Set and Check User Rights Assignment via Powershell
You can add, remove, and check user rights assignment (remotely / locally) with the following powershell scripts..
Posted by : blakedrumm on Jan 5, 2022
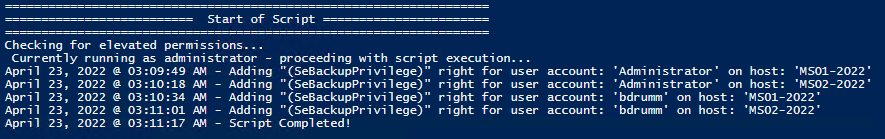

Local Computer
Remote computer, output types.
This post was last updated on August 29th, 2022
I stumbled across this gem ( weloytty/Grant-LogonAsService.ps1 ) that allows you to grant Logon as a Service Right for a User. I modified the script you can now run the Powershell script against multiple machines, users, and user rights.
Set User Rights
How to get it.
All of the User Rights that can be set:
Note You may edit line 437 in the script to change what happens when the script is run without any arguments or parameters, this also allows you to change what happens when the script is run from the Powershell ISE.
Here are a few examples:
Add Users Single Users Example 1 Add User Right “Allow log on locally” for current user: . \Set-UserRights.ps1 -AddRight -UserRight SeInteractiveLogonRight Example 2 Add User Right “Log on as a service” for CONTOSO\User: . \Set-UserRights.ps1 -AddRight -Username CONTOSO\User -UserRight SeServiceLogonRight Example 3 Add User Right “Log on as a batch job” for CONTOSO\User: . \Set-UserRights.ps1 -AddRight -Username CONTOSO\User -UserRight SeBatchLogonRight Example 4 Add User Right “Log on as a batch job” for user SID S-1-5-11: . \Set-UserRights.ps1 -AddRight -Username S-1-5-11 -UserRight SeBatchLogonRight Add Multiple Users / Rights / Computers Example 5 Add User Right “Log on as a service” and “Log on as a batch job” for CONTOSO\User1 and CONTOSO\User2 and run on, local machine and SQL.contoso.com: . \Set-UserRights.ps1 -AddRight -UserRight SeServiceLogonRight , SeBatchLogonRight -ComputerName $ env : COMPUTERNAME , SQL.contoso.com -UserName CONTOSO\User1 , CONTOSO\User2
Remove Users Single Users Example 1 Remove User Right “Allow log on locally” for current user: . \Set-UserRights.ps1 -RemoveRight -UserRight SeInteractiveLogonRight Example 2 Remove User Right “Log on as a service” for CONTOSO\User: . \Set-UserRights.ps1 -RemoveRight -Username CONTOSO\User -UserRight SeServiceLogonRight Example 3 Remove User Right “Log on as a batch job” for CONTOSO\User: . \Set-UserRights.ps1 -RemoveRight -Username CONTOSO\User -UserRight SeBatchLogonRight Example 4 Remove User Right “Log on as a batch job” for user SID S-1-5-11: . \Set-UserRights.ps1 -RemoveRight -Username S-1-5-11 -UserRight SeBatchLogonRight Remove Multiple Users / Rights / Computers Example 5 Remove User Right “Log on as a service” and “Log on as a batch job” for CONTOSO\User1 and CONTOSO\User2 and run on, local machine and SQL.contoso.com: . \Set-UserRights.ps1 -RemoveRight -UserRight SeServiceLogonRight , SeBatchLogonRight -ComputerName $ env : COMPUTERNAME , SQL.contoso.com -UserName CONTOSO\User1 , CONTOSO\User2
Check User Rights
In order to check the Local User Rights, you will need to run the above (Get-UserRights), you may copy and paste the above script in your Powershell ISE and press play.
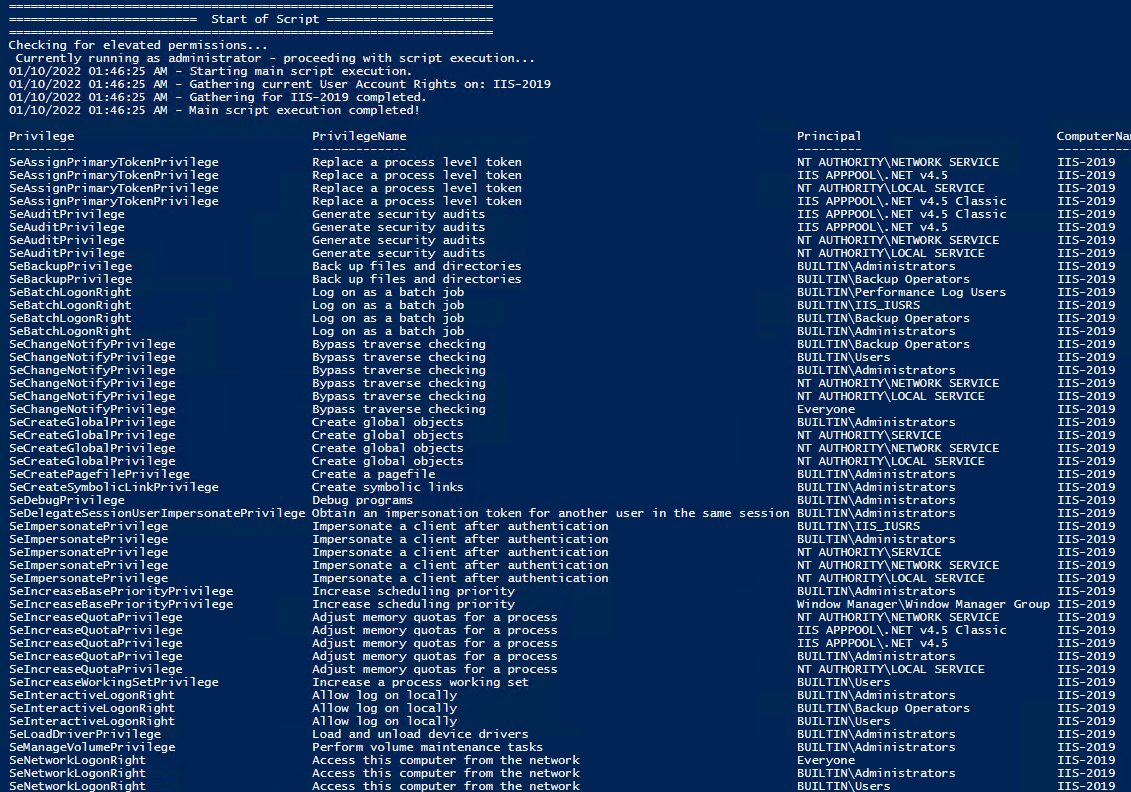
Note You may edit line 467 in the script to change what happens when the script is run without any arguments or parameters, this also allows you to change what happens when the script is run from the Powershell ISE.
Get Local User Account Rights and output to text in console:
Get Remote SQL Server User Account Rights:
Get Local Machine and SQL Server User Account Rights:
Output Local User Rights on Local Machine as CSV in ‘C:\Temp’:
Output to Text in ‘C:\Temp’:
PassThru object to allow manipulation / filtering:
I like to collaborate and work on projects. My skills with Powershell allow me to quickly develop automated solutions to suit my customers, and my own needs.
Email : [email protected]
Website : https://blakedrumm.com
My name is Blake Drumm, I am working on the Azure Monitoring Enterprise Team with Microsoft. Currently working to update public documentation for System Center products and write troubleshooting guides to assist with fixing issues that may arise while using the products. I like to blog on Operations Manager and Azure Automation products, keep checking back for new posts. My goal is to post atleast once a month if possible.
- operationsManager
- troubleshooting
- certificates

- PowerShell Forum Directory
- Publications
Managing Privileges using PoshPrivilege
A recent project of mine has been to write a module to manage privileges on a local system. What I came up is a module called PoshPrivilege that allows you to not only look at what user rights are available on a local or remote system, but also provide the ability to Add, Remove, Enable and Disable the privileges as well.
If you are running PowerShell V5, you can download this module from the PowerShell Gallery:
Otherwise, check out my GitHub page where I am maintaining this project:
https://github.com/proxb/PoshPrivilege
I won’t spend time talking about how I wrote this module and my reasons behind it. What I will say is that instead of writing out C# code and then using Add-Type to compile it, I went with the Reflection approach of building out everything from the pinvoke signatures for methods to the Structs and even the Enums.
Let’s get started by looking at what is available in this module. The first function that is available is Get-Privilege and it comes with a few parameters. This function’s purpose is to let you view what privileges are currently available on the system (local or remote) as well as what is currently applied to your current process token.

A quick run through of using this function with various parameters:

If this one looks familiar, then it is probably likely that you have used the following command:

I opted for boolean values instead to determine the state for easier filtering if needed.
Up next are the Enable/Disable-Privilege functions. These work to Enable or Disable the privileges that are currently available on your local system to your process token. This means that if something like SeDebugPrivilege isn’t available on your system (such as being removed via Group Policy), then you cannot use Enable-Privilege to add your process token to this privilege. As in the previous image where we can see what is enabled and disabled, these are the only privileges that are available for me to work with.
To show this point, I am going to enable both SeSecurityPrivilege and SeDebugPrivilege so you can see that while the first privilege will show as Enabled, the other will not appear as it has not been made available.

As you can see from the picture, SeSecurityPrivilege has been enabled as expected, but SeDebugPrivilege is nowhere to be found. If we want SeDebugPrivilege, we will need to go about this another way which will be shown shortly.
Disabling a privilege can be done using Disable-Privilege as shown in the example below.

Now that I have covered Enabling and Disabling of the privileges and their limitations, I will move onto the Add/Remove-Privilege functions which allow you to add a privilege for a user or group or remove them on a local system. Note that this only works up until it gets reverted if set by group policy. This will also note show up if you look at the privileges available on your current process token (you will log off and log back in to see it).
Remember that I do not have SeDebugPrivilege available to use? Well, now we can add it to my own account using Add-Privilege.

We can see it is now available, but as I mentioned before, it doesn’t show up in my current process. A logoff and login now shows that it is not only available, but already enabled.

With this now enabled, we could disable it as well if needed using Disable-Privilege. I added my account for show, but we can also add groups this was as well.
As with Adding a privilege, we can remove privileges as well using Remove-Privilege.

As with Add-Privilege, you will need to log off and log back in to see the change take effect on your account.
Again, you can install this module using Install-Module if running PowerShell V5 and this project is out on GitHub to download (and contribute to as well). Enjoy!
Share this:
4 responses to managing privileges using poshprivilege.
I downloaded the scripts from Github, but getting compile errors.
Specifically the errors are around the WInOS Structures listed below:
Unable to find type [LUID]: make sure that the assembly containing this type is loaded. Unable to find type [LSA_UNICODE_STRING]: make sure that the assembly containing this type is loaded. Unable to find type [LARGE_INTEGER]: make sure that the assembly containing this type is loaded. Unable to find type [LUID_AND_ATTRIBUTES]: make sure that the assembly containing this type is loaded. Unable to find type [TokPriv1Luid]: make sure that the assembly containing this type is loaded.
Unable to find type [TOKEN_INFORMATION_CLASS]: make sure that the assembly containing this type is loaded.
Unable to find type [ProcessAccessFlags]: make sure that the assembly containing this type is loaded.
BTW, I have posted the full error log @ https://docs.google.com/document/d/18boeWSbvlLwpoIAMTJAp0ooNaLxe6kniYrJr_q3ZNMQ/edit?usp=sharing
Just a question, how can I grant the SESecurityPrivilege to the Set-Acl process ? If I do a whoami /priv I can see my useraccount (PS –> run as administrator) I can see the privilege is enabled, but when I try to run the script I have I get the following error :
Set-Acl : The process does not possess the ‘SeSecurityPrivilege’ privilege which is required for this operation. At C:\Scripts\SESOG\ImportACLSEv2.ps1:16 char:16 + $acl | Set-Acl $path + ~~~~~~~~~~~~~ + CategoryInfo : PermissionDenied: (P:\Common:String) [Set-Acl], PrivilegeNotHeldException + FullyQualifiedErrorId : System.Security.AccessControl.PrivilegeNotHeldException,Microsoft.PowerShell.Commands.SetAclCommand
The script looks like this : $par = Import-Csv -Path “c:\scripts\sesog\ImportMainCC.csv” -Delimiter “;”
foreach ( $i in $par ) { $path= $i.Path $IdentityReference= $i.IdentityReference $AccessControlType=$i.AccessControlType $InheritanceFlags= $i.InheritanceFlags $PropagationFlags=$i.PropagationFlags $FileSystemRights=$i.FileSystemRights echo $path $IdentityReference $acl = Get-Acl $path $permission = $IdentityReference, $FileSystemRights, $InheritanceFlags, $PropagationFlags, $AccessControlType $accessRule = new-object System.Security.AccessControl.FileSystemAccessRule $permission $acl.SetAccessRule($accessRule) $acl | Set-Acl $path }
In the import csv a path is set and exported export rights from the original location (I am doing a fileserver migration) but on each of the folders mentioned the inherentance flag has been removed.
Pingback: PowerShell Magazine » The case of potentially broken PackageManagement for Windows 10 Insiders
You are a lifesaver! I have been fretting over how to manage service account rights on remote servers – each OU has a corresponding AD security group and GPO, and doing this manually is both time-consuming and fraught with error. I can’t wait to try this out. First PoshWSUS, then this …you rock.
Leave a comment Cancel reply
Translate this blog.
- Search for:
Recent Posts
- Dealing with Runspacepool Variable Scope Creep in PowerShell
- 2018 PowerShell Resolutions
- Quick Hits: Getting the Local Computer Name
- Recent Articles on MCPMag
- Quick Hits: Finding all Hyperlinks in an Excel Workbook
- Querying UDP Ports with PowerShell
- Changing Ownership of File or Folder Using PowerShell
- PowerShell and Excel: Adding Some Formatting To Your Report
- Quick Hits: List All Available WMI Namespaces Using PowerShell
- Avoiding System.Object[] (or Similar Output) when using Export-Csv
- Starting,Stopping and Restarting Remote Services with PowerShell
- Quick Hits: Finding Exception Types with PowerShell
- Using PowerShell Parameter Validation to Make Your Day Easier
- Quick Hits: Ping Sweep One Liner
- Locating Mount Points Using PowerShell
- background jobs
- Internet Explorer
- performance
- powerscripting
- Regular Expressions
- scripting games 2012
- scripting games 2013
- scripting guy
- winter scriting games 2014
Email Subscription
Enter your email address to subscribe to this blog and receive notifications of new posts by email.
Email Address:
Sign me up!
- 5,525,469 Visitors Since August 5, 2010
- Entries feed
- Comments feed
- WordPress.com

- Already have a WordPress.com account? Log in now.
- Subscribe Subscribed
- Copy shortlink
- Report this content
- View post in Reader
- Manage subscriptions
- Collapse this bar

Managing User Rights in Powershell
Managing User Rights Assignments in Powershell
Windows User Rights, also known as Windows Privileges, are traditionally managed via GPO or in the simplest of cases via the server’s Local Security Policy. These assignments control special permissions that are often needed by IIS applications or other application hosting on Windows Servers.
So how can we manage these assignments in Powershell? There’s no obvious solution provided in Powershell, but there are several options are available. None of which are a pure Powershell solution, but some are close.
- Wrap the ntrights.exe process in Powershell. This is relatively simple, but the downside is having an external dependency on the ntrights.exe file.
- Embed a wrapper class to the LSA API in your script. This is a pretty good solution but certainly bloats your script.
- Load and Reference the Carbon DLL (If you haven’t already checked out this Powershell library, you should it is very powerful and regularly updated. I choose this approach because it keeps the script clean and compact, it returns an array of strings for easy interrogation. It does require a dependency on carbon.dll, but this library provides a ton of functionality beyond just this.
I like the 3rd option, its very clean, and I like working with the Carbon library.
Now lets take this script to the next level and wrap it into a DSC Script implementation. We can use this same logic in a DSC configuration to make sure our desired User Rights Assignments are kept in place.
What else can we do? We could also create a Custom DSC Resource to have a cleaner DSC Configuration.
Related Posts

Local Administrator Audit Script

Powershell Log Archival Script
My new stories.

List all user rights assignment permissions in domain for specific account
Hi, this might be an overwhelming task but it is good to know whether this is possible. I want to list all permissions which are given to specific account via GPOs (default domain policy and default domain controller policy). It is account used by backup software and in order to work properly this account had to be given bunch of permissions to (Create a token object, Log on as a batch job, etc.). Of course given permissions can be seen in Group Policy MMC but I am interested only in getting permissions given to that account and exporting these permissions to some file for the purpose of documenting them.
Thanks in advance.
You are talking about UserRights Assignments, not permissions. With that said, here is a nice looking module someone wrote that can do what you are asking. I have not tested it, but looks very promising. Of course you should evaluate their code and confirm it will pose not threat to your environment before using anything taken from the internet.
https://userrights.codeplex.com/
Maybe I am wrong but it seems this module does the job only for local user rights assignment on given computer (local security policy). I need PowerShell code to retrieve user rights assignments given to specific account via GPOs (rights assigned to account in both Default Domain Policy and Default Domain Controller Policy).
Well, the rights on the local computer will be the culmination of the applied GPO’s, so it would be the effective rights after the GPOs have applied. If you are wanting to specifically look at the GPOs themselves, you can use the GPO cmdlets. Specifically, if you are good at XML, you can use the Get-GPOReport cmdlet.
[xml]$report = Get-GPOReport -Name “Default Domain Policy” -ReportType XML
I know that Curtis :-), rights on local computer will be result of applied GPOs on that computer. If used, this module has to be copied to one domain member machine and one domain controller and tested on both of them. Since you can do virtually anything with PowerShell nowadays I assume there is some way to pull out user rights assignments from GPO and filter them based on specific account.
The only way I can think to get the gpo settings was in the second part of my previous statement. …
If you are wanting to specifically look at the GPOs themselves, you can use the GPO cmdlets. Specifically, if you are good at XML, you can use the Get-GPOReport cmdlet.
Related Topics
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
How to Set Logon User Rights with the Ntrights.exe in windows 10(64 bit) [duplicate]
I need to know whether ntrights.exe 64 bit version exists?
If not, which is the 64 bit equivalent of ntrights.exe?
Thanks in advance.
- command-line
What is an equivalent for ntrights.exe on Windows 10?
Set and Check User Rights Assignment via Powershell You can add, remove, and check User Rights Assignment (remotely / locally) with the following Powershell scripts.
Read the blakedrumm page for detailed instructions, and download the script .
I just tested it successfully on Windows 2022 Standard.
- 1 This look really useful but all of the links are broken. – user2871239 Jan 26, 2023 at 13:35
Not the answer you're looking for? Browse other questions tagged windows-10 command-line 64-bit .
- The Overflow Blog
- Net neutrality is in; TikTok and noncompetes are out
- Upcoming research at Stack Overflow
- Featured on Meta
- Testing a new version of Stack Overflow Jobs
Hot Network Questions
- Horror/Monster movie shown on TV in Basic Instinct
- Movie where three people get locked in a hotel
- If microwave ovens run at 2.4 GHz, what is the long-term effect on living tissue of exposure to this frequency, but with a thousand times less energy?
- Determining Jordan canonical form(JCF) of an operator given by complex differentiation.
- Which was the first liquid non hypergolic engine to be reignited in space?
- How can I draw inner vertical line centered in tabular?
- What is the difference of these MOSFET symbols?
- If I give my daughter $50k for her wedding and she elects to use the money to pay down a house, can I sue her?
- One Syllabus Many Syllabontes?
- Can my step dad steal from my room when I’m gone
- How long can a period be?
- Redshift of the CMB
- Elliptic operators over noncompact manifold
- Why doesn't b = a; f[a_] := b; f[2] return 2?
- Does Hebrews 13:2 teach that God's elect have become angels in disguise?
- Why don't room temperature superconductors exist?
- Should I recommend a reviewer that I have no contact with?
- \DeclareUnicodeCharacter{2212}{-} does not work for LuaLatex Compiler
- Why doesn't Singapore stamp passports?
- Should I use an author's code made available on request to help retract their highly cited paper?
- Root couldn't write to file with rw permissions for all users and owned by other user
- Security of a non-random password but that relies on information an attacker cannot possibly know
- Modelling from curve
- Could a VTOL aircraft use a helipad for landing/taking off?
UserRightsAssignment
Analyze the effective User Rights Assignments on a computer and compare results
Minimum PowerShell version
Installation options.
- Install Module
- Install PSResource
- Azure Automation
- Manual Download
Copy and Paste the following command to install this package using PowerShellGet More Info
Copy and Paste the following command to install this package using Microsoft.PowerShell.PSResourceGet More Info
You can deploy this package directly to Azure Automation. Note that deploying packages with dependencies will deploy all the dependencies to Azure Automation. Learn More
Manually download the .nupkg file to your system's default download location. Note that the file won't be unpacked, and won't include any dependencies. Learn More
Copyright (c) 2021 Friedrich Weinmann
Package Details
- Friedrich Weinmann
Compare-UserRightsAssignment ConvertTo-UserRightsAssignmentSummary Get-DomainUserRightsAssignment Get-UserRightsAssignment Import-UserRightsAssignment
Dependencies
- PSFramework (>= 1.6.201)
- UserRightsAssignment.nuspec
- changelog.md
- UserRightsAssignment.psd1
- UserRightsAssignment.psm1
- bin\readme.md
- en-us\about_UserRightsAssignment.help.txt
- en-us\strings.psd1
- functions\Compare-UserRightsAssignment.ps1
- functions\ConvertTo-UserRightsAssignmentSummary.ps1
- functions\Get-DomainUserRightsAssignment.ps1
- functions\Get-UserRightsAssignment.ps1
- functions\Import-UserRightsAssignment.ps1
- functions\readme.md
- internal\configurations\configuration.ps1
- internal\configurations\readme.md
- internal\functions\readme.md
- internal\scriptblocks\scriptblocks.ps1
- internal\scripts\license.ps1
- internal\scripts\postimport.ps1
- internal\scripts\preimport.ps1
- internal\scripts\strings.ps1
- internal\tepp\assignment.ps1
- internal\tepp\example.tepp.ps1
- internal\tepp\readme.md
- tests\pester.ps1
- tests\readme.md
- tests\functions\readme.md
- tests\general\FileIntegrity.Exceptions.ps1
- tests\general\FileIntegrity.Tests.ps1
- tests\general\Help.Exceptions.ps1
- tests\general\Help.Tests.ps1
- tests\general\Manifest.Tests.ps1
- tests\general\PSScriptAnalyzer.Tests.ps1
- tests\general\strings.Exceptions.ps1
- tests\general\strings.Tests.ps1
- xml\readme.md
- xml\UserRightsAssignment.Format.ps1xml
- xml\UserRightsAssignment.Types.ps1xml
Version History
- Outlook – General Tab
- Outlook – Phone Tab
- ADUC – General Tab
- ADUC – Address Tab
- ADUC – Account Tab
- ISA/TMG Scripts
- Active Directory on Fixed Ports
- RPC Internet Ports in Windows 2008
- DNS High Memory Utilization Issue
- WP – Cookies for Comments
- PHPBB HTTP 403 Forbidden Issue
- Shift Key and RDP Woes
- Domain Controller crash – memory leaking process
- Associate MP3 files to MPG123.EXE with parameters
- Privacy Policy

- Active Directory

Powershell GPO Deep Dive – Part 1

Creating a GPO in order to set User Rights Assignment completely in PowerShell: Can it be done?
This series of posts aims to share some interesting things learned about how GPOs are structured and things discovered about what backup-gpo and import-gpo routines are doing within the Powershell GPO module . The research was limited to User Rights Assignments and scripting up such a GPO – with absolutely no warranties what so ever!
Remember that changing security settings and user rights assignments can cause issues.
It turnns out that there is another way that this can be done by creating a blank GPO and creating the relevant files directly in SYSVOL in around 10 lines of code but this does feel even more dangerous / hacky to me.
Create a GPO for User Rights Assignment in Powershell
One of my colleagues asked me if we could script up an end-to-end GPO that would add in some Deny elements within the User Rights Assignments section. I immediately replied with “yeah sure, no worries” with a vague recollection that there was now a bunch of GPO commands like New-GPO that could create a GPO and command-lets that let you set registry values ( Set-GPRegistryValue ).
Some time later I discovered that actually…. NO.. No it is not possible to script up a full GPO to do what we wanted. It is possible to make a new empty GPO, Link it, add registry settings but if there is a need to add Deny Logon type elements to the Security node under User Rights Assignment, this is not currently possible.
This discovery disappointed me to say the least. What other options are available? Before moving any further let’s talk about what our given scenario was:
We would like to script up a GPO that will allow us to dynamically inject the usernames and groups that we want to be denied access to various User Rights Assignment elements in a GPO.
Of course, you could make a GPO through the GUI and then export it as a Backup using the Backup-GPO command and then save that somewhere and you could just import that GPO using Import-GPO . In our scenario, this just won’t cut it. We need to be able to inject our own account and group names – If we just blindly import, we’ll just get a bunch of stuff that may or may not be valid based on some statically exported values.
This got me thinking: what if we could Back up a GPO, get the resultant files prepared in such a way that we can replace the relevant values in the files that it creates with the user and group names of the things we want inside the GPO, and THEN run the Import-GPO command?
Before we jump down that rabbit hole, let us consider what gets created by the backup-gpo command-let in the specific scenario we are looking at.
What’s in an Empty GPO?
In order to back up a GPO, we first need a GPO to back up. In our example, we will create a GPO called “NewGPO”
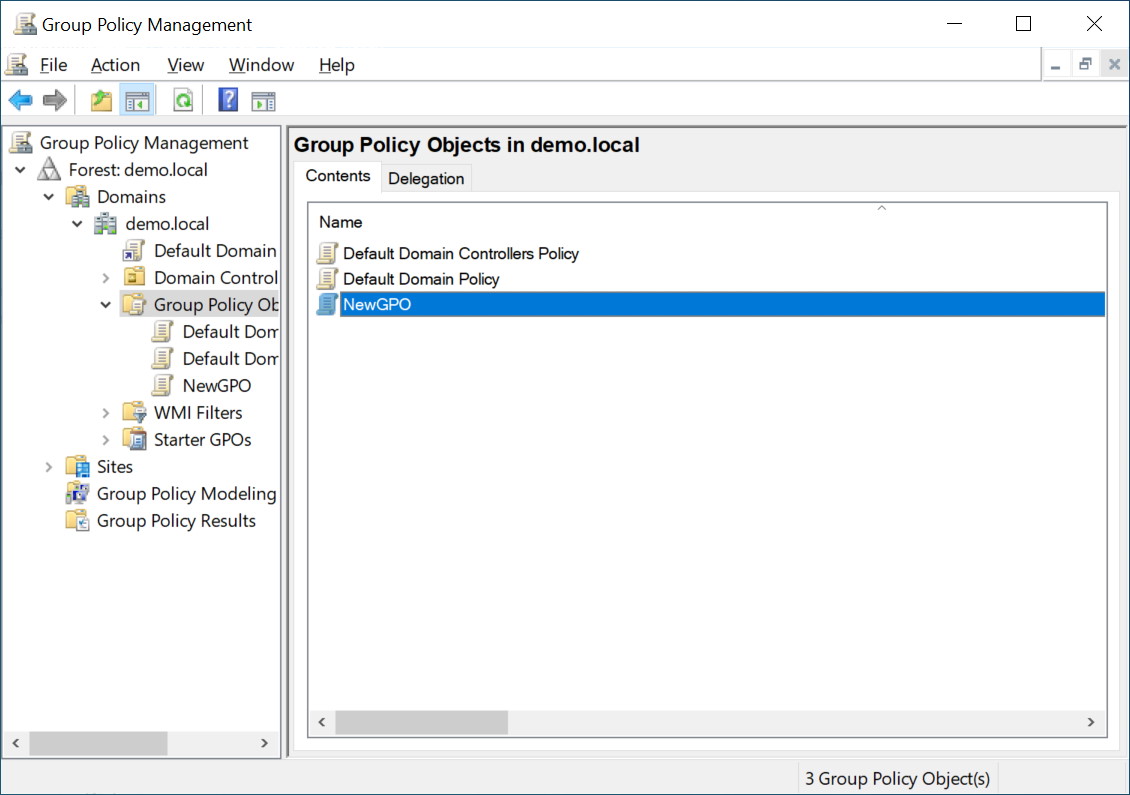
Looking at this GPO, we can see that it is empty. The only thing of note for us is the Unique ID (GUID) of {28AA0345-4804-4CE9-A41D-F7C89D5D5BD3}
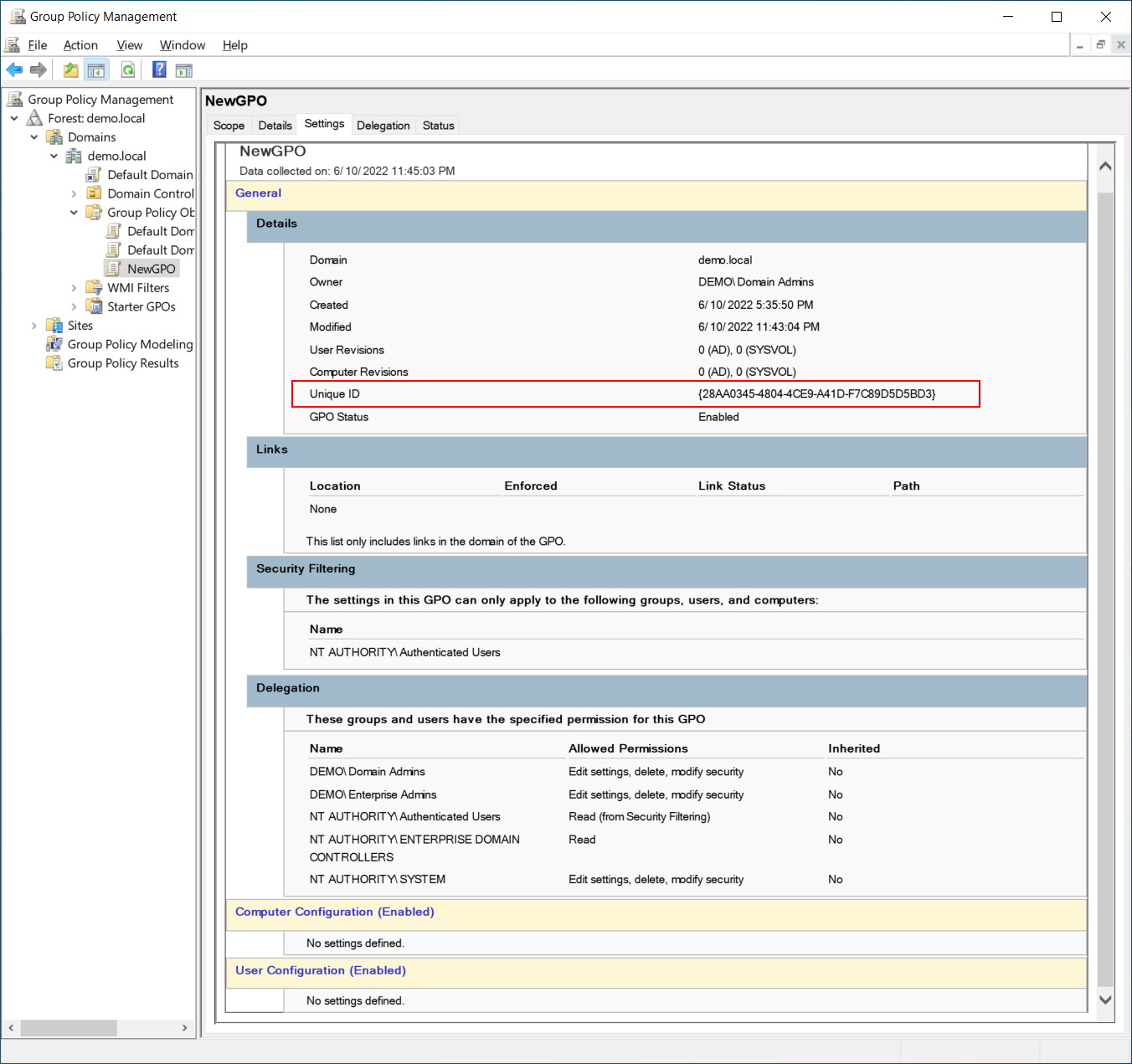
We will find this policy “{28AA0345-4804-4CE9-A41D-F7C89D5D5BD3}” under sysvol. In the filesystem, it looks like this:
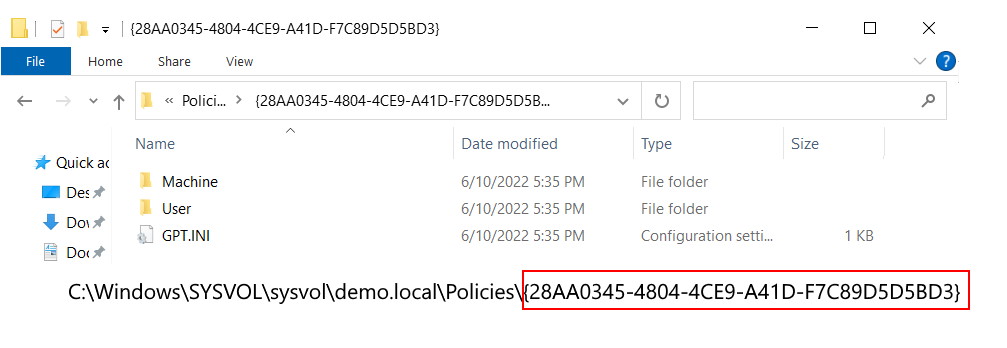
The first folder “Machine” is the structure for Computer related elements. The second folder “User” is for User related Policy Elements.
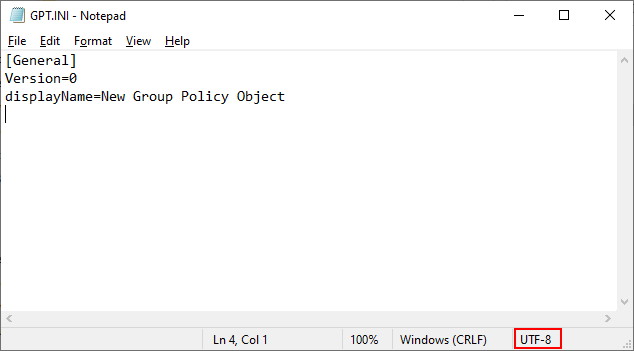
Since our GPO is empty, both folders will also be empty. However there is a file called “GPT.INI” in the root of this folder (note that the filename is in capital letters – strangely, capitals only when created not restored). At this point the GPT.INI contains the GPO Version (how many times the policy has been modified and saved) and displayName of the policy as shown in the console. The encoding for this file is “UTF-8” (see screenshot below as an example):
A GPO with one User Rights Assignment value set
Lets go back into our GPO and create a single element for Deny Access to this computer from the network and set it for Administrators as pictured below:
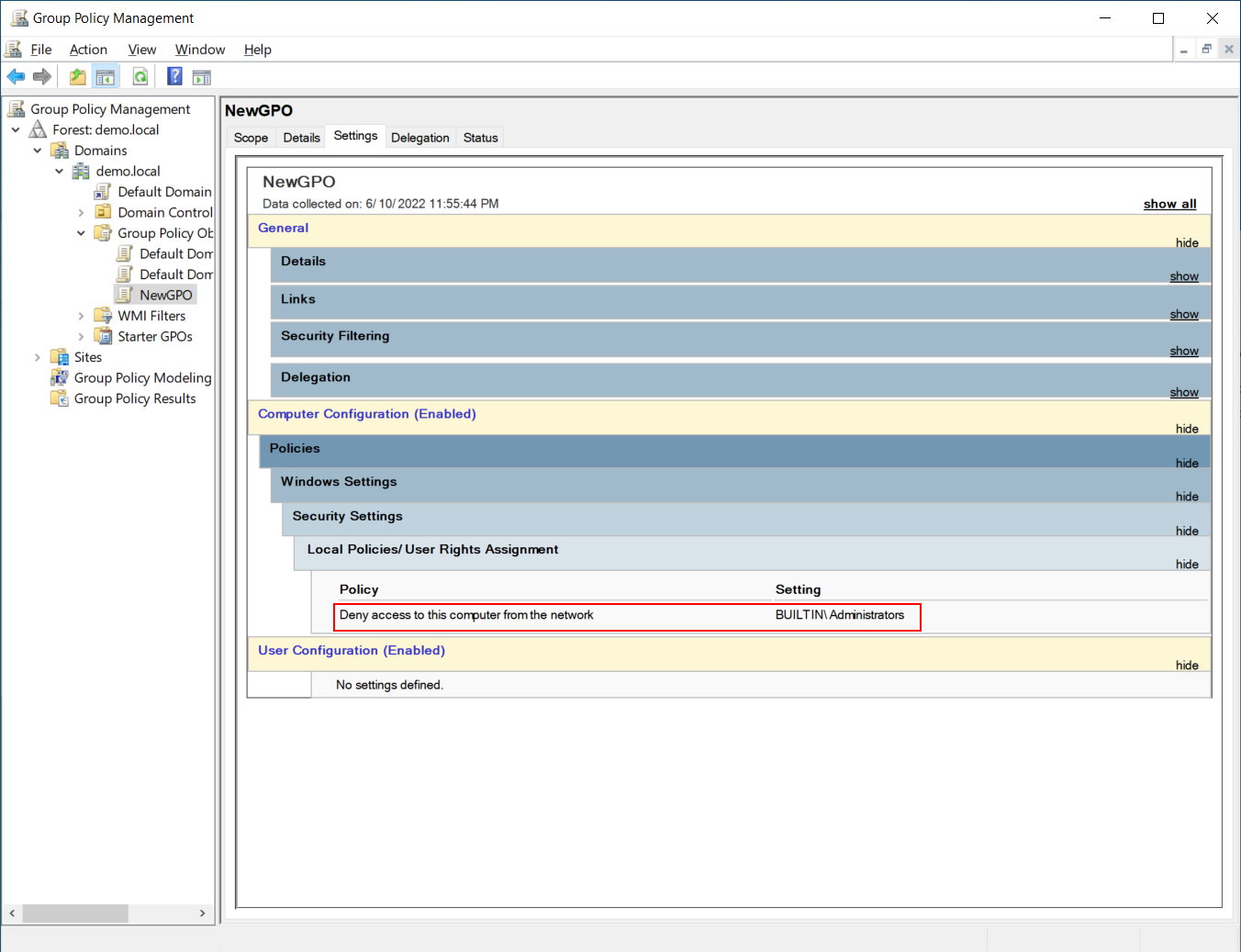
If we walk the filesystem under SYSVOL as we did earlier, we will find that everything is the same, except that the “Machine” folder tree now has a subfolder \Machine\Microsoft\Windows NT\SecEdit containing a single file called GptTmpl.inf
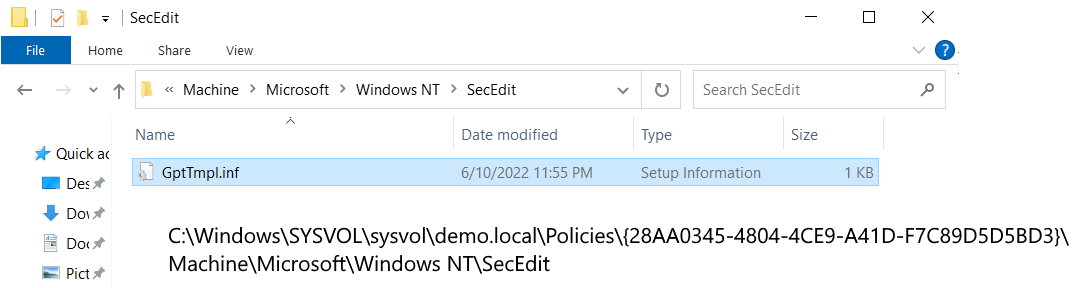
Looking at the file, we can see it is like any old school .inf file with sections in square brackets. The last section is where the actual Logon Rights are stored. In this case; we asked for Deny Access to this computer from the network to be set for administrators. The system translated that to DenyNetworkLogonRight = *S-1-5-32-544.
The system has converted our plain text request into this instruction. The SID shown here is simply a translation from the list of well known SIDs for Administrator.
What’s inside a Backup-GPO?
Let’s back up our example GPO using the Backup-GPO command in powershell:
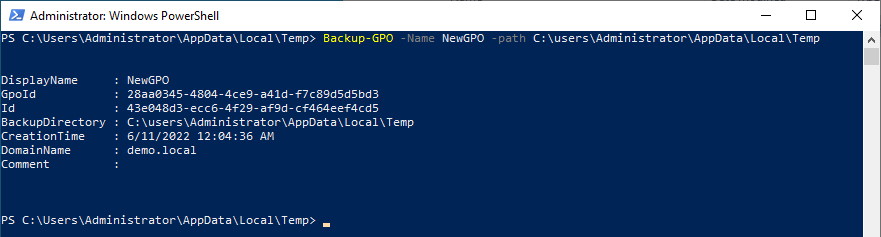
This creates a file structure within the Administrator’s temp folder. It creates a folder with a newly created random guid (referred to as the Backup ID). The original GPO’s GUID {28AA0345-4804-4CE9-A41D-F7C89D5D5BD3} is stored in the backup as “GpoID” and can be seen in the results of the command above (and in some of the GPO’s backed up files – more on that in a moment).
The backed up GPO has been saved under the new ID Folder name of {43E048D3-ECC6-4F29-AF9D-CF464EEF4CD5}.
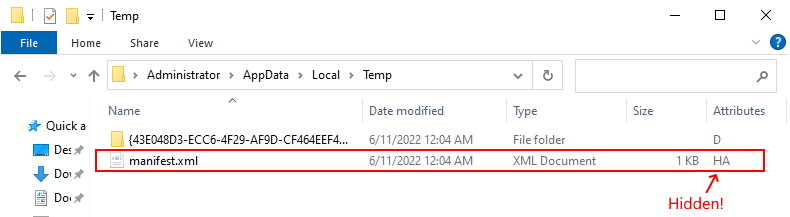
Be aware that there are two extra hidden XML files that get created after running a Backup-GPO command. The first file is outside the GUID folder at the folder where the command ran, The file is called Manifest.xml and is very important if you wish to import the GPO somewhere else.
The manifest.xml file is quite ugly. It is in XML, but it will probably show as one big long line of unbroken text. Here’s a version of our manifest.xml (encoding is UTF-8) with wordwrap turned on in Notepad:
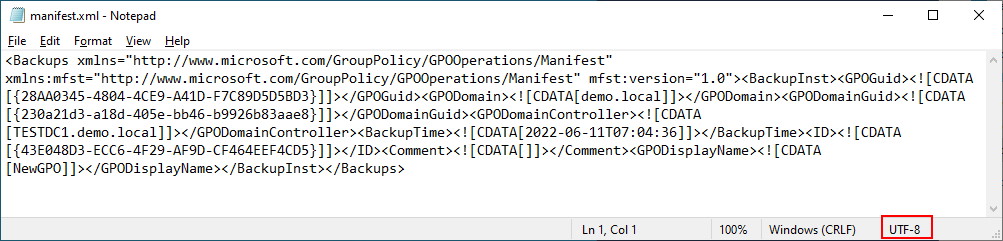
In short, the Manifest.xml file is used by the import-gpo routine to provide instructions on where GPOs that have been backed up can be found. It also contains information on the domain and domain controller it was backed up from. You will also find the time and the display name of the original GPO. Each GPO backed up will be found inside a <BackupInst> tag set.
As mentioned earlier, there is another hidden file. This file is in the GUID folder and called bkupinfo.xml. It looks remarkably similar to the Manifest file with one less tag. The first tag <backups> is not present – The Backups tag is only found in the manifest file and is used to encapsulate each GPO that can be found at the backed up folder location along with its associated GUID/ID pair. In our case, we only have one GPO, so the file looks almost identical (without the <Backups> tag).
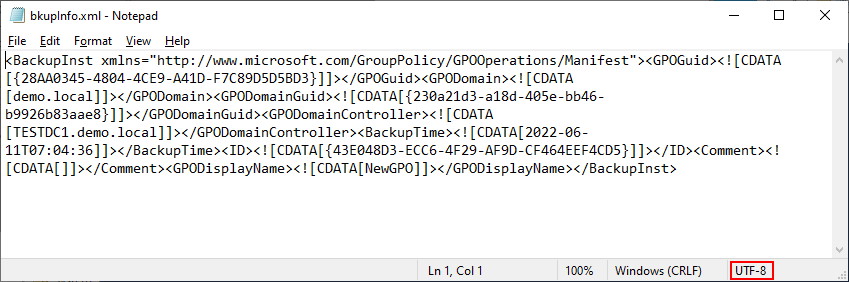
NOTE: For this file to be able to be imported, you must not break some tags over new lines or the import command will completely crash the powershell session; eg; The file formatted as below would cause the client to crash. You can remove the empty lines without a problem.

The purpose of the SecuritGroups section is so that if you have custom user/group names inside your policy, they can be transformed if imported into a new domain. Be aware that the entire SecurityGroups section MUST be on a single unbroken line otherwise Import-GPO will crash and terminate the current powershell session.
The purpose of the GroupPolicyCoreSettings is to capture some of the basic GPO settings, Domain, original GPO GUID (stored as ID) and any machine policies that are in use. In our example, we are only using the one policy for the Security section of our GPO – {827D319E-6EAC-11D2-A4EA-00C04F79F83A}{803E14A0-B4FB-11D0-A0D0-00A0C90F574B}. This section MUST all be on a single unbroken line otherwise Import-GPO will crash and terminate the current powershell session.
In our example, we are actually only using the Extension highlighted in blue, so we really don’t need the other extensions for import-gpo to work. In our scenario, we could safely remove the other extensions below the extension highlighted in blue. Be aware that the entire GPO Extension lines MUST be in a continuous unbroken line otherwise Import-GPO will crash and terminate the current powershell session.
Finally, we have the gpttmpl.inf file that is stored in the same subfolder location as the live GPO. The file also is identical to what was present in SYSVOL. Be aware that this file MUST be encoded as UTF-16LE (Unicode).
To build our GPO to set just our User Rights assignment, the minimum number of files is 4 (2 hidden):
Manifest.xml in the root of the folder where the backup was created (outside the GUID folder) – hidden. backup.xml inside the root of the GUID folder bkupinfo.xml inside the root of the GUID folder – hidden. GptTmpl.inf in the same subfolder structure as the oriignal real live GPO (<Guid>\DomainSysvol\GPO\Machine\microsoft\windows nt\SecEdit)
The structure looks like this:
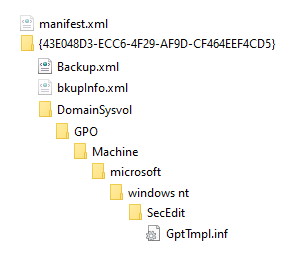
The Backup.inf file
What if I told you… we could build this all out and remove most of the values present in the backup.inf and still import fine with import-gpo ? Tune in next week for the next part in this series to learn more. I’ll put together some example template files.
In the mean time, here’s a sneak peak at the script that will be discussed: https://github.com/Jigsolving/powershell/blob/main/User%20Rights%20Assignment%20GPO/create-customURAGPO.ps1
Happy GPOing.
A full list of User Rights Assignment
The table below lists all the User Rights Assignments and their translated constant values. Each Policy setting is linked to a page over at Microsoft (***except one – there seems to be an error over there).
Notes: *You MUST specify at least Administrator for this right ** Administrators and SERVICE MUST be granted this right *** The associated description for this right is missing over at Microsoft at time of writing.
The featured photo in this post: Part of a photo by Francisco Jesús Navarro Hernández on Unsplash
RELATED ARTICLES MORE FROM AUTHOR
Domain join – minimum permissions, domain rejoin or prestaging – minimum permissions, install rsat tools via powershell, scheduled tasks: on event triggers with variables, protecting rpc, leave a reply cancel reply.
Save my name, email, and website in this browser for the next time I comment.
- +2808272282
- [email protected]
Calendar Folder Permissions Powershell
Calendar Folder Permissions Powershell . It lets the admins add, change or remove the calendar permissions in office 365 for each user as well as multiple. Getting a user's calendar folder permissions in exchange via powershell is pretty straight forward as you can just use the standard :\\calendar.
What can powershell do to assist in managing file and folder permissions? An organization/tenant administrator can grant access to any user calendar or a shared mailbox using.
Herein Lies The Power Of Powershell!
First step is that we need to connect to exchange online using powershell.
This Saves You Time By Allowing You To Assign.
There are a number of ways that powershell makes this process easier.
In This Article, We Will Discuss How To Get Permissions On.
Images references :.
To get calendar permission we will need to add :\calendar to after the userprincipalname.
The following instructions describe how to centrally customize calendar permissions on an exchange server from 2010 to 2019 using powershell.
First Step Is That We Need To Connect To Exchange Online Using Powershell.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
List Azure role assignments using Azure PowerShell
- 3 contributors
Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To determine what resources users, groups, service principals, or managed identities have access to, you list their role assignments. This article describes how to list role assignments using Azure PowerShell.
We recommend that you use the Azure Az PowerShell module to interact with Azure. See Install Azure PowerShell to get started. To learn how to migrate to the Az PowerShell module, see Migrate Azure PowerShell from AzureRM to Az .
If your organization has outsourced management functions to a service provider who uses Azure Lighthouse , role assignments authorized by that service provider won't be shown here. Similarly, users in the service provider tenant won't see role assignments for users in a customer's tenant, regardless of the role they've been assigned.
Prerequisites
- PowerShell in Azure Cloud Shell or Azure PowerShell
List role assignments for the current subscription
The easiest way to get a list of all the role assignments in the current subscription (including inherited role assignments from root and management groups) is to use Get-AzRoleAssignment without any parameters.
List role assignments for a subscription
To list all role assignments at a subscription scope, use Get-AzRoleAssignment . To get the subscription ID, you can find it on the Subscriptions blade in the Azure portal or you can use Get-AzSubscription .
List role assignments for a user
To list all the roles that are assigned to a specified user, use Get-AzRoleAssignment .
To list all the roles that are assigned to a specified user and the roles that are assigned to the groups to which the user belongs, use Get-AzRoleAssignment .
List role assignments for a resource group
To list all role assignments at a resource group scope, use Get-AzRoleAssignment .
List role assignments for a management group
To list all role assignments at a management group scope, use Get-AzRoleAssignment . To get the management group ID, you can find it on the Management groups blade in the Azure portal or you can use Get-AzManagementGroup .
List role assignments for a resource
To list role assignments for a specific resource, use Get-AzRoleAssignment and the -Scope parameter. The scope will be different depending on the resource. To get the scope, you can run Get-AzRoleAssignment without any parameters to list all of the role assignments and then find the scope you want to list.
This following example shows how to list the role assignments for a storage account. Note that this command also lists role assignments at higher scopes, such as resource groups and subscriptions, that apply to this storage account.
If you want to just list role assignments that are assigned directly on a resource, you can use the Where-Object command to filter the list.
List role assignments for classic service administrator and co-administrators
To list role assignments for the classic subscription administrator and co-administrators, use Get-AzRoleAssignment .
List role assignments for a managed identity
Follow these steps:
Get the object ID of the system-assigned or user-assigned managed identity.
To get the object ID of a user-assigned managed identity, you can use Get-AzADServicePrincipal .
To list the role assignments, use Get-AzRoleAssignment .
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources

IMAGES
VIDEO
COMMENTS
Personal File Server - Get-UserRights.ps1 Alternative Download Link. or. Personal File Server - Get-UserRights.txt Text Format Alternative Download Link. In order to check the Local User Rights, you will need to run the above (Get-UserRights), you may copy and paste the above script in your Powershell ISE and press play.
2. I'm new to PowerShell (PS). Currently I'm using windows server 2012 and I'm interested to know whether there is any way to export User Rights Assignment into a txt file. I tried. secedit /export /areas USER_RIGHTS /cfg d:\policies.txt. The above should should export it. So, I get this: Current Output.
9. You can use AccessChk in accomplish this task. Accesschk "domain\user" -a * will list all the permissions of a given domain user. You can call this program within a PowerShell script, concatenate the results into a text file, then filter out just the permissions you want to know about. Share.
As with Adding a privilege, we can remove privileges as well using Remove-Privilege. 1. Remove-Privilege -Privilege SeDebugPrivilege -AccountName boe-pc\proxb. As with Add-Privilege, you will need to log off and log back in to see the change take effect on your account.
1. 0. Managing User Rights Assignments in Powershell. Windows User Rights, also known as Windows Privileges, are traditionally managed via GPO or in the simplest of cases via the server's Local Security Policy. These assignments control special permissions that are often needed by IIS applications or other application hosting on Windows Servers.
1 Press the Win + R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy. 2 Expand open Local Policies in the left pane of Local Security Policy, and click/tap on User Rights Assignment. (see screenshot below step 3) 3 In the right pane of User Rights Assignment, double click/tap on the policy (ex: "Shut down the system") you want to add users and/or ...
Hi, this might be an overwhelming task but it is good to know whether this is possible. I want to list all permissions which are given to specific account via GPOs (default domain policy and default domain controller policy). It is account used by backup software and in order to work properly this account had to be given bunch of permissions to (Create a token object, Log on as a batch job ...
Logon rights control who is authorized to log on to a device and how they can log on. User rights permissions control access to computer and domain resources, and they can override permissions that have been set on specific objects. User rights are managed in Group Policy under the User Rights Assignment item.
How to Set Logon User Rights with the Ntrights.exe in windows 10(64 bit) [duplicate] Ask Question Asked 7 years, 9 months ago. Modified 8 months ago. ... Set and Check User Rights Assignment via Powershell You can add, remove, and check User Rights Assignment (remotely / locally) with the following Powershell scripts. ...
User rights are managed in Group Policy under the User Rights Assignment item. Each user right has a constant name and a Group Policy name associated with it. The constant names are used when referring to the user right in log events. You can configure the user rights assignment settings in the following location within the Group Policy ...
I want to modify the user rights associated with a local user account.I want to add groups and users to a particular User Rights. This is done by opening the group policy and opening the following folder in the console tree: Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment.
Manual steps: Open Group Policy Management. Navigate to the following path in the Group Policy Object. Select Policy. Right click & Edit: Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment. Add/remove the necessary users. Windows. Active Directory.
This cmdlets returns the effective policies for a user, based on either direct policy assignment or inheritance from a group policy assignment. For a given policy type, if an effective policy is not returned, this indicates that the effective policy for the user is either the tenant global default policy (if set) or the system global default policy. This cmdlet does not currently support ...
Analyze the effective User Rights Assignments on a computer and compare results. Minimum PowerShell version. 5.1. Installation Options. Install Module Install PSResource Azure Automation Manual Download Copy and Paste the following command to install this package using PowerShellGet More Info. Install-Module -Name UserRightsAssignment ...
Creating a GPO in order to set User Rights Assignment completely in PowerShell: Can it be done? This series of posts aims to share some interesting things learned about how GPOs are structured and things discovered about what backup-gpo and import-gpo routines are doing within the Powershell GPO module.The research was limited to User Rights Assignments and scripting up such a GPO - with ...
To find the permissions required to run any cmdlet or parameter in your organization, see Find the permissions required to run any Exchange cmdlet. ... The RoleAssignee parameter specifies the role group, assignment policy, user, or universal security group (USG) for which you want to view role assignments. If the RoleAssignee parameter is used ...
I've asked a similar question like this before to get the Local User right in PowerShell of a certain domain user, now I would like to enable the right. There are a few rights I am looking to enable, but for this example I will use Logon as a Batch Job. Ntrights does not come with Windows Server 2008 by default, so I cannot use that method.
As I understand this problem, you want to translate the text output produced by secedit /export /areas USER_RIGHTS /cfg d:\policies.txt command into the equivalent output "exported from gui". I borrowed the list of equivalences from the answer at this question, added a list of equivalences for each one of the terms and used they to write a Batch file that should perform such translation.
This Saves You Time By Allowing You To Assign. There are a number of ways that powershell makes this process easier. In This Article, We Will Discuss How To Get Permissions On. Images References : ... Get Calendar Permissions Powershell Edit Office 365 User Calendar, Getting a user's calendar folder permissions in exchange via powershell is ...
Use the Get-AzRoleAssignment command to list all role assignments that are effective on a scope. Without any parameters, this command returns all the role assignments made under the subscription. This list can be filtered using filtering parameters for principal, role and scope. The subject of the assignment must be specified. To specify a user, use SignInName or Microsoft Entra ObjectId ...
To find the permissions required to run any cmdlet or parameter in your organization, see Find the permissions required to run any Exchange cmdlet. Examples Example 1 Get-RoleAssignmentPolicy. This example returns a list of all the existing role assignment policies. Example 2 Get-RoleAssignmentPolicy "End User Policy" | Format-List
To list role assignments for a specific resource, use Get-AzRoleAssignment and the -Scope parameter. The scope will be different depending on the resource. To get the scope, you can run Get-AzRoleAssignment without any parameters to list all of the role assignments and then find the scope you want to list.