow area and the currently estimated Light Zone [ 78 ]. Stojkovic et al. [ 98 ] present a method for displaying the results of a fabricated part of an image that is based on a light direction anomaly. Using blind identification methods, the above method was used to estimate the picture’s plane normal matrix. Forgery detection accuracy was found to be 87.33% in this model. The approach proposed by Kumar et al. [ 51 ] detects image fraud by exploiting discrepancies in the light source direction. Initially, surface normal is generated using a surface texture profile on the input image during the preprocessing step. The RED band is primarily utilized to gather surface texture information and to perform surface normal calculations. The incidence angle θ i is calculated for various image patches using the estimated lighting profile and normal. The θ i angle is the estimated angle between the picture object and the direction of the light source. The inconsistency of θ i values is utilized as proof of tampering, and it has been discovered to be capable of identifying modified items in an image.
Light direction (3D)
This method is based on the surface reflection model of the image which uses convexity and constant reflectance as two parameters. It detects forgery especially Face forgery by taking occlusion geometry and surface texture information into major consideration. To estimate the 3D lighting SH (spherical harmonics) coefficients, it recreates the 3D face model from some face photos and uses the 3D normal information [ 77 ]. Kee et al. [ 44 ] describe a low-dimensional model for assessing the 3-D lighting environment. It evaluates model parameters based on a single image. Fan et al. [ 22 ] focuses on lighting-related forensics. It demonstrates how to use a simple counter-forensic method to deceive a forgery detection based on 2D lighting factors. For forensics, this intermediate result supports the application of more complex 3D lighting factors. Such a study route necessitates at least a rough approximation of the suspect object’s 3D surface. Kumar et al. [ 49 ] suggested a study that demonstrates a cutting-edge forgery detection system based on lighting fingerprints available in digital photos. Any alteration of the image(s) results in distinct fingerprints, which can be used to confirm the image(s)’ integrity after the analysis. This technique employs several processes to determine the intensity and structural information. The Laplacian approach is used to extract dissimilar features from an image, which is then followed by surface normal estimation. Using this information, the light’s source direction is calculated in terms of angle w. By recognizing distinct fingerprints based on illumination factors, the suggested technique offers an efficient tool for digital image forgery detection.
Geometric based forgery detection
Geometric constraints are used in forgery detection systems that utilize perspective views. These techniques are further divided into intrinsic camera parameters-based techniques (such as focal length, main point, aspect ratio, and skew), metric measurement-based techniques, and multiple view geometry-based techniques [ 52 ]. In real photographs, for example, the primary point (the intersection of the optical axis and the image plane) lies at the image’s center. When a small section of an image is moved or translated (copy-move example), or two or more photos are combined (splicing example), keeping the image’s main point in the correct perspective becomes problematic [ 27 ]. Johnson et al. [ 39 ] review and recommend many projective geometry tools, including a method for rectifying planar surfaces and the capacity to make real-world measurements from a planar surface. The first method makes use of polygons with well-defined shapes. The second method is based on the concept of vanishing points, which can be one or two in number on a plane. Every approach estimates the world-to-image transformation, which can be used to remove planar distortions and perform measurements.
Camera intrinsic parameters
Scale factor, focal length, lens distortion, skew, and principal point are the intrinsic parameters of a camera. This allows mapping the camera coordinates to the pixel coordinates. This mapping is a 3D to 2D mapping and lies upon many independent parameters [ 100 ]. Internal parameters estimated from a non-tampered image should be consistent across the image. As a result, variations in these parameters across the image are used to detect tampering [ 107 ]. Ng et al. [ 70 ] review and recommend many projective geometry tools, including a method for rectifying planar surfaces and the capacity to make real-world measurements from a planar surface. The first method makes use of polygons with well-defined shapes. The second method is based on the concept of vanishing points, which can be one or two in number on a plane. Every approach estimates the world-to-image transformation, which can be used to remove planar distortions and perform measurements.
Metric measurement
Metric measurements can be taken from a planar surface after rectifying the image. There are three methods for rectifying planar surfaces when using perspective projection. Only a single image is used by each method. The first method requires the knowledge of known-shape polygons, the second method is based on two or more vanishing points, and the third requires two or more coplanar circles that can be used to recover the image to world transformation, allowing metric measurements to be taken on the plane. Metric measurements help to detect the region of interest even if it lies out of the reference plane. [ 108 ]. Points on a plane, X, in the world coordinate system are imaged to the image plane with coordinates x, given by: x = H X .
Both points are homogeneous 3-vectors in their respective reference systems. Four or more points with known coordinates X and x are required to solve for the projective transformation matrix H. The estimation of H is determined up to an unknown scale factor. This scale factor must be determined from a single image and a known length on the world plane. The image is warped according to H −1 with a known H to produce a rectified image from which measurements can be taken. Nirmalkar et al. [ 72 ] review and recommend many projective geometry tools, including a method for rectifying planar surfaces and the capacity to make real-world measurements from a planar surface. The first method makes use of polygons with well-defined shapes. The second method is based on the concept of vanishing points, which can be one or two in number on a plane. Estimates the world-to-image transformation in each approach, allowing planar distortions to be removed and measurements to be taken.
Multi-view geometry
It is defined as a method for detecting picture composites by enforcing two-view geometrical constraints on image pairs: H and F constraints, where H denotes the planar homographic matrix and F is the fundamental matrix.
H constraint occurs when a camera rotates for an angle, corresponding points ×1 and ×2 on two image planes are related by: x 2 = K [ R | 0 ] X = KRK − 1 x 1 . F Constraint occurs when a camera moves in general and points are not coplanar. A Fundamental Matrix, F, can be used to connect them using a point x 1 on one image to a line l 1 on the other represented as x 2 Tl 1 = x 2 T F x 1 where x 2 corresponds to x 1 [ 68 ] .
Limitations of existing deep learning-based approaches and different open-access forensic datasets
There are certainly major issues where the deep learning approaches are also struggling hard and that can become the base for future research:-.
Lack of optimal model of image forgery model
Most of the models suffer from cumbersome algorithms fitted with wrong classifiers. Such frameworks lead to poor/faulty performance. Choice of the dataset (or its unavailability) is also a criterion where the models suffer. Overall, a faulty image forgery detection model is often seen to fail due to extra time consumption and expensiveness. Moreover, procedures in Deep learning Image Forgery Detection vary a lot from one another, in terms of pre-processing, training, and human decision analytical phase.
Lack of accuracy of automated forgery prediction
Even today, this aspect is still chiefly dependent on the classifiers. They often perform poorly in case of detecting intricate forgeries, such as Deep Fakes. Selection of initiation mode and detection location (pixel/region) become incompatible with one another during the analysis phase. Thus, automation for this phase cannot be ideally achieved. Rather, in almost every case they need an expert to intervene in the process.

Lack of availability of deep learning-based good tools
It is found that Deep Learning-Based Image Forgery Detections work efficiently only in limited areas, such as device detection, copy-moving detection, etc. Moreover, the experimental results are heavily dependent on dataset selection and utilization.
Lack of cost-effectiveness
Most of the mechanisms as categorized in the study are costly due to the inclusions of classifiers, high-end training algorithms, and computational issues. In Image Forensics, the existing dataset plays a major role for model training and development purposes. There are different types of datasets available to accompany these analyses, such as Dataset of original information, such as UCID dataset, RAISE dataset, Vision Dataset, etc. Dataset of Manipulated information, such as CASIA V1, CASIA V2 dataset, MICC-F220 dataset, etc. as shown in Table Table6 6 .
Listing most common use datasets in image forgery detection
Modern Deep learning-based forgery detection techniques
This section defines the most prevailing, demanding, and modern detection techniques used in the world nowadays in the field of forensic sciences. Joudar et al. [ 40 ] proposes a new optimization model for kernels redundancy reduction in CNN. Fernandes et al. [ 41 ] proposed that a particle swarm optimization-based algorithm could be used to search for the most effective convolutional neural networks.
Other than the conventional methods as described above, there are more complicated image forgeries done nowadays. An emerging Artificial Intelligence-based trick is Deepfakes done using Specific Datasets (human faces, shapes, figures, etc.) assisted Neural Net techniques capable of region/face detection and neat modification [ 10 ]. Deep fakes are images/ videos in which one person’s face has been convincingly replaced by a computer-generated face that often resembles a second person. Sharma et al. [ 93 , 94 ] explores an innovative method for determining an individual’s emotional state by analysing the shape of their lips at various points in time.
Anti-forensics
Anti-computer forensics, also known as counter-forensics, are methods of preventing forensic analysis. Through the drawbacks as present in deep learning-based Image Forensics approaches, such as adversarial attacks where the Convoluted Neural Network (CNN) Model of Image Forensics is poor, smarter tricks are developed that can bypass the deep learning detection systems. Examples are, Jacobian-based Saliency Map Attack (JSMA), Fast Gradient Sign Method (FGSM), etc. [ 32 ].
Image source location(location forensic approaches)
Image source location based forensic approaches discusses into three categories. Camera artifacts based, Imaging property based and Sensor imperfection based source locations.
Camera artifact based source location
Based on every camera specification, lens and CFA produce some amount of aberration that can be analyzed from a digital image, and accordingly, the image capturing device can be located. Works in this area include choi et al. [ 92 ] who implemented Devernay’s line extraction method and proposed an image source location approach based on lens aberration analysis. Van and others used Support Vector Machine (SVM) as a model training scheme to analyze Chromatic aberration as a fingerprint for locating the correct image source.
Sensor imperfection based source location
Three major sensor defects aid the Image Forensic Experts to locate the Image Source. These are fixed pattern noise (FPN), Photo Response Non-Uniformity (PRNU), and pixel defects. Lukas and others worked based on pattern noise as exhibited through FPN and PRNU and made a comparative study on locating the correct image source. Koppanati [ 46 , 47 , 48 ] highlights a novel model for the encryption of multimedia data on cloud and using LFSR which uses of the RGB channels to encrypt data with the assistance of Logistic Map and Linear Feedback Shift Register. The authors Mantri et al. [ 62 ] propose a Pre-Encryption and Identification Technique in order to detect crypto-ransomware attacks at the pre-encryption level (PEI).
Imaging property-based source location
Coding and post-processing features as present in recognized digital image capturing devices are evidence for identifying actual Image Sources. Taking this fact as a working rule, Kharrazi et al. used pre-storage color processing and size corrections as fingerprints to locate the actual image capturing device. His model utilized SVM as a training scheme. Keeping security related to transmission and storage, Manupriya et al. [ 63 ] proposes an encryption technique called V ⊕ SEE which requires less bandwidth and CPU than AES and DES.
High-speed internet access and free high-processing digital editing tools (image) worsen the problem of digital resource authenticity. Due to social networking sites, it’s difficult to find the source of digital resources. Finding the history (flow) of digital resources is crucial. Identifying forgeries and digital asset modifications to improve information clarity is difficult. The biggest challenge is identifying the few operations done on digital assets to improve clarity without changing their meaning or origin. New set of digital acquisition, processing, and tools and their accessible availability, widespread transmissions via social networking sites over the internet, and open source software have all contributed to a substantial and demanding problem of digital forgeries. Digital forensic is a new discipline that’s trying to figure out where digital media came from and how accurate it is. It detects the originality of photos or films, allowing for the management of enormous implications on a national and global scale caused by forgery done using Active, Passive or other deep learning based approaches including GAN the new and advance one in this field. The field of digital forensics research is finally focusing on solving more generic problems. As a result, it appears that universal solutions and strategies, such as the creation of standardized data sets, benchmarks, and evaluation criteria, generalized techniques will be required in order to achieve the new frameworks while reducing the risk of digital forgeries.
This paper critically reviews the broad classification of image forgery detection techniques. A comprehensive overview of active and passive forgery methods is analyzed by systematically surveying the literature. This study finds a wide scope of Deep Learning based methods in Passive Image Forgeries, ranging from pixel-based to geometric-based detection. Smarter algorithms are implemented to locate tampering in the fake face images as found in Deep Fake forgery. Future research in this field can be assisted using a variety of open-access datasets like CASIA V1, CASIA V2, MICC-F2000, CoMoFoD, etc. The paper concludes that advanced image forensics should incorporate more advanced methodologies that minimize executable time and operational cost. Key constraints like (1) accuracy of detection, (2) feature dimensionality, and (3) Robustness against a high degree of post-processing (4) High computational complexity (5) Vulnerability to multiple attacks such as rotation, scaling, JPEG compression, blurring, and brightness control, etc. (4) A large number of false matches with a regular backdrop are issues which require further studies. In a nutshell, despite deep learning methods showing wonderful results, there is still room for improvement to deal with more intense forgeries arising in today’s world.
In term of future work it appears that universal solutions and strategies, such as the creation of standardized data sets, benchmarks, and evaluation criteria, new deep generative techniques are extremely required in order to achieve the generalized solutions of detection of digital forgeries. Benchmarks for forged and unforged data sets are needed to evaluate collaborative research. Creation of open access data sets that are applicable for all possible forgeries such as copy paste, compositing, splicing, photomontage, blending, matting etc. is also promising area to explore in order to determine, analyse, and comprehend the usefulness of existing and future research studies. Designing more advance, generalized and robust forgery prevention and detection approaches that work efficiently for wild scenarios will be key research area to deal with more intense forgeries in future.
Data availability
Declarations.
The authors have no conflict of interest.
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Contributor Information
Preeti Sharma, Email: [email protected] .
Manoj Kumar, Email: [email protected] .
Hitesh Sharma, Email: ni.ca.sepu.ndd@amrahskh .
Toward Deep-Learning-Based Methods in Image Forgery Detection: A Survey
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

Literature review of Image forgery detection techniques from 2015 to 2019

The field of image forensics has matured with the development of nascent techniques to catch the image forgeries done with the applications and tools developed over a period of time. A large number of literature is produced in this field within a short span of time due to its importance both in daily life, and to achieve long term social benefits. The number of scholars has also increased many a folds. Literature presenting reviews on image forgery techniques holds importance for the scholars" endeavoring in the field of image forgery detection. The updating the literature review also is an important aspect of the field with the fast developments in the field. The author presents literature review of research papers on image forgery published in reputed journals from 2015 to 2019 to bring in light the latest tools, techniques and algorithms in the field of image forgery detection. The paper concludes with identification of latest tools, techniques and algorithm available in the field of image forensics in chorological order.
Related Papers
Gauravkumarsingh Gaharwar
Image forgery is emerging as a big problem not only for law enforcement agencies but also for citizens as well. With the readily availability of low cost hardware & software and all the images being digital only, it becomes easy for criminals to forge any image. This paper studies contemporary solutions proposed by different researchers for identifying forgery in copy-move forgery, image splicing, image retouching, and lightning condition forgery. The aim of this paper is to study for the single algorithm which is effective enough to identify any type of forgery.
Govindraj Chittapur
Digital Photo images are everywhere, on the covers of magazines, in newspapers, in courtrooms, and all over the Internet. We are exposed to them throughout the day and most of the time. Ease with which images can be manipulated; we need to be aware that seeing does not always imply believing. We propose methodologies to identify such unbelievable photo images and succeeded to identify forged region by given only the forged image. Formats are additive tag for every file system and contents are relatively expressed with extension based on most popular digital camera uses JPEG and Other image formats like png, bmp etc. We have designed algorithm running behind with the concept of abnormal anomalies and identify the forgery regions.
International Journal on Computational Science & Applications
International Journal of Advanced Research in Computer Science
Ashish Chakraverti
Image forgery and image forgery detection are emerging as well as hot research topics among researchers. In today’s digital scenario, images are playing a major role in our day to day life and its manipulation is increasing exponentially. This manipulation is known as Image forging. In this review paper, we will study image forging, its types and detection process.
International Journal IJRITCC
Forgery in digital images can be done by manipulating the digital image to conceal some meaningful or useful information of the image. It can be much difficult to identify the edited region from the original image in various cases. In order to maintain the integrity and authenticity of the image, the detection of forgery in the image is necessary. Adaption of modern lifestyle and advanced photography equipment has made tempering of digital image easy with the help of image editing soft wares. It is thus important to detect such image tempering operations. Different methods exist in literature that divide the suspicious image into overlapped blocks and extract some features from the images to detect the type of forgery that exist in the image. The image forgery detection can be done based on object removal, object addition, unusual color modifications in the image. Many existing techniques are available to overcome this problem but most of these techniques have many limitations. Images are one of the powerful media for communication. In this paper a survey of different types of forgery and digital image forgery detection has been focused.
Varsha Sharma
Varsha Sharma, Swati Jha , Dr. Rajendra Kumar Bharti Dept. of Computer Science and Engineering, BTKIT, Dwarahat, INDIA ---------------------------------------------------------------------***--------------------------------------------------------------------Abstract-Image forgery detection is emerging as one of the hot research topic among researchers in the area of image forensics. Many techniques have been suggested to detect such type of forgery with the original image, but the problem is not being solved. Some issues still remained either unsolved. Block matching algorithm or block tiling algorithm is the most commonly used method to detect the duplication in the image. One of the major challenges is the time complexity of such algorithms. In the proposed method this issue has been addressed without compromising the quality of the method. Discrete Cosine Transform (DCT) is used to represent the features of overlapping blocks.
International Journal of Advance Research in Computer Science and Management Studies [IJARCSMS] ijarcsms.com
IOSR Journal of Computer Engineering
Shivani Thakur
International Journal For Research In Applied Science & Engineering Technology
IJRASET Publication
'Image Forgery' is extremely pervasive in this universe of picture altering devices, for example, photoshop. As the picture is utilized for the verification processes, this is an extreme issue. Identification of a produced picture from the first one is an incredibly extreme assignment. The unaided eye can only with significant effort distinguish the altered territory from the actual Picture. Since it is indispensable to build up a technique that can differentiate the altered picture from the actual one. "Copy-Move Forgery" is a notable class of picture forgery, in which a specific piece of the picture is replicated and afterward stuck in a similar picture to conceal some significant info. "Copy-Move Forgery's" aim either making an object "imperceptible" or makes an additional picture of an item in a predefined area. This has immense application in the field of Information Security where the protection of information is of most extreme significance. This paper helps us to explore the forged region from the actual image using various techniques, which are discussed below.
IRJET Journal
RELATED PAPERS
Francisco Queiroz
Revista Escuela de Administración de Negocios
ENRIQUE DARÍO ROMERO Y CEJUDO
Taking Ethno-Cultural Diversity Seriously in Constitutional Design
Solomon Dersso
Annals of Tropical Research
Lolito Bestil
Electronic Research Archive
Edmundo Capelas de Oliveira
silvia fernandez
Journal of Biology, Agriculture and Healthcare
ADZEMI MAT ARSHAD
2013 IEEE International Symposium on Performance Analysis of Systems and Software (ISPASS)
Vincent Weaver
Journal of Molecular Biology
Bernard R. Glick
Dr. Adarsh Kumar
Annales d'Endocrinologie
Michael Fayon
kjgg fdfdgg
SSRN Electronic Journal
Joseph Jay Williams
Uniport Journal of Engineering and Scientific Research (UJESR)
Onyeka B E N J A M I N Onyeukwu , ovovwe diakparomre
Nuclear Instruments and Methods in Physics Research Section A: Accelerators, Spectrometers, Detectors and Associated Equipment
Karl-Heinz Kampert
出售澳洲斯威本科技大学毕业证 sut学位证书本科学位证书雅思证书原版一模一样
hyutrTT hytutr
Wilson Senne
Nature Medicine
Frederic Bertrand
Clinical Microbiology and Infection
Ferran Segura
Clinical Infectious Diseases
Masashi Mizokami
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
Detecting Moving Objects With Machine Learning
- Fraser, Wesley C.
The scientific study of the Solar System's minor bodies ultimately starts with a search for those bodies. This chapter presents a review of the use of machine learning techniques to find moving objects, both natural and artificial, in astronomical imagery. After a short review of the classical non-machine learning techniques that are historically used, I review the relatively nascent machine learning literature, which can broadly be summarized into three categories: streak detection, detection of moving point sources in image sequences, and detection of moving sources in shift and stack searches. In most cases, convolutional neural networks are utilized, which is the obvious choice given the imagery nature of the inputs. In this chapter I present two example networks: a Residual Network I designed which is in use in various shift and stack searches, and a convolutional neural network that was designed for prediction of source brightnesses and their uncertainties in those same shift-stacks. In discussion of the literature and example networks, I discuss various pitfalls with the use of machine learning techniques, including a discussion on the important issue of overfitting. I discuss various pitfall associated with the use of machine learning techniques, and what I consider best practices to follow in the application of machine learning to a new problem, including methods for the creation of robust training sets, validation, and training to avoid overfitting.
- Astrophysics - Earth and Planetary Astrophysics;
- Astrophysics - Instrumentation and Methods for Astrophysics;
- Computer Science - Machine Learning
Robust copy-move detection and localization of digital audio based CFCC feature
- Published: 10 May 2024
Cite this article

- Dongyu Wang 1 ,
- Xiaojie Li 2 ,
- Canghong Shi 1 ,
- Xianhua Niu 1 ,
- Ling Xiong 1 ,
- Hanzhou Wu 3 ,
- Qing Qian 4 &
- Chao Qi 1
40 Accesses
Explore all metrics
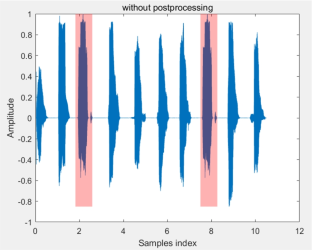
Copy-move forgery is a common audio tampering technique in which users copy the contents of one speech and paste them into another region of the same speech signal, thus achieving the effect of tampering with the semantics. To verify the authenticity of the audio, this paper proposes a method to detect and localize audio copy-move forgery based on the cochlear filter of cochlear filter cepstral coefficients (CFCC) feature. The pitch tracking algorithm is used to distinguish the voiced and unvoiced segments in the audio, and then the CFCC coefficients are extracted for each voiced segment. The CFCC feature simulates the entire transmission process of signals in the cochlear basilar membrane using wavelet transformation. Finally, we use Pearson correlation coefficients (PCCs) and dynamic time warping (DTW) in combination to compare the similarity of voiced segments, accurately determining the tampered locations in the audio through threshold judgment. Through extensive experiments on relevant datasets, this algorithm achieves a precision rate of 98.39% and a recall rate of 98.00% in detecting audio without post-processing. Even when detecting audio that has undergone different post-processing, the precision and recall rates remain above 90%. Compared to existing methods, this approach not only achieves precise localization of replicated segments but also demonstrates superior experimental results.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others
Robust copy-move detection in digital audio forensics based on pitch and modified discrete cosine transform
Detecting audio copy-move forgery with an artificial neural network
Speech watermarking robust against recapturing and de-synchronization attacks
Data availability statement.
The data that support the findings of this study are available from the corresponding author on reasonable request.
Khan MHK-KR, Zakariah MK (2018) A novel audio forensic data-set for digital multimedia forensics. Aust J Forensic Sci 50(5)
Bourouis S, Alroobaea R, Alharbi AM, Andejany M, Rubaiee S (2020) Recent advances in digital multimedia tampering detection for forensics analysis. Symmetry 12(11)
Zakariah M, Khan MK, Malik H (2018) Digital multimedia audio forensics: past, present and future. Multimed Tools Appl 77:1009–1040
Article Google Scholar
Bevinamarad PR, Shirldonkar MS (2020) Audio forgery detection techniques: present and past review
Zhao H, Chen Y, Wang R, Malik H (2016) Audio splicing detection and localization using environmental signature. Multimed Tools Appl 76(12)
Zhang X, Cui Y, Wang Y, Sun M, Hu H (2018) An improved ae detection method of rail defect based on multi-level anc with vss-lms. Mech Syst Signal Process 99:420–433
Xiao J-N, Jia Y-Z, Fu E-D, Huang Z, Li Y, Shi S-P (2014) Audio authenticity: duplicated audio segment detection in waveform audio file. J Shanghai Jiaotong Univ Sci 19:392–397
Imran M, Ali Z, Bakhsh ST, Akram S (2017) Blind detection of copy-move forgery in digital audio forensics. IEEE Access 5:12843–12855
Kucukugurlu B, Ustubioglu B, Ulutas G (2020) Duplicated audio segment detection with local binary pattern. In: 2020 43rd International conference on telecommunications and signal processing (TSP)
Xie Z, Lu W, Liu X, Xue Y, Yeung Y (2018) Copy-move detection of digital audio based on multi-feature decision. J Inf Secur Appl 43:37–46
Google Scholar
Liu Z, Lu W (2017) Fast copy-move detection of digital audio. In: 2017 IEEE Second International conference on data science in cyberspace (DSC), IEEE, pp 625–629
Li C, Sun Y, Meng X, Tian L (2019) Homologous audio copy-move tampering detection method based on pitch. In: 2019 IEEE 19th International conference on communication technology (ICCT), IEEE, pp 530–534
Wang F, Li C, Tian L (2017) An algorithm of detecting audio copy-move forgery based on dct and svd. In: 2017 IEEE 17th International conference on communication technology (ICCT), IEEE, pp 1652–1657
Mannepalli K, Krishna P, Krishna K, Krishna K (2019) Copy and move detection in audio recordings using dynamic time warping algorithm. Int J Innov Technol Explor Eng 9(2):2244–2249
Akdeniz F, Becerikli Y (2021) Detection of copy-move forgery in audio signal with mel frequency and delta-mel frequency kepstrum coefficients. In: 2021 Innovations in intelligent systems and applications conference (ASYU), IEEE, pp 1–6
Yan Q, Yang R, Huang J (2015) Copy-move detection of audio recording with pitch similarity. In: 2015 IEEE International conference on acoustics, speech and signal processing (ICASSP), IEEE, pp 1782–1786
Yan Q, Yang R, Huang J (2019) Robust copy-move detection of speech recording using similarities of pitch and formant. IEEE Trans Inf Forensics Secur 14(9):2331–2341
Ustubioglu B, Küçükuğurlu B, Ulutas G (2022) Robust copy-move detection in digital audio forensics based on pitch and modified discrete cosine transform. Multimed Tools Appl 81(19):27149–27185
Maksimovic M, Cuccovillo L, Aichroth P (2019) Copy-move forgery detection and localization via partial audio matching. In: Audio engineering society conference: 2019 AES International conference on audio forensics. Audio Engineering Society
Ulutas G, Tahaoglu G, Ustubioglu B (2022) Forge audio detection using keypoint features on mel spectrograms. In: 2022 45th International conference on telecommunications and signal processing (TSP), IEEE, pp 413–416
Ustubioglu B, Tahaoglu G, Ulutas G, Ustubioglu A, Kilic M (2023) Audio forgery detection and localization with super-resolution spectrogram and keypoint-based clustering approach. J Supercomput 1–33
Ustubioglu B, Tahaoglu G, Ulutas G (2023) Detection of audio copy-move-forgery with novel feature matching on mel spectrogram. Expert Syst Appl
Kinnunen T, Rajan P (2013) A practical, self-adaptive voice activity detector for speaker verification with noisy telephone and microphone data. In: 2013 IEEE International conference on acoustics, speech and signal processing, IEEE, pp 7229–7233
Drugman T, Alwan A (2019) Joint robust voicing detection and pitch estimation based on residual harmonics
Dong B (2017) Characterizing resonant component in speech: a different view of tracking fundamental frequency. Mech Syst Signal Process 88:318–333
Dang X, Wang F, Zhang X (2019) Cochlear filter cepstral coefficients of acoustic signals for mechanical faults identification of power transformer. In: 2019 IEEE Sustainable power and energy conference (iSPEC), IEEE, pp 1195–1200
Shi Y, Bai J, Xue P, Shi D (2019) Fusion feature extraction based on auditory and energy for noise-robust speech recognition. IEEE Access 7:81911–81922
Li Q, Huang Y (2010) An auditory-based feature extraction algorithm for robust speaker identification under mismatched conditions. IEEE Trans Audio Speech Lang Process 19(6):1791–1801
Kumaran U, Radha Rammohan S, Nagarajan SM, Prathik A (2021) Fusion of mel and gammatone frequency cepstral coefficients for speech emotion recognition using deep c-rnn. Int J Speech Technol 24:303–314
Download references
Acknowledgements
This study was supported by the Sichuan Science and Technology program (Grant nos. 2023NSFSC0470, 2023ZHCG0018), and the National Natural Science Foundation of China (NSFC) program (No.62171387).
Author information
Authors and affiliations.
School of Computer and Software Engineering, Xihua University, Chengdu, 610039, People’s Republic of China
Dongyu Wang, Canghong Shi, Xianhua Niu, Ling Xiong & Chao Qi
The College of Computer Science, Chengdu University of Information Technology, Chengdu, 610225, People’s Republic of China
School of Information, Shanghai University, Shanghai, 200444, China
School of Information, Guizhou University of Finance and Economics, Guiyang, 550000, China
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Canghong Shi .
Ethics declarations
Conflict of interest.
The authors declare that they have no known financial interests or personal relationships that might influence the work reported in this paper.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Wang, D., Li, X., Shi, C. et al. Robust copy-move detection and localization of digital audio based CFCC feature. Multimed Tools Appl (2024). https://doi.org/10.1007/s11042-024-19346-x
Download citation
Received : 20 June 2023
Revised : 02 March 2024
Accepted : 30 April 2024
Published : 10 May 2024
DOI : https://doi.org/10.1007/s11042-024-19346-x
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Digital audio
- Cochlear filter cepstral coefficient
- Pearson correlation coefficients
- Find a journal
- Publish with us
- Track your research

COMMENTS
In the last years, due to the availability and easy of use of image editing tools, a large amount of fake and altered images have been produced and spread through the media and the Web. A lot of different approaches have been proposed in order to assess the authenticity of an image and in some cases to localize the altered (forged) areas. In this paper, we conduct a survey of some of the most ...
Digital images can be forged by various techniques. Existing techniques for digital image forgery detection can be broadly classified into two major categories: active/non-blind approach and passive/blind approach [6], [7], [8].These categories and their sub-categories are depicted in Fig. 1.. Active approach: In the active approach, the image is pre-processed and information is embedded into ...
versus four types of image forgery detection techniques (copy-mov e, image splicing, resampling, retouching) for last two decades, over the years 1998-2017, collected from Google Scholar.
Contrary to the traditional methods of forgery detection, a deep learning model automatically builds the required features, hence it has become the new area of research in image forgery. The paper initially discusses various types of image forgery techniques and later on compares different approaches involving neural networks to identify forged ...
This image was shared thousands of times on different social media and news portals, which caused a lot of confusion and discussion. This forgery image can force political leaders to make wrong decisions and political movements, and even start a nuclear war [5]. Therefore, forgery detection is one of the important topics of machine vision.
A comprehensive overview of active and passive forgery methods is analyzed by systematically surveying the literature. This study finds a wide scope of Deep Learning based methods in Passive Image Forgeries, ranging from pixel-based to geometric-based detection. ... Deriche M (2014) A review on copy move image forgery detection techniques. In ...
López-García X, Silva-Rodríguez A, Vizoso-García AA, Oscar W, Westlund J (2019) Mobile journalism: systematic literature review. Comunicar Media Educ Res J 27(1). DOI ... Qureshi MA Deriche M A bibliography of pixel-based blind image forgery detection techniques Signal Process Image Commun 2015 39 46 74 10.1016/j.image ...
In the last decades, deep learning (DL) has emerged as a powerful and dominant technique for solving challenging problems in various fields. Likewise, in the field of digital image forensics, a large and growing body of literature investigates DL-based techniques for detecting and classifying tampered regions in images. This article aims to provides a comprehensive survey of state-of-the-art ...
Section 2 provides a literature review of image forgery detection methodologies. Section 3 introduces the proposed framework for detecting the presence of forgeries in an image. Section 4 contains a discussion of the experimentation and the results achieved. Finally, in Section 5, we summarize the conclusions.
In this survey, we mainly review forgery detection algorithms based on deep learning. 2.1.1. Basic Framework of Image Forgery Detection. ... There are still difficulties in the detection of tampered image metadata: the literature points out that the open-source ExifTool is applied to access and modify image metadata between digital workflows ...
The purpose of digital image manipu-. lation detection approaches is to detect the forgeries in an image. Digital image. manipulation detection techniques can be broadly divided into two main ...
1.1 Image forgery detection applications. Image forgery detection can mainly be divided into two categories: active and passive. Sometimes these methods also give a localization of the altered/forged areas of the image, and even provide an estimate of the original visual content.
Pixel-based image forgery detection: Pixel-based techniques emphasize on the pixels of the digital image. These techniques are roughly categorized into four types. We are focusing only two types of techniques copy-move and splicing in this paper. This is one of the most common forgery detection techniques. Figure 2.
by. SVM is the most machine learning technique used for forgery detection for its accuracy and because it performs well on datasets with limited number of samples. Nevertheless, recent works such as [12] use deep learning. CASIA, COMOFOD and UCID image databases are the most used sets in this field.
A Timely Survey on Vision Transformer for Deepfake Detection. This survey identifies ViT-based deepfake detection as a cutting-edge research direction, highlighting the need for a timely literature review to keep up with rapidly evolving ViT-based approaches. of a total of 14 ViT-based deepfake detection models categorized into standalone ...
Literature shows that passive image forgery detection is more significant than the active approach; therefore, in level 1 passive approach is used to make a decision.
The number of scholars has also increased many a folds. Literature presenting reviews on image forgery techniques holds importance for the scholars" endeavoring in the field of image forgery detection. The updating the literature review also is an important aspect of the field with the fast developments in the field.
To conduct a detailed literature review on image forgery detection method and related Technologies. 3. To ensure that the detection model is robust and can effectively identify forgeries in images with varying levels of complexity, quality, and resolution. 4. To Develop a user interface that allows users to easily upload images and view forgery ...
Literature Review: Detection of Image Splicing Forgery Araz Rajab Abrahim1, Mohd Shafry Mohd Rahim1,2 and Ghazali bin Sulong3. 1. Faculty of Computing, Universiti Teknologi Malaysia, Skudai, 81310, Johor Bahru, Malaysia. ... IFDS (Image Forgery Detection System) is a type of PRS (Pattern Recognition System) whose purpose is to allocate
Abstract. Aerial object detection, as object detection in aerial images captured from an overhead perspective, has been widely applied in urban management, industrial inspection, and other aspects. However, the performance of existing aerial object detection algorithms is hindered by variations in object scales and orientations attributed to ...
After a short review of the classical non-machine learning techniques that are historically used, I review the relatively nascent machine learning literature, which can broadly be summarized into three categories: streak detection, detection of moving point sources in image sequences, and detection of moving sources in shift and stack searches.
Copy-move forgery is a common audio tampering technique in which users copy the contents of one speech and paste them into another region of the same speech signal, thus achieving the effect of tampering with the semantics. To verify the authenticity of the audio, this paper proposes a method to detect and localize audio copy-move forgery based on the cochlear filter of cochlear filter ...