What is Dynamic VLAN Assignment?
Written by Sean Blanton on May 24, 2021

Share This Article
When it comes to the modern enterprise, few things are more important than network and identity security. With bad actors lurking around every corner (even inside of an organization itself), maintaining a strong, secure network along with keeping credentials safe is of utmost importance to the IT admin. Several network securing tools and techniques are being employed by IT admins today, especially during the global pandemic, but one that has been a foundational approach for many years is dynamic VLAN assignment. Since IT admins are dramatically stepping up the security of their IT environments, some are asking: what is dynamic VLAN assignment and how can it help secure the network?
Network Security with Dynamic VLAN Assignment
The simple answer is that dynamic VLAN assignment (or VLAN steering as it is sometimes called) is an excellent technique used to build on the underlying core strategy to control network access. VLAN assignments build on the use of RADIUS to control access to the network.
Via RADIUS integration, a WiFi access point (WAP) requires not only an SSID and passphrase, but a user’s unique set of credentials to access the network. Once a user has passed credentials through to the WAP to the RADIUS server and directory service, the RADIUS server will reply to the WAP that the user has been authenticated and inform what VLAN they are assigned to.
IT admins configure the system to identify which users and/or groups are assigned to which VLAN. Those VLANs can be set up on the WiFi network for any number of reasons including security and compliance. By segmenting users and authenticating them with their unique credentials, IT admins can increase security significantly. This approach helps separate out critical areas of the network, and can be especially helpful in compliance situations where, for example, the cardholder data environment (CDE) can be separated from the rest of the network making PCI Compliance far easier.
Challenges with Dynamic VLAN Assignments
The challenge with this approach is the overhead for IT admins. Traditionally, to implement dynamic VLAN assignments would require a great deal of infrastructure, configuration, and administration. For starters, IT organizations would need to set up their own FreeRADIUS server and connect that instance to the wireless access points and the identity provider (IdP), often, Microsoft ® Active Directory ® .
In many networks, the IT group would also need to configure endpoints with supplicants so that they could talk to the RADIUS server over the proper protocols. All of this ended up being a significant disincentive for IT admins, and that is why many WiFi networks are secured simply with an SSID and passphrase.
With the introduction of modern cloud RADIUS solutions, however, IT admins can virtually outsource the entire process for RADIUS authentication to WiFi and dynamic VLAN assignments. This Cloud RADIUS offering doesn’t focus on RADIUS only, but also acts as the identity management source of truth that can replace an on-prem Active Directory instance. It is available from the JumpCloud Directory Platform .
Cloud RADIUS and More
JumpCloud Directory Platform is everything a directory service was, and reimagines it for the cloud era. This includes endpoint management , identity and access management, single sign-on, multi-factor authentication, and network authentication tools such as Cloud RADIUS. Relatively new to the JumpCloud Suite is dynamic VLAN assignment functionality, so network administrators can better authorize their users’ access to crucial network resources. This feature just adds one more log to the bright flame of this cloud directory.
Interested in dynamic VLAN assignment and the rest of what the platform has to offer? Contact us , or check out our knowledge base to learn more.
- Remote Work
- User Access

Reduce IT costs and complexity
Sean Blanton is the Director of Content at JumpCloud and has spent the past decade in the wide world of security, networking and IT and Infosec administration. When not at work Sean enjoys spending time with his young kids and geeking out on table top games.
Continue Learning with Related Posts
Continue learning with our newsletter.
Dynamic VLAN vs. Static VLAN
What's the difference.
Dynamic VLAN and Static VLAN are two different methods of implementing VLANs in a network. In a Static VLAN, the administrator manually assigns ports to specific VLANs, and this configuration remains fixed unless manually changed. This method provides simplicity and stability, as the VLAN assignments do not change unless intentionally modified. On the other hand, Dynamic VLAN uses protocols such as VLAN Membership Policy Server (VMPS) or VLAN Query Protocol (VQP) to dynamically assign VLANs to ports based on certain criteria like MAC address or username. This allows for more flexibility and scalability, as VLAN assignments can be automatically updated as devices connect or disconnect from the network. However, Dynamic VLAN requires additional configuration and management overhead compared to Static VLAN.
Further Detail
Introduction.
Virtual Local Area Networks (VLANs) are an essential component of modern network infrastructure, allowing network administrators to logically segment a physical network into multiple virtual networks. VLANs provide numerous benefits, such as improved security, enhanced network performance, and simplified network management. When it comes to implementing VLANs, there are two main approaches: Dynamic VLAN and Static VLAN. In this article, we will explore the attributes of both Dynamic VLAN and Static VLAN, highlighting their differences and use cases.
Dynamic VLAN
Dynamic VLAN, also known as VLAN assignment based on user authentication, is a VLAN configuration method that dynamically assigns VLAN membership to network devices based on user credentials. This approach leverages protocols such as IEEE 802.1X and RADIUS to authenticate users and dynamically assign them to the appropriate VLAN. Dynamic VLANs offer several advantages over Static VLANs.
- Flexibility: Dynamic VLANs allow for greater flexibility in network management. As users move within the network, their VLAN membership can be automatically updated based on their authentication status. This flexibility is particularly useful in environments where users frequently change their physical location or require access to different resources.
- Enhanced Security: Dynamic VLANs provide an additional layer of security by ensuring that only authenticated users can access specific VLANs. By authenticating users before granting VLAN membership, organizations can prevent unauthorized access to sensitive resources and mitigate the risk of unauthorized network access.
- Reduced Administrative Overhead: With Dynamic VLANs, network administrators can automate the VLAN assignment process, reducing the need for manual VLAN configuration. This automation saves time and effort, especially in large-scale networks with a high number of users and frequent changes in VLAN membership.
- Scalability: Dynamic VLANs are highly scalable, making them suitable for environments with a large number of users. As new users join the network, they can be easily authenticated and assigned to the appropriate VLAN without requiring manual intervention from the network administrator.
- Granular Access Control: Dynamic VLANs enable granular access control by allowing network administrators to define different VLANs for different user groups or roles. This level of granularity ensures that users only have access to the resources and services that are relevant to their specific role, enhancing network security and reducing the risk of unauthorized access.
Static VLAN
Static VLAN, also known as port-based VLAN, is a VLAN configuration method where VLAN membership is manually assigned to network devices based on the physical switch port they are connected to. In Static VLANs, the VLAN assignment remains fixed unless manually changed by the network administrator. While Static VLANs lack the dynamic nature of Dynamic VLANs, they still offer several advantages in certain scenarios.
- Simplicity: Static VLANs are relatively simple to configure and manage. Since VLAN membership is manually assigned to switch ports, there is no need for complex authentication protocols or dynamic assignment mechanisms. This simplicity makes Static VLANs an ideal choice for small networks or environments with limited VLAN requirements.
- Predictability: With Static VLANs, network administrators have complete control over VLAN assignments. This predictability can be advantageous in scenarios where network resources need to be consistently accessible from specific VLANs. By manually configuring VLAN membership, administrators can ensure that devices connected to specific switch ports always belong to the desired VLAN.
- Compatibility: Static VLANs are widely supported by network devices and are compatible with a wide range of network equipment. This compatibility makes Static VLANs a reliable choice for organizations with diverse network infrastructure or legacy devices that do not support dynamic VLAN assignment protocols.
- Stability: Since VLAN membership remains fixed in Static VLANs, there is no risk of unexpected VLAN changes due to user authentication or dynamic assignment mechanisms. This stability can be beneficial in environments where network changes need to be carefully controlled to avoid disruptions or potential security vulnerabilities.
- Performance: Static VLANs can offer slightly better network performance compared to Dynamic VLANs in certain scenarios. Since there is no need for authentication or dynamic assignment processes, network devices connected to Static VLANs can establish connectivity faster, reducing potential latency or delays.
Both Dynamic VLAN and Static VLAN have their own strengths and use cases. Dynamic VLANs provide flexibility, enhanced security, reduced administrative overhead, scalability, and granular access control. On the other hand, Static VLANs offer simplicity, predictability, compatibility, stability, and potential performance advantages in certain scenarios. The choice between Dynamic VLAN and Static VLAN depends on the specific requirements and characteristics of the network environment. Network administrators should carefully evaluate their needs and consider factors such as network size, user mobility, security requirements, and compatibility with existing infrastructure when deciding which VLAN configuration method to implement.
Comparisons may contain inaccurate information about people, places, or facts. Please report any issues.

- PORTNOX CLOUD Unified Access Control Any Device. Any Data. Anywhere.
Zero Trust Network Access Control
- Cloud-native RADIUS Stand up Portnox’s cloud-native RADIUS is minutes.
- Passwordless authentication Leverage certificates for passwordless network authentication.
- Risk posture assessment Monitor the potential risk of every connected device.
- Compliance enforcement Automate device remediation & stay compliant 24/7.
- Explore Pricing

Zero Trust Conditional Access
- How does it work? Discover how to better secure your apps with Portnox.
- Passwordless authentication Bolster application access by going passwordless.
- 24/7 risk monitoring Ensure only trusted devices gain access to your apps.
- Automated remediation Automate device-based compliance enforcement.

Zero Trust Infrastructure Administration
- How does it work? Explore cloud-native TACACS+ from Portnox.
- Admin authentication Get started with simple, secure admin authentication.
- Access policy enforcement Make sure not just anyone can tinker with your infrastructure.
- Granular accounting Keep auditors at bay with cloud-native TACACS+.

Unified Zero Trust Security
- How does it work? Learn the ins and outs of the Portnox Cloud.
- Cloud-native RADIUS authentication Spin up our cloud-native RADIUS server in minutes.
- Passwordless application security Bolster application access by going passwordless.
- Zero trust network access control See and control access for every device across your network.
- Network device administration Keep auditors at bay with cloud-native TACACS+.

- Authentication
- Access Control
- Risk Monitoring
- Remediation
- IoT Security
- Guest Access
Applications
Infrastructure.
- Authorization
Integrations
- Case Studies
- Infographics
- Product Briefs
- White Papers
- Cloud Documentation
Compliance Center
Regulations, cybersecurity center.
- What is 802.1X? What are the benefits of NAC? How does zero trust work? Why go passwordless? What is IoT profiling? Explore All »
- Reseller Program
- Managed Services
- Become a Partner
- Register a Deal
- Get Started
Network Access Control , Network Security
Segmenting your network with dynamic vlan.

What is Dynamic VLAN?
VLANs (Virtual Local Area Networks) enable segmentation of the main organizational network. In practice, VLANs allow network administrators to keep devices and network resources separated despite being connected to the same physical network.
Dynamic VLAN assignment separates and isolates devices into different network segments based on the device or user authorization and their characteristics. The flow of traffic between those VLANs is governed by a firewall or another routing device which can then enforce specific network access rules.
Why Use Dynamic VLANs?
Segmenting the network is a security best practice, and in some cases is even a regulatory requirement – such as with PCI. Network segmentation is a measure that improves the effectiveness of all the current investments in other security tools, and can by itself help to prevent significant damage to critical organizational data across the network after a company has been breached.
Automating VLAN assignments and eliminating the need for manual intervention has historically been a challenge for network security teams. Today, automatic VLAN assignment is best implemented by the use of a RADIUS service, which functions as follows:
- A device connects to one of several the network access layers: wired ethernet switch or WiFi SSID
- The network access layer sends a request to the RADIUS server with the user’s credentials or certificates (using 802.1X)
- The RADIUS server sends a reply which contains attributes that provide the switch or access point with information on the device VLAN, result in properly VLAN assignment
Common Dynamic VLAN Assignment Use Cases
Network and security administrator most commonly encounter these use cases for dynamic VLAN assignment:
- The Sales & Marketing department does not need access to R&D resources, while R&D should not have access to the Finance Department resources. Using dynamic VLANs, each department will be placed in the correct VLAN with the required access.
- Devices that fail to authenticate due to wrong credentials or incorrect/expired certificate will be placed in a quarantine VLAN with internet access only.
- IP Phones using a dedicated voice VLAN and should be placed on that VLAN upon successful authentication.
- MAC bypass for devices that do not support 802.1X should be placed in their own dedicated VLAN.
- Devices that fail posture assessment (such as those without updated AntiVirus) should be placed in a quarantine VLAN with limited access.
- Employees connecting to one single WiFi SSID and get different access (VLANs) based on their authentication repository LDAP groups.
Dynamic VLAN Assignment with Portnox CLEAR
As mentioned earlier, the implementation of dynamic VLAN assignment has often been challenging for organizations since additional servers were needed on-site at the datacenter. This forced network teams to manage redundancies, complex configurations, and on-going maintenance.
To paint a clearer picture of this headache, consider this:
Take the case of connecting a new department, branch, or merely onboarding a lot of new employees at once…this can cause a surge in demand, which will in turn cause the whole network to “shutdown,” thus not accepting anyone who tries to connect.
Portnox CLEAR is a network access control solution, deployed as a cloud service, that provides all the mentioned use cases and more. CLEAR simplifies the implementation process of dynamic VLAN assignment. CLEAR allows you to easily set-up a cloud RADIUS server in a single click, and integrate with various authentication repositories like on-premise Active Directory, Azure AD, GSuite, OKTA. Plus, you can enforce your own unique access control policy to dynamically assign users to their respective VLANs.
In addition to VLAN assignment based on credentials authorization, CLEAR also allows you to implement dynamic VLAN assignment based on risk violation. This means that even devices that have authenticated successfully to the wired or wireless network can be dynamically moved to a dedicated VLAN if they fall out of compliance.
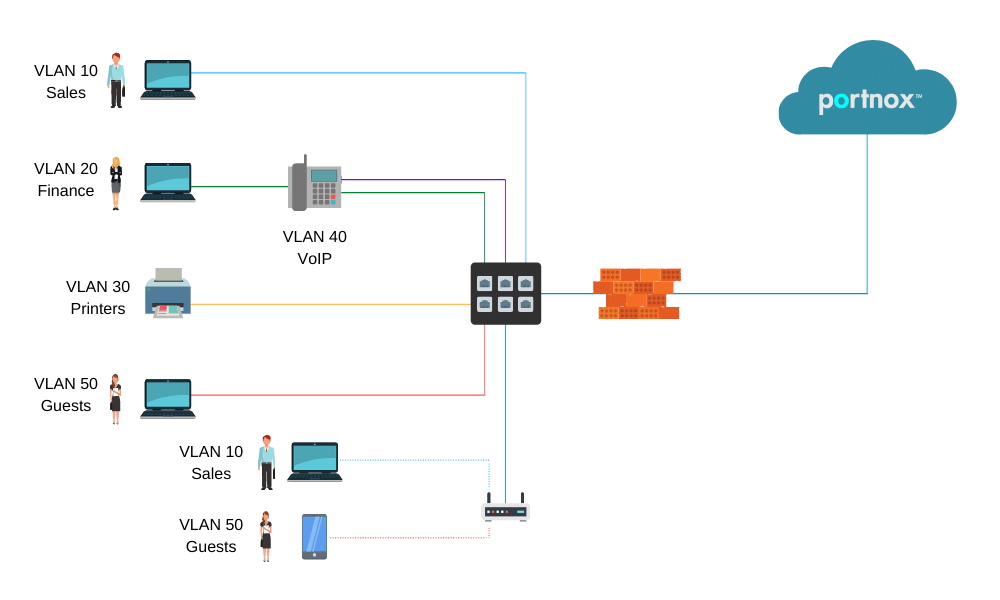
In the diagram above:
- PCs are dynamically assigned to the VLAN based on their credentials/certificate.
- IP Phones are assigned to the VOIP VLAN.
- Printers are assigned to the printers VLAN.
- Guests devices assigned to the internet-only access/quarantine VLAN.
How it Works – Setting up Dynamic VLAN Assignment in Portnox CLEAR:
1. enable cloud radius.
In the CLEAR portal, create your one-click cloud RADIUS server: Go to Settings > Services > CLEAR RADIUS Service , and add your RADIUS service instance:
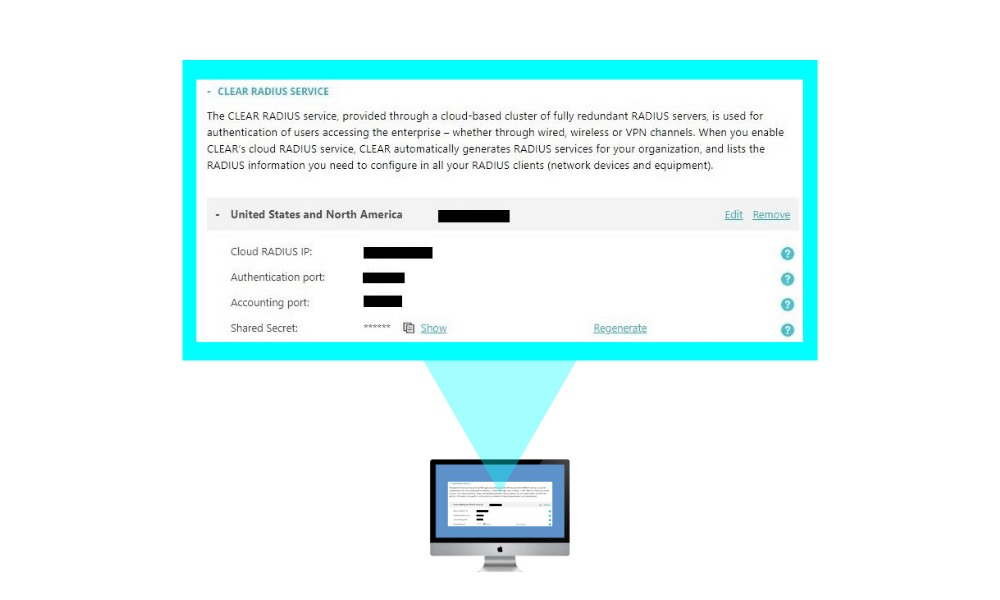
And point your network equipment: wired switches and/or wireless controllers to work with these CLEAR Radius service details.
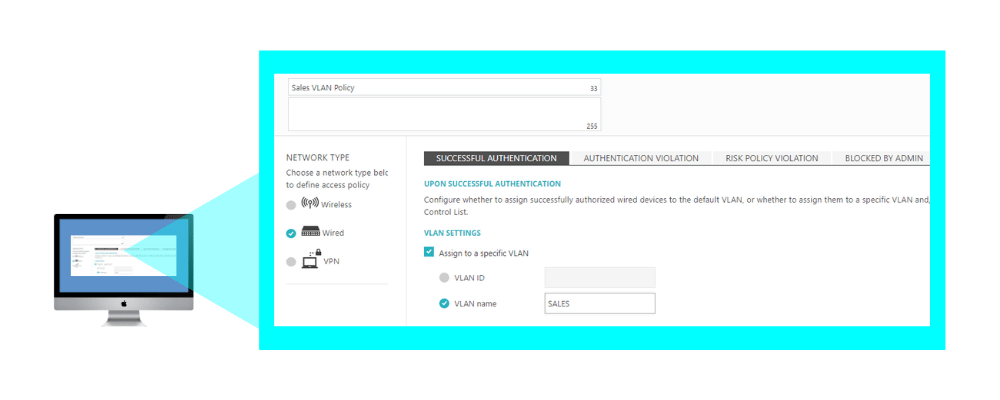
2. Creating an Access Control Policy – Dynamic VLAN Assignment:
In Policies > Access Control Policies , add or edit your existing access control policy, select the required access layer and add the correct VLAN ID or VLAN name for each event you want to create dynamic VLAN assignment for: successful authentication, authentication violation, risk assessment, blocked by admin. Then, map the access control policy to the relevant groups and users.
Related Reading

The Case for Cloud-Based: Evaluating Portnox Against Traditional On-Premises NAC Solutions

NAC’s Role in the Larger IAM Eco-System

Move Towards Passwordless Security: Embracing Change on Identity Management Day
Try portnox cloud for free today.
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!
Privacy Overview
WEBINAR 5/15 @ 12 PM EST: Deep Dive into Conditional Access
Static and Dynamic VLAN Membership Explained
There are two types of VLAN membership: static and dynamic. In the static method, administrators manually add switch ports to VLANs. In the dynamic method, the switch automatically assigns appropriate VLANs to ports.
What VLAN membership is
A VLAN is a group of devices that share broadcast messages. By default, switches have only one VLAN, called VLAN-1. However, you can create and configure additional VLANs to limit broadcast messages and logically arrange devices in groups. After creating VLANs, you need to add desired ports to VLANs. VLAN membership is an authorization to be part of the VLAN. There are two ways to assign VLAN membership to switch ports: Static and Dynamic.
Static VLAN membership
It is an easy and straightforward method. In it, you manually add ports to VLANs. VLANs configured in this way are typically called port-based VLANs .
Let us take an example.
The following image shows an 8-port switch. With the default configuration, all ports belong to the same broadcast domain.

Now, suppose you want to break this network into two broadcast domains. You create two VLANs: VLAN-10 and VLAN-20 . You enter the sub-configuration mode of ports and configure VLANs. You configure VLAN-10 on ports 1, 2, 3, and 4, and VLAN-20 on ports 5, 6, 7, and 8. It is an example of static VLAN membership.

Advantages of static VLAN membership
The main advantages of static VLAN membership are the following.
Easy configuration
Configuring a static VLAN membership is easy. To configure a static VLAN membership, you run only one command [switch(config-if)#switchport access vlan VLAN_ID ] in the sub-interface configuration mode.
Easy management
Managing static VLAN membership is also easy. From the sub-interface configuration mode of the port, you can easily add, update, and remove VLAN membership.
Since you manually add, update, and remove static VLAN membership on all ports, the static VLAN membership is more secure than the dynamic VLAN membership.
Availability
Static VLANs are available on almost all Cisco switches. You do not need any high-end Cisco switch to use them. You can configure and use them on existing Cisco switches.

Disadvantages of static VLAN membership
The disadvantages of static VLANs are the following.
Scalability
Static VLAN membership is not scalable. If your network is small, you can choose it because of its easy configuration. But if your network is big, you can not use it alone. For example, if your network has thousands of devices, assigning and managing static VLAN membership for these devices on switches will be a difficult task.
Static VLAN membership is not movable. If you move a PC from a switch port to another switch port, you need to manually remove the VLAN membership from the current port and add it to the new port.
Dynamic VLAN membership
Dynamic VLAN membership works on a server-client model. In this model, a policy server called the VLAN membership policy server (VMPS) saves VLAN mapping information. VLAN mapping information contains VLAN IDs and MAC addresses of end devices.
All other switches act as VLAN client switches. They forward MAC addresses to the VMPS switch. The VMPS switch finds VLAN ID associated with each MAC address and passes that ID to the VLAN client switch.
The following image shows a simple network. It uses dynamic VLAN membership.

In the above network, when you add PC2 to the VLAN client switch's port-2, it forwards PC2's MAC address to the VMPS switch. VMPS switch finds the VLAN ID related to PC2's MAC address and provides that ID to the VLAN client switch. The VLAN client switch assigns the received VLAN ID to port-2.
Now suppose, you remove PC2 from port-2 and attach it to port3. In this situation, the switch will take the following steps.

- It removes configured VLAN on port-2 as soon as you remove the connected device.
- When you attach PC2 to port-3, it sends the PC2's MAC address to the VMPS switch.
- VMPS switch finds the VLAN ID related to the PC2's MAC address and provides it to the VLAN client switch.
- The VLAN client switch assigns the received VLAN ID to port-3.
Advantages of Dynamic VLAN membership
The advantages of dynamic VLAN membership are the following.
The main advantage of dynamic VLAN membership is movability. If you move an end device from a switch port to another switch port, the switch automatically updates the VLAN information on both ports.
Centralized management
Dynamic VLAN membership provides centralized management. You need to manage VLAN information only on the VMPS swtich. Other switches automatically receive the updated information from the VMPS swtich.
Fast implementation
Since VLAN client switches automatically implement dynamic VLAN membership, it is faster than static VLAN membership. In static VLAN membership, if you change VLAN information, you need to manually update that information on all ports. In dynamic VLAN membership, switches automatically update the information on all ports.
Disadvantages of Dynamic VLAN membership
The disadvantages of dynamic VLAN membership are the following.
Complex configuration
The configuration of dynamic VLAN membership is complex. You need to map the MAC addresses of all end devices to VLANs on the VMPS switch. You also need to configure all other switches to get VLAN information from the VMPS switch.
Add extra cost to the network
You cannot use low-end Cisco switches as VMPS server switch. You need a high-end Cisco switch such as Catalyst 6500 switch to configure VMPS. High-end Cisco switches are costly.
This tutorial is a part of the tutorial series on VLAN, VTP, and DTP Concepts and Configurations on Cisco Routers. Other parts of this series are the following.
Chapter 01 VLAN Basic Concepts Explained with Examples
Chapter 02 Advantages and Disadvantages of VLANs
Chapter 03 Static and Dynamic VLAN Membership Explained
Chapter 04 Access Link and Trunk Link Explained
Chapter 05 VLAN Tagging Explained with DTP Protocol
Chapter 06 DTP Modes and Protocol Explained
Chapter 07 802.1Q Native VLAN concept Explained
Chapter 08 Cisco Inter-Switch Link (ISL) Explained
Chapter 09 Trunk Tagging and Frame Tagging Explained
Chapter 10 VTP Modes and VTP Protocol Explained
Chapter 11 VTP Pruning on switches Explained
Chapter 12 VLAN Practice Lab Setup in Packet Tracer
Chapter 13 Configure VTP Server and Client in Switch
Chapter 14 VLAN Configuration Commands Step by Step Explained
Chapter 15 Router on Stick Configuration Explained
By ComputerNetworkingNotes Updated on 2024-02-27 05:30:01 IST
ComputerNetworkingNotes CCNA Study Guide Static and Dynamic VLAN Membership Explained
We do not accept any kind of Guest Post. Except Guest post submission, for any other query (such as adverting opportunity, product advertisement, feedback, suggestion, error reporting and technical issue) or simply just say to hello mail us [email protected]


Dynamic VLAN Assignment for Cloud RADIUS
The landscape of cybersecurity is always changing, but there are a few constants. One unchanging aspect is the use of VLANs as a primary method of segmenting users and network resources. Like the Local Area Network it emulates, a VLAN is a useful tool for isolating sensitive resources and sheltering it from risk created by unnecessary access.
Our networks are becoming increasingly virtual, as illustrated by the industry trend of moving to the cloud. That makes VLAN more important than ever and, fortunately, VLAN technology is keeping pace. In this article we will discuss the methods through which users are assigned to VLANs and how to automate the process for ease-of-use and increased security.
What is Dynamic VLAN Assignment?
Dynamic VLAN Assignment, also referred to as “ VLAN Steering ”, is exactly what it sounds like. The process of assigning users or groups of users to VLAN can be handled by a RADIUS at the time of authentication, though the infrastructure and expertise needed for dynamic VLAN assignment has historically been an obstacle for smaller organizations.
Why use Dynamic VLAN Assignment?
The default state of a wireless (or wired) network is sometimes described as “flat”. Every user in the organization is tossed into a shared network that also contains all of the resources that organization has (files, data, source code, applications, etc.). Everyone potentially has access to everything, even if there is another login portal between them and, say, the payroll system.
That’s an unnecessary risk. Developers need access to very sensitive resources like the source code for their app, but that doesn’t imply that they require access to everything that is less confidential. It’s a basic tenet of security, cyber or not, to restrict access to only people that require it.
Those are the guiding principles that lead us to implement VLANs, but the “dynamic assignment” portion of dynamic VLAN assignment is equally important. There needs to be an automated process by which users are automatically shunted to the appropriate VLAN. Relying on IT to manually assign VLANs is short-sighted – humans are fallible and it doesn’t scale past a couple dozen users.
RADIUS Attributes for Dynamic VLAN Assignment
That’s why we configure a RADIUS server to assign users for us. It already has the responsibility of authorizing and authenticating users for network access, so it’s a relatively simple task to configure it to send users to a switch that can further sort users to a specific access point and/or a specific VLAN.
How does a RADIUS decide where to send the user? By the attributes assigned to them. Attributes are often stored as part of the user profile in the directory or as a part of the device/client profile for MAC authentication. SecureW2’s Cloud PKI can even amend attributes to digital certificates for seamless certificate-based EAP-TLS authentication with dynamic VLAN assignment.
The majority of VLAN assignment is done by configuring these 3 attributes:
- Tunnel-Type
- Tunnel-Medium-Type
- Tunnel-Private-Group-ID
SecureW2’s Cloud RADIUS supports additional VLAN assignment attributes such as:
- Custom groups
These additional parameters allow you an even greater degree of control and flexibility in assigning users to VLANs so that you can efficiently maximize your network security.
Which RADIUS for Dynamic VLAN Assignment?
Most, though not all, RADIUS servers can be configured to support dynamic VLAN assignment. Keep in mind the other needs of your organization when choosing which to configure.
Microsoft’s NPS is a popular DIY RADIUS solution because many organizations are already using a Microsoft environment. The ubiquitous Active Directory remains one of the most popular identity providers even though it’s mostly incompatible with many cloud-based applications and services (including Microsoft’s own Azure AD). The lack of compatibility with cloud services more or less eliminates NPS as a choice.
FreeRADIUS is another DIY RADIUS which actually is able to interact with cloud directories and the like. Unfortunately, the lack of a GUI is a turn off for most enterprises that want deep customizability and reporting.
SecureW2’s Cloud RADIUS is equipped with the latest in VLAN technology. Our Dynamic Policy Engine enables the RADIUS to make runtime-level policy decisions by directly referencing user attributes stored in any directory (including cloud directories like Google, Azure, and Okta). Not only does this reinforce the network segmentation of VLAN, but it also enables passwordless authentication for any cloud directory via the use of digital certificates.
If your organization already has an 802.1X network, SecureW2’s turnkey solutions can integrate into your network without any forklift upgrades. If you’re still considering the transition to a secure WPA2-Enterprise network, you’ll be interested in our managed Cloud PKI which has all the components necessary for top-of-the-line X.509 digital certificate security right out of the box.
We have affordable options for organizations of all sizes. See our pricing here.
Patrick Grubbs
Patrick is an experienced SEO specialist at SecureW2 who also enjoys running, hiking, and reading. With a degree in Biology from College of William & Mary, he got his start in digital content by writing about his ever-expanding collection of succulents and cacti.
Related Posts

How To Test RADIUS Response Time

Evil Twin Attacks Explained

Breaking Down the 802.1X Protocol

Configure EAP-TLS Authentication for Cloud Networks

Sync AD to Google for Cloud Authentication
You are using an outdated browser. Please upgrade your browser to improve your experience.
Your browser does not support JavaScript. Please turn it on for the best experience.
Configuration Guide on Dynamic VLAN with the VLAN Assignment function of RADIUS
OC200 , OC300 , Omada Software Controller , Omada Cloud-Based Controller
Recent updates may have expanded access to feature(s) discussed in this FAQ. Visit your product's support page, select the correct hardware version for your device and check either the Datasheet or the firmware section for the latest improvements added to your product.
With the VLAN Assignment feature of RADIUS, the Omada SDN solution can put clients authenticated by different accounts to the corresponding VLANs. In this way, clients will obtain IP addresses from different VLANs, and you don't have to create many SSIDs bound with different VLANs for wireless networks, or bind the PVIDs of the switch ports to specific VLANs for wired networks.
To achieve the above features, you will need the Omada SDN Controller, EAP for wireless assignment, JetStream Switch for wired assignment, and an external RADIUS server. In this article, we will share the configuration guide for below network topology.
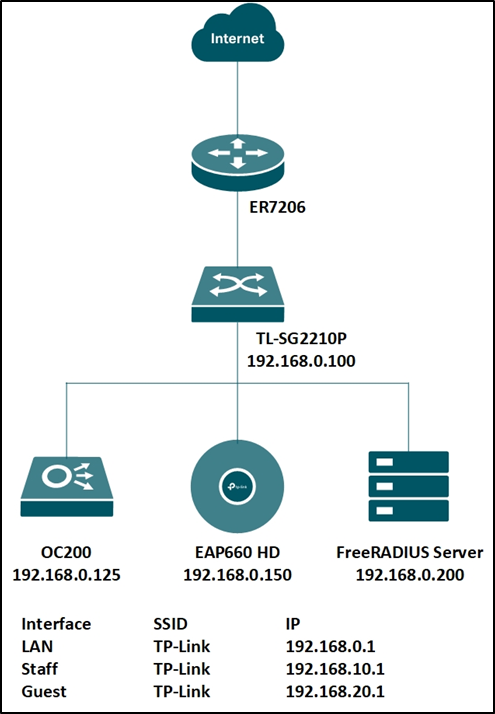
Step 1. Set up the RADIUS server.
Here we run a FreeRADIUS ® server on a Linux server. For more information on installation and configuration, please refer to the official website: https://freeradius.org/
First, edit the “ clients.conf ” file, set the client IP address as “192.168.0.0/24” and the password as “tplink”.
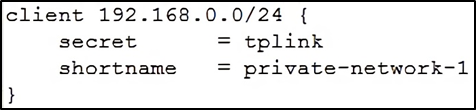
Next, edit the “ users ” file, create two accounts “test10” and “test20” in VLAN10 and VLAN20, respectively.
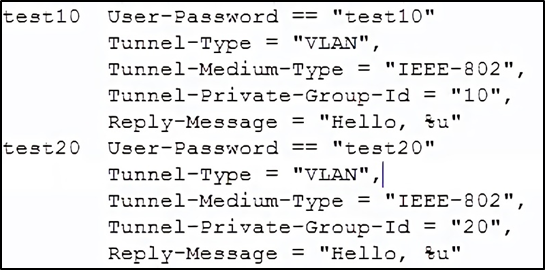
You may also edit the “ eap.conf ” to modify the EAP type for WPA-Enterprise. After configuration, run the RADIUS server to listen for access requests.
Step 2. Create the RADIUS profile.
Go to Authentication --- RADIUS Profile, create a new profile bound with the RADIUS server, and check “Enable VLAN Assignment for Wireless Network” to assign VLANs for wireless clients.
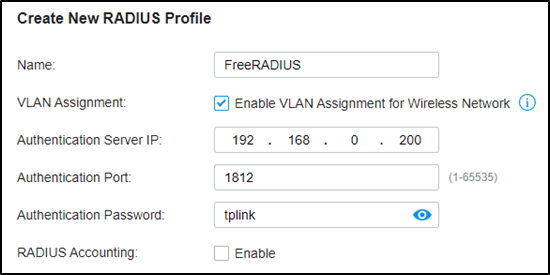
Step 3. Create more VLAN for VLAN assignments.
Assuming all Omada devices have been adopted by the controller, go to Settings --- Wired Networks --- LAN, and create two interfaces with VLAN10 and VLAN20.
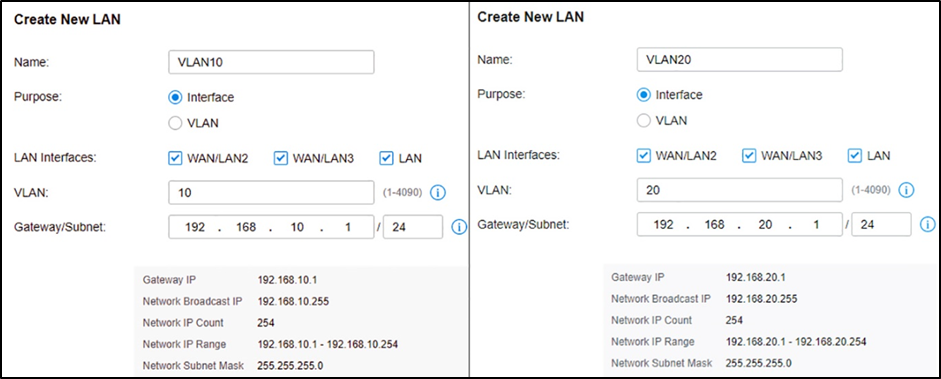
Step 4. VLAN assignment for wireless networks.
Go to Settings – Wireless Networks, and create a new SSID with WPA-Enterprise as below. For differences between WPA-Personal and WPA-Enterprise, please refer to FAQ500 .
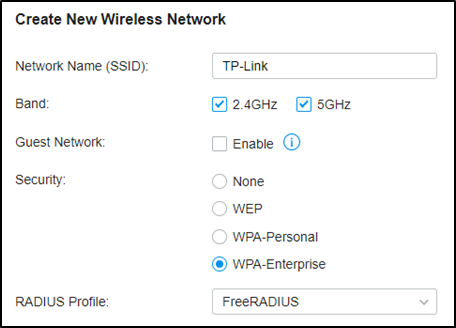
When connecting your client to the SSID, you will be asked to choose the authentication type of WPA-Enterprise, and enter the account username and password. After successfully authenticating with account “test10”, the client will obtain an IP address from VLAN10, while with account “test20”, it will get that from VLAN20.
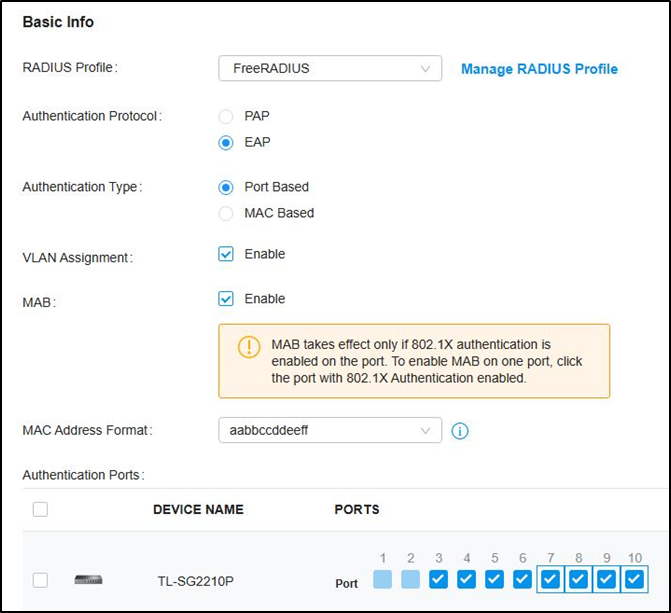
Step 5. VLAN assignment for wired networks.
Go to Authentication --- 802.1X and enable the feature, select Authentication Type as “Port Based”, enable “VLAN Assignment” and check the Ports to be authenticated according to your requirements.
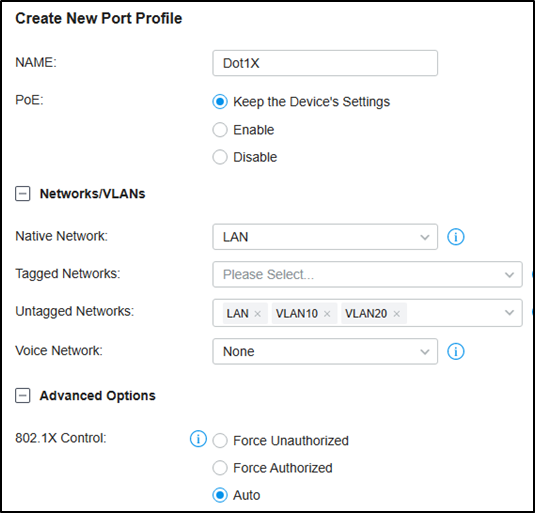
Not to click the ports twice to enable MAB for them.
Then go to Wired Networks --- LAN --- Profile, create a new port profile, add VLAN10 and VLAN20 to untagged networks, and make sure the 802.1X Control mode is Auto.
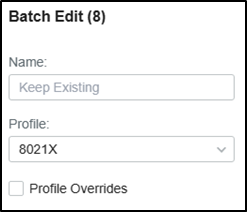
Then Go to Devices, click your switch, go to Ports, check the authentication ports, and batch edit to change the port profile to the one created just now.
For 802.1X authentication, you may need to run TP-Link 802.1X Client Software (click here to download) for authentication. Please refer to FAQ787 and Step 3. For detailed guidance.
Is this faq useful?
Your feedback helps improve this site.
What’s your concern with this article?
- Dissatisfied with product
- Too Complicated
- Confusing Title
- Does not apply to me
We'd love to get your feedback, please let us know how we can improve this content.
We appreciate your feedback. Click here to contact TP-Link technical support.
Recommend Products
Omada Cloud-Based Controller
Omada Software Controller

Omada Hardware Controller
TP-Link Community
Still need help? Search for answers, ask questions, and get help from TP-Link experts and other users around the world.
Visit the Community >
We have updated our Policies. Read Privacy Policy and Terms of Use here. This website uses cookies to improve website navigation, analyze online activities and have the best possible user experience on our website. You can object to the use of cookies at any time. You can find more information in our privacy policy .
Basic Cookies
These cookies are necessary for the website to function and cannot be deactivated in your systems.
accepted_local_switcher, tp_privacy_base, tp_privacy_marketing, tp_smb-select-product_scence, tp_smb-select-product_scenceSimple, tp_smb-select-product_userChoice, tp_smb-select-product_userChoiceSimple, tp_smb-select-product_userInfo, tp_smb-select-product_userInfoSimple, tp_top-banner, tp_popup-bottom, tp_popup-center, tp_popup-right-middle, tp_popup-right-bottom, tp_productCategoryType
__livechat, __lc2_cid, __lc2_cst, __lc_cid, __lc_cst, CASID
id, VISITOR_INFO1_LIVE, LOGIN_INFO, SIDCC, SAPISID, APISID, SSID, SID, YSC, __Secure-1PSID, __Secure-1PAPISID, __Secure-1PSIDCC, __Secure-3PSID, __Secure-3PAPISID, __Secure-3PSIDCC, 1P_JAR, AEC, NID, OTZ
Analysis and Marketing Cookies
Analysis cookies enable us to analyze your activities on our website in order to improve and adapt the functionality of our website.
The marketing cookies can be set through our website by our advertising partners in order to create a profile of your interests and to show you relevant advertisements on other websites.
Google Analytics & Google Tag Manager
_gid, _ga_<container-id>, _ga, _gat_gtag_<container-id>
Google Ads & DoubleClick
test_cookie, _gcl_au
cebsp_, _ce.s, _ce.clock_data, _ce.clock_event, cebs
OptanonConsent, _sctr, _cs_s, _hjFirstSeen, _hjAbsoluteSessionInProgress, _hjSessionUser_14, _fbp, ajs_anonymous_id, _hjSessionUser_<hotjar-id>, _uetsid, _schn, _uetvid, NEXT_LOCALE, _hjSession_14, _hjid, _cs_c, _scid, _hjAbsoluteSessionInProgress, _cs_id, _gcl_au, _ga, _gid, _hjIncludedInPageviewSample, _hjSession_<hotjar-id>, _hjIncludedInSessionSample_<hotjar-id>
lidc, AnalyticsSyncHistory, UserMatchHistory, bcookie, li_sugr, ln_or
Networking | Cloud | DevOps | IaC
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server is an important element to networking in the real world. User location cannot be predicted as they may be at and out of a desk and up and about should they need to do so. Tying them to a local VLAN may only be helpful if they are bound to desks in those locations, although the most ideal outcome, it is not the most practical.
It is only wise to incorporate IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server in areas where you expect different teams to come to. Meeting rooms could for a moment have the accounting group or the development group meeting there and based on the intelligent and dynamic vlan assignmnet with 802.1x authentication, users port-access are defined their appropriate vlans for their respective access to resources on the network.
How to Provision 802.1 X Authentication Step By Step With Dynamic VLAN Assignment With Windows Radius Server For 802.1x Clients.
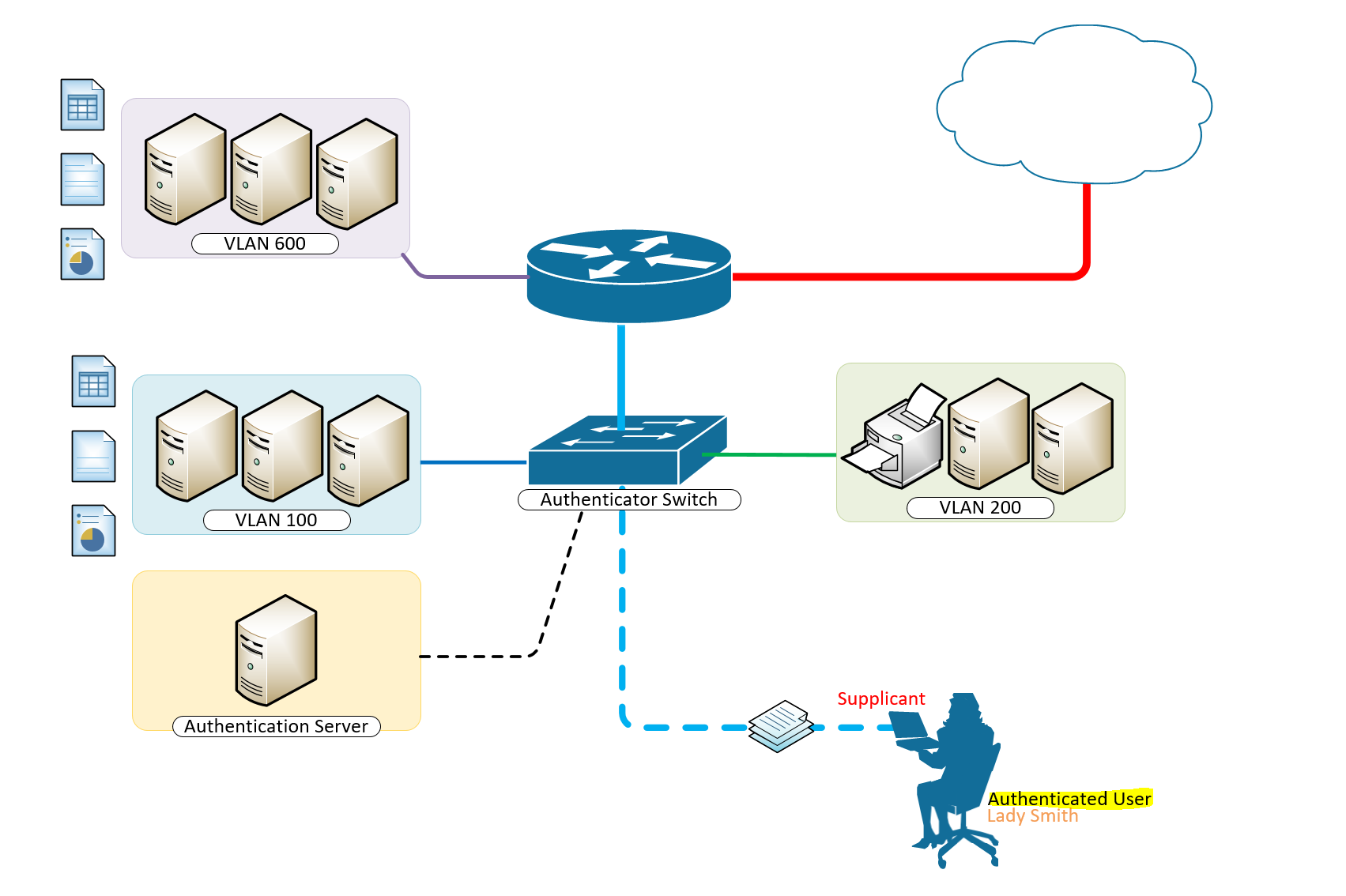
A typical configuration for a system under IEEE 802.1x Authentication control is shown in the following figure.
In this scenario, “Lady Smith” wishes to use services offered by servers on the LAN behind the switch. There are multiple VLANs with resources available based on user vlan membership. Her laptop computer is connected to a port on the Aruba 2920 Edge Switch that has 802.1x port authentication control enabled.
The laptop computer must therefore act in a supplicant role. Message exchanges take place between the supplicant and the authenticator which is the Aruba 2920 Switch, and the authenticator passes the supplicant’s credentials which is her (Windows Active Directory User Account Credentials) to the authentication server for verification. The NPS Server which is the authentication server then informs the authenticator whether or not the authentication attempt succeeded, at which point “Lady Smith” is either granted or denied access to the LAN behind the switch.
Setup Structure for IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
- Supplicant: Laptop running Microsoft Windows 10 or Windows 7
- Authenticator: HP Aruba 2920 Edge Switch
- Authentication Server: Microsoft NPS (Network Policy Server) running on Windows Server 2012 R2.
- User Database : Active Directory
For Windows Infrastructure
Create NPS Server – Add Role on Windows Server 2012 R2
- Create DHCP Scopes for VLANS
Create RADIUS Client on NAC using Network Policy Server
- Create Network Policies
- Configure a Network Policy for VLANs
- Start Wired Auto-Config Service
- Enable Network Authentication
Create the DHCP Scopes for VLAN100 and VLAN200 Groups
- Development Group Scope – VLAN 100
SVI: ip address 172.16.80.254 255.255.255.0 Scope Subnet: 172.16.80.1/24
- Accounting Group Scope – VLAN 200
SVI:ip address 172.16.70.254 255.255.255.0 Scope Subnet: 172.16.70.0/24
Secret Key: secret12
Add Edge Switch Management IP as the RADIUS Client
The Shared Secret Key: secret12 will be used in the Switch Configuration.
Create Network Policy Settings for Accounting Group for VLAN 200
Configuration Example
Here’s an example of how you might consider when configuring Microsoft NPS Server to assign users to a VLAN based on their user group, using NPS for the authentication and authorization of users. This configuration has worked flawlessly on the HP Aruba 2920 Switch. The key to getting this to work is the use of a RADIUS element called: ‘Tunnel-PVT-Group-ID’. This is a RADIUS attribute that may be passed back to the authenticator (i.e. the Aruba 2920 Switch) by the authentication server (i.e. Microsoft NPS Server) when a successful authentication has been achieved. There are a few other elements which need to accompany it, but this is the key element, as it specifies the VLAN number that the user should be assigned to.
The other elements that need to be returned by the NPS Server are as follows:
- Tunnel-PVT-Group-ID: 200
- Service-Type: Framed
- Tunnel-Type: VLAN
- Tunnel-Medium-Type: 802
For Client Infrastructure
On the Supplicant, Windows 7 or 10 configure the following steps on the Ethernet Adapter to enable IEEE 802.1X Authentication
For Network Infrastructure
Connect Server Infrastructure to VLAN 400
Create VLAN for Accounting Group
Create VLAN for Development Group
Create AAA Configuration on Switch for Radius Authentication
Download the Switch Configuration:
Test the IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
Verify Port-Access with the following user groups – VLAN 100 and VLAN 200
Think of what other clever things you can do from the information below;
Breakdown of Commands for RADIUS Authentication
Verification Commands
Thanks for reading. Please share your thoughts in the comment box below;
Published in Configuring , Design , Installing and Configuring , Networking , Security and Switching
- 802.1 x authentication step by step aruba
- 802.1 x authentication step by step cisco
- 802.1 x wireless authentication step by step
- 802.1x authentication process
- 802.1x authentication windows 10
- 802.1x authentication windows server 2012
- 802.1x certificate authentication
- assignment wlc
- cisco dot1x
- cisco ise dynamic vlan
- cisco ise dynamic vlan assignment wlc
- cisco wireless radius attributes
- configuration example
- dynamic vlan assignment cisco 2960 dynamic vlan configuration in packet tracer
- dynamic vlan assignment with windows radius server
- dynamic vlan cisco
- dynamic vlan ruckus
- meraki dynamic vlan assignment
- nps mac authentication wired
- nps policy for mac-based authentication
- radius multiple vlans
- vlan radius server
- vlan steering
- vmps server
How to Fix Dynamic VLAN assignment feature gets disabled automatically in SSID
By: Author Alex Lim
Posted on Last updated: May 3, 2024
Home > How to Fix Dynamic VLAN assignment feature gets disabled automatically in SSID
This article describes why the Dynamic VLAN assignment feature gets disabled
FortiGate, SSID.
By default, the Dynamic VLAN assignment is disabled.
This feature is useful when users need to change the VLAN automatically after changing the connected AP.
See the following image for reference:
By default, it is disabled. However, it can be enabled connect to the RADIUS server to authenticate the user continually while the user is moving across different APs.
As shown above, the Dynamic VLAN assignment is enabled.
However, it will get disabled automatically if the Security method of the particular AP is changed.
As shown in the image above, changing the security method disabled the RADIUS server settings, which meant the Dynamic VLAN assignment settings were disabled.
Log in to ask questions, share your expertise, or stay connected to content. Don’t have a login? Join now .

- Community Home
- Topic Thread
Aruba Central

- Discussion 470
- Members 1.1K
Dynamic VLAN assignment
1. dynamic vlan assignment, 2. re: dynamic vlan assignment.

3. RE: Dynamic VLAN assignment

This is what I'm looking for, but what does one choose in the previous step?

Or do I choose static unamed vlans (since one cannot choose multiple name vlans?) and add all the possible vlans for the MPSK stage?
4. RE: Dynamic VLAN assignment

Ah, you don't assign possible VLANs there. When a user role, or RADIUS response overrides the default VLAN for an SSID, that VLAN will be applied.
So set it in that VLAN screen to any (static) VLAN you want, or maybe a VLAN not in use if you want to enforce that an actual VLAN is derrived during the authentication.
In Instant/AOS10 this works a bit different that what you may have learned with other products as when a clients gets assigned with a VLAN (role/assignment rule/VSA) the AP will just tag all client traffic on the wired uplink port. Of course, your switch port that connects to the AP will need to have all possible VLANs assigned, but on the AP side it's not needed to pre-define the VLANs.
New Best Answer

- Environmental Citizenship
- Support Services
- Contact Support
- Training & Certification
- Software Downloads
- Licensing Login
- Find a Partner
- Become a Partner
- Partner Ready for Networking
- Technology Partner Programs
- Privacy policy
- Terms of service
© Copyright 2024 Hewlett Packard Enterprise Development LP All Rights Reserved.
- Support Forum
- Customer Service
- FortiClient
- FortiAnalyzer
- FortiAuthenticator
- FortiBridge
- FortiCarrier
- FortiConnect
- FortiConverter
- FortiDeceptor
- FortiDevSec
- FortiDirector
- FortiExtender
- FortiGate Cloud
- FortiHypervisor
- FortiInsight
- FortiIsolator
- FortiManager
- FortiMonitor
- FortiNDR (on-premise)
- FortiNDRCloud
- FortiPortal
- FortiRecorder
- FortiSandbox
- FortiSwitch
- FortiTester
- Wireless Controller
- RMA Information and Announcements
- FortiCloud Products
- 4D Documents
- Engage Services
- The EPSP Platform
- The ETSP Platform
- Getting Started Resources
- Technical Learning
- Discussions
- Knowledge Base
- Idea Exchange
- Announcements
- Fortinet Community
- Troubleshooting Tip: Dynamic VLAN assignment featu...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Printer Friendly Page
- Report Inappropriate Content
Created on 05-03-2024 07:00 AM
Troubleshooting Tip: Dynamic VLAN assignment feature gets disabled automatically in SSID

The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges.
- Threat Research
- FortiGuard Labs
- Threat Briefs
- Security Fabric
- Certifications
- Industry Awards
- Social Responsibility
- News Releases
- News Articles
Copyright 2024 Fortinet, Inc. All Rights Reserved.
- Terms of Service
- Privacy Policy
- Cookie Settings

IMAGES
VIDEO
COMMENTS
Dynamic VLAN assignment is one such feature that places a wireless user into a specific VLAN based on the credentials supplied by the user. The task to assign users to a specific VLAN is handled by a RADIUS authentication server, such as Cisco ISE. This can be used, for example, to allow the wireless host to remain on the same VLAN as it moves ...
The simple answer is that dynamic VLAN assignment (or VLAN steering as it is sometimes called) is an excellent technique used to build on the underlying core strategy to control network access. VLAN assignments build on the use of RADIUS to control access to the network. Via RADIUS integration, a WiFi access point (WAP) requires not only an ...
Configuring Dynamic Access Ports on a VMPS Client. To configure a dynamic access port on a VMPS client switch, perform this task: Enters global configuration mode. Enters interface configuration mode and specifies the port to be configured. Sets the port to access mode. Configures the port as eligible for dynamic VLAN access.
Dynamic VLAN, also known as VLAN assignment based on user authentication, is a VLAN configuration method that dynamically assigns VLAN membership to network devices based on user credentials. This approach leverages protocols such as IEEE 802.1X and RADIUS to authenticate users and dynamically assign them to the appropriate VLAN. Dynamic VLANs ...
Common Dynamic VLAN Assignment Use Cases. Network and security administrator most commonly encounter these use cases for dynamic VLAN assignment: The Sales & Marketing department does not need access to R&D resources, while R&D should not have access to the Finance Department resources. Using dynamic VLANs, each department will be placed in the ...
VLAN membership is an authorization to be part of the VLAN. There are two ways to assign VLAN membership to switch ports: Static and Dynamic. Static VLAN membership. It is an easy and straightforward method. In it, you manually add ports to VLANs. ... Dynamic VLAN membership works on a server-client model. In this model, a policy server called ...
Dynamic VLAN assignment separates and isolates devices into different network segments based on the device or user authorization and their characteristics. The flow of traffic between those VLANs is governed by a firewall or another routing device which can then enforce specific network access rules.
Dynamic VLAN Assignment, also referred to as " VLAN Steering ", is exactly what it sounds like. The process of assigning users or groups of users to VLAN can be handled by a RADIUS at the time of authentication, though the infrastructure and expertise needed for dynamic VLAN assignment has historically been an obstacle for smaller ...
In the CLI (host)(config) # interface vlan < id> ip address < address> < netmask> Configuring a VLAN to Receive a Dynamic Address. In a branch office, you can connect a controller to an uplink switch or server that dynamically assigns IP addresses to connected devices. For example, you can connect the controller to a DSL or cable modem, or a broadband remote access server (BRAS).
Dynamic VLANs are assigned to a port based on the MAC address of the device plugged into a port. Dynamic VLAN configuration requires a VLAN ... this mapping is returned to the requesting switch. The VLAN assignment is based on the name returned. If the name is not found on the local switch, the assignment is not made. Configure the VMPS server. ...
• Dynamic VLAN's are based on the MAC address of a PC• Switch automatically assigns the port to a VLAN• Each port can be a member of multiple VLAN's• For Dyn...
After configuration, run the RADIUS server to listen for access requests. Step 2. Create the RADIUS profile. Go to Authentication --- RADIUS Profile, create a new profile bound with the RADIUS server, and check "Enable VLAN Assignment for Wireless Network" to assign VLANs for wireless clients. Step 3.
How to Provision 802.1 X Authentication Step By Step With Dynamic VLAN Assignment With Windows Radius Server For 802.1x Clients. A typical configuration for a system under IEEE 802.1x Authentication control is shown in the following figure. In this scenario, "Lady Smith" wishes to use services offered by servers on the LAN behind the switch
Dynamic VLAN assignment allows clients to connect to the network anywhere and, based on their credentials, they get placed in the correct VLAN irrespective of the ports to which they are connected. MAC authentication and 802.1X authentication support dynamic VLAN assignment, where a port can be placed in one or more VLANs based on the attribute ...
Creating VLAN Assignment Rules for Dynamic VLAN Assignment in Bridge Mode. To create a VLAN Virtual Local Area Network. In computer networking, a single Layer 2 network may be partitioned to create multiple distinct broadcast domains, which are mutually isolated so that packets can only pass between them through one or more routers; such a domain is referred to as a Virtual Local Area Network ...
By default, the Dynamic VLAN assignment is disabled. This feature is useful when users need to change the VLAN automatically after changing the connected AP. See the following image for reference: Dynamic_vlan_disable.PNG. By default, it is disabled. However, it can be enabled connect to the RADIUS server to authenticate the user continually ...
Dynamic VLAN assignment is one such feature that places a wireless user into a specific VLAN based on the credentials supplied by the user. The task to assign users to a specific VLAN is handled by a RADIUS authentication server, such as Cisco ISE. This can be used, for example, to allow the wireless host to remain ...
Dynamic VLAN assignment. 1. Dynamic VLAN assignment. We've come from Extreme to Aruba and recently purchased several AP505s. We would like to set up a dynamic vlan assignment based on a MPSK Local passphrase. I believe I've got most of the settings correct, but when I try to connect, obtaining an IP address from our external DHCP server fails.
As shown above, the Dynamic VLAN assignment is enabled. However, it will get disabled automatically if the Security method of the particular AP is changed. As shown in the image above, changing the security method disabled the RADIUS server settings, which meant the Dynamic VLAN assignment settings were disabled. Related document: