Cisco Secure Endpoint (AMP) - An Introduction to Cisco Secure Endpoint (AMP)

Summary Cisco Secure Endpoint (AMP) is an advanced endpoint protection software which is supported and monitored by a central console. Secure Endpoint ( AMP) is an application that monitors the machine on which it is installed, searching for suspicious activity. Endpoints with Secure Endpoint ( AMP) clients installed will report back to a central console, where IT administrators can view events, set up alerts, and get an overview of the volume of suspicious activity occurring on their network. Finally, Secure Endpoint ( AMP) also provides traditional Anti-Virus scanning through Tetra (Windows) and Clam AV (Mac & Linux) which can be enabled via policy settings within the console.

- Customizable Endpoint Protection: Secure Endpoint (AMP) can be configured to either be in audit or protect modes, or a mix of both depending on the type of event.
- Can be installed on many host types: Laptop, desktop, server, virtual machine.
- Real time data: Extracts and consolidates endpoint event data, and checks in with the console to report events as they occur.
- Easy installation: can be automated.
- Built-in antivirus scanner: The Secure Endpoint (AMP) application comes with a built-in anti-virus scanner (Tetra & Clam AV) that can be activated & deactivated from within the console, which allows for offline endpoint scanning.
Advantages of using Cisco Secure Endpoint (AMP):
- Secure Endpoint (AMP) is a powerful tool for the end user and the IT administrator as both can see events as they occur.
- Quick event reporting and notifications allow IT administrators to address a malicious event quickly before further damage can occur.
- When in Protect Mode AMP can immediately stop malicious activity in its tracks.
- Easily greenlist applications that are friendly in the case that they are flagged as suspicious by AMP.
Event Types Monitored:
- Threats (rootkits, malicious activity, suspicious system activity, etc.)
- Indications of compromise (multiple infected files, dropper infection, suspicious download, ransomware, Cloud IOCs, etc.)
- Quarantine status
- Endpoint status
- Miscellaneous events (vulnerable application detected, application installed, application uninstalled)
Secure Endpoint (AMP) FAQ
- What does the Secure Endpoint (AMP) Endpoint Connector (client) do exactly? The Endpoint Connector sits on the endpoint, monitoring for and potentially blocking malicious/suspicious activity. If the machine is connected to the internet, the connector will send event information to the console for easy management.
- How quickly does the console receive event information from endpoints? So long as the machine is connected to the internet, the endpoint connector will send information to the console as events occur. This means that the console is aware of events within minutes of their occurrence.
- How do I stay up to date on events occurring in my environment? You can configure the console to send alerts and reports to your email in real time, or on an aggregated hourly/daily/weekly basis. Additionally, you can log in to the console to monitor events on your environment. See the following KB article to learn about setting up alerts and reports: https://kb.wisc.edu/internal/page.php?id=89843
- How can I get set up on the console? If your IT group already has access to the AMP console and you're looking for account access for yourself, use the following KB to request access to the console: https://kb.wisc.edu/internal/page.php?id=89544 If you are the first person in your IT group to request access to the console, you will need follow the steps in this kb to get a new group and account provisioned in AMP: https://kb.wisc.edu/internal/page.php?id=89564
What Operating Systems are supported by Secure Endpoint (AMP) Endpoint Connector?
- Microsoft https://www.cisco.com/c/en/us/support/docs/security/amp-endpoints/214847-amp-for-endpoints-windows-connector-os-c.html
- Windows 8, 8.1
- Windows Server 2008 R2, 2012, 2012 R2, 2016, 2019, 2022
- Linux https://www.cisco.com/c/en/us/support/docs/security/amp-endpoints/215163-amp-for-endpoints-linux-connector-os-com.html
- Red Hat Enterprise Linux or CentOS 6.4-6.10, 7.x & 8.x
- Ubuntu/Debian 18.04, 20.04
- Oracle Linux
- Amazon Linux 2
- AlmaLinux 8.3-8.5
- Rocky Linux 8.4-8.5
- SUSE Linux 15 SP0 - 15 SP3
- Android 8, 9, 11
- Apple https://www.cisco.com/c/en/us/support/docs/security/amp-endpoints/214849-amp-for-endpoints-mac-connector-os-compa.html
- iOS 12 and above (requires compatible Mobile Device Management tool to deploy and configure)
- MacOS 10.13, 10.14, 10.15, 10.16/11.0 ,12
- How often should I update Secure Endpoint (AMP) endpoint clients? It is recommended to regularly check for AMP Connector updates (perhaps on a monthly basis) to ensure that Secure Endpoint (AMP) is functioning as it should. Secure Endpoint (AMP) connectors can be updated through the Secure Endpoint (AMP) console, which is often the most convenient method of updating. For instructions on how to update the Secure Endpoint (AMP) endpoint connectors see the KB article Updating Endpoint Clients .
- It's too good to be true. Are there any disadvantages of doing this? Secure Endpoint (AMP) is a very powerful tool, but it needs to be configured correctly. For instance, Secure Endpoint (AMP) does not mix well with other endpoint protection software or anti-virus software unless these applications are greenlisted from within the console. Occasionally, Secure Endpoint (AMP) can flag benign files as suspicious but this can be easily remedied by adding file exclusions through the console
- What if I'm not sure that an event flagged by Cisco Secure Endpoint (AMP) is malicious or not? Cisco Secure Endpoint (AMP) offers a variety of methods for investigating files and events. See the KB article here for more information on investigating an event: https://kb.wisc.edu/internal/page.php?id=90059
- What can I do once I confirm an event was malicious? If the Cisco Secure Endpoint (AMP) Endpoint Connector is set to protect mode, it will generally have already killed the malicious process or quarantined the suspicious file. If the Endpoint Connector is set to Audit mode you will have to follow up on the suspicious activity on the endpoint yourself. However, even if you have protect mode on, it is still generally a good idea to follow up on suspicious activity as having one malware infection can often lead to others.
- Hey! I'm certain this file or event flagged by Secure Endpoint (AMP) is a false positive! When this occurs, the best way to address this issue is to add the file to the exclusion list or the application to the greenlist. See instructions on how to do so here: https://kb.wisc.edu/internal/page.php?id=89648
- My endpoints are already running an anti-virus application. Should I use Secure Endpoint (AMP) along with it or as a replacement for it? Secure Endpoint (AMP) can work quite well when used in tandem with another anti-virus application. In most cases we would recommend using both AMP and additional anti-virus software if you already have other AV software installed on your endpoints. However, if the proper exclusions are not configured in Secure Endpoint (AMP), it is not uncommon for Secure Endpoint (AMP) to identify anti-virus activity as malicious activity. As such, it is important to make sure that the anti-virus executable and file folders are listed as exclusions (items not to take action on or monitor) in the Secure Endpoint (AMP) console.
- What is the usage footprint of AMP on the endpoint? Will it bog the endpoint down? For most machines AMP has a quite minimal footprint, and should not typically slow the endpoint down. However, if the endpoint is a server or processes a lot of data on a regular basis, it will be necessary to configure filepath exclusions for high-volume filepaths to keep the AMP resource footprint low.
- Who manages the Cisco Secure Endpoint (AMP) console, me or DoIT? As an IT administrator, you generally have control over the policies, exclusions, and greenlists for your department. You can request access to the console and request DoIT to create a console group for your endpoints. At this time DoIT does not mandate any particular Secure Endpoint (AMP)configurations, so you will generally have full autonomy as the Secure Endpoint (AMP) administrator for your managed area. To request the creation of a new group in the Secure Endpoint (AMP) console: https://kb.wisc.edu/internal/page.php?id=89564 To request access to the console: https://kb.wisc.edu/internal/page.php?id=89544
- Where can I get more information? See the KB articles found here for more information: https://kb.wisc.edu/search.php?q=cisco+amp If you have additional questions, please contact [email protected] .
| Keywords | amp cisco endpoint connector advanced malware protection threat FAQ frequently asked questions getting started beginner's guide AV software antivirus secure endpoint | Doc ID | 90958 |
|---|---|---|---|
| Owner | Rachel L. | Group | Cybersecurity |
| Created | 2019-04-10 15:29:01 | Updated | 2024-06-04 13:03:14 |
| Sites | DoIT Departmental Support, DoIT Help Desk, Office of Cybersecurity | ||
| Feedback | 0 2 | ||
Cisco Blogs / Security / Prevent, Detect and Respond with Cisco AMP for Endpoints


Prevent, Detect and Respond with Cisco AMP for Endpoints
John dominguez.
Cyberattacks are ever evolving to circumvent and evade “protection-only” technologies. Despite your best efforts to protect against compromise, a persistent attacker will eventually breach your defenses and get inside. Then what? IT security teams need to automatically detect a threat when it gets in. They need to know where it came from, how it entered, where it has been, what it is doing, and how to contain and remediate it before data is stolen and damage is done.
The good news for IT security teams is that next generation capabilities that go beyond protection, to also include automated detection and response, are rapidly emerging. The convergence of these capabilities marks a next generation in endpoint security.
Cisco AMP for Endpoints provides next generation capabilities to prevent, detect, and respond to cyberattacks quickly and effectively.

Prevent: AMP for Endpoints blocks malware and helps strengthen endpoints from attack:
- Global Threat Intelligence – Prevention starts with strengthening your defenses using the best global threat intelligence so you can block malware as new threats emerge. Cisco’s team of threat researchers continuously feed threat intelligence into AMP for Endpoints so customers are protected 24/7.
- Malware Blocking – AMP for Endpoints uses a framework of complementary detection engines, including one-to-one signatures, fuzzy fingerprinting, machine learning, and an AV detection engine—all working together to catch and block malware before it can execute.
- File Sandboxing – A built-in sandbox automatically analyzes unknown files against over 700 behavioral indicators to detect malicious files and automatically block and quarantine them.
- Proactive Protection – Closing attack pathways before they can be exploited is a key strategy for preventing compromise. AMP’s vulnerable software feature shows you all the software on your endpoints that can be exploited, with the ability use application control to harden against attacks. AMP’s low prevalence capability detects targeted malware and prevents it from slipping under the detection radar.
One of the key tenets of a next generation endpoint security solution is the ability to go beyond prevention, since no prevention method will ever catch 100% of threats, 100% of the time.
Detect: That’s why AMP continually monitors all activity on your endpoints to quickly spot malicious behavior, detect indicators of compromise, and drastically decrease time to detection.
- Continuous Monitoring and Analysis – Once a file lands on the endpoint, AMP for Endpoints continues to watch, analyze, and record all file activity, regardless of the file’s disposition. If malicious behavior is detected at some point in the future, AMP can automatically block the file across all endpoints, and show the security team the entire recorded history of the malware’s behavior. You can see where it came from, where it’s been, and what it’s doing across all of your endpoints: PC, Mac, Linux, mobile devices. This helps you understand the full scope the compromise and quickly respond.
- Agentless Detection – AMP for Endpoints delivers agentless detection, a unique capability that detects compromise across customer environments, even if a host does not (or cannot) have an agent installed. Using Cisco’s Cognitive Threat Analytics (CTA) technology, AMP inspects web proxy logs to uncover things like memory-only malware and infections that live in a web browser only.
- File-less detection – Get visibility into what command line arguments are used to launch executables to determine if legitimate applications, including Windows utilities, are being used for malicious purposes. For instance, see if vssadmin is being used to delete shadow copies or disable safe boots; see PowerShell-based exploits; see into privilege escalation, modifications of access control lists (ACLs), and attempts to enumerate systems.
Respond: AMP for Endpoints provides a suite of response capabilities to quickly contain and eliminate threats across all endpoints, before damage can be done.
- Threat Hunting Made Easy: Accelerate investigations and reduce management complexity by easily searching for threats across all endpoints using AMP’s simple, cloud-based UI. Search across the cloud and the endpoint to see file, telemetry, IoC, and threat intelligence data. Uncover artifacts left behind as part of the malware ecosystem. These capabilities let you quickly understand the context and scope of an attack so you can stop it fast.
- Surgical, Automated Remediation: When AMP sees a threat, it automatically contains and remediates it across all of your endpoints: PCs, Macs, Linux, and mobile devices. Instantly, full-stop. No need to wait for a content update. Also, with just a few clicks, you can block a specific file across all or selected systems; block families of polymorphic malware; contain a compromised application being used as a malware gateway and stop the re-infection cycle; and stop malware call-back communications at the source, even for remote endpoints outside the corporate network.
Furthermore, AMP for Endpoints is not a siloed point product. It has an API that lets customers sync AMP for Endpoints with their other security tools or SIEMs. But most importantly, AMP for Endpoints is part of the larger, integrated security ecosystem of “AMP Everywhere”. In other words, AMP for Endpoints can share and correlate information from the endpoint to the network IPS, to the firewall, to your web or email gateways, and more. So that when you see a threat in one place, your whole entire security ecosystem can respond systemically. This allows you to respond faster and more comprehensively. This integrated architecture is a force multiplier for security teams.
To learn more about how AMP for Endpoints can protect your organization, please visit www.cisco.com/go/ampendpoint . View a demo or watch an overview video .

Product Marketing
Cisco security business group.

Cisco Cybersecurity Viewpoints
Where security insights and innovation meet. Read the e-book, see the video, dive into the infographic and more...

Why Cisco Security?
Explore our Products & Services
CONNECT WITH US
Cisco Advanced Malware Protection (AMP) Explained
Cisco Advanced Malware Protection (AMP) is a malware analysis and protection security solution that goes beyond point-in-time detection of advanced malware problems. Typical security solutions scan files and traffic at the network’s point of entry, block known threats, and allow “good” or “unknown” files and traffic to enter the network. Then, the analysis stops here.
Attacks have become so advanced that point-in-time detection techniques can be easily evaded using targeted, context-aware malware. When advanced malware enters a computer system, it can self-replicate and infect the system’s programs and files. It may even become dormant for a period of time. Advanced malware may also test for Sandbox conditions designed to restrict malicious files and deceive security software into thinking it is not malware.
AMP is intended to strengthen network defenses by preventing, detecting, and assisting in the removal of threats from computer systems using real-time threat intelligence, dynamic malware analytics, and retrospective security wherein files and traffic that entered the network are still being monitored and analyzed. It also provides insight, context, and control that security professionals would need to identify quickly, contain, and remediate threats that slip front-line defenses, all while being cost-effective and operationally efficient.
Cisco AMP Security
Cisco AMP is fully integrated and intelligence-powered. It delivers full security for organizations throughout the entire threat continuum: before, during, and after an attack.
- Before – AMP uses global threat intelligence data from Cisco Threat Grid and Cisco Talos to safeguard against known and emerging risks.
- During – AMP checks the file reputation to see whether a file is malicious or not. Policy-violating file types, exploit attempts, and malicious files infiltrating the network are blocked. Sandboxing is also utilized for detecting risks during an attack.
- After – Cisco AMP continuously monitor, analyze, and retrospect all file activities and traffic, looking for any indicators of compromise (IoCs). If a previously “good” file starts behaving badly, AMP will identify it and immediately alert the security team, indicating a potential breach. It then tracks and shows where the malware came from, which systems were impacted, and what it is doing. It also includes options for quickly responding to the intrusion and remediating it with a few clicks. This provides the security team with deep visibility and controls needed to identify the attacks immediately, scope a compromise, and contain malware before it does harm.
Cisco Advanced Malware Protection Components
Attacks can be launched in different entry points into the organization. Therefore, various AMP solutions are available to be deployed on the different control points, and these AMP solutions include:
- Cisco AMP for Endpoints – for Windows, Macs, and Linux PCs. Also, for Android and Apple iOS mobile devices.
- Cisco AMP for Networks – AMP is integrated into Cisco Firepower NGIPS security appliances.
- Cisco AMP on Firewalls and ASA with FirePOWER Services – AMP is integrated into the Cisco NGFW or Adaptive Security Appliance (ASA) firewall.
- Cisco AMP Private Cloud Virtual Appliance – AMP for on-premises, air-gap solutions.
- Cisco AMP on ESA and WSA – for Cisco Email Security Appliance (ESA) or Web Security Appliance (WSA).
- Cisco AMP for Meraki MX – provides cloud-based security solutions with advanced threat capabilities.
- Cisco Threat Grid – integrated with AMP to enhance malware analysis.
All of these AMP solutions are connected to the AMP Cloud, which contains the database of files and their dispositions as received from Cisco Talos and Cisco Threat Grid. In this way, all connected AMP components are updated in real-time as well.
Download our Free CCNA Study Guide PDF for complete notes on all the CCNA 200-301 exam topics in one book.
We recommend the Cisco CCNA Gold Bootcamp as your main CCNA training course . It’s the highest rated Cisco course online with an average rating of 4.8 from over 30,000 public reviews and is the gold standard in CCNA training:

- Skip to content
- Skip to search
- Skip to footer
Installation and Configuration of AMP Module Through AnyConnect 4.x and AMP Enabler
Available Languages
Download options.
- PDF (551.4 KB) View with Adobe Reader on a variety of devices
- ePub (494.3 KB) View in various apps on iPhone, iPad, Android, Sony Reader, or Windows Phone
- Mobi (Kindle) (605.4 KB) View on Kindle device or Kindle app on multiple devices
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Introduction
This document goes through steps to install the Advanced Malware Protection (AMP) connector with AnyConnect.
The AnyConnect AMP Enabler is used as a medium to deploy AMP for Endpoints. Itself it does not have any capability to convict file disposition. It pushes the AMP for Endpoints software to an endpoint from ASA. Once the AMP is installed it uses cloud capacity to check for files disposition. Further AMP service can submit files to dynamic analysis called ThreatGrid, to score unknown files behaviour. These files can be convicted as malicious if certain artifacts are met. This is widely usefull for zero-day attacks.
Prerequisites
Requirements.
- AnyConnect Secure Mobility Client Version 4.x
- FireAMP / AMP for Endpoints
- Adaptive Security Device Manager (ASDM) Version 7.3.2 or later
Components Used
The information in this document is based on these software and hardware versions:
- Adaptive Security Appliance (ASA) 5525 with Software Version 9.5.1
- AnyConnect Secure Mobility Client 4.2.00096 on Microsoft Windows 7 Professional 64-bit
- ASDM Version 7.5.1(112)
AnyConnect Deployment for AMP Enabler through ASA
The steps involved in the configuration are as follows:
- Configure the AnyConnect AMP Enabler client profile.
- Edit the AnyConnect VPN group policy and download the AMP Enabler Service Profile.
- Login to the AMP dashboard in order to get the connector URL download link.
- Verify the installation on the user machine.
Step 1: Configure the AnyConnect AMP Enabler Client Profile
- Navigate to Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Client Profile .
- Add the AMP Enabler Service Profile .

Step 2: Edit the Group-Policy to Download the AnyConnect AMP Enabler
- Navigate to Configuration > Remove Access VPN > Group Policies > Edit .
- Go to Advanced > AnyConnect Client > Optional Client Modules to Download.
- Choose AnyConnect AMP Enabler.
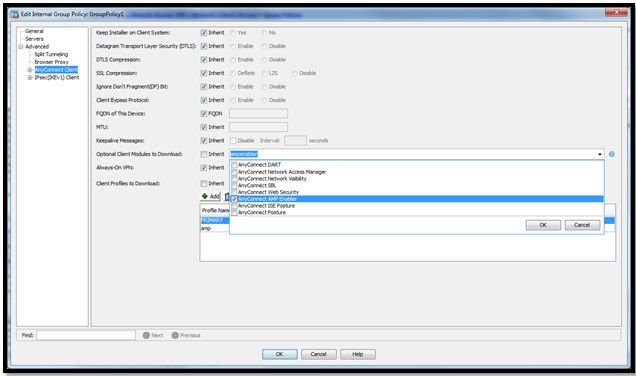
Step 3: Download the FireAMP Policy
Note : Before you proceed, check if your system meets the requirements for the AMP of Endpoints Windows Connector.
System Requirements for AMP for Endpoints Windows Connector
These are the minimum system requirements for the FireAMP Connector based on the Windows operating system. The FireAMP Connector supports both 32-bit and 64-bit versions of these operating systems. The latest AMP documentation can be found in AMP deployment
|
|
|
| ||
|
| 1 GHz or faster processor | 1 GB RAM | 150 MB available hard disk space - Cloud-only mode | 1GB available hard disk space - TETRA |
|
| 1 GHz or faster processor | 512 MB RAM | 150 MB available hard disk space - Cloud-only mode | 1GB available hard disk space – TETRA |
|
| 1 GHz or faster processor | 512 MB RAM | 150 MB available hard disk space - Cloud-only mode | 1GB available hard disk space - TETRA |
|
| 2 GHz or faster processor | 2 GB RAM | 150 MB available hard disk space – Cloud only mode | 1GB available hard disk space – TETRA |
|
| 2 GHz or faster processor | 2 GB RAM | 150 MB available hard disk space - Cloud only mode | 1 GB available hard disk space – TETRA |
Most common is to have the AMP installer placed on the enterprise web server.
In order to download the connector, navigate to Management > Download Connector . Then choose type, and Download FireAMP (Windows, Android, Mac, Linux).
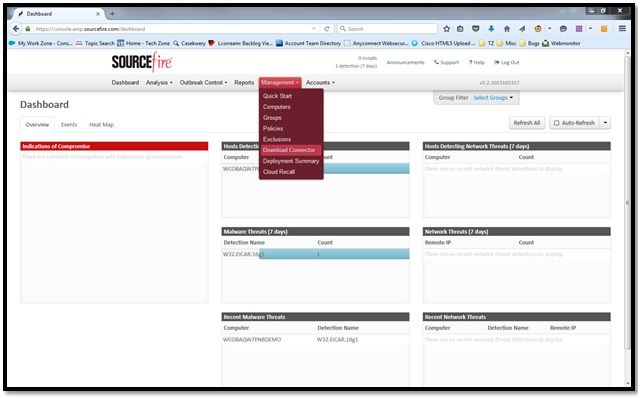
The Download Connector page allows you to download the install packages for each type of FireAMP connector. This package can be placed on a network share or distributed via management software.
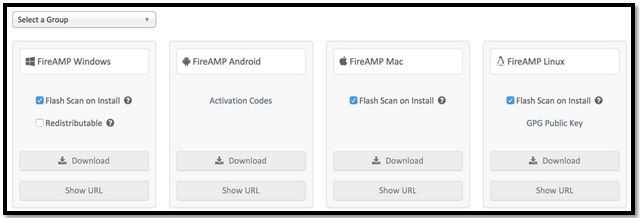
Select a Group
- Audit Only: Monitoring the system based on SHA-256 calculated over each file. This Audit only mode does not quarantine the malware, but sends an event as an alert.
- Protect: Protect mode with quarantine malicious files. Monitor file copy and move.
- Triage: This is for use on already compromised/infected computer.
- Server: Installation suite for Windows server, where the connector installs without Tetra engine and DFC driver. This group is designed by its name for non-domain controller servers.
- Domain Controller: The default policy for this group is set to audit mode as in Server group. Associate all your Active directory servers in this group, that means the connector will be running on a Windows Domain Controller.
The AMP has the feature called TETRA, which is full antivirus engine. This option is optional per policy.
- Flash Scan on Install: Scan process runs during the installation. It is relatively quick to perform and recommended to run only once.
- Redistributable: You should download one single package, which contains 32-bit and 64-bit installers. Rather than a bootstrapper, which is available leaving this option unticked and downloads the installer files, once executed.
Note : You can create your own group and configure associated policy to it. The purpose is to place all e.g. Active directory servers into one group, where the policy is in audit mode. The bootstrapper and redistributable installer also both contain a policy.xml file that is used as a configuration file for the AMP connector.
Step 4: Download the Web Security Client Profile
Specify company web server or a network share with AMP installer. This is most commonly used across companies to save bandwidth and place trusted installers in centralized location.
Please be sure that the HTTPS link can be reached on the endpoints without any certificate error and that root certificate is installed in the machine store.
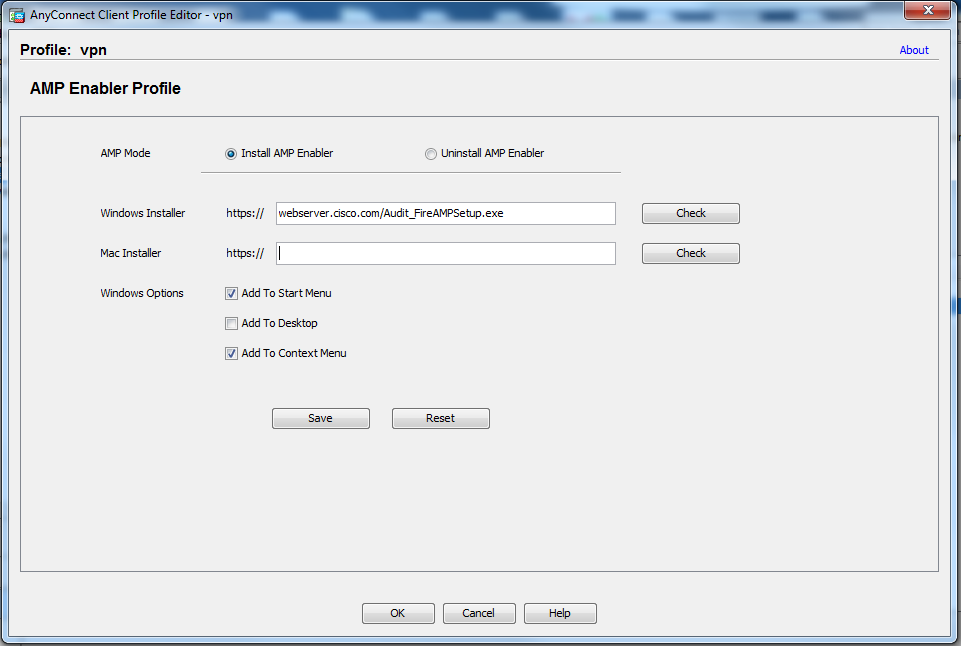
Go back to the AMP Profile created before on the ASA (step 1) and edit AMP Enabler Profile :
- For AMP Mode, click the Install AMP Enabler radio button.
- In the Windows Installer field, add the IP for the web server and the file for the FireAMP.
- Windows Options are optional. Click OK and apply the changes.
Step 5: Connect with AnyConnect and Verify the Installation of the Module
When Anyconnect VPN users connect, ASA pushes the AnyConnect AMP Enabler module through the VPN. For already logged in users, it is recommended to log off and then log in back for the functionality to be enabled.
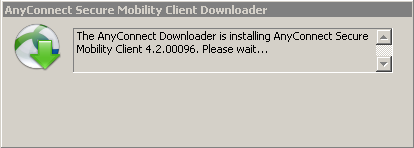
Step 6: Start VPN Connection install AMP Enabler and AMP connector
Once you hit the button connect to start the VPN, it downloads the new downloader module. This will have AMP enabler and downloads the AMP package from the URL path you specified couple of steps before.
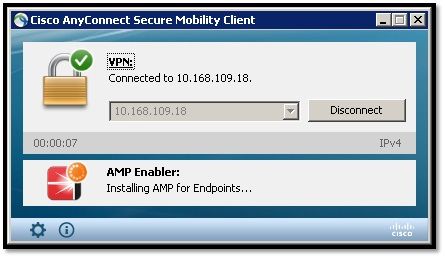
Step 7: Check AnyConnect and Verify If Everything is Installed
Once the VPN is connected and the configuration of the web server is installed, check AnyConnect and verify everything is installed properly.
In the services.msc you can find a new service called CiscoAMP_5.1.3. In the Powershell command we see:
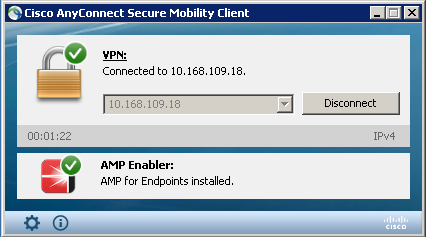
The AMP Installer adds new drivers to the Windows OS. You might use the driverquery command to list the dirvers.
Step 8: Test with an Eicar String Contained in a Zombies PDF File
Test with an Eicar string contained in a Zombies PDF file in a test computer in order to verify the malicious file is quarantined.

Step 9: Deployment Summary
This page shows you a list of successful and failed FireAMP connector installs as well as those currently in progress. You can go to Management > Deployment Summary .
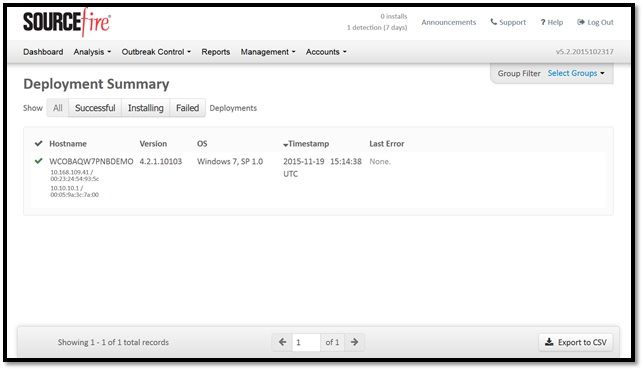
Step 10: Thread Detection Verification
Zombies.pdf triggered an quarantine event, send to the AMP dashboard.


Additional Information
To get your AMP account, you can sign up for the ATS University. This gives you an overview of AMP functionality in LAB.
Related Information
- Configure AMP Enabler
- Technical Support & Documentation - Cisco Systems
Contributed by Cisco Engineers
- Leonardo Correa Cisco TAC Engineer
- Giovanny Gonzalez Cisco TAC Engineer
- Andres Vega Cisco TAC Engineer
Was this Document Helpful?

Contact Cisco
- (Requires a Cisco Service Contract )
This Document Applies to These Products
- AMP for Networks
- Secure Endpoint
- Secure Endpoint Private Cloud
- Secure Malware Analytics Appliances
- Secure Malware Analytics Cloud (Threat Grid – Cloud)
- Sourcefire AMP for FirePOWER Software License
- Sourcefire AMP for Network Virtual Appliance

Cisco Advanced Malware Protection, Cisco AMP
Aug 04, 2017
350 likes | 694 Views
CipherEx Inc,Cisco Consulting Services complete resource for Cisco Advanced Malware Protection,Cisco AMP in South San Francisco Bay Area.
Share Presentation
- advanced malware
- malware attacks
- malware attack
- advanced level malware
- combating advanced malware threats

Presentation Transcript
Cisco Advanced Malware Protection Cisco AMP
Everything You Need to Know About Advanced Malware Protection In this era, the threat of cybercrime, hacking, and malware attack is more imminent than ever before. The enterprise’s data is at risk of being stolen and abused by the attackers. The Malware attack, a shortened form of Malicious Software, can change or erase the data, lock the data, gain access to confidential information, or can affect systems and networks. The different types of malware are Trojan horses, worms, rootkits, viruses, and spyware and as the technology to identify and remove them has evolved, this malware has become far more dangerous and stealthy. The advanced malware is designed by manipulating the malware for the particular mission. The malware is prepared to attach a certain organization, a certain software, or certain systems within the organization and these use various ways to penetrate the system. The enterprises need to have Advanced Malware Protection in place to combat these advanced level Malware.
Combating Advanced Malware Threats Combating the advanced malware threats require two level solutions including detection and protection. The advanced malware solutions are highly intelligent software that can quickly decipher data, detect behavioral anomalies in the files and software, and find the problematic files. However, the company should also have enough resources to contain and act on the information and detection provided by detection software. The two steps are required to run in parallel as the attackers are continuously trying to evade system and compromise common sandboxing techniques. So, the advanced systems like Cisco Advanced Malware protection ,Cisco AMPboth identify and protect the enterprise against these threats.
Finding an Advanced Malware Detection and Protection Software The Advanced Malware Protection is becoming a critical factor in an organization’s data security and safety. The worldwide security breaches in the recent years indicate that the companies had to bear hundreds, thousands and even millions of dollars in loss due to malware attacks. So, finding a robust AMP is one of the most important factors in securing company’s data, networks, and systems. There are several service providers that deploy AMP in organizations to protect them. Organizations useCisco AMPwhich is based on global intelligence, advanced detection techniques, and vigilant combating solutions. These advanced service providers install AMP&D devices in the organization to monitor the incoming files and data request. Also, these systems analyze the already present files, software, and data to identify evasive malware.
Benefits of Cisco Advanced Malware protection (AMP) Full System Emulation The AMPD is designed to ensure full system emulation that goes beyond traditional sound box technology to identify advanced level malware that can evade sandbox environment. Customized Intelligence Based Services The AMPD has intelligence based services with research and actionable insights customized according to your requirements. It helps the organization to be secured and become capable of responding to the threats with customized research and solutions.
Accurate Malware Detection This AMPD accurately identify and detect the malware, providing complete information about them. Therefore, you know what you are up against and have better chance to combat it. • Quick response Another benefit of AMPD is that they provide real-time actionable insights to combat malware threat.
Contact: CipherEx IncAddress:32 Valley View DriveOrindaCA94563Phone=8887749244 Website= http://www.cipherex.com
- More by User

Cisco Telepresence
By Michael Brook. Cisco Telepresence. What is Telepresence?. Cisco Telepresence is an advanced video conferencing system Advantages over normal video conferencing: Very low latency Crisp video and audio quality Directional sound People appear life size Allows for direct eye contact.
354 views • 10 slides

SNMPv3, SSH & Cisco
SNMPv3, SSH & Cisco. Matthew G. Marsh Chief Scientist of the NEbraskaCERT. Scope. Quick Overview Important Points Security Models Authentication Privacy General Usage Supported Platforms IOS Configuration CatOS Configuration Usage Example C Words. Overview of SNMPv3.
318 views • 13 slides

We provide online tech support for Cisco
249 views • 9 slides

Malware Protection
Malware Protection. By Joshua T. I. Towers. 13.3. $13.3 billion was the direct cost of malware for business in 2006
1.14k views • 23 slides

Integration of Advanced Malware Protection (AMP) on Cisco Email and Web Security
Integration of Advanced Malware Protection (AMP) on Cisco Email and Web Security. Cisco Partner Confidential: Not For Distribution: Under NDA. Advanced malware in the news. Source: Providence Journal. There is No Silver Bullet. Attack Continuum. BEFORE. DURING. AFTER. Detect Block
724 views • 18 slides

Giovanni Martinelli, Cisco (*) Moustafa Kattan , Cisco Gabriele Galimberti , Cisco
Information Model for Wavelength Switched Optical Networks (WSON) with Optical Impairments Validation . draft-martinelli-ccamp-wson-iv-info-01. Giovanni Martinelli, Cisco (*) Moustafa Kattan , Cisco Gabriele Galimberti , Cisco Andrea Zanardi , Create-Net. Optical Impairment Reload.
361 views • 15 slides

Cisco WebEx
Cisco WebEx. Jon Milford. WebEx Offers on Cisco Price Lists Offer Comparison. Small Business. Access. Company Wide. Start Small & Grow. Strategic Sale. Land & Expand. Departmental or Pilot. Full Deployment. 2 or more hosts. 250 Host Minimum Capacity 1000 Meeting Center
350 views • 5 slides

Cisco Router
Cisco Router. Network Design.
177 views • 2 slides

CISCO. Routers. 1. (B). IOS Images are stored in Flash. 2. (D). A router's startup configuration file is kept in Non-Volatile RAM (NVRAM). The contents of NVRAM are not lost on reload. 3. (A). A router's running configuration file is kept in RAM. The contents of RAM are lost on reload.
178 views • 2 slides

BITES 2006 Cisco Systems sijones@cisco
BITES 2006 Cisco Systems [email protected]. Core aspects of BSF. Transforming Education Putting the Learner at the centre , Citizenship, Skills Efficiency Workforce Reform, Buildings, Energy, Security Social Inclusion Equal Access , Every Child Matters (ECM, ICS)
570 views • 40 slides

CISCO. Computer Networking. The Internet. The Internet Yesterday. Basics of Computing. Parts of a Computer. CPU - Central Processing Unit Memory - ROM, RAM, etc. Interface - Modem, Video Card, Floppy, etc. All are connected by a bus which is plug in slots. NIC. Network Interface Card
377 views • 17 slides
校本部. 同轴电缆. Cisco. Baystack350-12T. Baystack310-24T. Baystack310-24T. Baystack310-24T. 多台 PC. 多台 PC. 多台 PC. 某学院东校区网络拓扑结构图.
163 views • 1 slides

Networking Basics & Cisco
Networking Basics & Cisco. Shoaib Iqbal IT Engineer. Date: 10-02-2014. Networking Basics. Network. Connectivity of two or more than two devices so that they can communicate with each other. Network = Connectivity + Communication.
1k views • 33 slides
Cisco. Software Engineer Five plus years experience with server/X86 and Familiar with C, C++ and assembly programming. General operating systems software expertise. Familiarity with Ethernet networking and Fibre channel. Needs to have worked on at least one major device driver.
210 views • 4 slides

Cisco Switching
Cisco Switching. Layer 2 Switching. Switching breaks up large collision domains into smaller ones Collision domain is a network segment with two or more devices sharing the same bandwidth. A hub network is a typical example of this type of technology
2.34k views • 74 slides

Advanced Malware Protection
Malware has become an epidemic and the onslaught of attacks shows no sign of abating. Desktops, laptops, mobile devices, networks and virtual machines are all under attack.
237 views • 6 slides

Cisco Advanced Certifications Courses - Online Training
Cisco Certifications - Online Training - Online Certification Courses | E-Learning Center. Cisco training offering in the e-Learning Center will not only help boost your career in IT : http://www.e-learningcenter.com/
361 views • 5 slides

Malware protection
We offer strong security services to our clients such as penetration testing, malware analysis, cyber threat intelligence, red team testing, incident response, digital forensics and the full spectrum of PCI DSS https://cyberbyte.org
109 views • 9 slides

Cisco UCS Training, Cisco UCS Basics, Cisco UCS Ar
Course objectives Describe the Cisco UCS architecture Describe Cisco UCS LAN connectivity configuration Describe Cisco UCS B-Series SAN connectivity configuration Explain how to connect to and manage Cisco UCS components Define Workflows using Orchestration. Describe how to configure Cisco UCS virtualization Administer the software effectively. Understand Data Center Challenges using Cisco UCS Director. Describe how to configure Cisco UCS administration Describe Cisco UCS C-Series features Customize the features for building proof of concepts. Explain how Cisco UCS addresses key problems in Data Center server environments Describe the Cisco UCS system architecture, hardware components, and options
339 views • 5 slides

Cisco Routers
Cisco Routers. Presented By Dr. Waleed Alseat Mutah University. Cisco Routers models. How to choose the appropriate Cisco router. http://www.cisco.com/en/US/products/hw/routers/. Router Initialization. Router components. Router is typically like a computer which operates with
253 views • 21 slides

#Cisco Switches | Cisco Dubai | Cisco Supplier In Dubai | Cisco Dubai | catalyst 2960
access point access point router catalyst 2960 cisco 3850 cisco 9300 cisco access point Cisco Catalyst cisco dubai cisco firewall cisco ip phone cisco ip phone 7945 cisco phone cisco router cisco sfp modules cisco sg350 cisco supplier in dubai cisco switch cisco uae cisco wireless access point cisco wireless router outdoor access point sfp module sfp transceiver wireless access point
127 views • 9 slides

183 views • 17 slides

IMAGES
VIDEO
COMMENTS
Cisco Secure Endpoint Demo Data Stories..... 197. Version 3.7 Secure Endpoint Private Cloud Console User Guide 10 CHAPTER 1 User Guide DASHBOARD The Secure Endpoint (formerly AMP for Endpoints) Dashboard gives you a quick overview of trouble spots on devices in your environment along with updates about malware and network threat detections ...
Cisco Secure Endpoint Deployment Strategy Guide. This guide provides a more detailed look at preparing and planning for a production deployment of Secure Endpoint along with best practices and troubleshooting tips. Download the Deployment Strategy Guide.
Summary Cisco Secure Endpoint (AMP) is an advanced endpoint protection software which is supported and monitored by a central console. Secure Endpoint (AMP) is an application that monitors the machine on which it is installed, searching for suspicious activity.Endpoints with Secure Endpoint (AMP) clients installed will report back to a central console, where IT administrators can view events ...
Cisco Systems, Inc. www.cisco.com AMP for Endpoints User Guide. Last Updated: April 28, 2020
Advanced malware protection software is designed to prevent, detect, and help remove threats in an efficient manner from computer systems. Threats can take the form of software viruses and other malware such as ransomware, worms, Trojans, spyware, adware, and fileless malware. Watch overview (3:05)
This document explains the preventative security engine added to Cisco® Advanced Malware Protection (AMP) for Endpoints as a part of AMP Connector version 6.0.5 (and enhanced with version 6.2.1) for Windows—Exploit Prevention. The document is intended to provide a technical explanation of the technology as well as help assess the value of ...
Select your AMP for Endpoints Connector installation folder (C:\Program Files\Cisco for versions 5.1.1 and higher or C:\Program Files\Sourcefire for previous versions by default) from the dialog and click OK. Click the Add button on the Exceptions dialog. Select Folder from the SONAR Exception submenu.
Session ID: 2024-09-07:463aa6153c08a5ce1002c2d4 Player Element ID: video-cisco-secure-endpoint-explainer-1. Cisco Secure Endpoint explainer video. The sooner threats are detected, the faster businesses can recover. Secure Endpoint offers advanced endpoint protection across control points, enabling your business to stay resilient.
The convergence of these capabilities marks a next generation in endpoint security. Cisco AMP for Endpoints provides next generation capabilities to prevent, detect, and respond to cyberattacks quickly and effectively. Prevent: AMP for Endpoints blocks malware and helps strengthen endpoints from attack: Global Threat Intelligence - Prevention ...
DevNet Learning Labs Dive deeper into Cisco and Cisco Partner technologies with DevNet Learning Labs, including Enterprise Networks, Data Center, Collaboration, Cloud, SDN, and IoT. Whether you're getting started or need a programming refresher, the Learning Labs get you started with tutorials covering REST APIs, Python, JavaScript, and other engineering technologies and concepts.
Cisco AMP for Endpoints (Cisco AMP) is an intelligent, enterprise- class advanced malware analysis and protection solution used to detect, track, analyze, control, and block advanced malware. It provides protection before, during, and after an attack. Cisco AMP is not a replacement for antivirus, it performs more in- depth analysis than the
Cisco Advanced Malware Protection (AMP) is a malware analysis and protection security solution that goes beyond point-in-time detection of advanced malware problems. Typical security solutions scan files and traffic at the network's point of entry, block known threats, and allow "good" or "unknown" files and traffic to enter the ...
User account setup. User Management in Secure Endpoint Console is described in detail in the Secure Endpoint User Guide. To add new users, do the two following steps. Open the XDR console and navigate to Administration/users. Add a user account there and send out the invitation to the new user for the Security Cloud.
Go back to the AMP Profile created before on the ASA (step 1) and edit AMP Enabler Profile: For AMP Mode, click the Install AMP Enabler radio button. In the Windows Installer field, add the IP for the web server and the file for the FireAMP. Windows Options are optional. Click OK and apply the changes.
Click on Create Exclusion Set to create a new list of exclusions. Enter a name for the list, select whether it will be for Secure Endpoint Windows or Secure Endpoint Mac connectors, and click Create. Next click Add Exclusion to add an exclusion to your list.
Benefits of Cisco Advanced Malware protection (AMP) Full System Emulation The AMPD is designed to ensure full system emulation that goes beyond traditional sound box technology to identify advanced level malware that can evade sandbox environment. Customized Intelligence Based Services The AMPD has intelligence based services with research and ...
Selecting an event in Device Trajectory highlights the entire activity line so you can more easily see which system the event relates to. The AMP for Endpoints Console UI has been updated to use a new look and feel. Connector filenames have been updated to take the format amp_groupname.extension.