Removing Unknown Azure RBAC Role Assignments with PowerShell
5 minute read
Ever wondered how to programmatically find and remove Azure RBAC role assignments of ‘Unknown’ ObjectType, at scale, in your Azure subscription?
In this blog I’ll describe the problem using an example scenario and then show you a scripted solution using PowerShell.

Unknown Role Assignments with Identity Not Found
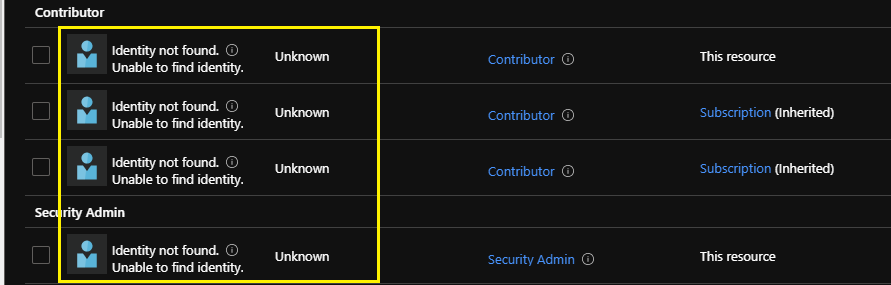
Looking at Access Control (IAM) role assignments within the Azure portal, you might’ve noticed that a security principal is listed as “Identity not found” with an “Unknown” type.
There’s 2 possible reasons this can occur:
- You recently invited a user when creating a role assignment
- You deleted a security principal that had a role assignment
Note - a security principal can be a:
- Service Principal
- Managed Identity
Example Scenario of How This Can Occur
Let’s examine an example scenario for the 2nd possible reason listed above: You deleted a security principal that had a role assignment.
Imagine you’re testing Azure policy definitions using ‘deployIfNotExists’ or ‘modify’ effects - a managed identity needs to be created because that’s how Azure policy has the required permissions to action those effects specified in your policy definitions.
In the screenshot below you can see a managed identity will be created automatically as part of the task to assign a policy initiative. So far, so good!
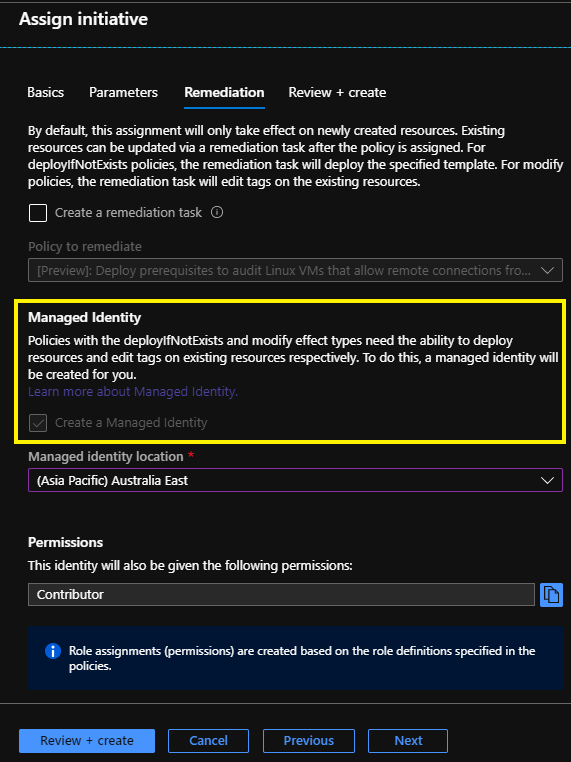
Now this new managed identity will also have a corresponding RBAC role assignment created on the scope defined by the policy assignment.
So if you are assigning your policy to the subscription scope a role assignment will be applied at the subscription level.
If, later on, you delete that policy assignment the managed identity will also automatically get deleted, which makes sense, because you might not need that managed identity ever again - but wait, for some reason the RBAC role assignment still exists for the deleted managed identity.
This leaves you with a security principal on the Access Control (IAM) role assignments page that displays as “Identity not found” with an “Unknown” type. Not harmful, I think, but also not a clean/tidy experience to encounter.
My hope is that Microsoft identify this as a problem and resolve it - so I’ve reached out to the Azure Policy Program Managers via Twitter…
TIL - via testing #AzurePolicy Assignments using DeployIfNotExists/Modify effects - a Managed Identity is created. If I delete the #AzurePolicy Assignment the Managed Identity is also deleted - BUT the RBAC Role Assignment still exists for the Managed Identity. Oops :) — Jesse Loudon (@coder_au) May 18, 2020
Finding Role Assignments of ‘Unknown’ ObjectType with PowerShell
There’s no current method I know of to easily find and remove these ‘Unknown’ type role assignments via the Azure Portal without doing a bunch of clicking.
So to programmatically discover Azure RBAC role assignments of the ‘Unknown’ type we can use the Get-AzRoleAssignment cmdlet:
Above you can see we are searching on the ObjectType field matching the value ‘Unknown’.
An example output of the above cmdlet is shown below.
You may have noticed above that the values for DisplayName and SignInName are null (empty) and that ObjectType equals ‘Unknown’. This is clear indication that you’ve found a role assignment where the corresponding security principal has either been deleted, or a security principal has been invited (while the role assignment was created) and has not yet replicated across regions.
Removing Role Assignments of ‘Unknown’ ObjectType with PowerShell
To programmatically remove Azure RBAC role assignments of the ‘Unknown’ type we can use the Remove-AzRoleAssignment cmdlet.
Please note:
- When removing a role assignment you’ll need to specify the ObjectID, RoleDefinitionName and Scope
- You’ll also need Microsoft.Authorization/roleAssignments/delete permissions, such as User Access Administrator or Owner
- Always test your scripts in a development environment first before using in production.
The PowerShell script above does the following:
- Finds all Azure role assignments in the subscription where ObjectType equals ‘Unknown’
- Exports the results to CSV where you can review/send off for ITSM approvals, etc
- Imports the results from CSV and sets variables for the required fields needed to remove a role assignment (ObjectID, RoleDefinitionName and Scope)
- Uses a for each loop to remove each role assignment specified from the imported CSV
For the simplest removal script without any authentication or CSV export/import for documentation purposes, you can use the following PowerShell script:
Closing Remarks
Finding and removing Azure RBAC role assignments might not be a common occurence for your team but I think it’s important to share with the community how to complete a task like this programmatically.
I came across this problem during my testing of Azure policy assignments, which use a managed identity for certain effects, and would’ve never thought to look for these role assignments otherwise.
If you don’t look, you’ll never find :)
Leave a comment
You may also enjoy.

Flexing your Security Governance with Azure Policy as Code
3 minute read
I recently had the pleasure of presenting a livestream session via Microsoft Reactor Sydney on a subject close to my heart.

Talking Azure Policy as Code on CtrlAltAzure podcast
4 minute read
Appearing as a guest on the Ctrl+Alt+Azure podcast to talk Azure Policy as Code with hosts Tobias Zimmergren and Jussi Roine

How to Win vs Azure Policy Non-Compliance
Fixing a design flaw with the existenceCondition for builtin policies
HashiTalks ANZ: DRY Coding with Terraform, CSVs, ForEach
How combining Terraform with CSVs and ForEach we can deploy at scale from large datasets

Contribute to the Microsoft 365 and Office forum! Click here to learn more 💡
April 9, 2024
Contribute to the Microsoft 365 and Office forum!
Click here to learn more 💡
Subscription, account, billing Top Forum Contributors: NoOneCan - Dillon Silzer - Stefan Blom 👍✅
April 17, 2024
Subscription, account, billing Top Forum Contributors:
NoOneCan - Dillon Silzer - Stefan Blom 👍✅
- Search the community and support articles
- Microsoft 365 and Office
- Subscription, account, billing
- Search Community member
Ask a new question

Enable-OrganizationCustomization cmdlet failed
I am trying to enable organization customization to set roles in our office 365 tenant. To enable I ran following
Install-Module ExchangeOnlineManagement -Force -Scope AllUsers Connect-ExchangeOnline -UserPrincipalName <UPN> -ShowProgress $true Enable-OrganizationCustomization
When I ran " Enable-OrganizationCustomization" I am getting following error.
The role assignment policy "Default Role Assignment Policy" wasn't found. Make sure that you typed the identity correctly
Need help on what needs to be done to create the role assignment policy
Report abuse
Replies (6) .
- Microsoft Agent |
Hello Shahir (iMemori),
Welcome to Microsoft community.
To replace the built-in default role assignment policy with your own default role assignment policy, you can use the Set-RoleAssignmentPolicy cmdlet to select a new default. When you do this, any new mailboxes are assigned the role assignment policy you specified by default if you don't explicitly specify a role assignment policy. More information can be found in the article below:
https://technet.microsoft.com/en-us/library/dd638090(v=exchg.160).aspx
Best regards,
Was this reply helpful? Yes No
Sorry this didn't help.
Great! Thanks for your feedback.
How satisfied are you with this reply?
Thanks for your feedback, it helps us improve the site.
Thanks for your feedback.
How is it going? I haven’t heard back from you, if there’s anything I can help you, please do not hesitate to contact me.
You guys and your non-answers...
Ran into this today trying 'Enable-OrganizationCustomization". Here is what I have tried.
new-roleassignmentpolicy -Name "Temporary Policy"
The command you tried to run isn't currently allowed in your organization. To run this command, you first need to run
the command: Enable-OrganizationCustomization.
(edited for brevity)
So I cant create a new policy...
Remove-RoleAssignmentPolicy "Default Role Assignment Policy"
And I cant remove the policy...
Get-roleassignmentpolicy -identity "Default Role Assignment Policy"
RunspaceId : 4646e0f2-9546-4069-9df5-dfaec294f2f0
IsDefault : True
Description : This policy grants end users the permission to set their options in Outlook on the web and perform
other self-administration tasks.
RoleAssignments : {My Marketplace Apps-Default Role Assignment Policy, MyTeamMailboxes-Default Role Assignment
Policy, MyProfileInformation-Default Role Assignment Policy, MyTextMessaging-Default Role
Assignment Policy...}
AssignedRoles : {My Marketplace Apps, MyTeamMailboxes, MyProfileInformation, MyTextMessaging...}
AdminDisplayName :
ExchangeVersion : 0.11 (14.0.509.0)
Name : Default Role Assignment Policy
So the policy "Enable-OrganizationCustomization" errors on ("Default Role Assignment Policy") does exist. But I cannot create new nor delete policies because 'organization customization' is not on.
Circular logic at its finest...
Any other suggestions?
Just a follow up for anyone looking at this later. After 24 hours I was able to create a temporary role assignment policy. I was still unable to do other functions though (such as enable admin audit logging).
After 48 hours I can perform / enable all functions related to Organization Customization.
So it looks like it can take up to 48 hours to enable Organization Customization on 'mature' tenants. This specific instance was on a ~1 year old account that we recently took over management of.
3 people found this reply helpful
I found running Set-ExecutionPolicy Unrestricted fixes the problem, and no need to wait 48 hours for the changes to take place
10 people found this reply helpful
This working for me in sep 2021, thanks @ dionisvozian !!!
Question Info
- Norsk Bokmål
- Ελληνικά
- Русский
- עברית
- العربية
- ไทย
- 한국어
- 中文(简体)
- 中文(繁體)
- 日本語
Search code, repositories, users, issues, pull requests...
Provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement . We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
az role assignment delete fails if the assignee principal no longer exists #20349
jiasli commented Nov 16, 2021 • edited
- 👍 1 reaction
jiasli commented Nov 16, 2021
This behavior has been there since 2016-07-27 ( #553 ) and the error message was later polished by #12617 .
I am not sure if changing this behavior is a good idea, as it also affects
- az role assignment create
- az role assignment list
as _resolve_object_id_and_type is also called by these commands: non-existing objectId results in failure. Changing this behavior will certainly be a breaking change.
Please use --ids argument to delete the role assignment if assignee doesn't exist anymore, such as:
Sorry, something went wrong.
ShachafGoldstein commented Dec 15, 2021
lucashby commented Jan 25, 2024 • edited
No branches or pull requests
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Common errors returned for a new request
- 3 contributors
Following is a list of common errors that you may encounter while creating a new request and how to mitigate them.
Additional resources

IMAGES
VIDEO
COMMENTS
The assignment policy you want to remove can't be assigned to any mailboxes or management roles. Also, if you want to remove the default assignment policy, it must be the last assignment policy. Do the following before you attempt to remove an assignment policy: Use the Set-Mailbox cmdlet to change the assignment policy for any mailbox assigned the assignment policy you want to remove. If the ...
After such then switch to the subscription you are looking to run by Select-AzureSubscription like: Select-AzureSubscription -SubscriptionName <SUBSCRIPTION NAME>. Then run the Get-AzRoleAssignment like: Get-AzRoleAssignment -RoleDefinition ROLENAME. If this returns a list then run the Remove-AzRoleAssignment for each Object ID returned:
Hi, wonder if anyone can help. I have a user with 3 'default role assignment policies' set in Office365 under the Exchange admin section (permissions > user roles). There should only be one such policy. This is causing a problem when I setup new users with a mailbox - I see the message below and their mailbox setup never completes. I can't work out how to remove the 2 other policies (we ...
Hi Team, My customer contacted me today as they had this issue where they were trying to remove an RBAC admin assignment on PowerShell but kept seeing the response Remove-AzRoleAssignment: Cannot delete the last RBAC admin assignment I c...
Automated RBAC diagnostic checks. To help troubleshoot RBAC issues faster, we have now released two automated self-serve diagnostic checks that you can use when troubleshoot Exchange Online RBAC issues for your users. You can launch the diagnostic as an Administrator by either clicking on the below buttons or going to Help & Support in ...
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window.
Jesse Loudon • 2 years ago. Hey there, thanks for the heads up, I just tested this end to end and found. 1 - An orphaned role assignment still shows ObjectType as 'Unknown'. 2 - Running the PowerShell script shown in this article still works to cleanup/remove these orphaned role assignments. Cheers.
Failed to remove Role assignment(s). Failed to remove as <role_name> for <resource_name>: The scope <role_assignment_resourceid> cannot perform delete operation because following scope(s) are locked: . ... A cannot-delete lock on a resource prevents the deletion of Azure RBAC assignments.
With the use of the JSON payload that is sent to the Function, a PowerShell script is executed to remove the unauthorized Role Assignment. To do so, the Function App uses a System-assigned Managed Identity that has the permissions to remove Role Assignments. With the solution overview out of the way, let's have a look at how the solution ...
To replace the built-in default role assignment policy with your own default role assignment policy, you can use the Set-RoleAssignmentPolicy cmdlet to select a new default. When you do this, any new mailboxes are assigned the role assignment policy you specified by default if you don't explicitly specify a role assignment policy.
Add or remove roles from a role assignment policy. Step 1: Sign in to Office 365 admin center. Step 2: Navigate to the Exchange admin center. Step 3: Go to Permissions > User roles, select the role assignment policy, and then click Edit. Step 4: Select the check box next to the role. Step 5: Click Save. Need Support?
az role assignment create; az role assignment list; as _resolve_object_id_and_type is also called by these commands: non-existing objectId results in failure. Changing this behavior will certainly be a breaking change. Workaround. Please use --ids argument to delete the role assignment if assignee doesn't exist anymore, such as:
Delete role assignments. (autogenerated) az role assignment delete --assignee 00000000-0000-0000-0000-000000000000 --role "Storage Account Key Operator Service Role" Optional Parameters--assignee. Represent a user, group, or service principal. supported format: object id, user sign-in name, or service principal name.
This is a list of common errors that you may encounter while creating a new request through Azure Privileged Identity Management API and how to mitigate them
Role assignment creation failed. why did role assiment creation failed? How to solve this? azure; Share. Improve this question. Follow edited Nov 11, 2023 at 18:55. MikiBelavista. asked Nov 11, 2023 at 18:42. ... Temporary policy: Generative AI (e.g., ChatGPT) is banned.