Vulnerability Response assignment\n rules overview
Define the criteria by which vulnerable items (VIs) are automatically assigned to an\n assignment group for remediation.
Assignment type, whether Manual or Rule is\n available from the VI form and the list view. Any VI that was originally assigned by a rule\n but subsequently manually reassigned contains a reference to the original rule.
Use Assignment rule and Assignment type information to identify cases where the assignment\n rules did not find a correct match for the intended recipient. You can also use the\n information to identify which rules had the most reassignments.
Case sensitivity for the\n search text you enter in the condition builder is not supported on this record or\n form.

Assigning vulnerable items automatically
- User group: This option allows you to select any of the existing Now Platform® user groups.
- None: Indicates no default value for this mandatory field
- Configuration Item: Approval Group
- Configuration Item: Assignment Group
- Configuration Item: Support Group
- Script: This option allows you to define the conditions using a script. This option\n requires coding or advanced ServiceNow expertise.
Run high priority rules (items that need special handling, where risk is critical, or a VI\n should be handled by regulatory compliance) first. Next, run your general rules, where no\n special handling is required, and you know who should be responsible for them. Finally,\n create a default rule to assign VIs to the group that will figure out what assignment group\n it should belong to. This group could add another rule to cover their decisions. This\n default rule would run last.
Assignment rule evaluation process
Assignment rules are used to evaluate and assign a VI when a new VI is opened, that is,\n imported, created manually, or reopened. Unless you manually reapply assignment rules after\n the VI or its state changes, a VI is evaluated once.
- For each vulnerability assignment rule, the VI is compared to the assignment filter,\n lowest order rule first.
- Where the condition matches, the VI is assigned an assignment group. The lookup\n stops.
- Where the conditions do not find a match among all the other rules, the VI is assigned\n to the default assignment group, if a default rule exists. Once the vulnerable item\n has been assigned, the appropriate remediation task rule uses assignment as one of its\n criteria for placing the vulnerable items into a remediation task. See Vulnerability Response remediation tasks and task rules overview and Filtering within Vulnerability Response for more\n information. Note: The default rule is the rule with the highest execution order\n value. A final rule to use that is a good catch-all is\n active=true . If there is no default rule, the VI\n remains unassigned when the remediation task rule makes the\n assignment. \n \n
Reapplying assignment rules
If the Reapply all vulnerability assignment rules scheduled job has not run before the first time you use Apply Changes , then it runs all the assignment rules on all Open VIs except\n those VIs that were manually assigned. After that, all subsequent uses of Apply Changes rerun only the changed rules and any dependent rules. Changes to one rule may result in a VI matching a different\n unmodified rule. Reapplying assignment rules does not regroup the vulnerable items.
The scheduled job [ Reapply all vulnerability assignment rules ] is inactive by default. When activated, it applies all the rules to all open VIs except those manually assigned. It\n can run Daily , Weekly , Monthly , Periodically , Once , or On Demand . Depending on how many\n active VIs you have in your environment, remember to set the Run field appropriately following the initial run to prevent performance impacts.
Upgrade customers should refer to the VR Release Notes for information regarding the impact of this feature on existing VIs.
When an assignment group on an assignment rule changes, the vulnerable items can be automatically reevaluated and regrouped by enabling the system property sn_vul.rerun_task_rules and business rule Link to\n Remediation Tasks.
- Navigate to All > System Properties > All Properties .
- Open sn_vul.rerun_task_rules system property.
- In the Value field, set the value to true.
To automate the regrouping of vulnerable items, you must active the business rule Link Remediation Tasks.
- Navigate to All > System Definition > Business Rules .
- Open Link to Remediation Tasks business rule.
- Select the Active check box to activate the business rule.
- The vulnerable items are removed from the groups without deleting the groups.
- Only those items are removed which are created using remediation task rules or remediation effort.
- Regrouping is done automatically only when the assignment group changes as part of an assignment rule and not when it is manually changed.

Find and prioritize application vulnerabilities with ServiceNow and Checkmarx

- September 14, 2023
A brand-new integration for enterprise-scale AppSec is ready for Checkmarx and ServiceNow customers to download in the ServiceNow plugin store. The ServiceNow Vulnerability Dashboard now enables organizations to easily integrate Checkmarx SAST and SCA.
We’re so excited to launch support for ServiceNow customers, given the growing need for streamlined, end-to-end vulnerability management.
Let's dive a bit deeper into what Checkmarx and ServiceNow customers can expect from the integration.
Prioritize and remediate with a centralized dashboard
ServiceNow is a leading cloud-based platform that offers comprehensive solutions for IT service management, human resources, customer service, security operations, and more. It enables organizations to automate workflows, optimize processes, and provide seamless digital experiences to users across multiple departments.
The ServiceNow® Vulnerability Response application is an important tool within the ServiceNow ecosystem that AppSec managers can leverage to drive efficiencies within application security.
This application imports and automatically groups vulnerable items according to group rules, which allows teams to remediate vulnerabilities quickly. Data is pulled from both internal and external sources, such as the National Vulnerability Database (NVD) and third-party integrations, like the new Checkmarx plugins.
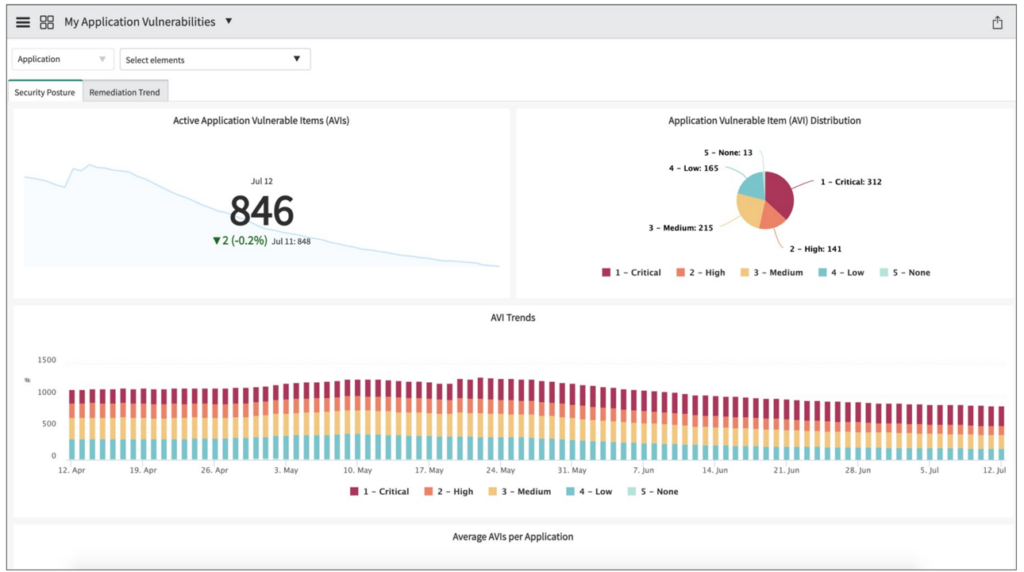
The ServiceNow Application Vulnerability Response dashboard displays trends and summaries of vulnerabilities from leading scan vendors like Checkmarx.
The Checkmarx ServiceNow Vulnerability Integration is now available for Checkmarx SAST and Checkmarx SCA. The integration for Checkmarx SAST is available for both Checkmarx One and on-premise deployments, while SCA is available for Checkmarx One.
The plugins enable enterprises to run the integrations required to import projects, scan summaries, and scan results within the ServiceNow platform, giving your application security managers a clear view and top-tier prioritization and triage powers. The latest vulnerabilities found for each scan are then inserted on the ServiceNow as Application Vulnerability Items (AVIs).
The plugins do not scan code; instead, they pull data from Checkmarx and map the results into the ServiceNow tables.
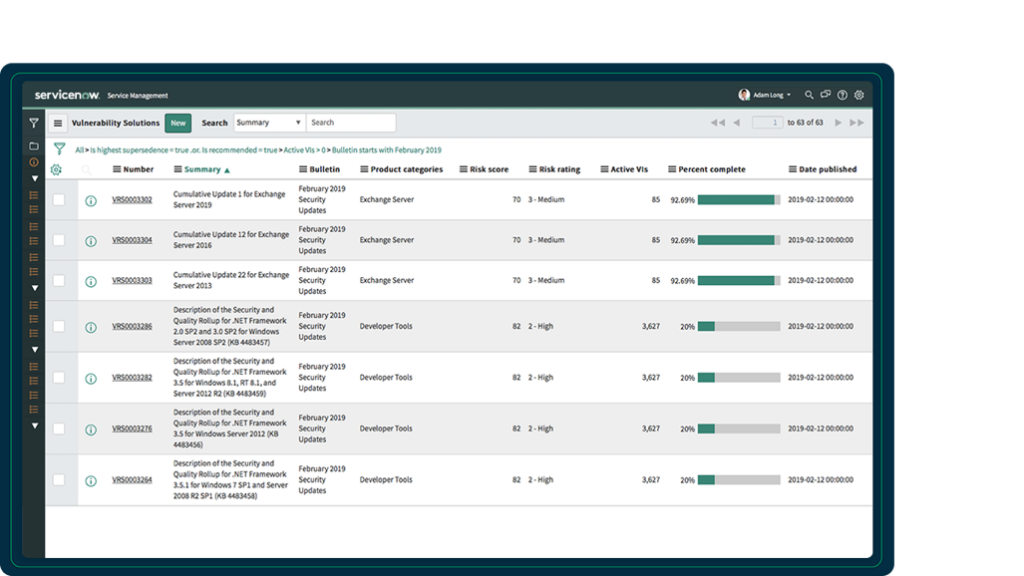
ServiceNow Vulnerability Solutions Management: View your organization’s most impactful remediation activities and monitor their completion.
Every time Checkmarx provides updated scan results, the ServiceNow Vulnerability Response Application can automatically assign the found vulnerabilities to a specific person, or team, by building custom workflows and automation triggers. This process accelerates the security workflow, ensuring an efficient vulnerability management process.
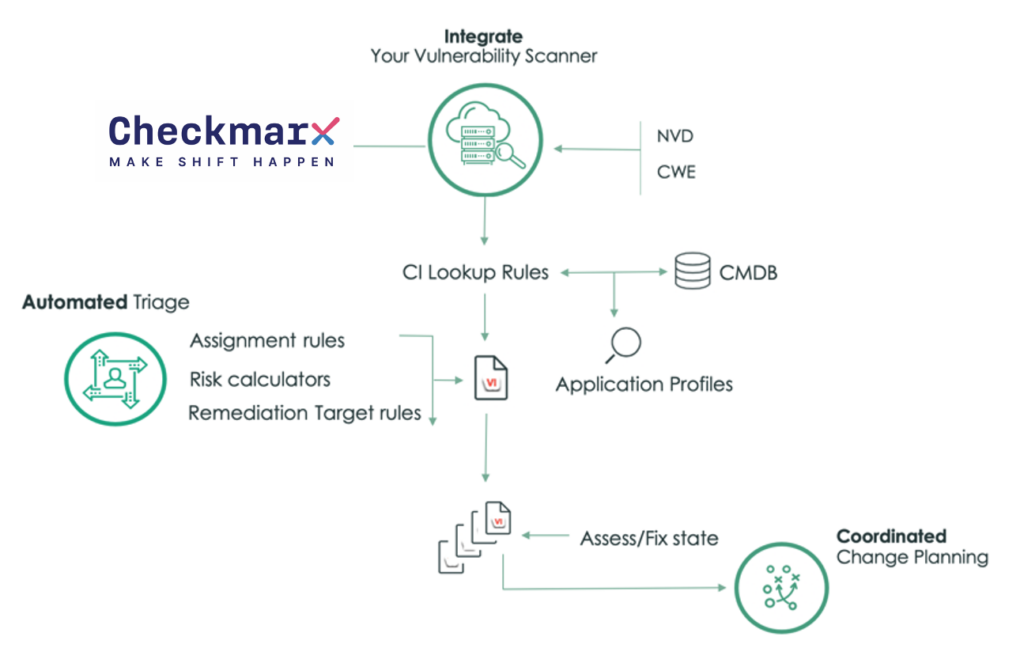
Use Application Vulnerability Response to follow the flow of information, from integration through investigation, and then on to resolution.
After vulnerability data is imported, users can compare the data to applications identified in Application Vulnerability Response, relate a single third-party vulnerability to multiple CWE entries, and find the primary CWE for the vulnerability in determining risk. And, users can easily prioritize vulnerabilities by create assignment rules or using calculators to determine business impact.
Getting started
With the addition of ServiceNow to the growing list of Checkmarx integrations, we’re making our products as compatible as possible with business-critical applications, so organizations can optimize workflows and keep their own applications secure.
For customers already using both ServiceNow + Checkmarx One or Checkmarx SAST, head over to the ServiceNow Store to download the app.
Checkmarx One Vulnerability Integration with ServiceNow (Checkmarx SAST and Checkmarx SCA)
Download the app
View the documentation
Checkmarx SAST On-Prem Vulnerability Integration with ServiceNow
For existing ServiceNow customers that would like to learn more about the accuracy and power of Checkmarx One, especially how to easily view and triage scan results within ServiceNow, contact us today.
Wrap up
Vulnerability risk management is crucial for organizations to protect their IT infrastructure from cyber threats and to comply with regulatory requirements.
By integrating Checkmarx scan results into the ServiceNow Vulnerability Response Application, users can better manage vulnerabilities and ensure seamless communication with incident response tasks, change requests, and problem management.
We’re so excited to announce this integration and can’t wait to hear from more customers about the day-to-day impact it makes on building smart and efficient workflows and the ability to better track, prioritize, and remediate the vulnerabilities in one centralized dashboard.
About the Author

Kaitlyn Huff
Never miss an update. subscribe today, more resources to consider.

Solutions For
Terms of Use | Checkmarx Privacy Policy | Checkmarx.com Cookie Policy
©2024 Checkmarx Ltd. All Rights Reserved. iISO/IEC 27001:2013 Certified
Privacy Overview
Exciting news! Thirdera has been acquired by Cognizant.

Thirdera generates transformation, digitization, and automation for our customers at the speed of NOW.

Assessment & Roadmap
Develop a long-term, transformational strategy for growing your business around ServiceNow alongside the most experienced leaders in the ecosystem.

Design Services
Adopt tailored experiences that harness organizational capabilities.

Organizational Change Management
Achieve improved team buy-in and ServiceNow ROI with our experts in executing a proactive organizational change management strategy.

Work with industry-leading certified ServiceNow trainers to build effective practices and increase user confidence within your organization.

Improve IT service KPIs across your organization through automated processes that align with your overall business objectives.

Employee Experience
Engage your employees, promote self-service, and free your HR team from manual and repetitive tasks with ServiceNow and the HR experts at Thirdera.

Find threats and take action with more speed, intelligence, and consistency.

Risk & Continuity
Confront risks with confidence and resilience.

Customer Service Management
Create a modern and intelligent customer experience.

Experience Management
Explore tailored experiences that harness organizational capabilities.
ServiceNow Store
Explore Thirdera’s applications in the ServiceNow Store.

- DevOps Connect
Managed Services
Get the right people in to support and enhance your ServiceNow platform, and realize digital transformation.


Experience-led Design
Custom apps.
Build custom applications in ServiceNow that are durable, intuitive, and designed to solve your business needs at scale.

- Audit Management
- Business Continuity Management
- Certificate Management
- Configuration Compliance
- Cybersecurity Hardening
- Employee Center Migration
- HR Service Delivery
- IRM Foundation
- Policy & Compliance
- Privacy Management
- Risk Management
- Security Incident Response
- Third-Party Risk Management
- Vulnerability Response
AI and Future of Work
C apture the strategic advantage of AI to maximize platform value.

We help organizations adopt better patterns of work and get more from ServiceNow. Our team unlocks enterprise potential to elevate experiences across the world of work.

- Leadership Team
- Partner Network
- Thirdera Digital
- Thirdera Store
- Thirdera University
- 3VP Rewards
.png?width=500&height=276&name=MicrosoftTeams-image%20(396).png)
Thirdera recognized as the 2023 ServiceNow Americas IT Workflow Partner of the Year
Find the right level of expertise to meet your specific ServiceNow needs.

Financial Services
Create seamless experiences for customers and agents with compliance.

Eclipx modernizes Accident Management with ServiceNow CSM
Telecom, Media & Tech
Scale and support operations with end-to-end digital workflows.

ngena Achieves Telecom operational Excellence with Thirdera and ServiceNow
Health Care & Life Science
Deliver better outcomes now and into the future with health IT.

Improve customer service metrics from weeks to days.
Manufacturing
Set a new standard for manufacturing with truly connected operations.

Transforming employee experience at a global level
Enable better decision-making to deliver optimized government services.

Data-Driven Innovation with ServiceNow Performance Analytics
Modernize learning to create amazing experiences for all.

Simplifying Higher Education Credit Management with ServiceNow CSM
Energy & Utilities
Automate critical operations to provide highly available, reliable services.

Saving time and energy by automating risk and compliance.
Retail & Hospitality
Digitize and automate workflows to enhance the customer experience, online and in-store.

Modernizing global HR Service Delivery.
Transportation & Logistics
Streamline complex operations for lower costs and improved customer experiences.

Value-driven project management
Business & Consumer Services
Develop innovative solutions with a modern service provider platform.

Creating new levels of efficiency in Order Management.
Stay up to date with the insights from ServiceNow experts and explore our blogs, news, case studies culture posts, partner updates and more.

- Case Studies

Thirdera is being acquired by Cognizant.

- Deutsch – Deutschland
- English - Australia
- English - United Kingdom
- Español - España
- Español - Estados Unidos
- Français - France
- English - North America
- Español - LATAM
ServiceNow Demo: Vulnerability Response Remediation Targets

In this video, we demo new functionality added to Vulnerability Response remediation target rules in the November 2022 release of Vulnerability Response. This is a big change that makes remediation targets much more flexible and powerful by allowing the selection of the remediation target start date.
Watch the demo
Video Snapshots
1:18 - How to create remediation target rules
2:24 - Use case examples
Talk to the Security Experts
Connect with Thirdera's Security specialists to learn how to leverage the ServiceNow platform to synchronize existing Security Operations data into one solution. Click below to take the next steps in bolstering your security posture with a faster, smarter, and more consistent way of identifying and remediating risks.

Tommy LaMonte
Related posts, servicenow demo: prioritizing vulnerable items.
Prioritizing and addressing crucial vulnerabilities stands as a cornerstone for an effective vulnerability response process. ServiceNow efficiently triages key attributes,...
ServiceNow Demo: Vulnerability Exception...
Effective exception management is crucial for organizations to maintain a strong security posture and mitigate vulnerabilities promptly. ServiceNow's Vulnerability Response...
ServiceNow Demo: Performance Analytics for...
Performance Analytics (PA) for Vulnerability Response in ServiceNow offers organizations a powerful tool for maximizing their security posture and mitigating cyber risks. In this...
Prioritizing Vulnerable Items for Improved...
In an era where data breaches are not a matter of "if" but "when," organizations face a pressing need to fortify their security postures. Recent statistics from the Ponemon...

IMAGES
VIDEO
COMMENTS
Define the criteria by which vulnerable items (VIs) are automatically assigned to an assignment group for remediation. Starting with v15.0 of Vulnerability Response, the table labels for vulnerability.
Vulnerability Response assignment rules overview - Product Documentation: Utah - Now Support Portal.
vulnerability is fixed, the record will be closed. Business risks due to critical vulnerabilities or overdue remediation can also be tracked as part of your enterprise risk management program. This helps ensure good security hygiene with a holistic approach. ServiceNow Security Operations Application Vulnerability Response is part of ServiceNow
Tips and trick for Vulnerability Assignment Rules
Grow your skills and RiseUp with ServiceNow. Rise up and join the digital revolution. Help fill the need for people with ServiceNow expertise. Mitigate application security risks with ServiceNow Application Vulnerability Response. Centralize vulnerability management and coordinate fixes with ease.
In conclusion, ServiceNow Vulnerability Response is a powerful module within the ServiceNow platform that enables organizations to streamline their vulnerability management processes. By utilizing automated scanning, risk assessment, and remediation task management, ServiceNow VR helps organizations identify and address vulnerabilities ...
The ServiceNow solution. ServiceNow® Security Operations is a security orchestration, automation, and response (SOAR) engine built on the Now Platform. Designed to help security and IT teams respond faster and more efficiently to incidents and vulnerabilities, Security Operations uses intelligent workflows, automation, and a deep connection ...
Vulnerability Response Download ServiceNow Vulnerability Response Harden the attack surface exploding across cloud, infrastructure, and applications According to the Enterprise Strategy Group (ESG) Security Hygiene and Posture Management report, nearly 7 out of 10 respondents admitted to a cyber breach resulting from exploitation of unknown ...
ServiceNow Learn about features, functionality, configurations, and integrations in ServiceNow Vulnerability Response (VR). - Now Learning
To showcase how Dengene introduced an Intelligent and efficient Vulnerability Assignment and Grouping for ServiceNow Vulnerability Response application.
The ServiceNow® Vulnerability Response application is an important tool within the ServiceNow ecosystem that AppSec managers can leverage to drive efficiencies within application security. This application imports and automatically groups vulnerable items according to group rules, which allows teams to remediate vulnerabilities quickly.
ServiceNow's Vulnerability Response solution, paired with Snyk Code insights, enables teams to centrally manage and respond to first-party code vulnerabilities in their applications. ... ServiceNow automates and expedites assignments using the Snyk app so your developers can focus on what's most important — improving productivity and ...
ServiceNow Vulnerability Response application. Select this check-box to map the vulnerability (detection) state in the Vulnerable Items table, that is, AVIT table (sn_vul_app_vulnerable_item) as per the Triage map maintained ... to let the customer add remediation rules, assignment rules etc for AVR. Customers can enable the inactive ...
Tommy LaMonte January 10, 2023. In this video, we demo new functionality added to Vulnerability Response remediation target rules in the November 2022 release of Vulnerability Response. This is a big change that makes remediation targets much more flexible and powerful by allowing the selection of the remediation target start date.
Note: As recommended by ServiceNow only 'Qualys Web Application List Integration' is kept active and other integrations are inactive, to let the customer add remediation rules, assignment rules etc for AVR. Customers can enable the inactive integrations once they have added desired rules.