Home PowerPoint Templates Business PowerPoint Templates Cybersecurity Presentation Template

Cybersecurity Presentation Template
Are you looking for an interactive presentation template for your cybersecurity seminar? Then try our 100% editable Cybersecurity Presentation Template. This cybersecurity PPT template is a slide deck prepared using customizable elements to discuss various aspects of the importance of cybersecurity. It starts with a title slide, showing imaginative lines to represent how the devices and online surfing are secured with the cybersecurity protocols. All slides have a similar background and a unique dual-shaded color scheme. Next to the title slide , the following slides are for presenting general topics about cybersecurity, such as introduction, key importance points, and threats.
Further, this template provides personalized slides for presenting company or agency details, e.g., why choose us, services, team members, success stories, data protection protocols, and testimonials. We have also added the preset layout for adding pricing plans to subscribe to the company.
In this era, cyber threats are rising with every passing day. Thus, companies always need external parties to manage the impending threats whenever they launch their online services, applications, or products. For that, many agencies have developed teams of experienced ethical hackers and engineers to protect their clients’ products from harmful cyber attacks. This Cybersecurity Presentation Template is specially crafted for such companies to help them display their services and expertise in this field. They can conveniently download and edit this template to present the main highlights of their company and working methodology. The business PowerPoint template can be adapted to the required theme settings by changing the color scheme and graphical elements. The slides are well-designed for adjusting relevant information. For instance, the global footprint slide has an editable map with a guiding chart, and the success story slide has highlighting text boxes to show the keypoints. Likewise, the data protection process slide has a modern flow diagram with icons. So, presenters can edit the placeholder text boxes and create their personalized presentations in a go. Download and edit this template now!

You must be logged in to download this file.
Favorite Add to Collection
Details (13 slides)

Supported Versions:
Subscribe today and get immediate access to download our PowerPoint templates.
Related PowerPoint Templates

Simple Business Overview PowerPoint Template
Internal vs External Factors SWOT PowerPoint Template
Horizontal SWOT PowerPoint Template
External & Internal Factors SWOT Analysis PowerPoint Template
- Home Accounts
- Business Accounts
- Canada/English
- Deutschland
- New Zealand
- South Africa
- United Kingdom
- United States
Why Businesses Need Security Awareness Training
If you’re a business, you might think you don’t need to educate your end users about cyberattacks, compliance issues, and other risks they face online. If you’re an MSP, maybe you have clients who don’t yet see the value of security awareness training. Either way, here are some facts that will help build a strong case. Need help making that case to someone else? Download our Security Awareness Training PowerPoint presentation.
Let's Start with the Facts
Many businesses think they’re too small to be a target, or that their end users already know how to avoid phishing. But every business is a target, and cyberattacks are expensive enough that a single breach could be disastrous. When you understand the real-world risks and statistics around actual end user behavior, the importance of training is pretty undeniable. Here are 6 reasons why security awareness training is crucial for businesses.
1. If you think your end users know better… they probably don’t.
Hackers use social engineering attacks to take advantage of end users’ curiosity, trust, fear, negligence, and greed to drop malware on business networks. More importantly, 49% of employees admit they click links in messages from unknown senders while at work. 1 When you consider that 1 in 50 URLs is malicious 2 , businesses really can’t afford to have half their workforce taking these kinds of risks.
2. The average person has terrible online habits.
Of workers who are certain their personal information has been compromised in a cyberattack, more than one-third didn’t even bother to change their account passwords afterward! 1 In fact, 67% of workers worldwide are certain they have received at least one phishing email at work. Of those, nearly 40% didn’t report it to anyone, let alone their company’s IT or security teams. 1 Ouch.
3. The threats just keep on coming, and phishing isn’t going away.
According to the 2019 Verizon Data Breach Investigations Report, most breaches involve phishing and the use of stolen credentials. 3 Because phishing continues to be such a successful method for breaching business networks, cybercriminals are going to keep using it. And they’re getting better at looking convincing; nearly 1 in 3 phishing sites use HTTPS to give page visitors a false sense of security. 2
4. Criminals often target small businesses BECAUSE they are small.
Hackers are banking on small and medium-sized businesses (SMBs) believing they won’t be targeted due to their size. The bad guys also know that, while SMBs can hold a fair amount of private and financial data, they are significantly less likely to have the resources to invest in comprehensive security programs. Not only that, but because a single small business could have connections to other, larger companies, they may be targeted simply so that criminals can gain access to systems belonging to “bigger fish”.
5. Many businesses are subject to compliance regulations that require training.
If a business operates in healthcare, finance, retail, insurance, or energy, these industries typically require end user awareness training at least annually. Basically, if a company takes credit card payments or wire transfers for any reason; or stores customers’ personal data (SSNs, account numbers, payment card data, etc.) for any length of time; then it’s critical for them to look into the applicable compliance and/or cybersecurity regulations ASAP. The fines for non-compliance can be painfully high. Why risk that?
6. When you consider the costs of a breach, training has pretty significant ROI.
Did you know the average total cost of a data breach is now up to $3.92 million? 4 Or that 90% of the malware businesses encounter is delivered via email? 3 If you could stop employees from falling victim to phishing and email malware, you’d do it, wouldn’t you? Well, the results of training speak for themselves. After 12 months of ongoing phishing simulations and security awareness training courses, end users are 70% less likely to click through on a phishing message. 5 When you consider all these numbers together, it’s pretty clear that training can save you a lot of time and headache—not to mention money.
1 Webroot Inc. “Hook, Line, and Sinker: Why Phishing Attacks Work.” (September 2019)
2 Webroot Inc. “2019 Webroot Threat Report: Mid-Year Update.” (September 2019)
3 Verizon. “2019 Data Breach Investigations Report.” (May 2019)
4 IBM. “2019 Cost of a Data Breach Report.” (July 2019)
5 Webroot Inc. “2019 Webroot Threat Report.” (February 2019)
Read about the Webroot solution for business security awareness training
Webroot can help.
Start a free 30-day,no-risk, no-software-conflict trial today to see the Webroot difference for yourself. Have other questions on implementing MSP-friendly security awareness training? Ask away.

Welcome back!
Stay protected and renew your subscription before it's too late.

Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories

Cybersecurity awareness training powerpoint presentation slides
Introducing our cybersecurity awareness training PowerPoint presentation slides. Spread awareness about the matters of cyber security in your team with the help of this IT security awareness PPT layout. Explain malware attacks and hacking to the employees of your company with the help of our internet safety PowerPoint design. This well built network protection PPT theme contains a slide that lets you talk about the new strategies of learning about cyber security. Associate with this cyber protection recognition PowerPoint set to provide justification for the need of having an automated cyber security awareness program. This security reliability PPT bundle contains a slide that elaborates on the budget allocation for the cyber security awareness program. The network security apprehension PPT deck lets you make required variations to the icons and colors making our PPT more practical. Choose our computer security awareness PowerPoint design to showcase organization and assurance. Download our cybersecurity ppt slide to explore true perfection.

- Add a user to your subscription for free
You must be logged in to download this presentation.
Do you want to remove this product from your favourites?
PowerPoint presentation slides
Presenting our cybersecurity awareness training PowerPoint presentation slides. This PowerPoint design contains fifty-one slides in it which can be completely customized and edited. It is available for both standard as well as for widescreen formats. This PowerPoint template is compatible with all the presentation software like Microsoft Office, Google Slides, etc. It can be downloaded in varying formats like JPEG, PDF, PNG, etc. You can download this PPT layout by clicking on the button below.

People who downloaded this PowerPoint presentation also viewed the following :
- Business Slides , IT , Flat Designs , Teamwork , Complete Decks , All Decks , Communication Process , IT , Cyber Security
- Cybersecurity Awareness Training ,
- Organization ,
- Communication
Content of this Powerpoint Presentation
The Mailchimp incident that happened in 2023 reminds us how important it is to watch out for online dangers. This cyber-incident itself was the reinforcement of, Nobody can mess with your security unless you give them a chance. It showed that even the most password-secure tools that our employees use daily can pose a threat to the company’s integrity.
Since, employees represent the face of the company, and in such instances, they are usually the first ones to face cyber threats. Therefore, organizations need to train their staff to combat these threats or avoid falling for their tricks altogether.
Such Cyber Security awareness training should focus on educating employees on potential risks they may face, allowing them to safeguard the firm and themselves from any cyber threat.
Companies may initiate cybersecurity awareness training for a number of reasons. These could be for improving existing security, creating cyber threat visibility, or for regulatory compliance.
SlideTeam’s 100% customizable Cybersecurity Templates are designed to help you educate your team on cybersecurity in a way that's tailored to your organization's needs.
Let’s uncover a powerful complete deck of Security Awareness Training Templates and examine its features, customization options and interactive assessments.
Slide 1: Cyber Attacks Experienced By the Company in Previous Financial Year
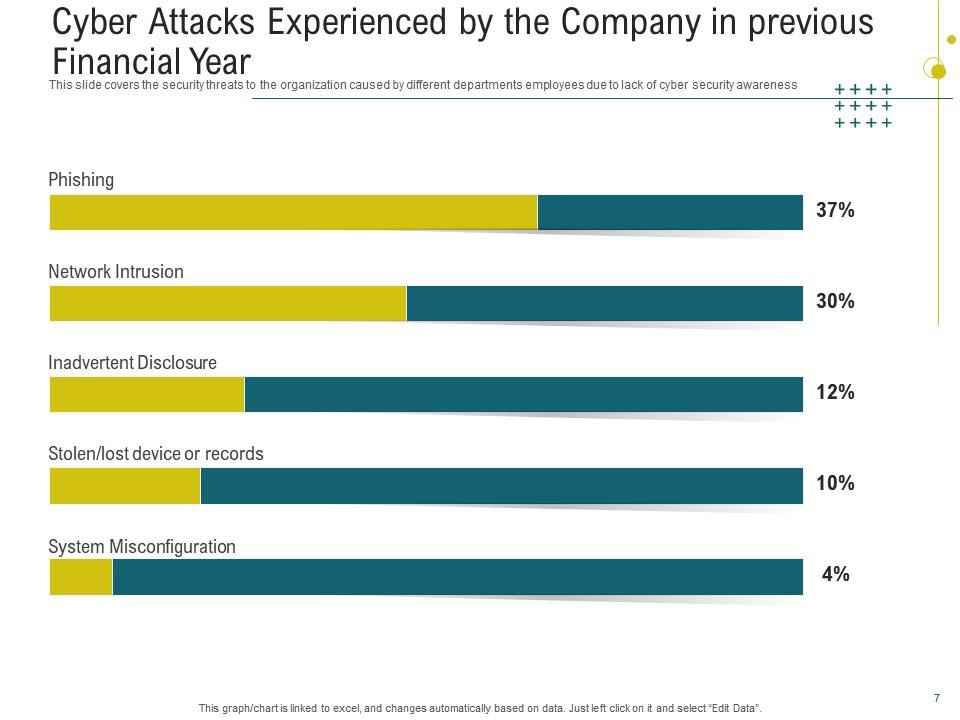
A precise risk assessment is crucial for identifying the company's vulnerabilities and allocating security solutions appropriately. This PPT Slide allows you to develop future preventions by learning from previous cyber assaults. It also allows you to examine your present security posture and identify opportunities for improvement. This presentation template also serves as a reporting tool for stakeholders to make strategic decisions on cybersecurity investments.
Slide 2: Security Training Program Frameworks
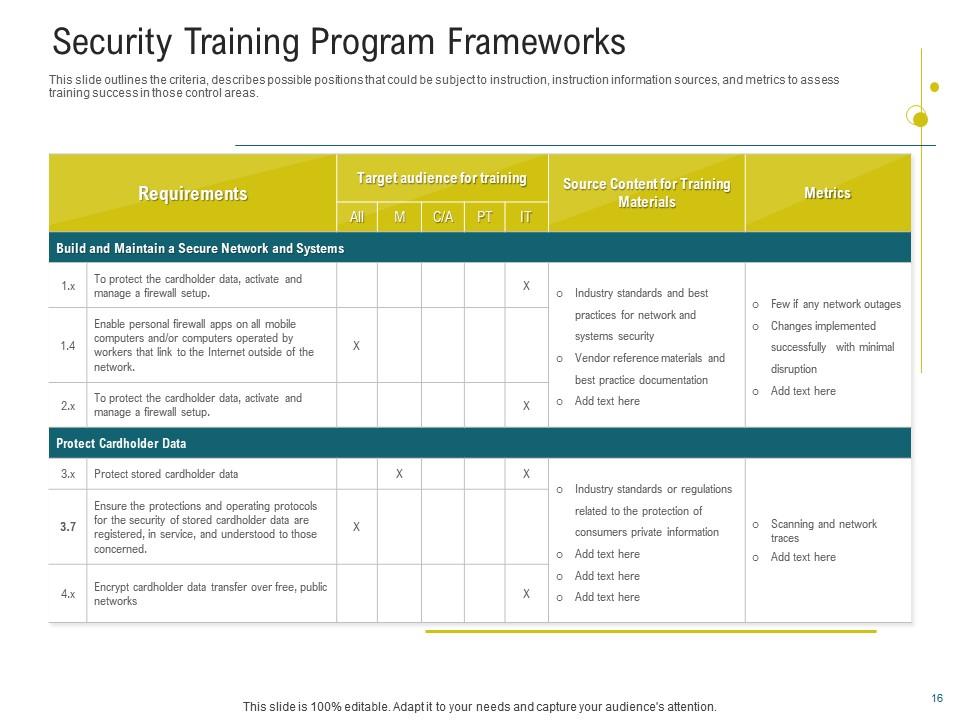
This comprehensive cybersecurity training slide covers different sections to provide a clear roadmap for enhancing organizational cybersecurity resilience. Using the requirements section, you can outline the objectives of your cybersecurity training program. Next, under the Target Audience for Training section, specify who will be receiving cybersecurity instruction. You may also provide case studies and real-world examples of cyber mishaps. The presentation also lists the leading performance indicators for evaluating your training efficacy. The use of yellow and green tones effectively conveys a sense of professionalism and dependability. A clean and straightforward presentation layout ensures that each part of the training framework is clearly defined.
Slide 3: Security Training Program Contd.
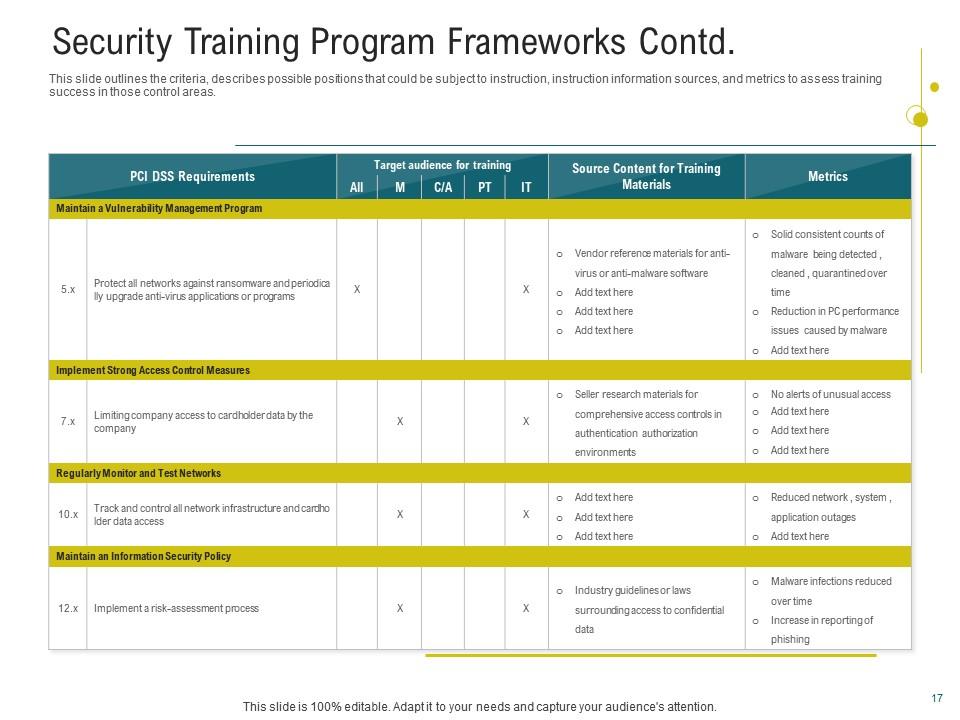
Use this PPT Layout to outline the scope, clear criteria, and objectives of your training program. Customizing training materials to match employees' needs defines training success. A separate Target Audience section in the slide proves how clearly it guides you. It emphasizes the significance of tailoring information to specific demographics' learning goals and preferences. Every moment matters when it comes to system security, so make the most of it by setting up and executing effective cybersecurity training campaigns within your company before hackers gain access to your systems and data.
Slide 4: Organization Compliance Metrics
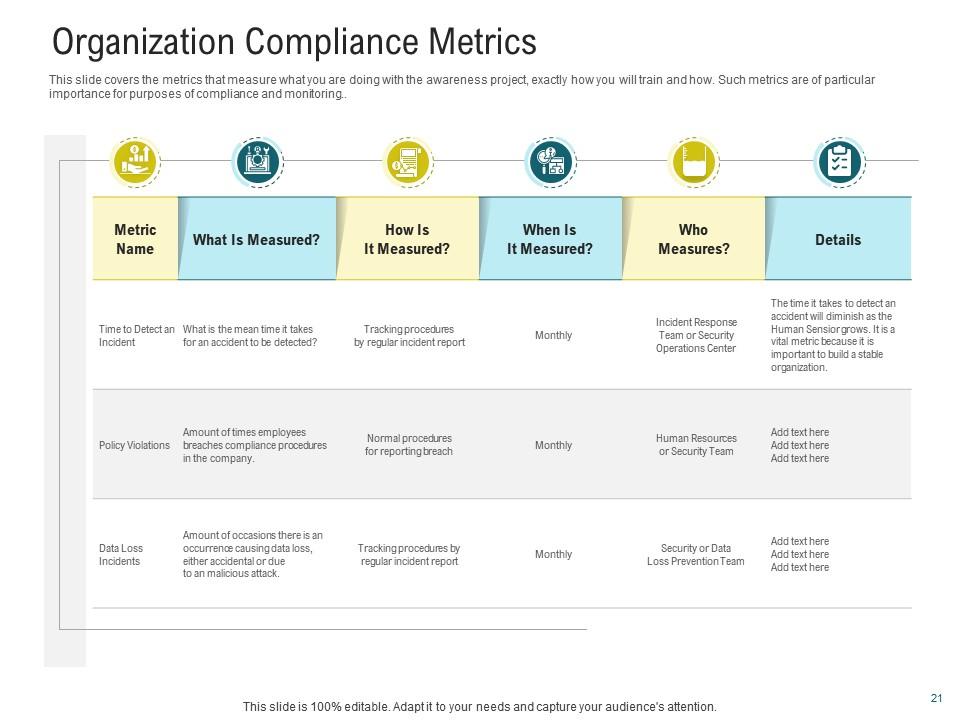
This PPT Template provides segments on What is Measured to describe the achievement of your set objectives. There is a section on How it is Measured as well. This provides ongoing tracking of how events unfold. It also specifies who will be in charge of administering the project and ensuring that everything works well. Deploy this PPT Slide's refreshing combination of spring daffodils and cyan shades to draws attention and promote audience involvement in exploring the importance of compliance.
Slide 5: The ROI of Security Awareness Training
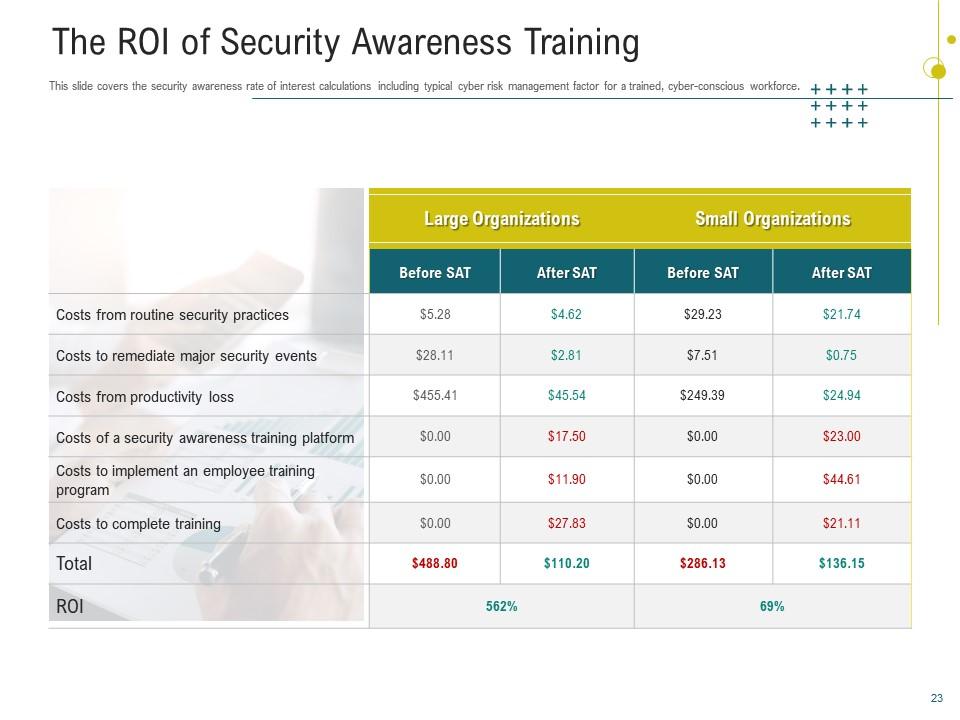
Use this PPT Slide to show how a skilled, cyber-conscious workforce may help your organization manage those risks. This presentation layout helps determine the return on investment for security awareness training. It allows you to determine whether security awareness training is worthwhile by examining how much better your security becomes as a result of the training.
Slide 6: Communication Plan for CyberSecurity Events and Incidents
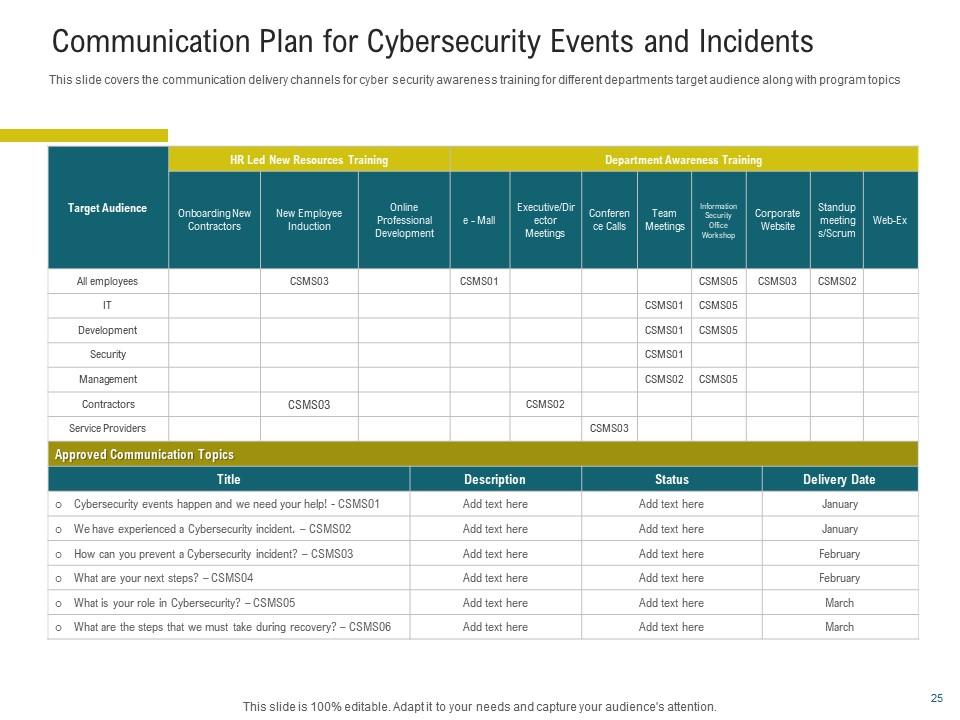
This PowerPoint Design goes beyond just identifying communication channels. It precisely defines a complete framework to ensure that information flows efficiently and participants are notified correctly in the case of a cybersecurity incident. Employ it to outline the roles of various team members clearly. Establish dates and procedures for alerting relevant stakeholders. It makes it easier for teams dealing with a cyber challenge to collaborate and solve problems more effectively.
Slide 7: Employee Security Awareness Training Budget
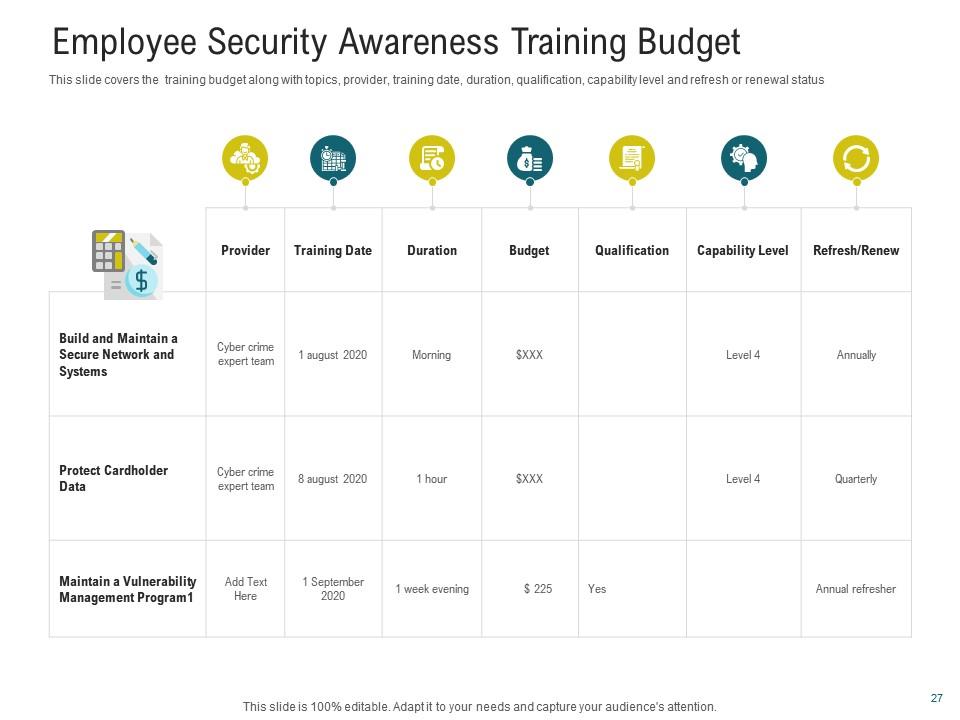
Well-trained staff can quickly identify and respond to security issues, reducing the potential for hacking and assaults. By implementing security awareness training, businesses can avoid costly data breaches and legal fees, resulting in long-term cost savings. This PPT Layout includes critical elements such as the date, money allocation, targeted capability levels, and renewal considerations for planning training sessions.
Slide 8: Security Awareness Program Timeline
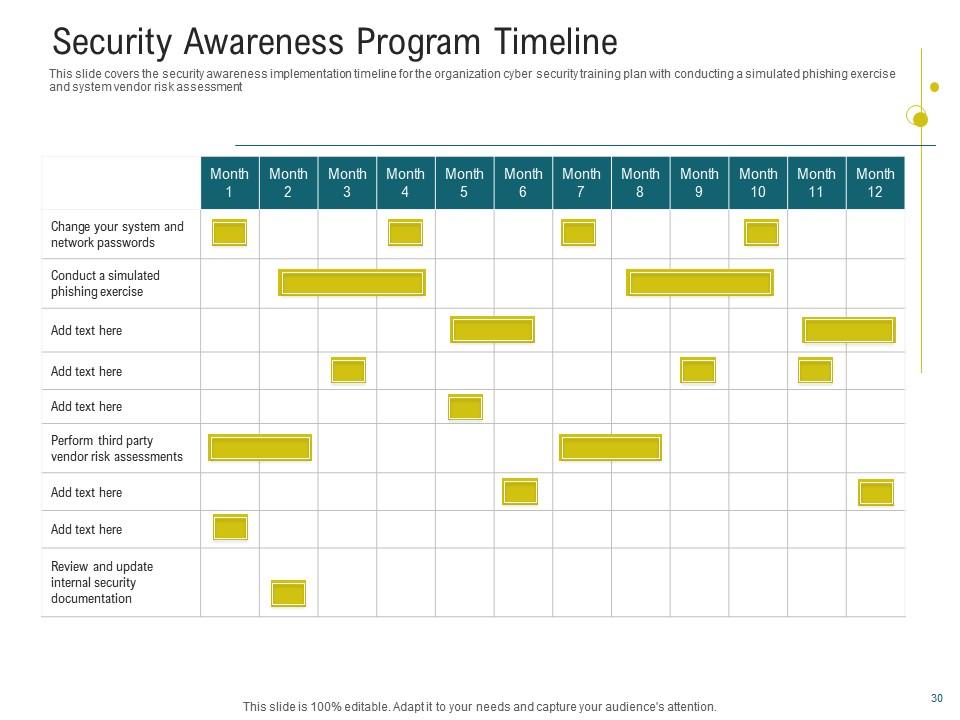
Employ this PPT Template to establish a comprehensive cybersecurity training strategy in your firm. The presentation template includes two essential exercises. The first is a simulated phishing exercise in which staff are given bogus emails to see if they prey on phishing scams. It functions as a wake-up call and promotes a culture of vigilance among employees. Another function is a critical examination of system vendor risks, which includes monitoring external threats posed by outside vendors. This proactive strategy not only strengthens the organization's resilience to developing cybersecurity threats but also develops a culture of collective responsibility in which everyone plays an integral part in protecting sensitive data and maintaining organizational integrity.
Template 9: Impact of Security Awareness Training
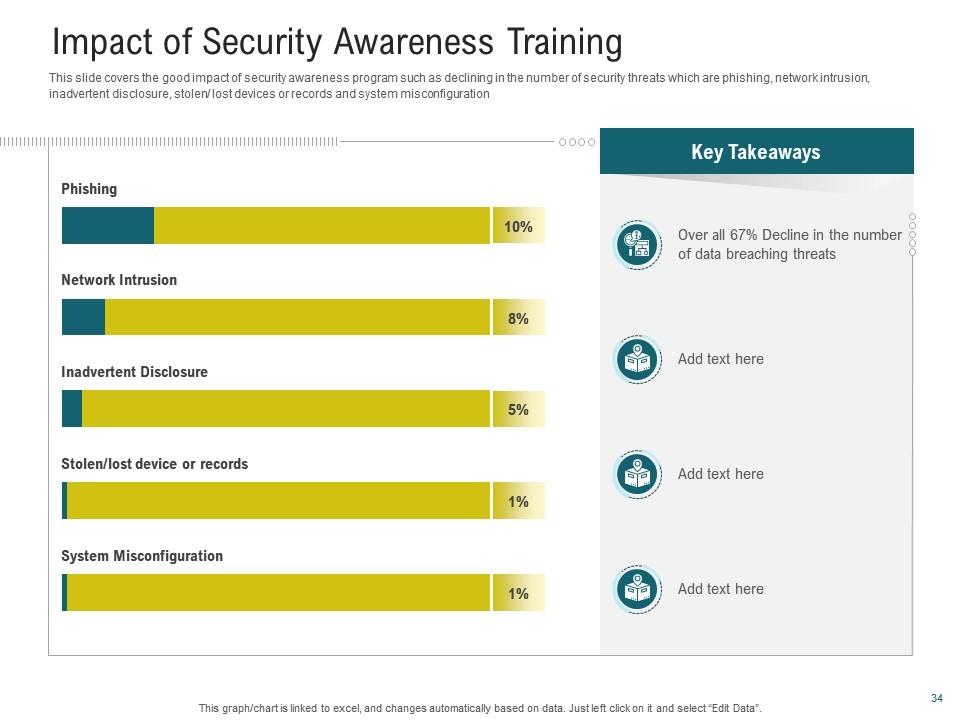
This PowerPoint Design provides the complete framework to ensure that information flows efficiently and participants are notified correctly in the case of a cybersecurity incident. Employ it to outline team members' duties and roles clearly. Establish dates and procedures for alerting relevant stakeholders. It makes it easier for teams dealing with a cyber challenge to collaborate and solve problems more effectively. This PPT Layout includes the date, money allocation, targeted capability levels, and renewal considerations for planning training sessions.
Slide 10: Organization Cyber Security Dashboard
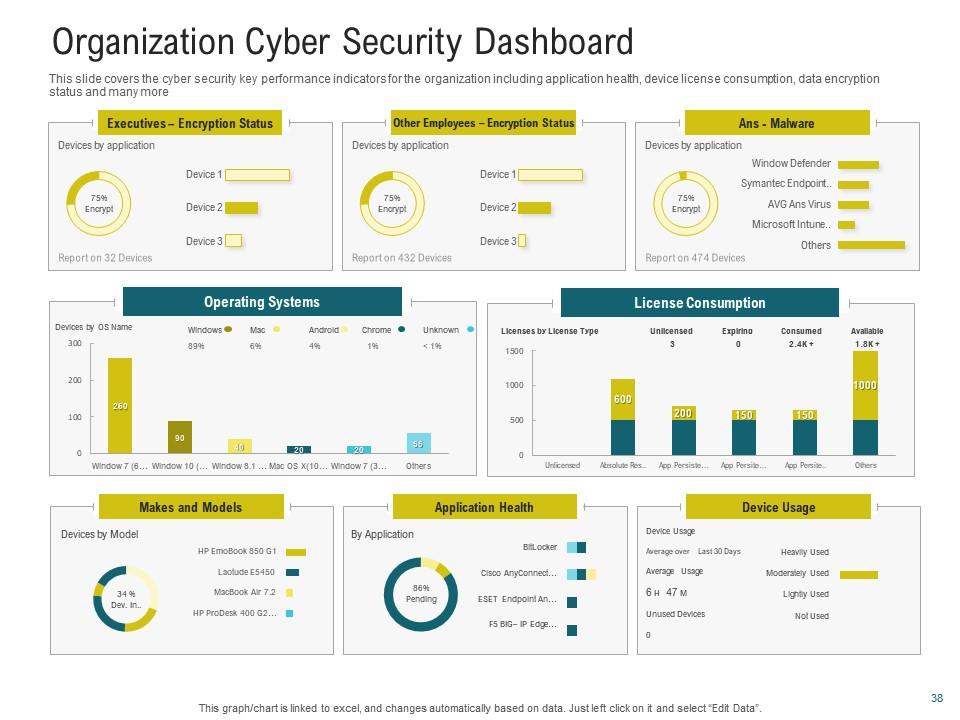
Detect security incidents as they happen using this PPT Dashboard. The slide also depicts real-time monitoring of cybersecurity indicators. It provides centralized visibility into the business's cybersecurity environment. That enables you to integrate data into a single, intuitive interface. The slide's alerting features notify cybersecurity teams of questionable behaviors as soon as they occur. The critical indicators on the slide are: application health, device license consumption, data encryption state, etc.
Supercharge your Anti Phishing Defense with our PPT Templates
Most safety breaches happen due to human error. SlideTeam's comprehensive and 100% customizable cybersecurity awareness training templates will assist you in turning each employee into a cyber defender. These security awareness training templates will train your workforce to think critically about their data and data hygiene, what they get in their inbox, how to respond, and how to keep information safe in their physical offices.
Cybersecurity awareness training powerpoint presentation slides with all 51 slides:
Use our Cybersecurity Awareness Training Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.

Ratings and Reviews
Items 1 to 10 of 11 total
- You're currently reading page 1

by Edgar George
December 15, 2021
by Williams Morales
by Clement Patel
by Cletus Ross
by Dorsey Hudson
by Douglass Riley
July 13, 2021
by Chester Kim
May 26, 2021
by Alexander Ramirez
by Cristopher Cole
by Dexter Weaver


16 Trending Cyber Security Seminar Topics for 2023

Cybersecurity is securing computer systems from unauthorized access, theft, damage, and other internet-based threats using modern technologies.
Also, it helps you maintain the confidentiality and integrity of the data so that the user’s privacy isn’t compromised.
We know, in this modern world where we need the internet in our daily lives, how important it is to know about cybersecurity and let others know, and the best way to let others know is through a seminar.
So, let’s discover 16 trending ybersecurity seminar topics.
16 Updated seminar presentation topics on cybersecurity
Let’s get to know the best seminar topics on cyber security, which will help you spread awareness about the topic.
1. The rise of ransomware: detection, prevention, and response strategies
Ransomware is one of the most dangerous malicious software mostly used by cybercriminals. These cyberweapons encrypt an organization’s data, and the criminal demands money from the company to receive the decryption key.
Possible topics you may include in your seminar presentation:
- Why the rate and the scale of ransomware attacks are increasing
- Types of ransomware
- Examples of high-profile ransomware attacks
- Role of using anti virus software to protect from ransomware attacks
- Ransomware detection and prevention strategies
2. Cybersecurity for small businesses: best practices and cost-effective solutions
Cybercriminals often target small businesses because of the less competent cybersecurity mechanism and an acute lack of data backup and protection knowledge.
Possible topics to cover in the seminar presentation:
- What are the primary cyber attack types that small businesses often face?
- Share recent examples of cyber attacks against small businesses
- How to implement a risk management framework?
- Role of cybersecurity training programs to spread awareness
- Introduction to cybersecurity regulations and standards such as GDPR and HIPAA
- Cybersecurity best practices for small businesses
3. Artificial intelligence in cybersecurity: opportunities and risks
Artificial intelligence is feeding data to a system and making it capable of doing a few things automatically without much human intervention.
It requires intense knowledge of computer science, programming, coding, etc. It is an ever-evolving field that has now started revolutionizing the cybersecurity field, also.
- The opportunities and threats of implementing AI in cybersecurity
- Introduction to deep learning and cyber security
- Examples of NLP applications in cybersecurity
- How AI is used in incident response, including automated incident analysis and response
- Explain how AI is changing the grand landscape of threats
Find the best seminar topics for computer science for final-year students .
4. The future of passwords: alternatives and innovations for secure authentication
Passwords are the oldest forms of securing a digital asset or a device. However, with the passing of time and the advent of cyber criminals, passwords have become easy to crack, insecure, and inconvenient.
Thus, there was a demand for alternative methods of securing a device. Face locks, iris scanners, and fingerprint sensors answered the demands.
Possible topics to cover in this seminar:
- Introduction to password-based authentication
- Explanation and examples of biometric authentication
- How Multi-Factor Authentication (MFA) words
- Explanation of zero-trust security (with examples)
- Role of continuous authentication and blockchain-based authentication
5. Cybersecurity and IoT: challenges and solutions
The Internet of Things (IoT) , better known as IoT, refers to the network of devices, vehicles, buildings, and anything with electro and software embedded to exchange data. IoT devices are increasing with changing times, and these devices are susceptible to cyber-attacks.
Sub-topics to cover in your seminar on cyber security and IoT:
- Introduction to cybersecurity threats and vulnerabilities faced by IoT devices
- Highlight common security challenges faced by IoT devices including lack of encryption.
- How to maintain the end-to-end security of these devices
- Emerging IoT security technologies
- Recommend cybersecurity leadership training programs to the audience
6. Ethical hacking: testing the security of your systems
Ethical hacking is a way of gaining authority over a computer by legal means. It is opposite to what people mean by regular hacking. Nevertheless, it is a practice that is prevalent in defence organizations all around the world, especially in the cybercrime branch.
You may include the following topics in the seminar:
- Introduction to ethical hacking and malicious hacking
- Highlight types of ethical hacking such as penetration testing, vulnerability scanning, etc.
- How ethical hacking works
- Web Application Security Project (OWASP) methodology
- Types of ethical hacking tools like network scanners, vulnerability scanners, etc.
7. Cybersecurity in the cloud: risks and strategies for protection
Data storage in the cloud is backing up data not in your hard drives but on the internet or in the servers and systems of some other company. Google Drive is an excellent example of cloud storage.
Nowadays, the cloud is a place for storage, computing, and other intellectual work.
- Companies based on cloud technologies
- Introduction to Cloud Service Provider (CSP) security
- Help companies assess the potential risks associated with the cloud environment
- How companies can presevnt cybersecurity issues
📌 Relevant pick for you: Cybersecurity advantages and disadvantages
8. The human factor in cybersecurity: addressing insider threats and social engineering
One of the weakest links when discussing cybersecurity is human negligence and human error, which leads to significant scale loss of revenue for a company due to data breaches and cyber-attacks. However, there are different ways employers can consider when training their employees about cybersecurity.
The employer can conduct a seminar to discuss a few points:
- How critical cybersecurity is for the company?
- Help people better understand the internet’s potential risks and threats
- Types of human-related security incidents such as insider threats, social engineering attacks, and phishing.
9. Cybercrime and law enforcement: cooperation and challenges
With the increasing number of cybercrime cases worldwide, the laws surrounding the correct use of the internet and giving justice to people and businesses who are victims of cyberattacks have become pretty tough.
However, every country has a vigilant cyber crime department that keeps a keen eye on the cybersecurity affairs of both attacks inside and outside the country.
Topics you may cover:
- What kind of cyber-attacks does the business face or may face in the future?
- Law enforcement in investigating cybercrime
- Introduction to government’s policies and laws for cybersecurity
- Best practices to prevent strategies for cybercrime
📌 Further resources on cyber security:
- What is cloning in cyber security?
- What is shimming in cyber security?
- Is cybersecurity hard to learn for a beginner?
- What is spooling in cyber security (with pros & cons)
- Handpicked cyber security training classes in Mumbai
10. Cryptography: The science behind data protection
Cryptography is the practice of encrypting data and then decrypting it. It is one of the most prominent cybersecurity domains and a fascinating subject.
Cryptography helps secure your data and prevents cybercriminals from catching your data midway, and even if the person gets the data, he won’t get any information because of the encryption.
Instead, the criminal will require a decryption key. Cryptography also helps in the production of the decryption key.
The seminar may cover topics:
- Introduction to cryptography and its application
- Explain encryption algorithms, decryption algorithms, and keys
- Explain techniques, such as symmetric-key cryptography, public-key cryptography, and hash functions
- Cryptographic Protocols and standards
11. Zero Trust Architecture: Reimagining network security
Zero Trust Architecture, or ZTA, is a security model that grants permission to no users and devices without proper authentication. As a result, it is a highly secure network and doesn’t allow malicious attacks.
As traditional perimeter-based security techniques are becoming obsolete with changing times, ZTA is the way to go. Thus, a seminar is crucial to make people:
- Aware of the technology
- Explain zero trust network access (ZTNA)
- Introduction to Zero Trust security and how it works
- Types of ZTA models and their benefits
- Best practices for implementing the ZTA
12. Biometric authentication: challenges and opportunities
Biometric authentication is not a technology for the future. It has been there for many years and constantly evolving, like fingerprinting, facial recognition, and iris scanner.
However, not only does the authentication model have numerous benefits but also many challenges.
Topics you may cover in your presentation:
- Potential vulnerabilities linked to biometric authentication
- Best practices for implementing biometric authentication
- Types and benefits of biometric authentication
- How do biometrics work for authentication?
13. Cyber insurance: understanding policies and coverage
Because of awareness, most people worldwide don’t know they can be insured against cyber threats. Cyber-attacks are rampant in this modern world, cyber-attacks are rampant, and their risks include potential losses. To reduce the damage and losses, a seminar is essential.
A seminar on cyber insurance can help people become:
- Advantages, disadvantages, and types of cyber insurance
- Explanation to network security
- Computer data loss and restoration
- Market and future trends in cyber insurance
14. Quantum computing and cryptography: what’s the future?
Quantum computing is a revolutionary technology that has taken the world by storm. It helps in faster processing, more power, and speed.
However, quantum computing may pose a challenge to cryptographic systems, and many people are unaware of it.
Topics to cover:
- Explanation of how quantum computing poses a threat to traditional cryptographic systems
- Introduction to quantum key distribution
- Challenges in building a practical quantum computer
- Google’s quantum supremacy claim
15. Incident response and recovery: best practices for managing cyber attacks
Incident response and recovery plans are significant for tackling sophisticated cyber-attacks. Moreover, different kinds of cyber-attacks pose different levels of danger for an organization. Thus, the company must keep itself prepared for such a disastrous event.
Some topics to cover in this seminar:
- Best practices for managing a cyber-attack
- Explanation of the incident recovery process
- Highlight different phases of cybersecurity implementation
- Security information and event management (SIEM) systems
📌Relevant article: Do you need math skills to become a cybersecurity expert?
16. Cybersecurity in healthcare: best practices and compliance requirements
Healthcare is one of the essential departments of any country. It is essential and confidential, which shouldn’t go out into the hands of the public. But what will happen if there is a data breach in the system? What should the owners of the hospital know about?
The computer systems of healthcare departments should have robust cybersecurity systems. A seminar can make people:
- Possible cybersecurity threats in the healthcare industry
- Cybersecurity in healthcare laws and regulations
- Types of cyber-attacks in healthcare such as web application errors, System intrusions, etc.
- Introduction to HIPAA security rule
- Explanation of access control and authentication strategies for healthcare
Final words
Seminars are a great way to spread awareness about a particular event or to market your brand and product. It instantly impacts a lot of people, and knowledgeable people are the ones who bring change to this world.
Cybersecurity is an evolving field, and the more people become aware of it, the faster it grows.
We hope you’ll like this list of seminar topics on cyber security and nail your next seminar presentation.
10Pie Editorial Team is a team of certified technical content writers and editors with experience in the technology field combined with expert insights . Learn more about our editorial process to ensure the quality and accuracy of the content published on our website.

10Pie is your go-to resource hub to start and grow your Tech Career.
Send us your queries at [email protected]
CAREER GUIDES
- Data Science
- Cyber Security
- Cloud Computing
- Artificial Intelligence
- Business Intelligence
- Contributors
- Tech Glossary
- Editorial Policy
- Tech Companies
- Privacy policy
📈 Tech career paths
- AI career paths
- Python career paths
- DevOps career paths
- Data engineer career paths
- Data science career paths
- Software testing career paths
- Software engineer career paths
🏆 Tech courses
- Cloud computing courses in Pune
- Data analytics courses in Hyderabad
- Data science courses in Mangalore
- Cloud computing courses in Hyderabad
- Data analytics courses in Indore
- Data analytics courses in Mumbai
- Data analytics courses in Pune
📌 Featured articles
- AI seminar topics
- Which tech career is right for me?
- Will AI replace software engineers?
- Top data annotation companies
- Cyber security career roadmap
- How Tesla uses Artificial Intelligence
- Cloud computing seminar topics
© 2023 All rights reserved. All content is copyrighted, republication is prohibited.
Question? Call Us +1 785.370.3444

Cybersecurity Awareness Presenter
Awareness Training (Presenter)
Cybersecurity Awareness training slides

Get active in your community
Our team dedicated months to crafting top-tier cybersecurity awareness training material, meticulously refining it with feedback from professionals across various fields, including information security and IT. We spared no effort in perfecting the content, presenting it extensively throughout the central United States, both publicly and in closed-door sessions.
And then, we made a bold decision—we gave it away. Our commitment to advancing cybersecurity awareness led us to release the presentation to the public, free of charge. The response was overwhelming. Within the first six months of its release in late 2019, the material was downloaded thousands of times in over 150 countries worldwide.
But the impact didn’t stop there. Our presentation garnered widespread recognition within the industry, being shared repeatedly by numerous industry experts and featured at some of the most prestigious security conferences across the globe. Our mission to promote cybersecurity awareness had truly resonated on a global scale.
At TreeTop Security, we believe that knowledge is power, and we’re dedicated to sharing our expertise for the greater good. Join us in our mission to empower individuals and organizations worldwide with the knowledge and tools they need to stay safe in an increasingly digital world.
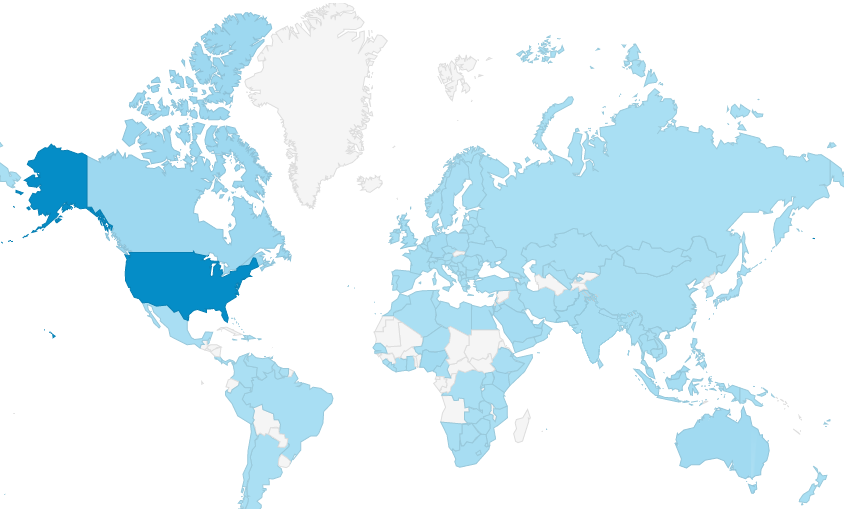
Cybersecurity awareness spanning the globe!
Downloaded in over 150 countries… and counting!
Open Source Training Platform
You read that right… fREE!
At TreeTop Security, we recognize that as just one company, our ability to make a widespread impact on cybersecurity is limited. That’s why we’re committed to extending our reach far beyond our own capabilities by embracing open-source initiatives.
Our decision to release our cybersecurity awareness training material as open-source content was driven by a desire to empower individuals and communities to take charge of their own cybersecurity education. By making tried-and-true material freely available, we aim to catalyze a grassroots movement of end-user training across the globe.
But the benefits extend beyond warm, fuzzy feelings. Presenting this material offers tangible advantages:
Empowering Communities : By educating people in your community, you’re arming them with the knowledge and tools they need to protect themselves from a wide range of cyber threats, from phishing emails to phone and SMS scams.
Personal Development : Presenting the material improves your own presentation skills, boosting your confidence and effectiveness as a communicator.
Recognition as an Expert : By sharing your knowledge, you establish yourself as a subject matter expert in your area, earning recognition and respect from your peers and community.
Fulfillment : Volunteering your time and expertise in a meaningful way can be incredibly rewarding, allowing you to make a positive impact while utilizing your talents and knowledge effectively.
Doing the Right Thing : Ultimately, promoting cybersecurity awareness is simply the right thing to do. By contributing to this cause, you’re helping to create a safer, more secure digital world for everyone.
At TreeTop Security, we believe that together, we can make a difference. Join us in our mission to empower individuals and communities through cybersecurity education and awareness. Together, we can create a safer, more resilient digital future for all.
Cybersecurity Awareness Training (CAT) Slide Deck & Worksheets v2024.03
This video is our team presenting version 2021.08 of the content via a webinar. The recording is ad-free and it will always be so it is safe to share. Even if the video is all you need right now, we still strongly encourage you to present the material in your own community in the future!
The presentation is roughly 45 mins. The timing depends on your presentation style so we encourage a few dry runs beforehand. We also suggest stories to make the presentation more relate-able. There are quite a few slides, however, there should be very little discussion on the transition slides. If you schedule an hour, that will give a little time for discussion during the presentation and/or for Q&A at the end.
What are you waiting for? You can make a difference! Don’t think about it. Just call your local library, co-working space, or other business event today and find someone to talk to about scheduling a date/time for the training. You won’t regret it!
You can download the slide deck as a Microsoft PowerPoint (pptx-ppt) file format. Alternatively, you can open the slide deck in Google Slides and make your own copy. Under no circumstances will we grant a request for edit access to the main slide deck, but there’s really no reason to have access… download/copy, edit, and make it your own! We do, however, love feedback so feel free to let us know of changes that you make and we might incorporate them into future versions!
Update/Clarification: Shortly after we released this slide deck, several folks reached out asking if they could “white label” it for their own purposes. Quite honestly, there isn’t a need to ask. The slide show is open-sourced under the “Creative Commons Attribution-NonCommercial” license. We selected this particular license because it means a) you can’t charge someone for the slides, b) you can make any modifications you deem necessary, and c) you must provide “appropriate” credit. For all practical purposes, text on the final slide works as credit if you want to avoid the murky legal interpretation of “appropriate.” So while we would love for you to leave the ‘Content By’ on the first slide, it is not necessary. Recognition for this work is far less important than getting it in the hands of those willing to share/present the content in their own communities and more importantly, who want to make a difference. The details of the CC license are also available on the SlideShare upload of these slides (link) for further reading as well as visibility.
Previous SlideDeck Versions
Version: 2022.08 – release date: august 31, 2022, version: 2021.08 – release date: august 19, 2021, version: 1.3 – release date: april 10, 2021, version: 1.2 – release date: september 30, 2019, version: 1.1 – release date: march 26, 2020, version: 1.0 – release date: september 12, 2019, previous worksheet versions, we'd love to hear from you.
Drop us a line or give us a call, and let's start securing your digital future together.
Main Headquarters
507 Main St, Suite A Hays, Kansas 67601
785-370-3444
Company Name
Services You're Interested In Services You're Interested In Peak - SMB Cybersecurity Platform Schedule an In-Person Training Schedule a Virtual Training Security Assessment Network Penetration Testing Social Engineering Assessment Virtual CISO (vCISO) Vulnerability Assessment Web Application Penetration Testing Other
How'd you hear about us? How'd you hear about us? Online Referral Word of Mouth Security Conference Friend or Colleague Search Engine Online Advertising

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
https://www.nist.gov/publications/slides-security-awareness-training-workforce-moving-beyond-check-box-compliance
Slides: Security Awareness Training for the Workforce: Moving Beyond "Check-the-box" Compliance
Download paper, additional citation formats.
- Google Scholar
If you have any questions about this publication or are having problems accessing it, please contact [email protected] .

- Conferences
- Last updated April 30, 2020
- In AI Origins & Evolution
10 Popular Cybersecurity Presentations On Slideshare You Should Refer To

- Published on August 12, 2019
- by Ambika Choudhury

Securing networks and protecting data from breaching has become one of the crucial motives in an organisation. Cybercrime has eventually risen with the widespread use of emerging technologies and we have been witnessing data breaches and other hacks for a few years now. In this article, we list down 10 popular presentations on cybersecurity one must read on Slideshare.
(The list is in alphabetical order)
1| Artificial Intelligence And Cybersecurity
This presentation was published in March 2019 by Olivier Busolini, a cybersecurity professional who also works with AI in cybersecurity. This presentation includes a basic introduction to AI, an overview of AI technologies, an overview of machine learning underlying technologies, basics of deep learning, introduction to red and blue AI, emerging usages of blue AI, difficulties faced during developing AI solutions and tips for cybersecurity strategy.
2| Cyber Crime And Security
This powerpoint presentation was published by Lipsita Behera, a software developer and it has gathered more than 350,000 views till now. In this PPT, you can understand the basics of cybersecurity such as how cybersecurity emerged, know about cyber threat evolution, types of cybercrime, how to take preventive measures in order to control the threats, learn various security reasons as well as methods.
3| Cybersecurity
This presentation has got more than one lakh viewers and more than 700 clipping. Here, the author introduces the basics of cybersecurity and what is the actual need of cybersecurity, what are the major security problems, different viruses and worms and its solutions, brief introduction of hackers and measures to prevent hacking, what are malware and steps to stop malware, what are trojan horses and safety measures to avoid trojans, password cracking and securing password, cybersecurity strategy in India and much more.
4| Combating cybersecurity Using Artificial Intelligence
Combating Cybersecurity using Artificial Intelligence was published in January this year by Inderjeet Singh, Director – Strategic Accounts. This presentation discusses the threats with AI and machine learning. Here, you can learn about the advanced behavioural attacks, applications of emerging technologies in cybersecurity, various malicious activities, including the future of AI and machine learning in cybersecurity.
5| Cyber Crime And Security
This powerpoint presentation was published by Aeman Khan, an automation test engineer and it has crossed over 410,000 views till now. Here, the writer discusses the basics of cybersecurity such as its introduction, history, the various categories of cybercrime, its types, how cybersecurity threatens national security, advantages of cybercrime and other safety tips to cybercrimes including cyber law in India.
6| Cybersecurity
This ppt is published by Bijay Bhandari, an engineer and project manager by profession. It has been viewed for over 210,000 times where the author discusses how to take action against cybercrime. You will know about the basics of cybersecurity and cybercrime, what constitutes cyber crimes, protection measures for cybercrime, advantages of cybersecurity and various safety measures.
7| Cyber Crime
This presentation has been viewed for over 294,000 times and it includes a basic introduction to cybercrime. You will get to know about the variants of cybercrime such as phishing, vishing, cyberstalking, cost of cybercrime in India, cyber laws, various ACTs including the preventive measures for such activities.
8| Overview Of Artificial Intelligence In cybersecurity
This presentation, an overview of artificial intelligence in cybersecurity was published in June 2019 by Olivier Busolini, a cybersecurity professional. Here, he talks about artificial imitation augmented intelligence, basic types of AI and machine learning, difficulties to develop AI solutions, challenges in machine learning, AI in cybersecurity, key flaws of cybersecurity, AI risk framework, basic introduction to defensive AI, adversarial AI as well as offensive AI and much more.
9| Security Automation And Machine Learning
The security automation and machine learning ppt is published by Siemplify, a security platform in January this year and has got more than 100 viewers. It includes a basic introduction to cybersecurity and machine learning, types of machine learning techniques, security analysis for machine learning, threats on machine learning, machine learning for prevention, detection, incident response and SOC management.
10| The Role Of Big Data, AI And ML In Cyber Intelligence
The role of big data, AI and ML in cyber intelligence ppt was published by Aladdin Dandis, an information security manager who gives a brief introduction to cyber intelligence, raw threat data and threat intelligence, understanding AI and machine learning drivers, various kinds of cybersecurity options such as phishing, anti-malware, fraud detection, cyber intelligence framework and its challenges.
Access all our open Survey & Awards Nomination forms in one place
Ambika Choudhury

Cisco Unveils AI-Native Cybersecurity Innovations

Commvault’s Arlie Spearheads AI Democratisation in Cyber Resiliency

How Securonix is Building Cybersecurity for LLMs

AI Will Open a Pandora’s Box of Escalating Privacy and Security Woes: Splunk Report

Nearly 83% of Indian Firms Were Hit by Cyber Breaches in 2022

After WormGPT, FraudGPT Makes it Easier for Cybercriminals

Meta Needs You in Its Generative AI Gambit

Digital India Act Expectations & Concerns

CORPORATE TRAINING PROGRAMS ON GENERATIVE AI
Generative ai skilling for enterprises, our customized corporate training program on generative ai provides a unique opportunity to empower, retain, and advance your talent., upcoming large format conference, data engineering summit 2024, may 30 and 31, 2024 | 📍 bangalore, india, download the easiest way to stay informed.

6 Techniques to Reduce Hallucinations in LLMs
Using techniques like better prompts, knowledge graphs, and advanced RAG can help prevent hallucinations and create more robust LLM systems.

Bad Times for Perplexity AI Begins

Top 9 Apple Vision Pro Use Cases in India
Top editorial picks, openai brings generative ai search experience to chatgpt, kunal shah says ‘gpt makes him 10x more efficient in sharing ideas with the team’, chatgpt brings data to life with interactive charts and tables directly from google drive and microsoft onedrive, after stack overflow, reddit succumbs to openai, subscribe to the belamy: our weekly newsletter, biggest ai stories, delivered to your inbox every week., also in news.

US Fears China’s Rise in AI Could Dominate Global Economy and Politics

We Live in an Era Where it’s Easy to Build but Difficult to Figure Out What to Build
Indian Companies are Good at Copying Ideas Generated Elsewhere

Why Ollama is Good for Running LLMs on Computer

10 Free Courses to Build AI Agents in 2024

VMware Makes Workstation Pro and Fusion Pro Free for Personal Use

L&T Technology Services Trains 3,000 Engineers in GenAI

Zoho Ventures into Chipmaking, Plans $700M Investment
AI Forum for India
Our discord community for ai ecosystem, in collaboration with nvidia. , "> "> flagship events, rising 2024 | de&i in tech summit, april 4 and 5, 2024 | 📍 hilton convention center, manyata tech park, bangalore, machinecon gcc summit 2024, june 28 2024 | 📍bangalore, india, machinecon usa 2024, 26 july 2024 | 583 park avenue, new york, cypher india 2024, september 25-27, 2024 | 📍bangalore, india, cypher usa 2024, nov 21-22 2024 | 📍santa clara convention center, california, usa, genai corner.

OpenAI Hires Google Veteran to Build ‘Google Search Alternative’

Meet the Child Prodigy from India Who Helped Build OpenAI’s GPT-4o

Transform Your Career with Praxis’s Top-Ranked PGP in Data Science with Generative AI and ML

Intel is Bullish on India with its Xeon Processors
Top Data Engineering Service Providers – PeMa Quadrant 2024

OpenAI Needs Apple, Badly!

Hitachi Vantara & Veeam Partner to Provide Data Protection for Hybrid Cloud Environments

92% of Indian Knowledge Workers Embrace AI at Work: Microsoft & LinkedIn Report
World's biggest media & analyst firm specializing in ai, advertise with us, aim publishes every day, and we believe in quality over quantity, honesty over spin. we offer a wide variety of branding and targeting options to make it easy for you to propagate your brand., branded content, aim brand solutions, a marketing division within aim, specializes in creating diverse content such as documentaries, public artworks, podcasts, videos, articles, and more to effectively tell compelling stories., corporate upskilling, adasci corporate training program on generative ai provides a unique opportunity to empower, retain and advance your talent, with machinehack you can not only find qualified developers with hiring challenges but can also engage the developer community and your internal workforce by hosting hackathons., talent assessment, conduct customized online assessments on our powerful cloud-based platform, secured with best-in-class proctoring, research & advisory, aim research produces a series of annual reports on ai & data science covering every aspect of the industry. request customised reports & aim surveys for a study on topics of your interest., conferences & events, immerse yourself in ai and business conferences tailored to your role, designed to elevate your performance and empower you to accomplish your organization’s vital objectives., aim launches the 3rd edition of data engineering summit. may 30-31, bengaluru.
Join the forefront of data innovation at the Data Engineering Summit 2024, where industry leaders redefine technology’s future.
© Analytics India Magazine Pvt Ltd & AIM Media House LLC 2024
- Terms of use
- Privacy Policy
Subscribe to our Youtube channel and see how AI ecosystem works.
There must be a reason why +150k people have chosen to follow us on linkedin. 😉, stay in the know with our linkedin page. follow us and never miss an update on ai.
- Back to main menu
- BROWSE BY TOPIC BROWSE BY TOPIC
- Global IT Asset Management
- IT Security
- Cloud & Container Security
- Web App Security
- Certificate Security & SSL Labs
- Developer API
- Cloud Platform
- Start a discussion
Qualys Is Proud to Sign CISA’s Secure by Design Pledge
Last updated on: May 8, 2024
Table of Contents
Why secure by design is important, the 7 secure by design pledge goals.
Cybersecurity leaders in the U.S. are very familiar with the Cybersecurity and Infrastructure Security Agency (CISA) and their important work to keep the internet, our country, and its citizens safe from cyber threats. As part of their efforts, CISA has identified secure by design software as a key element to ensuring the integrity and security of our critical infrastructure.
That’s why I am proud to announce that Qualys is signing CISA’s Secure by Design Pledge. Qualys was founded to help companies minimize cyber risk, and one of our fundamental tenets is making the digital world safer for everyone. As our President and CEO, Sumedh Thakar, says (and I’m paraphrasing here), “You can’t go through a day without working with a company that Qualys protects.” With that much responsibility, we take our commitment to security seriously—the security of our customers, our organization, and the broader digital universe. Keeping our customers safe by including security as a foundational element embedded in our product is a fundamental part of this commitment.
One of the best use cases for why this standard is important is what happened to Colonial Pipeline about two years ago. That breach occurred because of a default password. The pipeline that carries almost half of the East Coast’s fuel supplies shut down, and panicked customers sat in mammoth lines at the gas station—all because of a default password. These kinds of easily preventable incidents happen because, all too often, security in software products is seen as an afterthought. Products are released, vulnerabilities are exposed, and security is dealt with later.
At Qualys, we firmly agree with CISA that designing and maintaining a secure product is fundamental. As a cybersecurity company, our business runs on trust. Our customers trust that we have secure products that will keep their organizations and their most sensitive data safe. That’s why we have always believed that security is foundational and should be woven into a product’s lifecycle. And that’s why we’re committed to the secure by design principles.
The security by design principles seek to introduce security at the design stage of product development, massively reducing the number of risks in a product before it ever reaches the customer, and then follow along the lifecycle with things like simple and timely patches. The Secure by Design Pledge lists seven goals to help meet this philosophy. I firmly believe that all software manufacturers should institute these principles as part of their larger security program to keep their organization and customers safe, which is why Qualys meets and, in many cases, goes far beyond the security principles outlined in these goals. Those goals are:
- Reducing entire classes of vulnerability: Organizations will reduce the prevalence of one or more vulnerability classes, such as SQL injection or cross-site scripting, across all products.
- Security patches: This part of the pledge applies after the product has shipped and asks that an organization make it easier for customers to install patches.
- Vulnerability disclosure policy (VDP): In order to incentivize the white hat disclosure of vulnerabilities, this goal requires vendors to publish a vulnerability disclosure policy that gives researchers a safe way to report vulnerabilities to the vendor.
- CVEs: Here organizations agree to be accurate and timely in reporting the details for every Common Vulnerabilities and Exposures (CVE) record for their products.
- Evidence of intrusions: This goal is meant to enable customers to detect and understand security incidents by requiring organizations to provide customers with the logs that would assist them in gathering evidence of intrusions.
- Multi-factor authentication (MFA): Organizations agree to measurably increase the use of MFA across their products, with the goal to get more customers to use MFA.
- Default passwords: Within a year, organizations will reduce the amount of default passwords in their products, particularly internet-facing products.
At Qualys, we have already implemented stringent security policies to keep our customers and products safe. We will be pleased to report to CISA within the year how we have achieved, if not exceeded, all of these secure by design pledge goals.
Comments Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

COMMENTS
The material is in sections: Cybersecurity Basics; Cybersecurity Threats; Risk Management; Cybersecurity Framework; and Small Business Cybersecurity Resources. You and your team will become familiar with common threats like phishing and ransomware, understand steps you can take every day to prevent falling victim and steps to take to recover ...
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an outstanding presentation on the topic using this Cybersecurity Awareness Training Organization Cyber Security Dashboard Ppt Model Graphics.
Free Canva presentation template. Elevate your cybersecurity awareness with our dynamic Violet Illustrated Presentation Template, tailored specifically for business professionals. Perfect for workshops, seminars, and team meetings, this slideshow template is designed to make complex concepts accessible and engaging. Whether you're aiming to ...
SANS Leadership & Cloud Security - Crystal City 2024: Keynote - Security Culture: The What, Why and How. Lance Spitzner. read more. Cloud Security, Digital Forensics, Incident Response & Threat Hunting, Industrial Control Systems Security, Cybersecurity Leadership. Thursday, 23 May 2024 1:00PM EDT (23 May 2024 17:00 UTC)
This free cybersecurity awareness training slide deck is meant to be used by organizations and end users to help them better understand ways they can avoid scams, cyber attacks, and become more security aware. This slide deck is based on version 2021.08 of our wildly popular slide deck we originally released as open-source in September 2019.
Template 14 Cyber Security Training PPT Template Bundles . This PPT template is a great starting point for conveying your messages and building collaboration. The twelve slides added to this PowerPoint slideshow help you present a thorough explanation of the topic. You can use it to study and present information in the form of stats, figures ...
This free cybersecurity awareness training slide deck is meant to be used by organizations and end users to help them better understand ways they can avoid s...
Are you looking for an interactive presentation template for your cybersecurity seminar? Then try our 100% editable Cybersecurity Presentation Template. This cybersecurity PPT template is a slide deck prepared using customizable elements to discuss various aspects of the importance of cybersecurity. It starts with a title slide, showing imaginative lines to represent how the devices and online ...
Here are 6 reasons why security awareness training is crucial for businesses. 1. If you think your end users know better… they probably don't. Hackers use social engineering attacks to take advantage of end users' curiosity, trust, fear, negligence, and greed to drop malware on business networks. More importantly, 49% of employees admit ...
Stay abreast of the newest threats & connect with professionals in the cyber community at one of our biggest events of 2024. View Courses & Certifications. Las Vegas, NV or Live Online - PT September 4-9, 2024 45+ Courses Join SANS in early September for industry-leading insight from world-class instructors in the bright lights of Las Vegas ...
WEEK 4: Week of October 25 Cybersecurity First. 18. Please join us in promoting Cybersecurity Awareness Month this October as we encourage all users to own their role in protecti\൮g connected devices. "Do Your Part. #BeCyberSmart." \爀屲This year, October 1st falls on a Friday.
Cyber Security Awareness Seminar Presented By: Ryan Moore Ohio Cyber Range Institute, University of Cincinnati. Ohio Cyber Range Institute, University of Cincinnati About This Seminar • Designed for everyday cyber citizens • Online Webinar • 2 -hour Presentation • 10 Minute break • Questions? • Resource Guide • Follow-up survey ...
Such Cyber Security awareness training should focus on educating employees on potential risks they may face, allowing them to safeguard the firm and themselves from any cyber threat. ... Slide 5: The ROI of Security Awareness Training. Use this PPT Slide to show how a skilled, cyber-conscious workforce may help your organization manage those ...
Heavily discounted (use code HISPI-COVID-19) online, on-demand Cyber Security Management Course. Hopper's Roppers Security Training Community built around a series of free courses that provide training to beginners in the security field. IBM (hosted by Coursera) Free (7-day trial) suite of courses on IT Fundamentals for Cybersecurity ...
The 15-Minute, 7-Slide Security Presentation for Your Board of Directors. Help the board understand why cybersecurity is critical to the business. When the request comes in to give a cybersecurity presentation to the board, security leaders should jump at the chance to educate the executives. However, a lengthy, in- depth presentation is more ...
16 Updated seminar presentation topics on cybersecurity. Let's get to know the best seminar topics on cyber security, which will help you spread awareness about the topic. 1. The rise of ransomware: detection, prevention, and response strategies. Ransomware is one of the most dangerous malicious software mostly used by cybercriminals.
Version: 1.3 - Release Date: April 10, 2021. Download version 1.3. Drop us a line or give us a call, and let's start securing your digital future together. Access cybersecurity presenter slides from TreeTop Security. Equip yourself with expert resources to educate others on cyber threats and protection.
Abstract. This presentation focus on cybersecurity and mainly four parts 1) Introduction to cybersecurity tools and cyber attack 2) Cybersecurity roles, processes and operating system security 3 ...
An official website of the United States government. Here's how you know
7| Cyber Crime. This presentation has been viewed for over 294,000 times and it includes a basic introduction to cybercrime. You will get to know about the variants of cybercrime such as phishing, vishing, cyberstalking, cost of cybercrime in India, cyber laws, various ACTs including the preventive measures for such activities.
D. DebrajKarmakar. In this PowerPoint presentation, you can understand the basics of cybersecurity such as how cybersecurity emerged, know about cyber threat evolution, types of cybercrime, how to take preventive measures in order to control the threats, learn various security reasons as well as methods. Read more. Technology.
My role in cybersecurity! End-users are the last line of defense. As an end-user, you; Create and maintain password and passphrase. Manage your account and password. Secure your computer. Protect the data you are handling. Assess risky behavior online. Equip yourself with the knowledge of security guidelines, policies, and procedures.
Cyber security presentation. Oct 17, 2013 • Download as PPTX, PDF •. 469 likes • 622,671 views. Bijay Bhandari. All about Cyber security... Technology. 1 of 12. Download now. Cyber security presentation - Download as a PDF or view online for free.
Cybersecurity leaders in the U.S. are very familiar with the Cybersecurity and Infrastructure Security Agency (CISA) and their important work to keep the internet, our country, and its citizens safe from cyber threats. As part of their efforts, CISA has identified secure by design software as a key element to ensuring the integrity and security of our critical infrastructure.